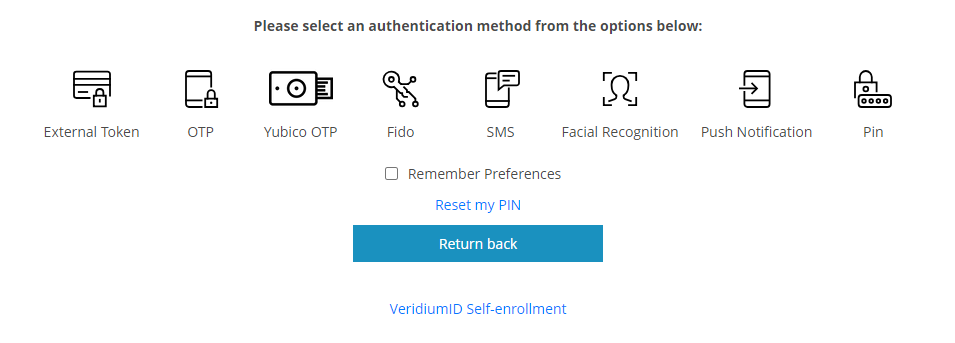
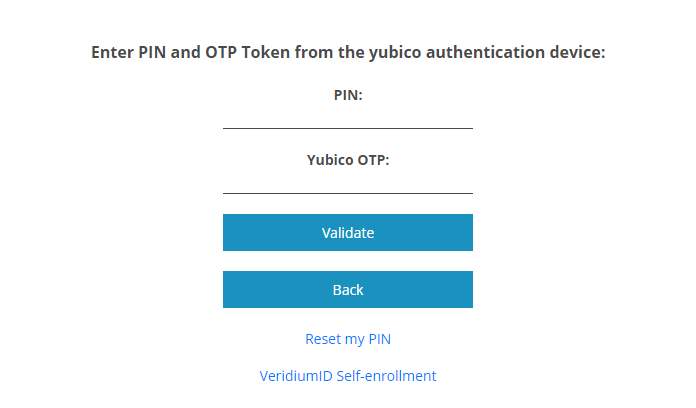
OTP authentication method
There are several ways to enroll and authenticate using OTP tokens in the Veridium server allowing various integration scenarios. There are 5 different devices that can be used for generating OTP codes:
TOTP - enrolled during Veridium Authenticator (Mobile Veridium SDK) identity enrollment
TOTP Desktop - standalone desktop application that only provides support for TOTP enrollment.
OATH-OTP
OTP application - use a 3rd party application to generate OTP codes (e.g. Microsoft Authenticator, Google Authenticator)
OTP Hardware token - use a dedicate hardware device
Yubico OTP - Yubico proprietary OTP implementation
To ensure strong factor authentication method, it’s recommended that all the OTP authentication methods are used in conjunction with Veridium PIN during enrollment and authentication.
For special cases, a switch to disable Veridium PIN is available for each of the OTP authentication methods.
This switch can be configured in Veridium Manager / Orchestrator / Authentication / Commands / [cmd_yubico_otp, cmd_otp, cmd_sms_browser, cmd_totp_browser] - "usePin": false
Default value for “usePin” parameter is “true” and the default behavior is not affected, PIN is still mandatory in default orchestration commands.
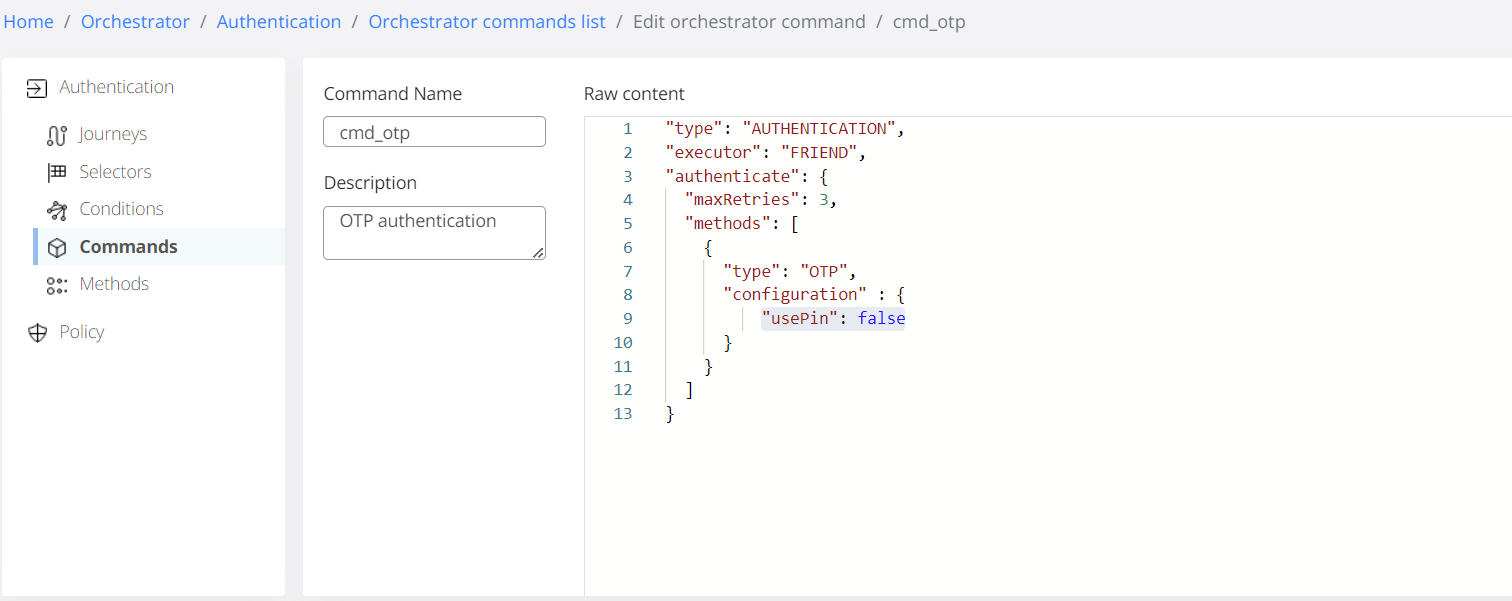
In Veridium Server 3.2.4 all the OATH-OTP protocol authentication methods - TOTP, TOTP Desktop, OTP application, OTP Hardware token - were merged during the authentication under a single OTP entry to provide a simple UX for a user that may use multiple OTP authentication methods.
Server side sends: | New Exploiter Clients (> 3.2.4) | Legacy Exploiter Device clients (<v3.2.4) |
|---|---|---|
TOTP only | Display OTP, uses TOTP authentication method | Displays "TOTP" |
TOTP_DESKTOP only | Display OTP, uses TOTP_DESKTOP authentication method | Displays "TOTP_DESKTOP" |
TOTP_DESKTOP+TOTP | Display OTP, uses any TOTP_DESKTOP or TOTP authentication method | Displays "TOTP_DESKTOP" and “TOTP“ |
OTP only | Display OTP, uses OTP authentication method | Displays nothing (does not interpret the command) |
TOTP+OTP | Display OTP, uses OTP authentication method | Displays "TOTP" |
TOTP_DESKTOP+OTP | Display OTP, uses OTP authentication method | Displays "TOTP_DESKTOP" |
TOTP+TOTP_DESKTOP+OTP | Display OTP, uses OTP authentication method | Displays "TOTP" and "TOTP_DESKTOP" |
TOTP
Introduced in version 2.0, it allows the user to enroll a TOTP secret during identity enrollment on the Veridium Authenticator. Uses OATH-TOTP (RFC-6238) to generate the OTP codes. The secret key is stored secured on the mobile device and service.
Configure Options
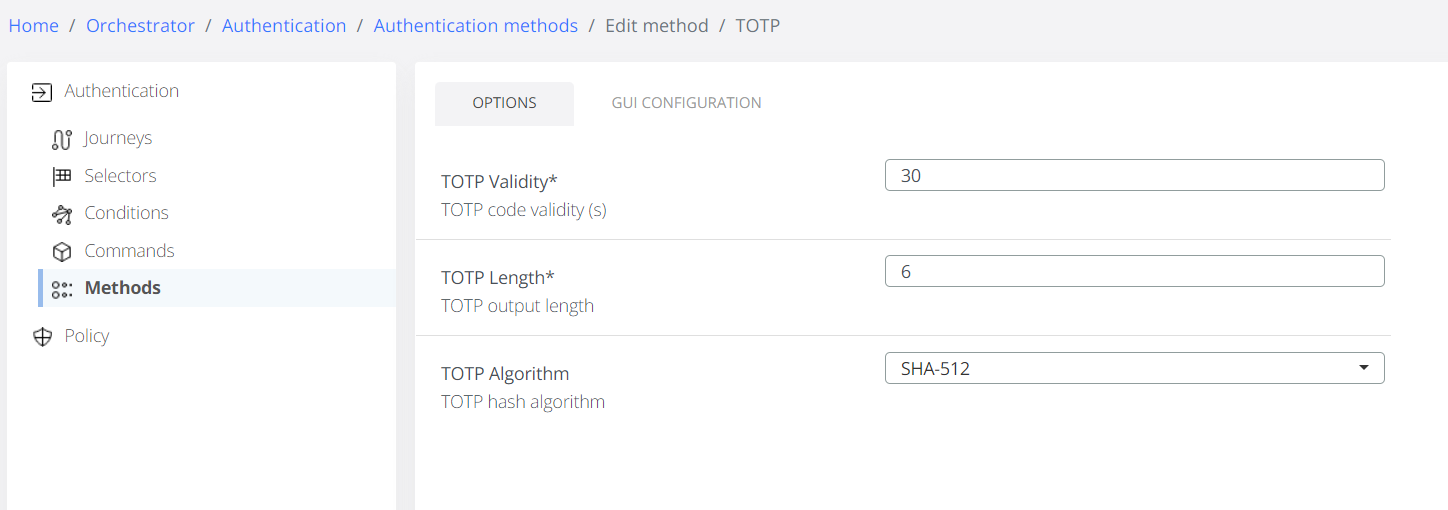
TOTP Validity - number of seconds a TOTP is valid.
TOTP Length - the number of digits in the generated OTP code.
TOTP Algorithm - the algorithm used to generate OTP code.
An user may have multiple TOTP authentication methods enrolled and the limit is controlled by the maximum number of mobile devices permitted. This can be configured for version 3.2.4 in General Settings / Device Limitation Per Profile / Max Mobile Phones Per Profile Key, or via file editing in Advanced / config.json / "maxMobilePhonesPerProfileKey"
Administration
As admin the configuration for the enrollment and authentication are possible in the Veridium Manager / Orchestrator / Authentication Methods / TOTP.
TOTP Desktop
This is a standalone desktop application that allows the user to enroll an OTP secret and use during authentication. The application uses Self Service Portal to enroll the device.
