SSO Token Protection
Overview
This document explains the concept of how the SSO Tokens (SAML or OIDC) are protected by Veridium and the correlation between Windows login and browser user session.
Recap Windows logon
On Windows machines, we have the following Veridium components:
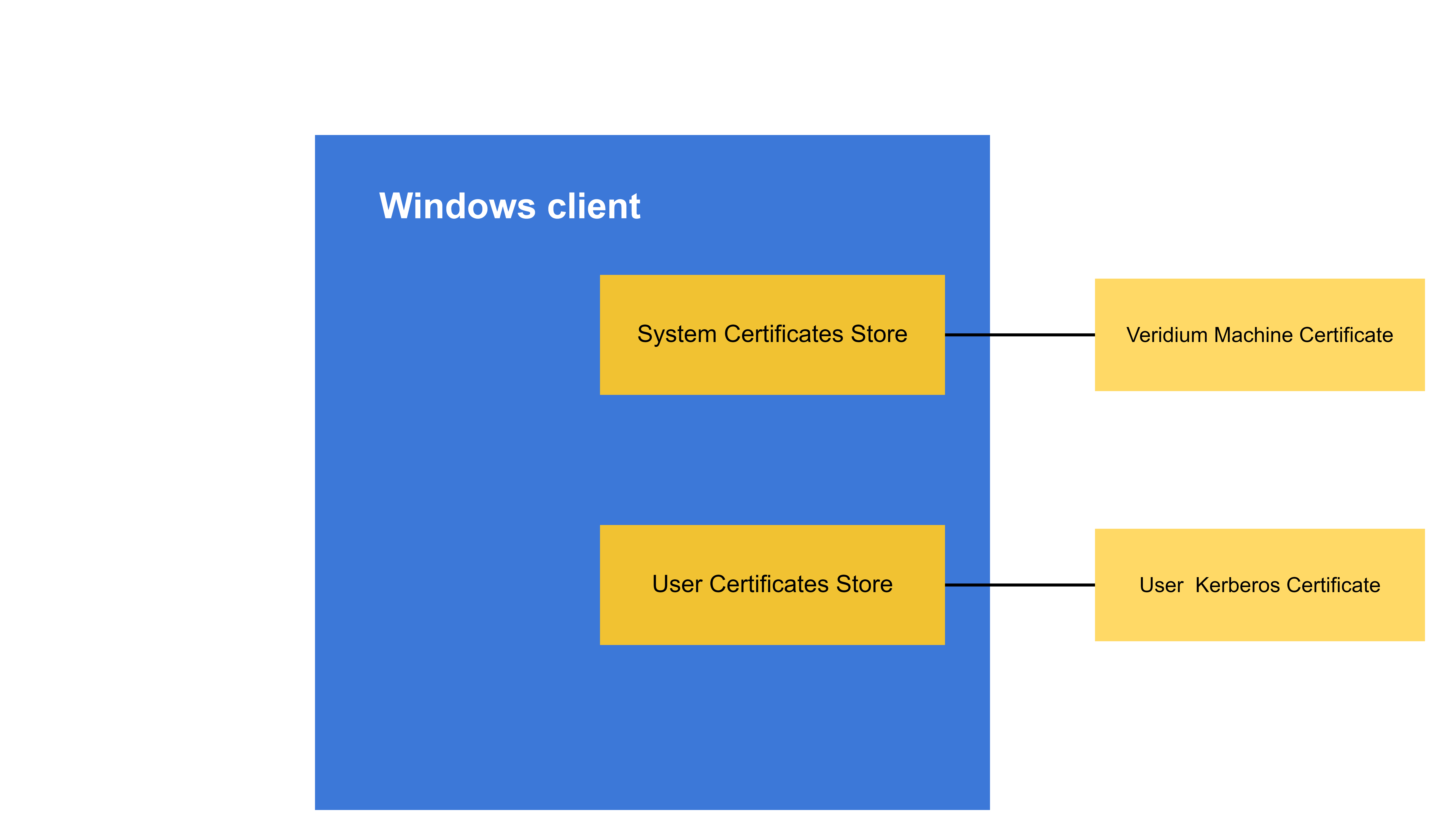
BopsLogonService – system services which enrolls the Windows machine in Veridium , and obtains a machine certificate which will be presented to Veridium service during the authentication flows.
After a Veridium authentication, an user certificate is issued by the Registration Authority, installed in the user store and the Windows Kerberos logon is performed.
Information about the Windows machine is reported back to VeridiumID server.
Recap on Veridium IdP
In version 3.6 we add support for certificate login as authentication method. That means that the user can present a certificate when authenticating in browser.
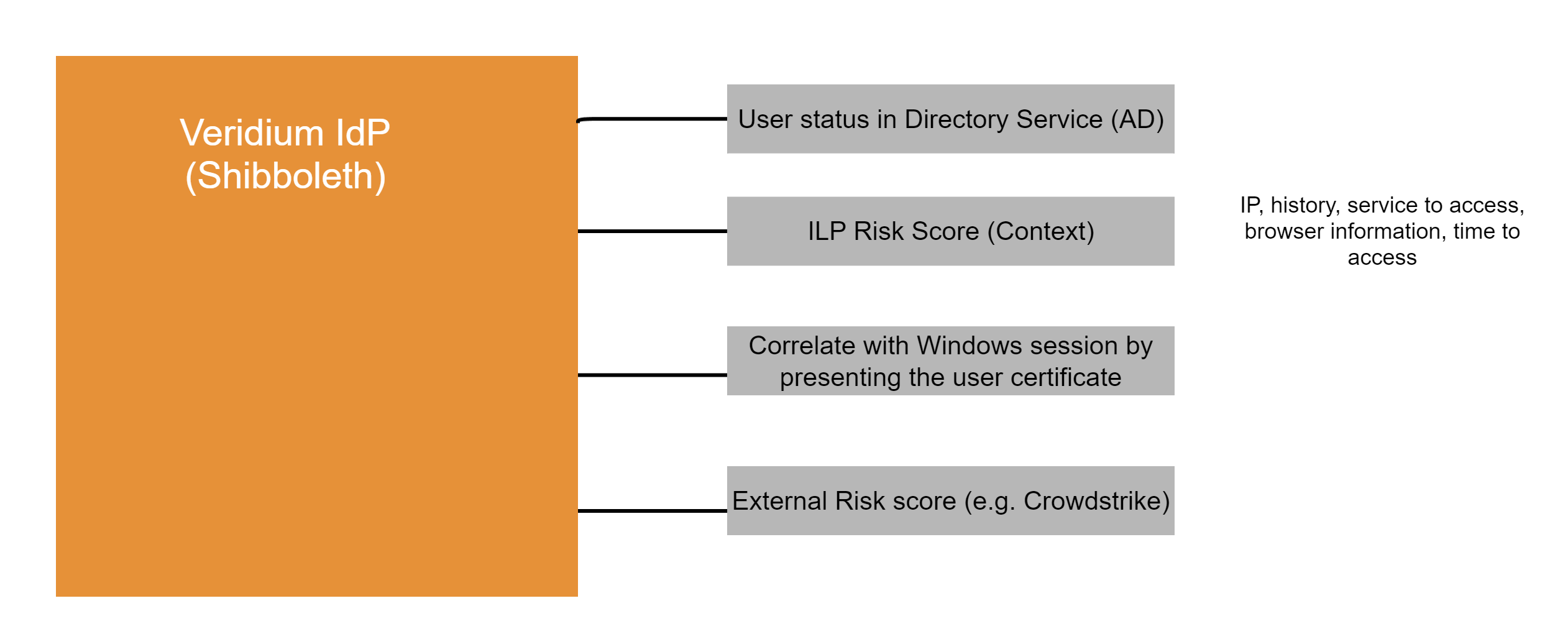
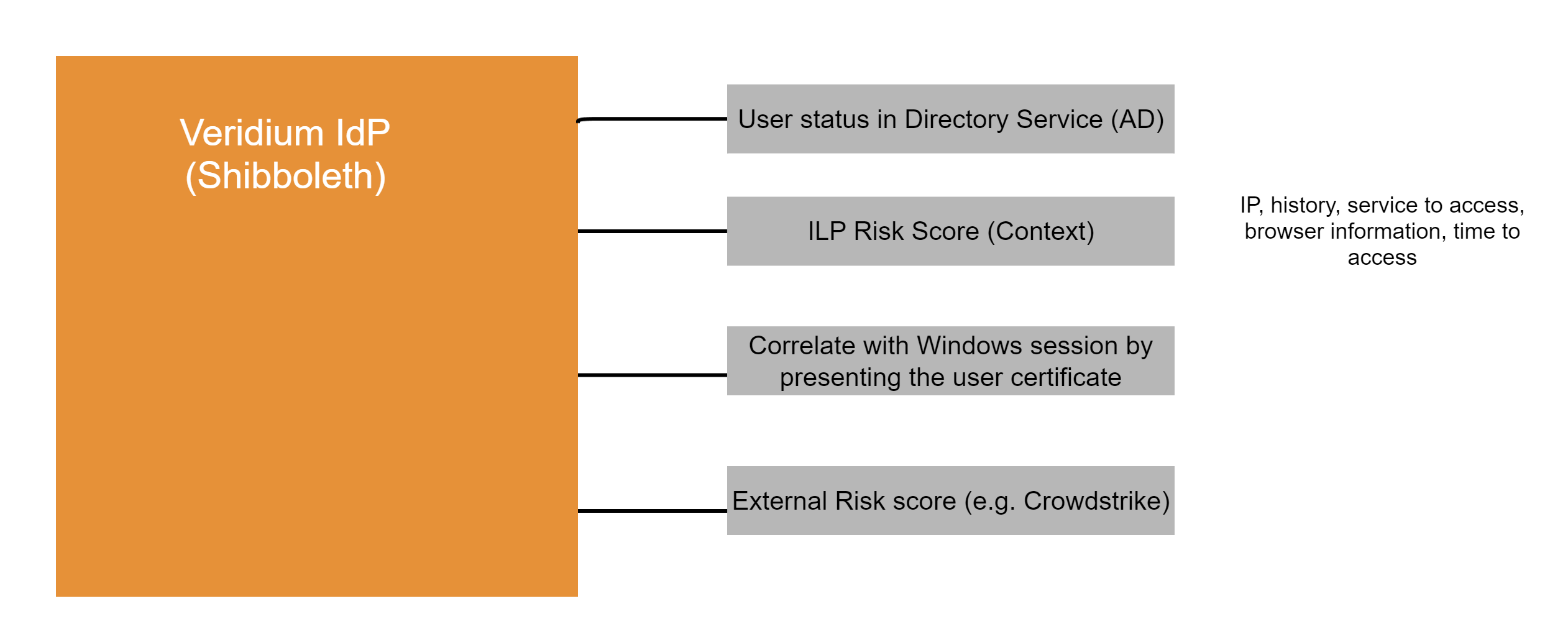
How we protect SSO experience
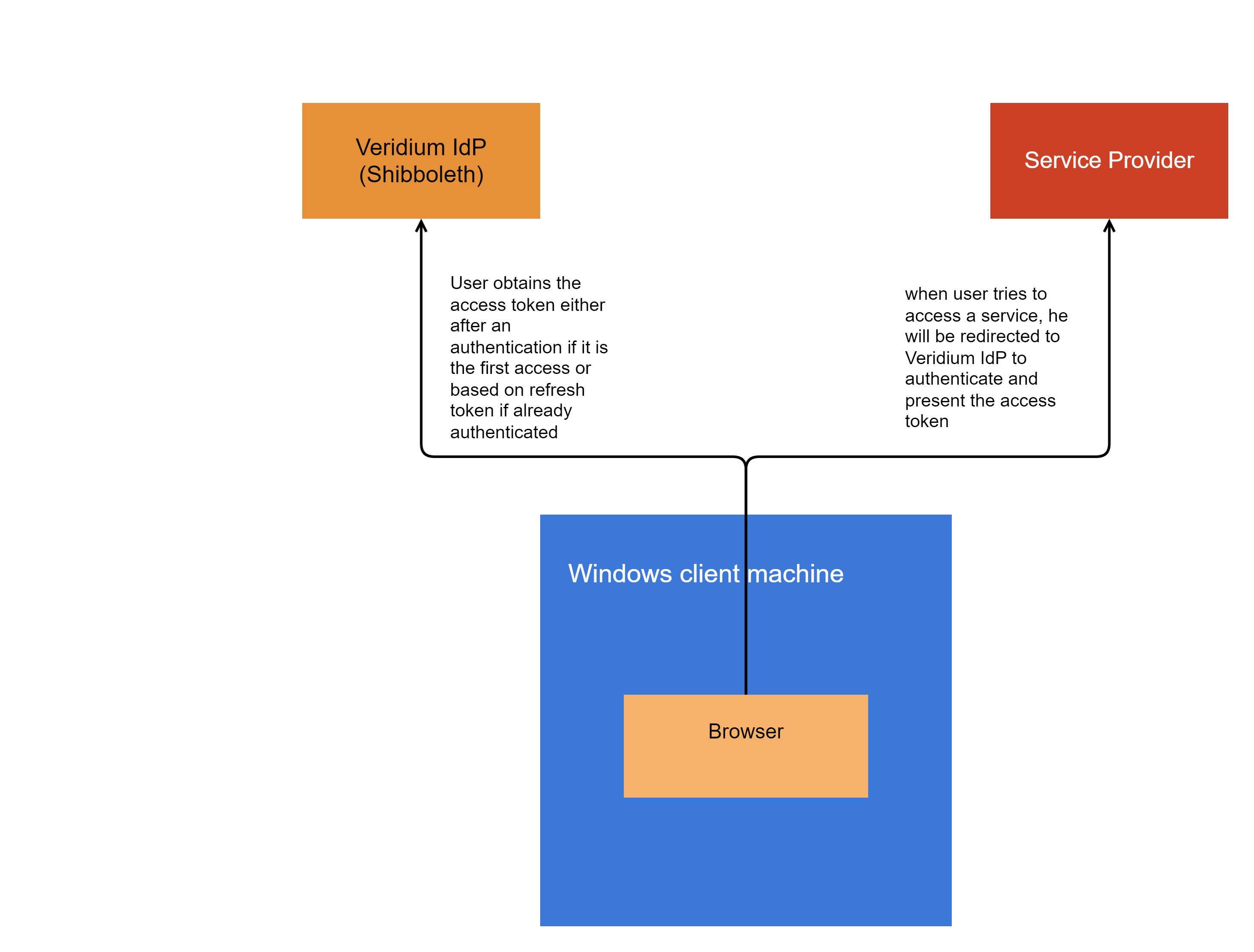
SSO Authentication
When user first authenticates in a browser, we can leverage the user certificate already used and correlate it with the information gathered during Windows logon. (e.g. same IP address, browser version, location, etc.). Therefore, the session binding is done by correlating Windows logon information and initial authentication in browser against Veridium IdP.
Single Sign On Experience in-browser
Once the user is authenticated and obtains the Primary Refresh Token (PRT), then the access to services is based on access tokens obtained from IdP based on PRT. That requires a roundtrip to Veridium IdP service and presenting the PRT.
That means that Veridium IdP can re-evaluate the context like: user certificate, browser information, what service user tries to access, IP address, and a risk score can be calculated by Veridim ILP or External Risk tool.