Server Installation
General architecture:
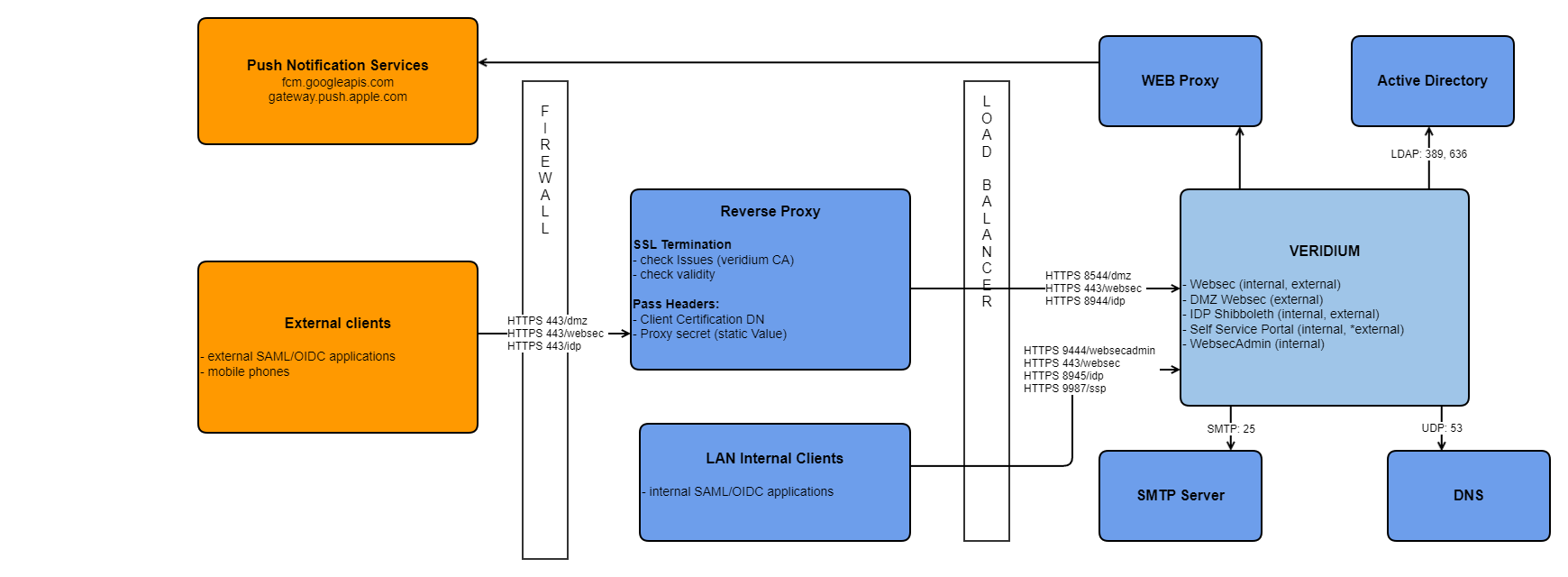
Network Access Control List and DNS hosts for port implementation:
DNS entries:
DNS internal: HOST.DOMAIN.INTERNAL (eg. veridium.dev.local)
DNS external: HOST.DOMAIN.EXTERNAL (eg. veridium.veridium-dev.com)
Services and ports:
Internal access: 443 (websec), 9444 (websecadmin), 8945 (idp), 9987 (ssp)
External access: 443 (websec), 8544 (dmzwebsec), 8944 (idp), 9987(self service portal - optional, for registration)
Network Access Control List and DNS hosts for FQDN implementation:
DNS entries:
Internal: HOST.DOMAIN.INTERNAL (websec), admin-HOST.DOMAIN.INTERNAL (websecadmin), shib-HOST.DOMAIN.INTERNAL (idp), ssp-HOST.DOMAIN.INTERNAL (self service portal)
External: HOST.DOMAIN.EXTERNAL (websec), dmz-HOST.DOMAIN.EXTERNAL (dmzwebsec), shib-HOST.DOMAIN.EXTERNAL (idp), ssp-HOST.DOMAIN.EXTERNAL (self service portal - optional, for registration)
Ports:
Internal access: 443
External access: 443
Other services:
Service | Source | Destination | Port | Protocol | Bi-directional |
Deployment | Deployment Server (ex. normally, it is used one of the nodes) | WEBAPP + PERSISTENCE | 22, 443, 9444, 8945, 9987 (for PORTS) 22, 443 for FQDN implementation | TCP | No |
|
|
|
|
|
|
Web Service | WEBAPP | PERSISTENCE | 2181, 9042, 9092, 9095 | TCP | No |
Persistence Service | PERSISTENCE | PERSISTENCE | 2181, 2888, 3888,7000, 7001, 7199, 9092, 9042, 9095 | TCP | No |
* if ILP installed | WEBAPP ILP | PERSISTENCE | 2181, 9042, 9092, 9095 | TCP | No |
* if ILP installed | WEBAPP | WEBAPP ILP | 443 | TCP | No |
RAEP | Windows RAEP Servers | Intranet Balancer for WEBAPPS | 443 | TCP | No |
RAEP | Windows RAEP Servers | Load Balancer for ADCS - PKI (active-active setup) | 443, 135, 139, 49152 - 65535 | TCP | No |
RAEP | Windows clients W11/W10 | Load Balancers for Windows RAEP Servers | 443 | TCP | No |
RAEP | Load Balancers for Windows RAEP Servers | Windows RAEP Servers | 443 | TCP | No |
CP | Windows clients W10/W11 Credential Provider | Intranet Load Balancers for Webapps | 443, 8945 | TCP | No |
WEBAPP Servers | WEBAPP | ADDS - LDAP | 636 or 3269 (or 389,3268) | TCP | No |
|
|
|
|
|
|
DNS | All Nodes | DNS Server | 53 | UDP | Yes |
NTP | All Nodes | NTP Server | 123 | UDP | No |
SMTP | All Nodes | SMTP | 25 | UDP | No |
SIEM | All Nodes | SIEM |
|
|
|
SMS Gateway | WEBAPP (via reverse proxy or direct) | SMS Gateway, if required | 443 | TCP | No |
|
|
|
|
|
|
SSO Integration | SSO | Intranet Load Balancers for Webapps | 443, 8945 | TCP | No |
CITRIX Integration | Storefront, Netscaler | Intranet Load Balancers for Webapps | 443, 8945 | TCP | No |
CITRIX Integration | VDA | Domain Controller | 389, 636, 3268, 3269 | TCP | No |
RADIUS | Client Freeradius Server | WEBAPP | 2083 | TCP | No |
RADIUS | Client Freeradius Server | WEBAPP | 1812, 1813 | UDP | No |
|
|
|
|
|
|
Admin (WebAPP and Persistence Nodes) | Vendor PCs - MFA Admin PCs | WEBAPP and Persistence nodes | 22 | TCP | No |
Admin (Windows RAEP Servers) | Vendor PCs - MFA Admin PCs | Windows RAEP Servers | 3389 | TCP | No |
|
|
|
|
|
|
Google push - Android Verdium Application | WEBAPP (via reverse proxy or direct) | 443 | TCP | No | |
Apple push iOS Verdium Application | WEBAPP (via reverse proxy or direct) | 443 | TCP | No |
Email, SMS Messaging and Push Notification Services
For using the directory services PoC, OTP code delivery method must be configured either via email (SMTP), or SMS messages to users during enrollment.
To use email, use the administration dashboard to enter your email server SMTP parameters into the appliance. Instructions are provided later in this guide.
Using Unique Names
To perform end-to-end testing, you will need to use a publicly trusted certificate and Public DNS records that match the name(s) on your certificate. Choose whether you use:
Port Mapping. One unique DNS record with port numbers for different service endpoints. In this instance you will use a certificate with one subject name for all endpoints. (i.e. vid.domain.com)
SNI Mapping. Multiple unique DNS record (SNI mappings) for different service endpoints. (i.e. admin-vid.domain.com). Use a multi-domain (SAN) certificate with subject alternative names for the different endpoints or a wildcard certificate (*.domain.com)
Based on your decision, obtain a valid, globally recognized SSL certificate for your server. Using a self-signed certificate will require configuring your smartphone to trust the root CA that generated the certificate, so it is generally easier to use a public certificate. Your certificate must be in PEM format and include any Intermediate and Root certificates in the chain as well as the unencrypted private key.
Obtain licenses from your Veridium sales engineer. As licenses are based on the certificate digest, you must have the certificate before Veridium can generate the licenses.
In the table below, the first URL is used for SNI service mapping and second URL is used for PORT service mapping depending on your configuration. Typically you would choose either SNI or the port based approach, not both. (Examples are shown for an environment name of PoC and a domain of poc.veridium.com, substitute your values as appropriate.)