Administration
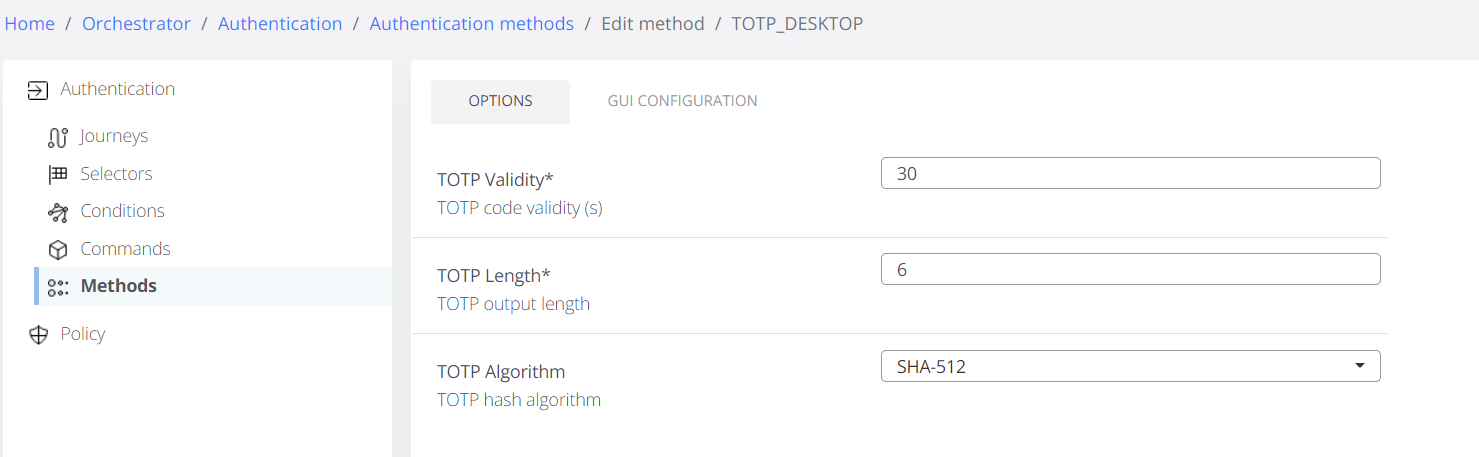
As admin the configuration for the enrollment and authentication are possible in the Veridium Manager / Orchestrator / Authentication Methods / TOTP Desktop
Configure Options
TOTP Validity - number of seconds a TOTP is valid.
TOTP Length - the number of digits in the generated OTP code.
TOTP Algorithm - the algorithm used to generate OTP code.
OATH-OTP
Introduced in version 3.2.4
The OATH-OTP authentication methods allows enrollment and authentication using software or hardware tokens. Since the enrollment and provisioning is different for these devices, the enrollment procedure is different. Both hardware and software allows usage of either OTP standards:
TOTP: Time-Based One-Time Password Algorithm (RFC 6238)
OTP Application
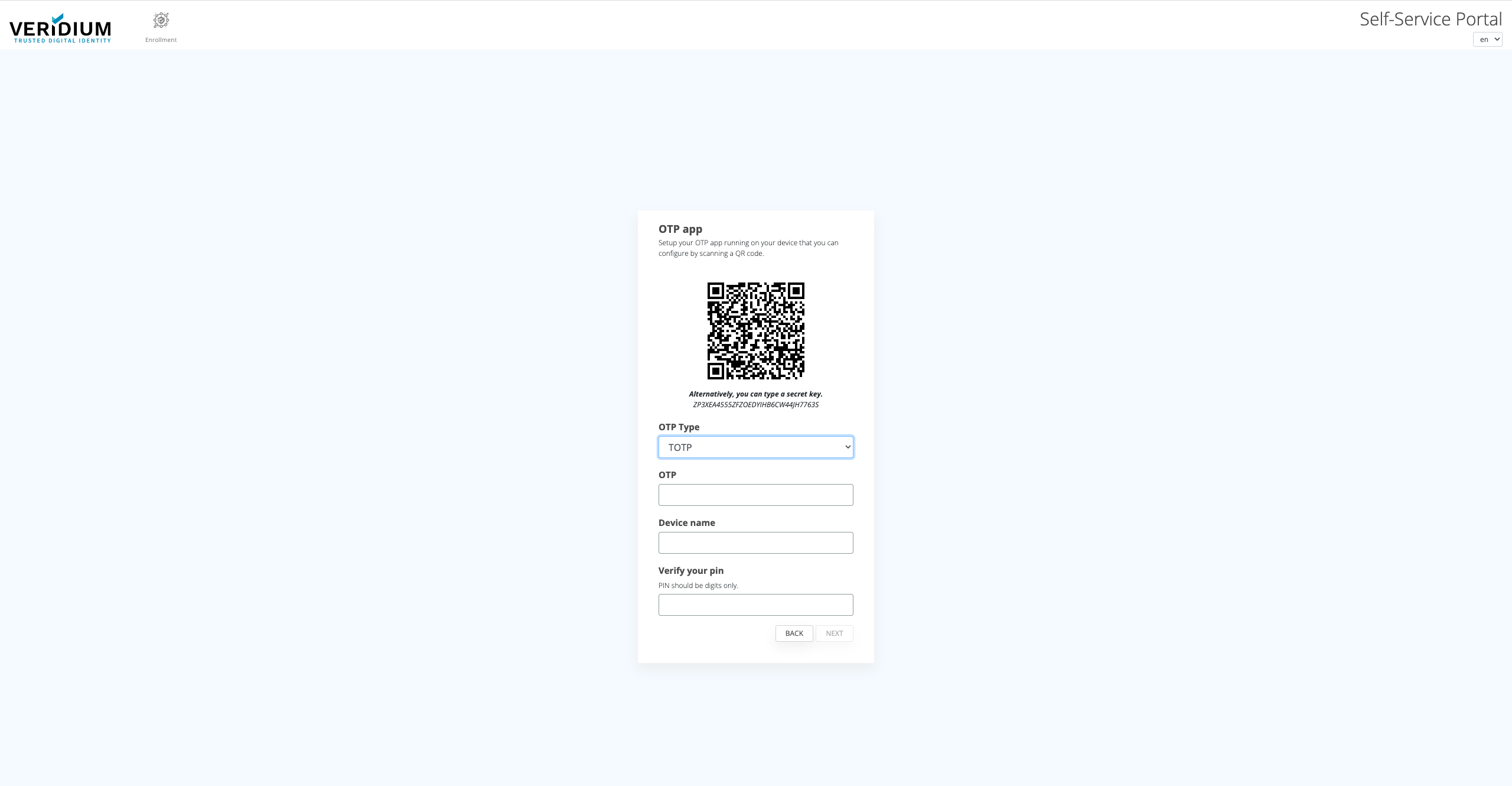
An user may enroll an OTP application through the Self Service Portal using the option configured by the administrator. May scan the QR or use the displayed secret as manual input if the application supports it.
An user may only have 1 OTP application authentication method enrolled. If a new OTP application is enrolled, the existing one will be overwritten.
Some of the 3rd party OTP application allows synchronization between multiple devices - i.e. Google Authenticator. Please consult your authenticator’s documentation for further details.
Administration
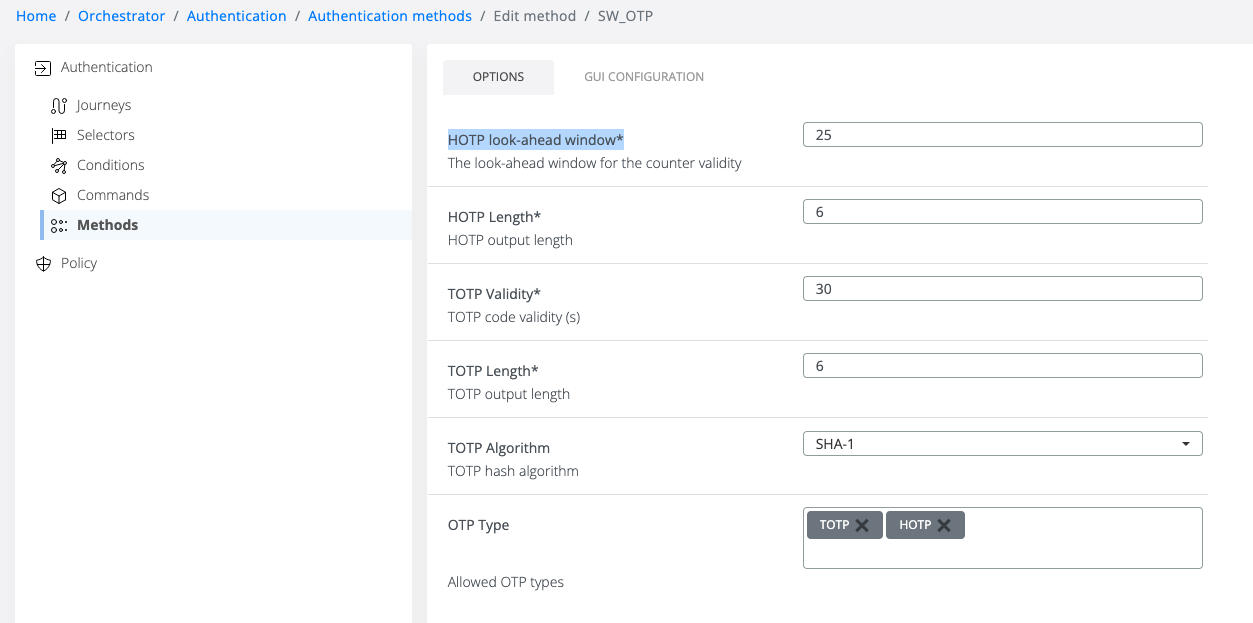
As admin the configuration for the enrollment and authentication are possible in the Veridium Manager / Orchestrator / Authentication Methods / SW_OTP.
Configure Options
OTP Type - Allowed OTP types for enrollment
HOTP Options
HOTP look-ahead window - maximum number of out-of-sync and accepted codes by the server before re-enrollment is necessary.
HOTP Length - the number of digits in the generated OTP code.
TOTP Options
TOTP Validity - number of seconds a TOTP is valid.
TOTP Length - the number of digits in the generated OTP code.
TOTP Algorithm - the algorithm used to generate OTP code. (SHA-1 is used by most applications)
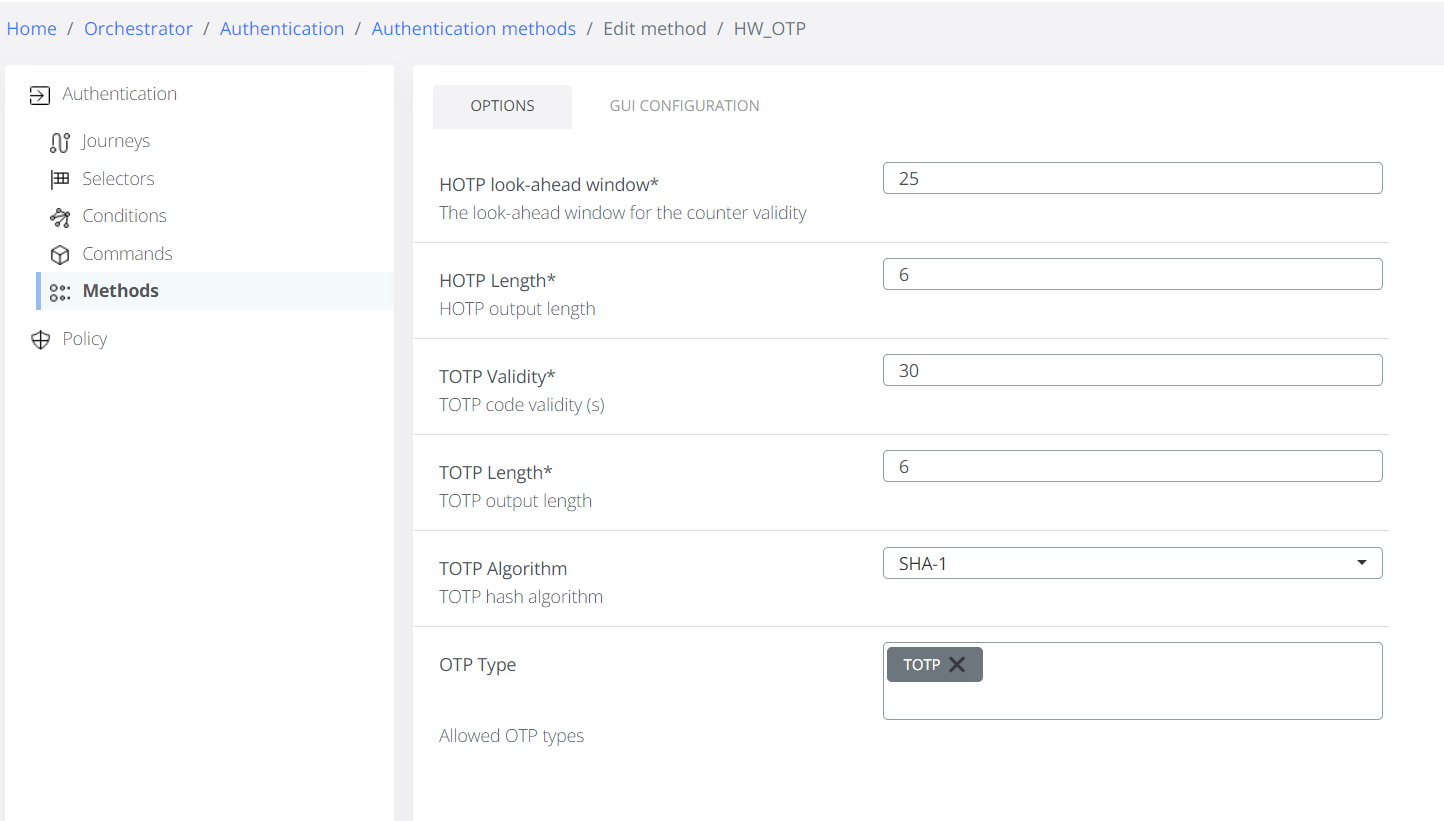
OTP Hardware Token
The OTP Hardware Tokens are usually provided to the end users already configured. Therefore the Veridium Manager provides support for Hardware Device token management in Devices / Hardware auth devices management.
Administration
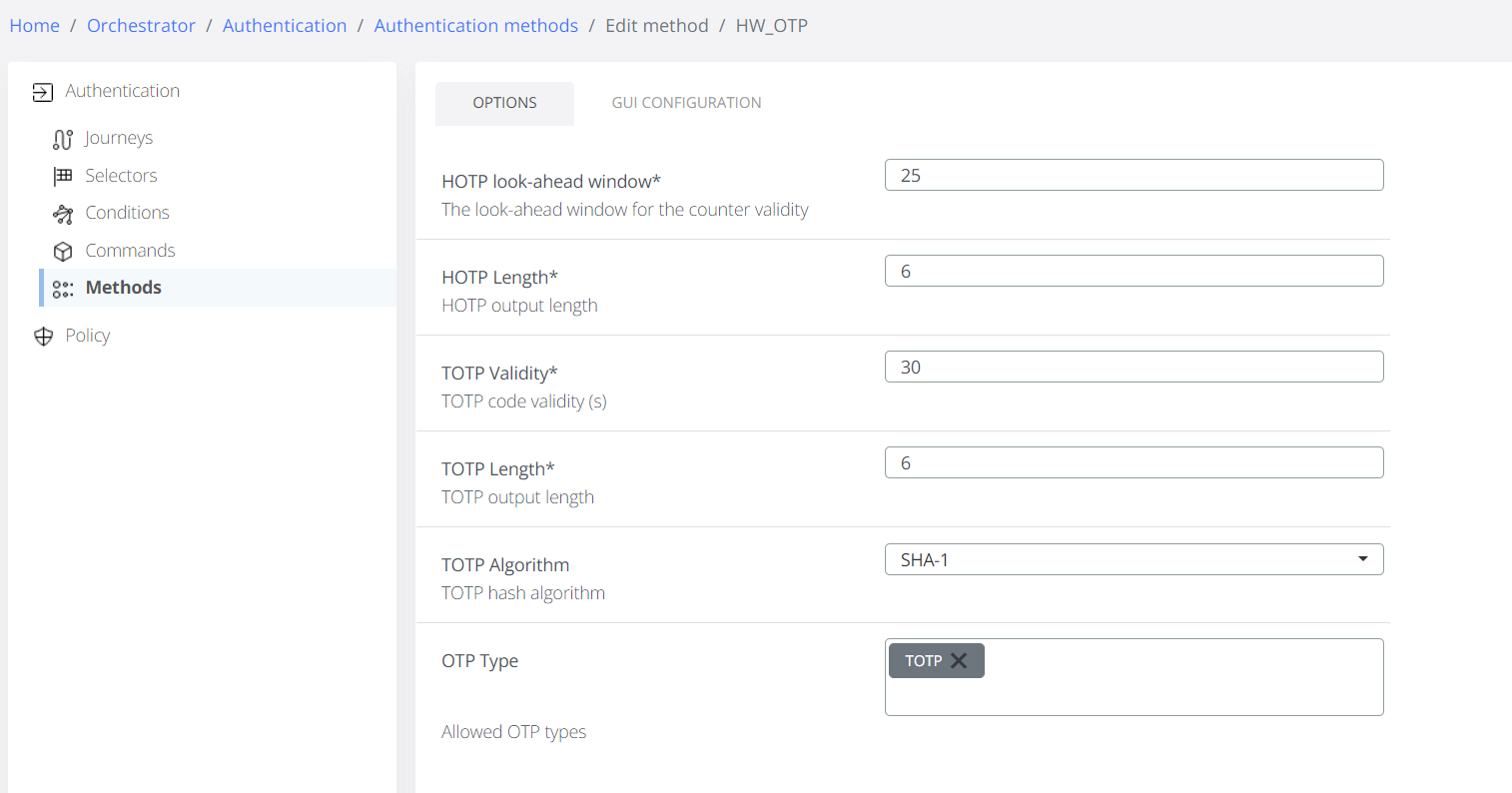
As admin the configuration for the enrollment and authentication are possible in the Veridium Manager / Orchestrator / Authentication Methods / HW_OTP.
Configure Options
OTP Type - Allowed OTP types for enrollment
HOTP Options
HOTP look-ahead window - maximum number of out-of-sync and accepted codes by the server before re-enrollment is necessary.
HOTP Length - the number of digits in the generated OTP code.
TOTP Options
TOTP Validity - number of seconds a TOTP is valid.
TOTP Length - the number of digits in the generated OTP code.
TOTP Algorithm - the algorithm used to generate OTP code.
Yubico OTP
Introduced in version 3.2.4
Veridium enabled support for enrollment and authentication using Yubico OTP proprietary authentication algorithm - https://www.yubico.com/resources/glossary/yubico-otp/. The validation of the OTP code is implemented in the VeridiumID server and YubiCloud is not supported at the moment.
The Yubico OTP are usually provided to the end users already configured. Therefore the Veridium Manager provides support for Hardware Device token management in Devices / Hardware auth devices management.
Administration
As admin the configuration for the enrollment and authentication are possible in the Veridium Manager / Orchestrator / Authentication Methods / HW_OTP.
Manage Hardware OTP Tokens
Hardware OTP Token setup and provisioning is mandatory to allow the user to enroll from Devices → Manage Hardware Auth Devices. An admin is allowed to add, view and delete the Hardware authentication devices.
Hardware OTP tokens setup is required before an admin can provision it to Veridium Platform. Depending on the token type informations like Serial Number, Secret Key and Model are required. These steps are detailed below in Appendix A.
Adding new devices
Navigate to Devices / Hardware auth devices management.
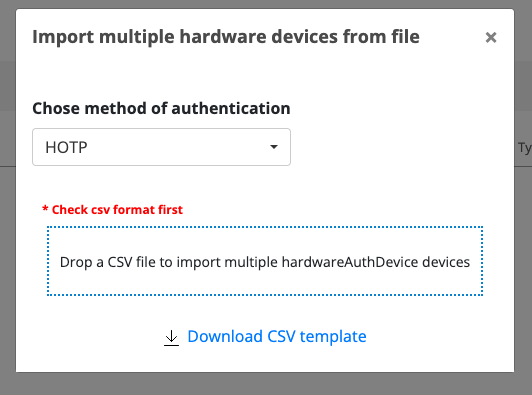
Fill in the details for the desired OTP Token or use the CSV Bulk import. Use the template available for download for each authentication method to see the required fields for a successful import.
In case of an importing error, a template containing suffix “Error_” will be downloaded automatically and inside it the problematic section will be highlighted with a descriptive message.
Appendix A - Enroll and Authenticate with Yubico OATH-OTP
Setup Yubico OATH-OTP device
Install YubiKey Manager application
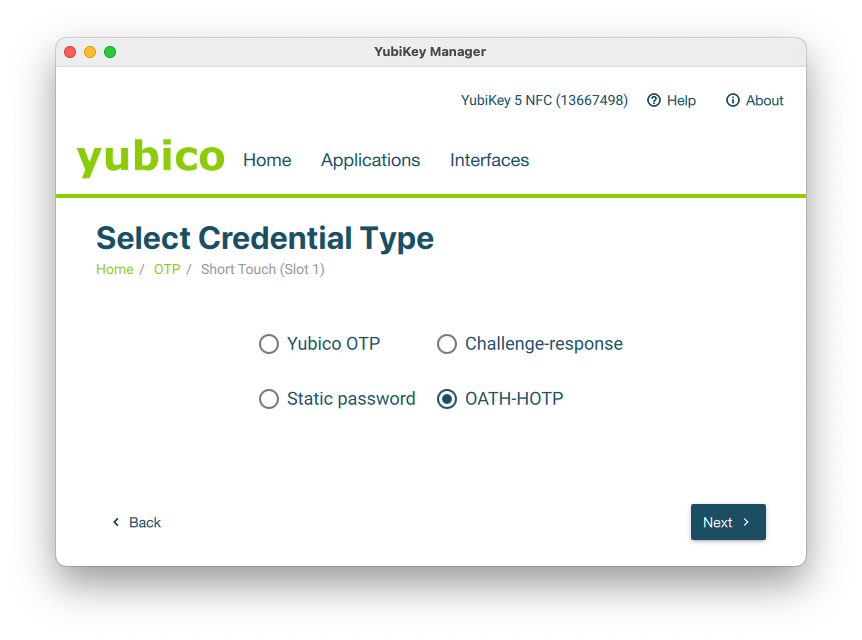
Plug-in your Yubico key and configure any slot with OATH-OTP (Applications / OTP / OATH-OTP)
Generate a base32 secret key and save the configuration. Remember to save the secret key, as it will be used in the Veridium Manager / Devices / Manage Hardware auth devices.
