FIDO 2.1 (Webauthn level 3)
The FIDO protocol is continuously evolving to meet the market demands, starting with Passkeys adoption and the support of synchronizable credentials targeting mainly consumer markets and wrapping up with Passkeys adoption for Enterprise ready solutions (like Microsoft Authenticator).
The latest features and changes within the protocol should be adopted in the Veridium FIDO server.
There are several steps to accomplish, as this is a continuous process that follows the evolution of the FidoAlliance specifications:
Redesign the FIDO server integration APIs
Remove the Veridium device business logic from the FIDO server.
Improve support for authentication device management during enrolment and authentication
Provide out-of-the-box FIDO conformance testing APIs;
Enable FIDO Resident Key authentication as User Engagement in the Veridium IdP;
Enable support for commonly used extensions:
User Verification Method Extension (uvm);
Device-bound public key extension (devicePubKey);
minPinLength - enforce a minimum pin length for client pin verification method;
Support iframe for cross-domain FIDO passkey registration and authentication:
This may be useful to allow single credential registration for different domains. For example register within Veridium Self Service Portal credentials for Veridium internal/external domains or even Microsoft Entra.
Address known issues:
Improve Relying Party default configuration;
Improve the FIDO authenticator management list and remove deprecated code;
Fix the FIDO credential enrolment flow on SSP credential registration delegation.
The latest specifications are currently in release/working draft, but they will be published as
3.c. minPinLength extension
The organizations using FIDO keys want to have the possibility to enforce the minimum PIN length. To achieve this, Veridium Server uses the minPinLenght extension to get the minimum PIN length configured on the key.
If the key is not supporting this extension, or the key is not configured to share it with the server, then the validation ignores the configured values - they are not applied.
Also, for keys enrolled before this feature was available the validation is skipped because the key’s minPinLength is shared with the server during enrollment.
Configuration
Step 1
In Veridium Manager interface, go to Settings section, then select FIDO Relying Parties, then select the desired Relying Party and edit it
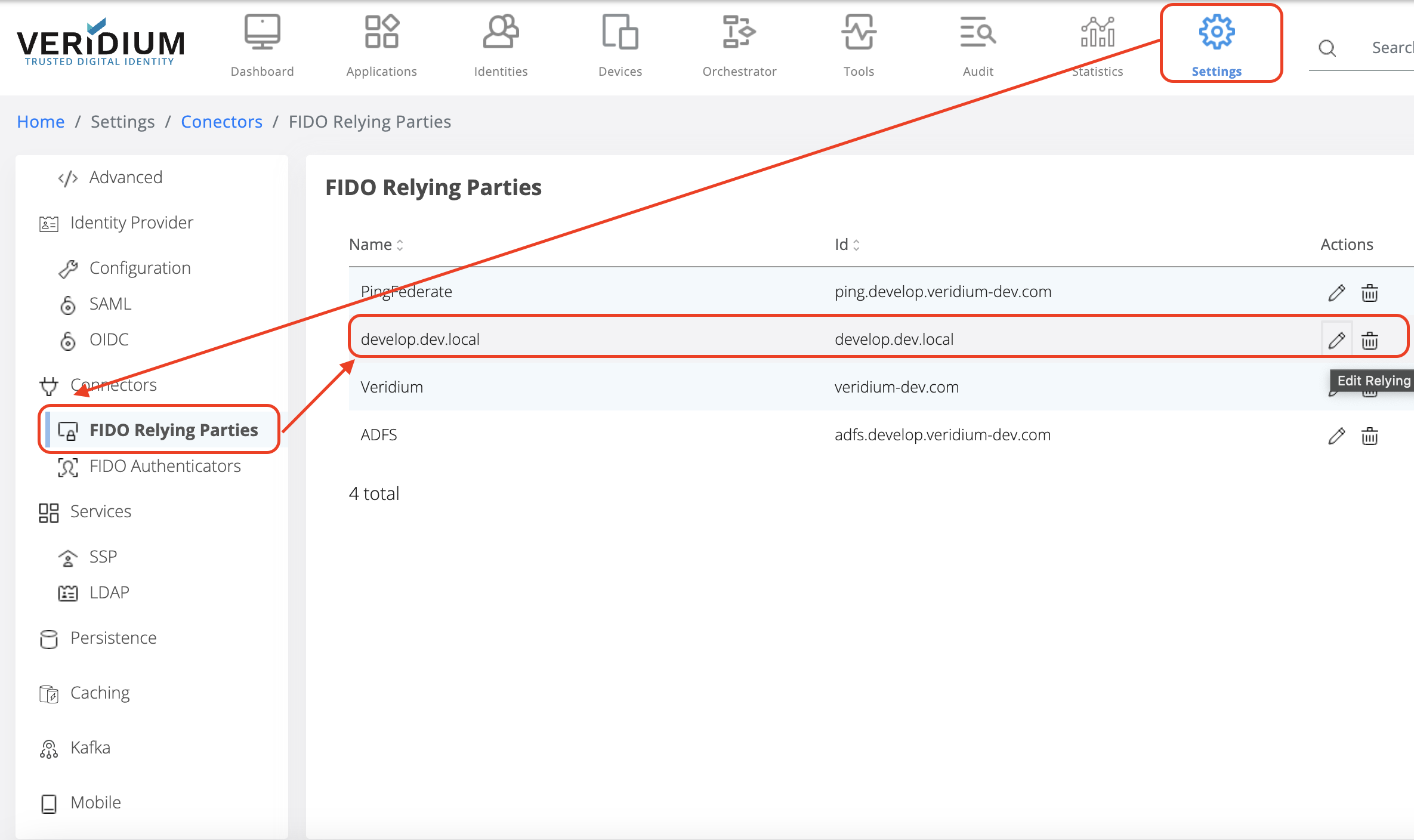
Step 2
In the Relying Party details, scroll down to minPinLength configuration section, as shown below:
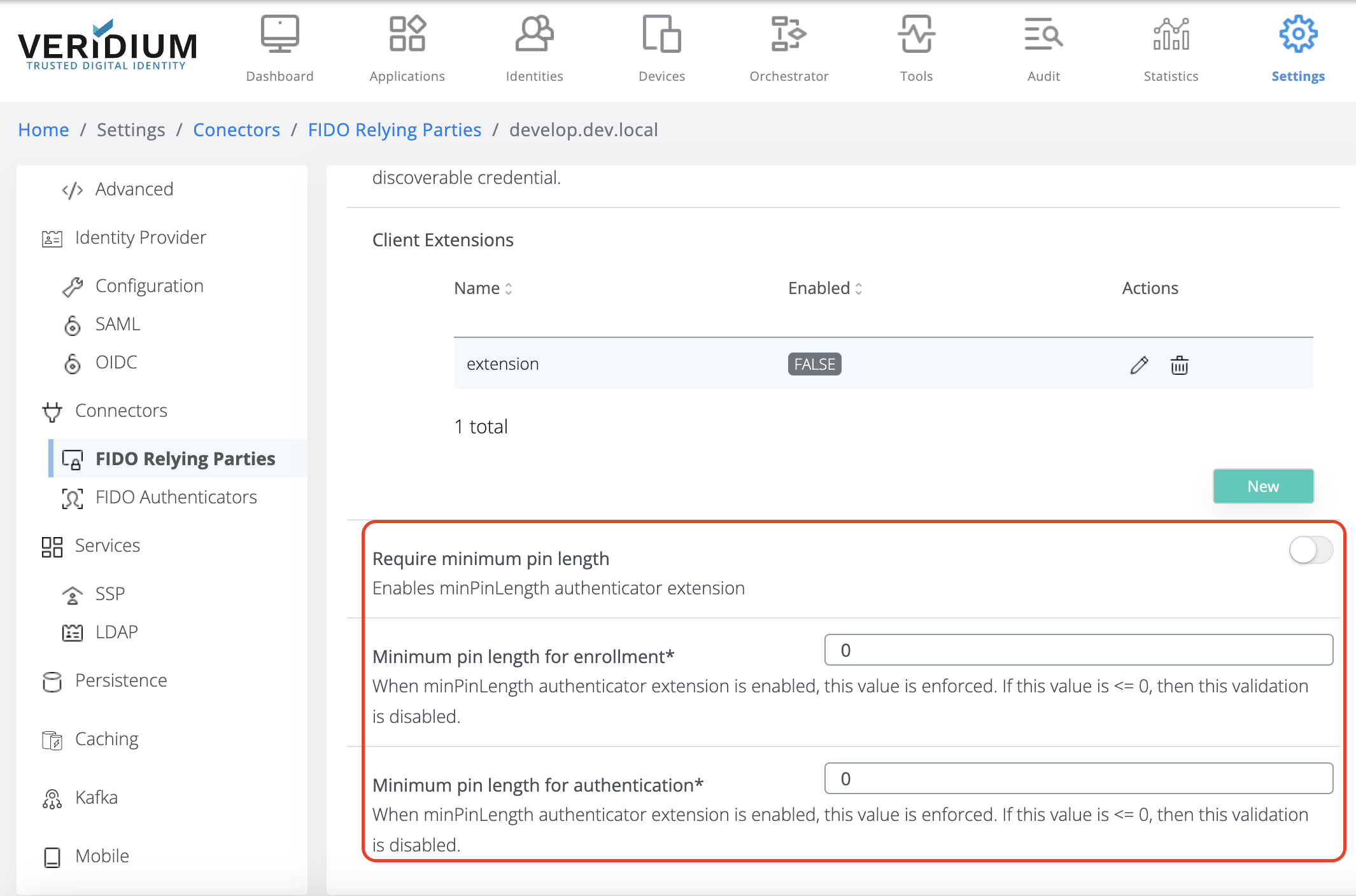
Step 3
Configure as indicated below:
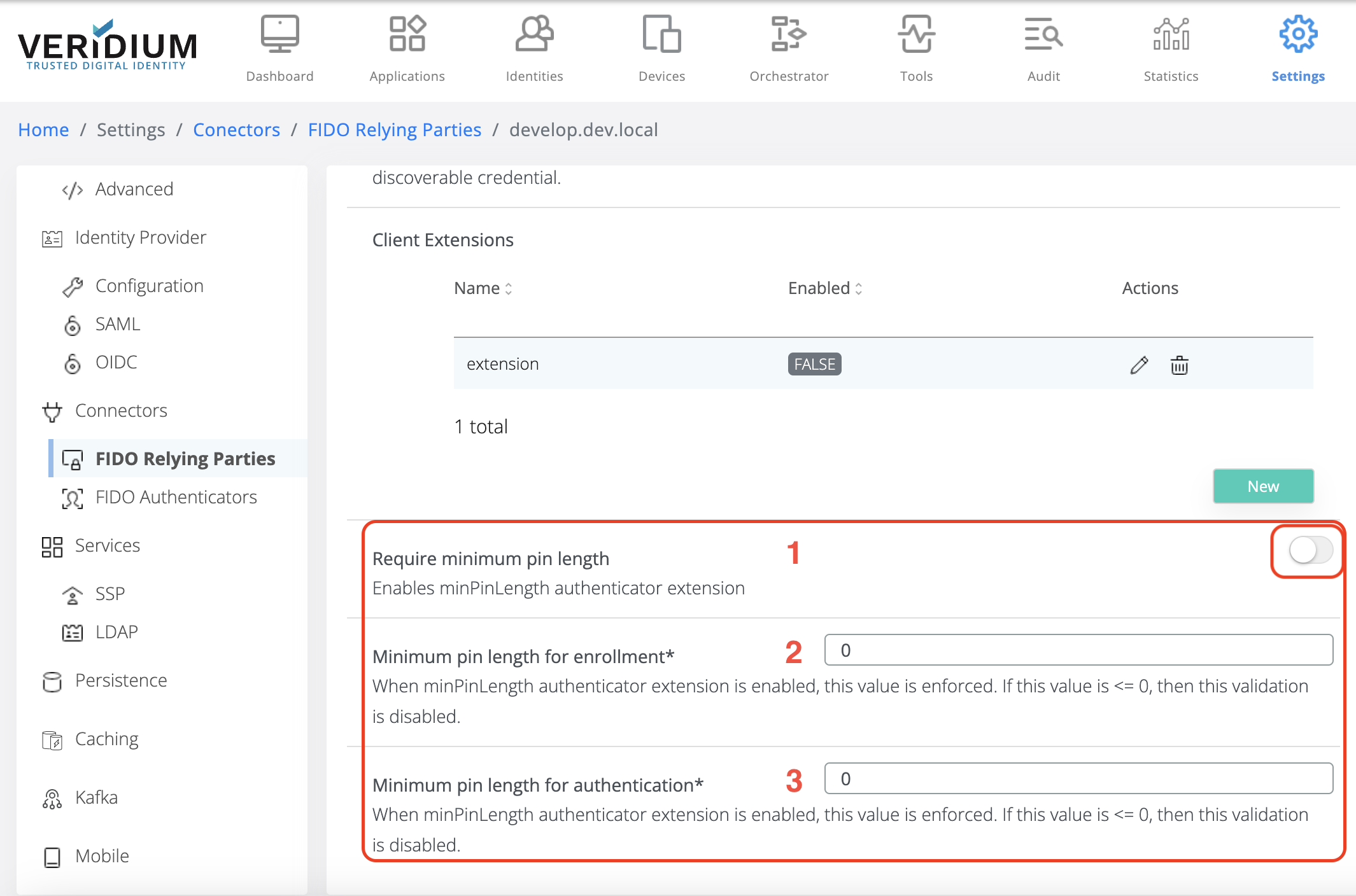
Enable/disable minimum PIN length validation. This validation can be enabled/disabled by checking/unchecking the flag indicated below.
If it is enabled, then the following values are enforced at enrollment and authentication, respectively.
If the extension is disabled, then the validation is skipped, regardless of the values set for the following fields.
Minimum PIN length value for enrollment.
If this value is strictly positive, greater than 0 (zero), then this value is enforced at FIDO Enrollment, minPinLength value set on the device should be greater or equal to this value. If the device minPinLength is less than this value, then the enrollment fails with an error.
If this value is 0 (zero) or negative, then the validation is skipped for enrollment.
Minimum PIN length for authentication.
If this value is strictly positive, greater than 0 (zero), then this value is enforced at FIDO Authentication, minPinLength value set on the device should be greater or equal to this value. If the device minPinLength is less than this value, then the authentication fails.
If this value is 0 (zero) or negative, then the validation is skipped for authentication.
Device setup
For this functionality to work, FIDO devices need to be instructed to share the minimum PIN length configuration with the desired relying party. This is a device specific/vendor specific operation, but for example, for Yubico Yubikey the following command sets the minimum PIN length to 8 and share this value with Relying Party, given by its ID (e.g: local.veridium-dev.com)
ykman fido access set-min-length 8 -R relyingParty (e.g: ykman fido access set-min-length 8 -R local.veridium-dev.com)
The Relying party ID is available in Veridium Manager interface, in the Relying party details, on top of the page with minimum PIN length details: