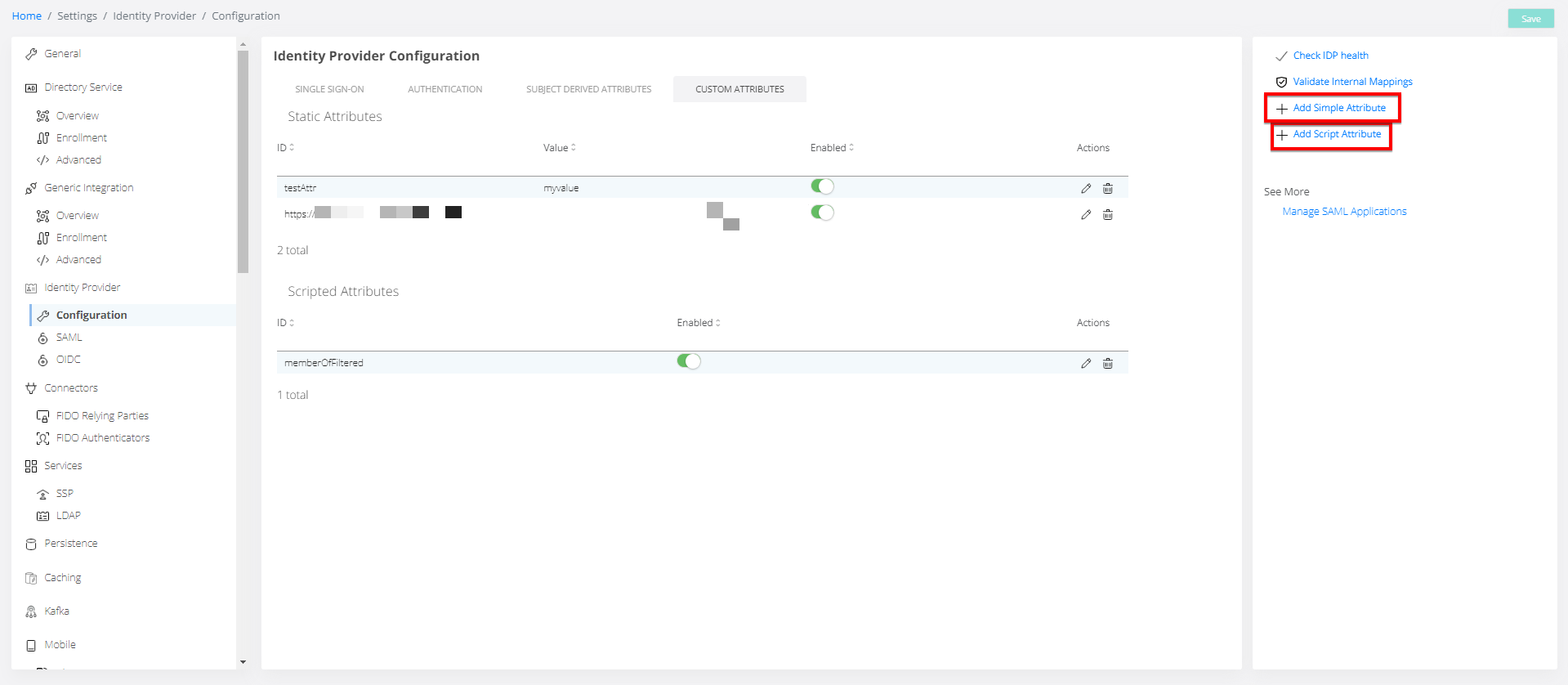
Identity Provider configuration
Single sign-on tab
Name | Basic Description | Default Value |
|---|---|---|
Authentication Default Lifetime | A user's authentication results may be used for implicit SP authentication for as long as this parameter indicates. After this period, the user will be asked to authenticate again. | PT7S |
Authentication Default Timeout | If the last authentication result is not used in SAML responses within this time frame the user will be asked to authenticate again next time it reaches the IdP. | PT7S |
Session Timeout | The idle time for the IdP session. The value must be at least as long as the Authentication Default Lifetime. | PT24h |
Enable Single Logout (SLO) | User Sessions as stored in Cassandra and the user can be logged out everywhere at once | Turned off |
Default Service Provider lifetime* | Controls how long the IdP will store the Service Providers' sessions. In case of Single Logout, this value should be greater than the Service Providers' session lifetime. | PT2h |
Logo file | Custom logo displayed in Shibboleth page |
|
Actions available on the page:
Check IDP health - used to verify the health of the IDP
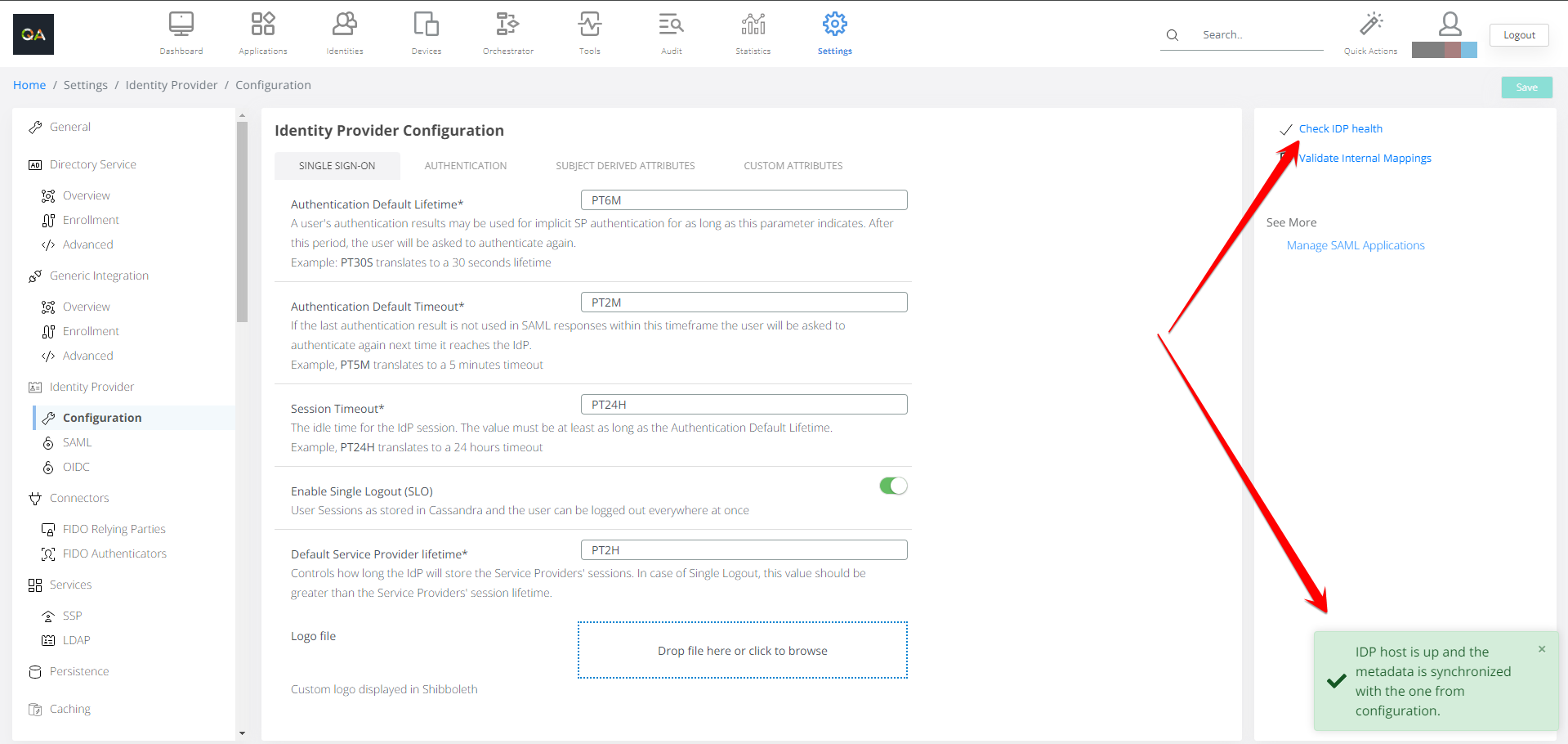
Validate Internal Mappings - used to verify the mapping between attributes
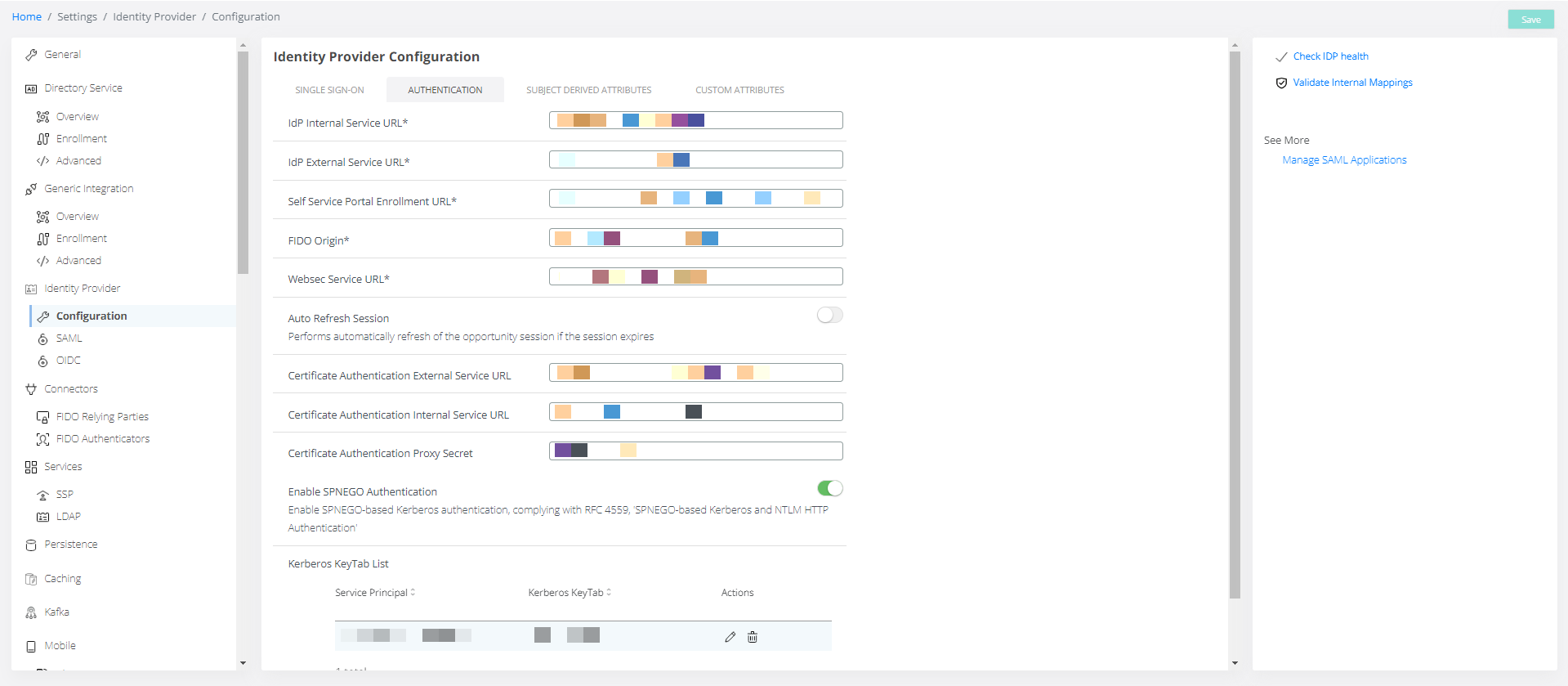
Authentication tab
Name | Basic Description | Default Value |
|---|---|---|
IdP Internal Service URL* | <fqdn>:8945 | |
IdP External Service URL* | <fqdn>:8944 | |
Self Service Portal Enrollment URL* | <fqdn>:9987/ssp/index.html#enrollment | |
FIDO Origin* | <fqdn> | |
Websec Service URL* | <fqdn>/websec | |
Auto Refresh Session | Performs automatically refresh of the opportunity session if the session expires | Turned off |
Certificate Authentication External Service URL | <fqdn>:8946 | |
Certificate Authentication Internal Service URL | <fqdn>:8947 | |
Certificate Authentication Proxy Secret | <secret> | |
Enable SPNEGO Authentication | Enable SPNEGO-based Kerberos authentication, complying with RFC 4559, 'SPNEGO-based Kerberos and NTLM HTTP Authentication' | Turned off |
Kerberos KeyTab List | No value |
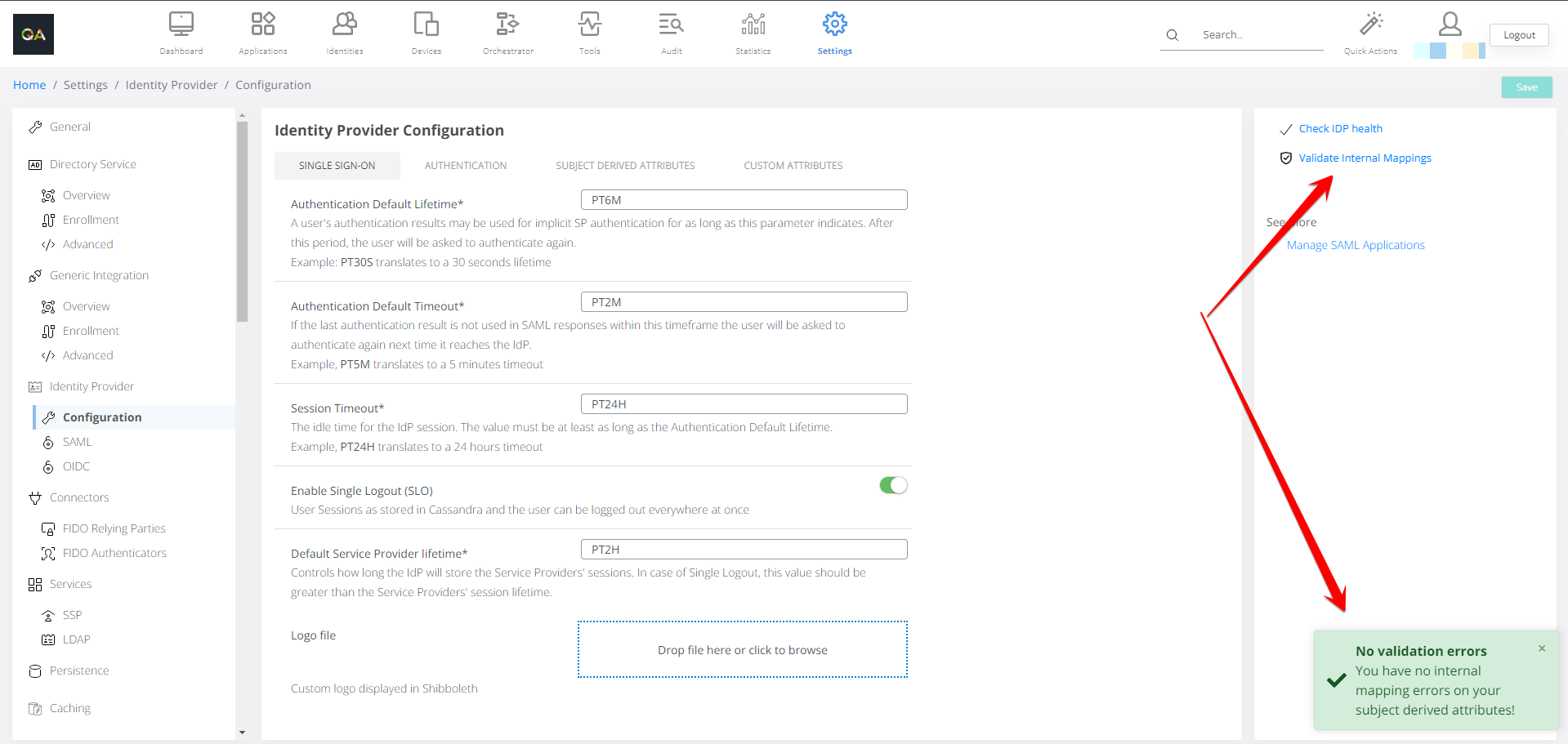
Actions available on the page:
Check IDP health - used to verify the health of the IDP
Validate Internal Mappings - used to verify the mapping between attributes
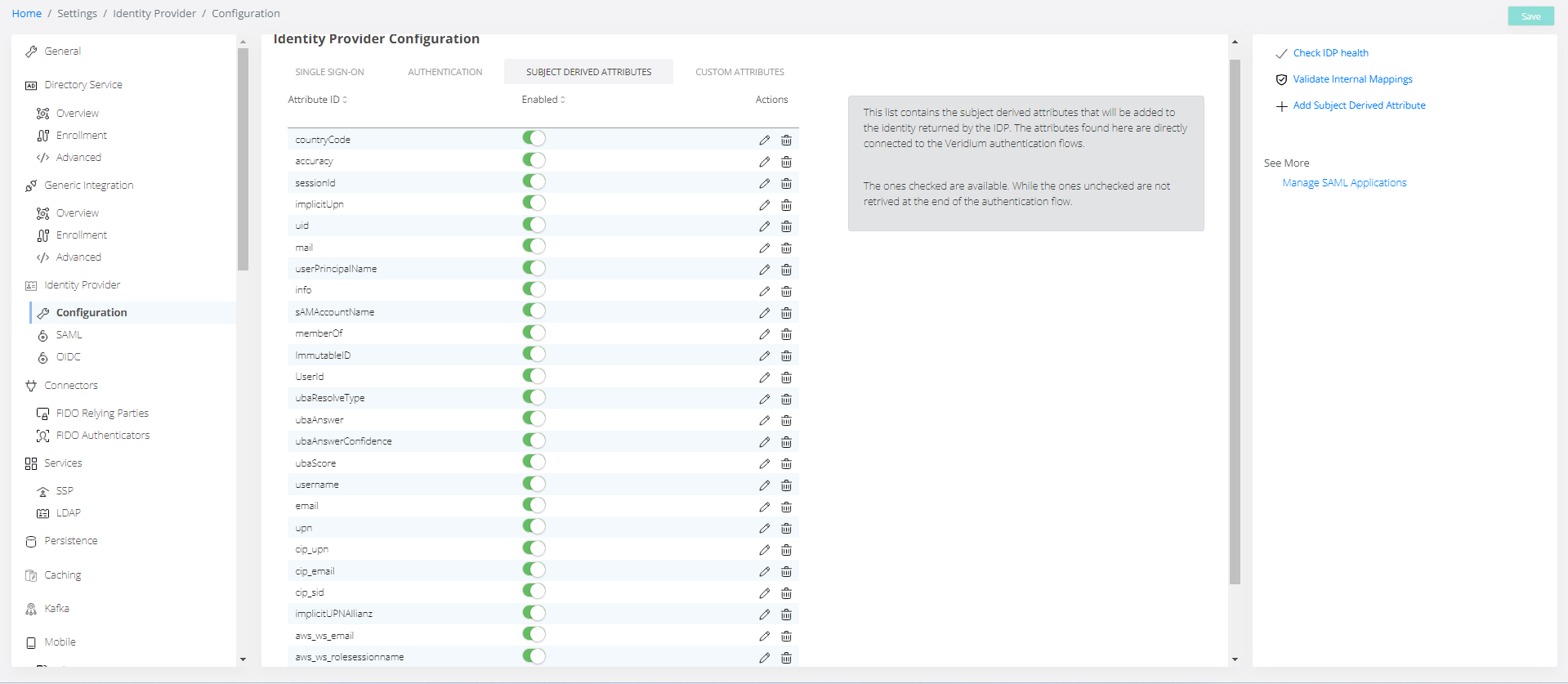
Subject derived attributes tab
This list contains the subject derived attributes that will be added to the identity returned by the IDP. The attributes found here are directly connected to the Veridium authentication flows.
The ones checked are available. While the ones unchecked are not retrived at the end of the authentication flow.
One can Edit, Delete an existing attribute or add a new attribute.
Actions available on the page:
Check IDP health - used to verify the health of the IDP
Validate Internal Mappings - used to verify the mapping between attributes
Add subject derived attribute
Custom attributes tab
Actions available on the page:
Check IDP health - used to verify the health of the IDP
Validate Internal Mappings - used to verify the mapping between attributes
Add simple attribute
Add script attribute