Select the number of digits. This have to be the same as Veridium Manager / Orchestrator / Methods / HW_OTP / HTOP - HOTP Length)
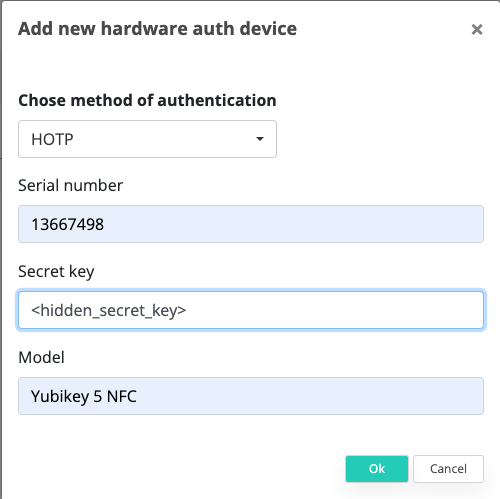
Add the device in Veridium Manager
Navigate to Veridium Manager / Devices / Manager Hardware auth devices
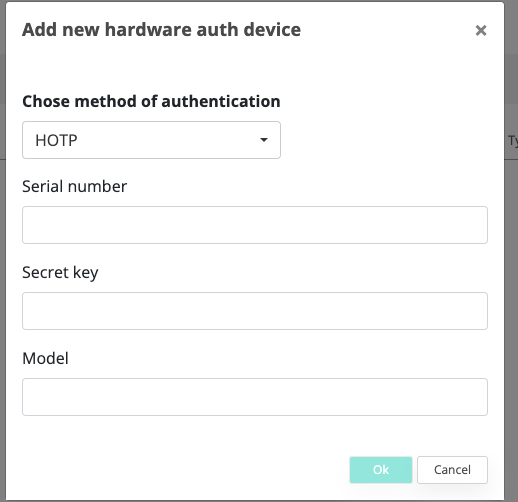
Add new hardware auth device
Select HOTP Type
Fill the serial number of the Yubico Key (e.g. 13667498)
Fill the secret key configured above in the Yubico Key Manager
Fill the device model (e.g. Yubikey 5 NFC)
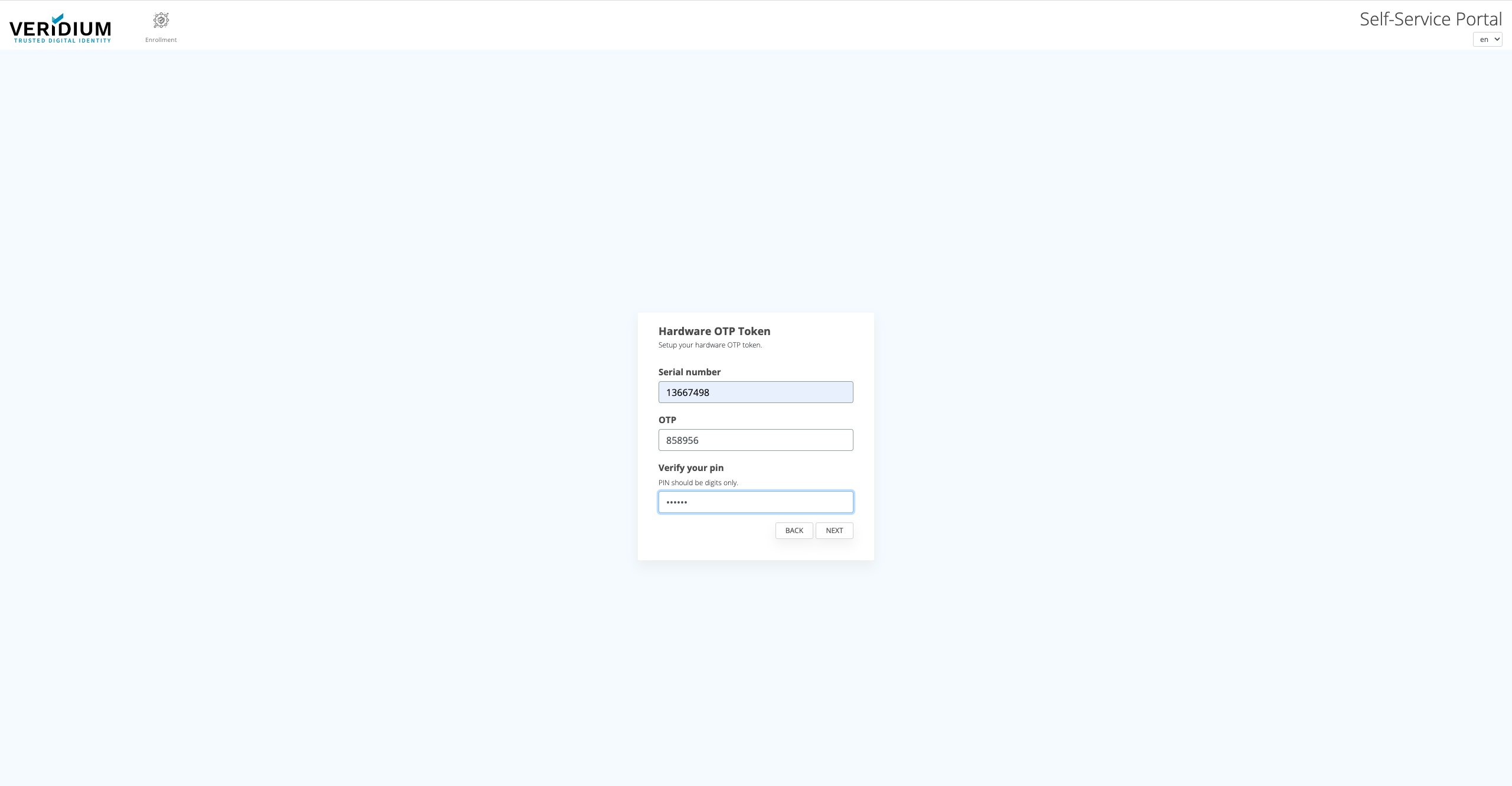
After the device was added by the admin, an user can bind the device to his account by enrolling it.
Enroll in the Self Service Portal
After a successful enrolment, the key will appear in Veridium Manager - Devices - Manager Hardware table associated to the account.
Notes:
You can use this script to generate the base32 secret key on a linux based device.
