SAML Authentication
The standard deployment provides out-of-the box VeridiumID SAML IdP installation and takes full advantage of the VeridiumID Authentication Orchestration Engine while maintaining the full benefits of a SAML integration like:
Standardization - SAML is an open standard that is widely adopted and allows easy interoperability between systems.
User Experience - SAML provides out-of-the-box SSO (Single Sign-on) experience and allows users to access multiple Service Providers by signing in just once.
Increased security - as a single point of authentication, in the secured IdP, the accounts are no longer duplicated or shadowed, reducing the attack points for identity theft.
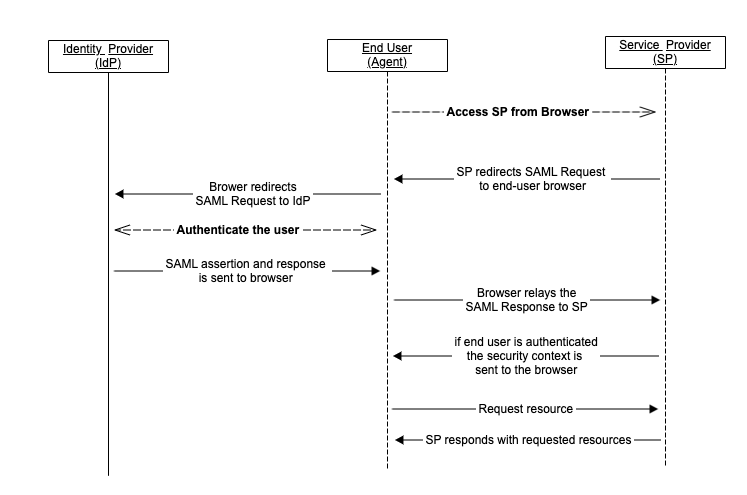
SAML 2.0 (Security Assertion Markup Language) is an open standard created to provide cross-domain single sign-on (SSO). In other words, it allows a user to authenticate in a system and gain access to another system by providing proof of their authentication.
Terminology
A Service Provider (SP) is the entity providing the service (e.g. Microsoft Outlook).
An Identity Provider (IdP) is the entity providing the identities, including the ability to authenticate a user. Also contains the user profile and additional information about the user such as first name, last name and may provide a richer set of user data (location, group/role, authentication risk score etc.).
A SAML Request is an authentication request that is generated by the SP to "request" an authentication.
A SAML Response is the authentication response generated by the IdP and contains the assertion of the authenticated user. Additionally, it may contain other information, such as user profile information and group/role information, depending on what the Service Provider may support.
A Service Provider Initiated (SP-initiated) sign-in describes the SAML sign-in flow when initiated by the Service Provider. This flow is triggered by an action of the end-user that aims to access a protected resources.
An Identity Provider Initiated (IdP-initiated) sign-in describes the SAML sign-in flow initiated by the Identity Provider. The Response that is redirected to the Service Provider to assert the user's identity.
Integrate SAML Application
Prerequisites:
Valid LDAP configuration
The VeridiumID server provides easy integration for any SAML Service Provider. Integrated SAML applications are managed from Veridium Manager, under Applications section.
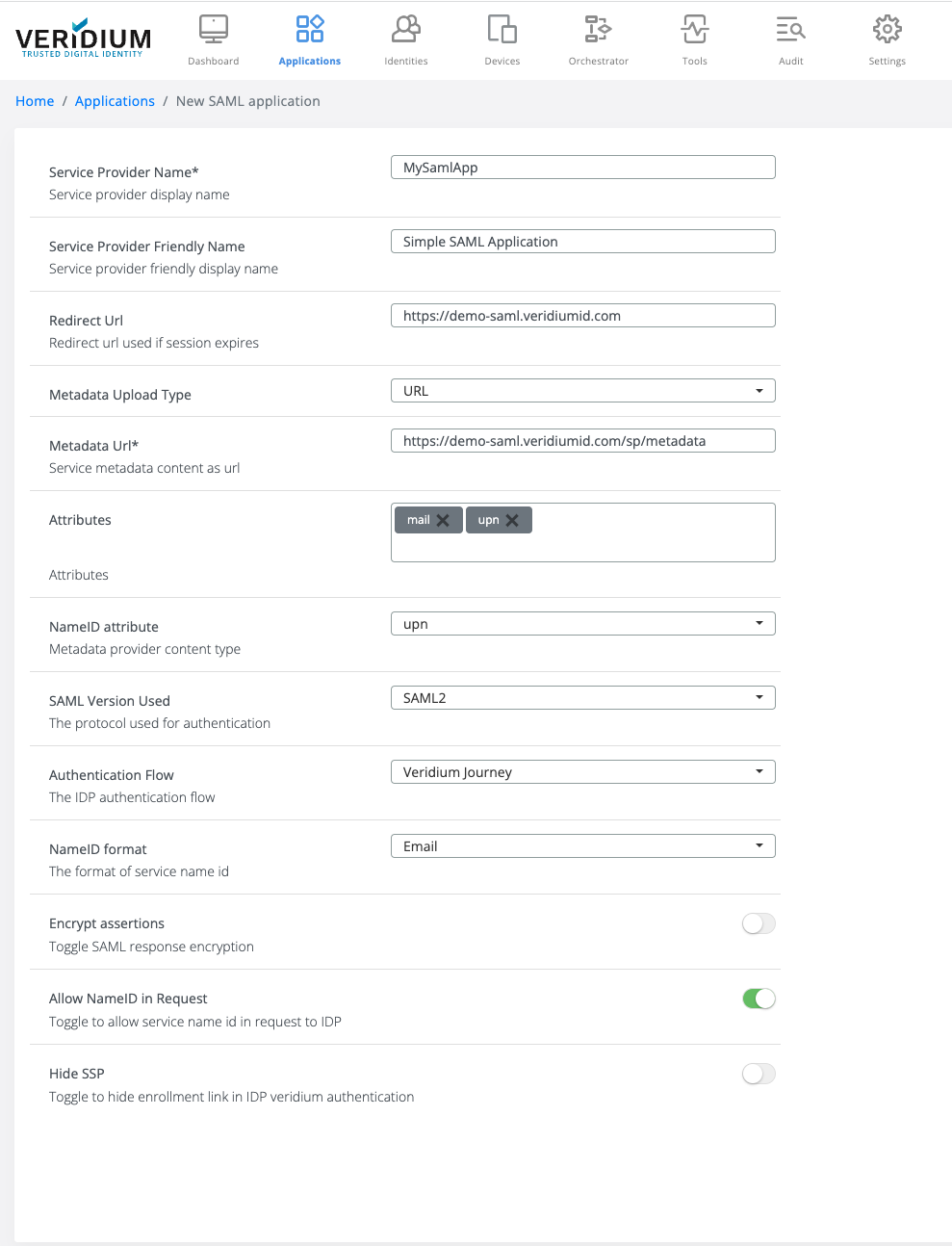
Create your SAML application integration by accessing Add SAML app from actions panel SAML Application and complete the configuration form:
Complete SAML application identification details:
Service Provider Name - the application name identifier
Service Provider Friendly Name - the application display name that will be displayed in the context screen or session details.
Redirect URL - the URL used for recreate an opportunity session in the Veridium IdP during an authentication. (Refresh Session Opportunity QR).
Configure SP-IdP trust
The SAML trust relationship and initial configuration is established by SAML metadata exchange between SP and IdP. The SAML Metadata contains end points to be used to authenticate users, bindings (transportation methods) supported, requirements on signing and very important, public keys and certificates that is used to establish trust.
a. Configure SP metadata on the IdP
URL Resource Type (recommended) - a dynamic resource that is periodically refreshed and validated by the Veridium IdP. This ensures that the configuration we’ll be automatically refreshed when the signing/encryption are updated or the binding mechanism is changed.
File Resource Type - the metadata may be statically uploaded on the IdP and requires manual updates when the signing/encryption are updated or the binding mechanism is changed.
There are cases when the SP do not provide out of the box metadata resource (URL or File) and in this case the metadata file must be manually filled in.
b. Configure IdP metadata on the SP
The IdP metadata may be referenced from SAML - Connectors actions panel by using Copy IDP Metadata URL or Download IDP Metadata, depending on the SP supported configuration.
The IdP configuration is managed from SAML Connectors - IDP Properties

3. Configure SAML assertion attributes
When the user is identified and validated the IdP will respond with the SAML assertion that attest the user attributes. The attributes of the SAML assertion may be configured for each SAML application integration and may be addressed as user display information or for authorization purposes. (e.g. First Name, Last Name, Groups/Roles etc.)
a. Attributes - all the attributes that will be included in the SAML Assertion
b. NameID Attribute - the Subject of the SAML Assertion
If you need to define new attributes please see SAML Connectors - Subject Derived Attributes and LDAP extended attributes
4. Configure Authentication Flow
By default the authentication flow is Veridium Journey that uses the Veridium Orchestrated Authentication Engine, but SPNEGO is also supported if configured. See more on SPNEGO configuration here.
5. Enable/Disable Encrypt Assertions
Some Security Policies may require that SAML Assertions to be encrypted as extra security level. Apply this by asking guidance from your Security Policies advisors.
6. Allow NameID in Request
There are cases when the SP may already collect relevant information about the user (e.g. username) and they may forward it to the IdP. This check will permit and verify the user assertions at the end and provide SAML Assertions only if the same user was identified during validation.
7. Hide SSP
During an authentication the IdP may display or hide a link to the Self Service Portal enrollment to manage account enrollment - enroll or reset authentication methods.
Advanced IdP Configuration
Configure User Attributes
The user attributes are important in a SAML Assertion as it provides relevant trusted information to the SP without integrating the SP to the same identity pool (e.g. LDAP). The IdP support static and dynamic attributes that may be added on the SAML assertion. See SAML Connectors - Subject Derived Attributes and SAML Connectors - Static Attributes for more information.
Scripted Attributes
There are cases when the raw attributes from LDAP connection should be processed. The IdP supports to scripted attributes and may be extend to complete any post-processing operation.
An example for filtering only relevant member groups may be found here.
Security keys configuration
The IdP security keys may be configured in the SAML Connectors - Security & keys. The IdP security keys may be the subject of HSM Configuration.