LC_ALL=C tr -dc 'A-Z2-7' </dev/urandom | head -c 32; echoAppendix B - Enroll and Authenticate with Yubico OTP
Setup Yubico OTP device
Install YubiKey Manager application
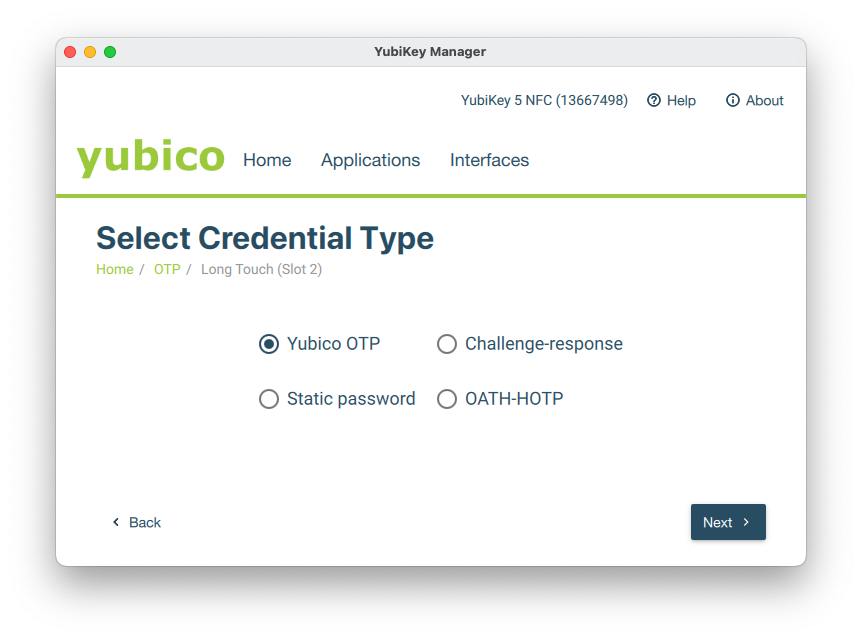
Plug-in your Yubico key and configure any slot with Yubico OTP (Applications / OTP / Yubico OTP)
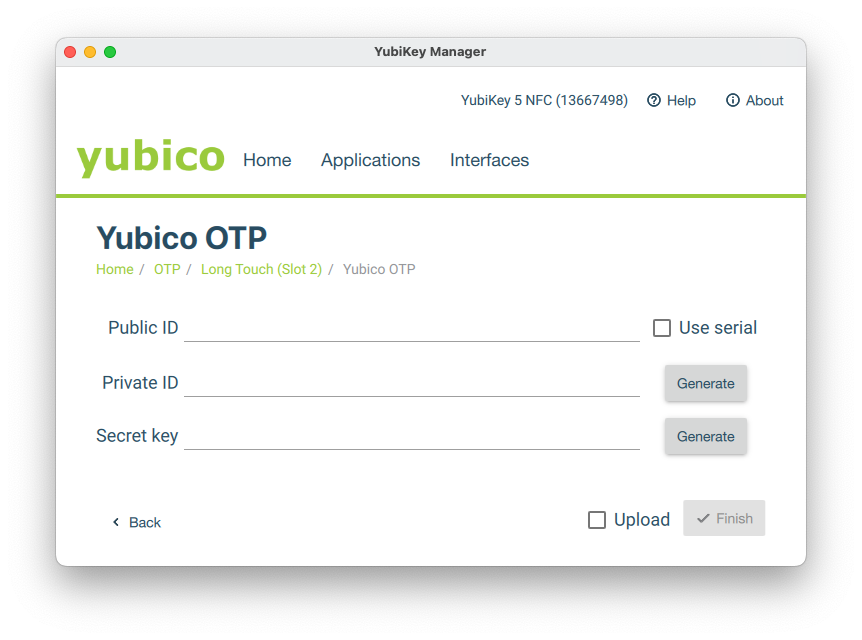
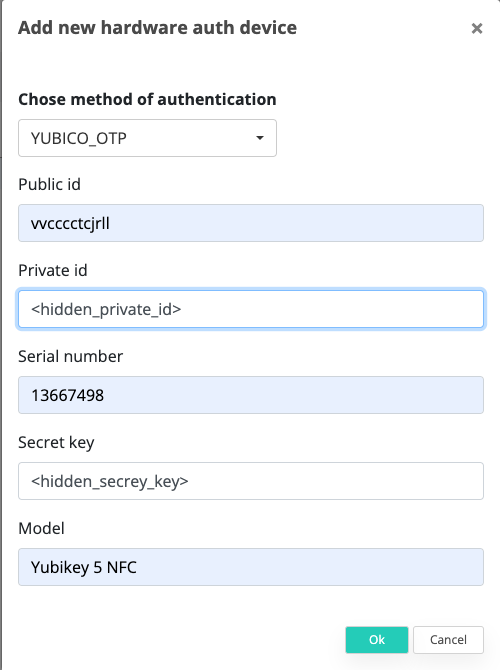
Fill in the details Public ID, Private Key and Secret Key (save them because they are required for provisioning in the Veridium Manager).
Make sure Upload is not checked since Veridium doesn’t use YubiCloud to verify the OTPs.
Add the device in Veridium Manager
Navigate to Veridium Manager / Devices / Manager Hardware auth devices
Add new hardware auth device
Select Yubico OTP Type
Fill the serial number of the Yubico Key (e.g. 13667498)
Fill the Public Id configured above in the Yubico Key Manager
Fill the Private Id configured above in the Yubico Key Manager
Fill the the secret key configured above in the Yubico Key Manager
Fill the device model (e.g. Yubikey 5 NFC)
Enroll in the Self Service Portal
After a successful enrolment, the key will appear in Veridium Manager / Devices / Manager Hardware table associated to the account.
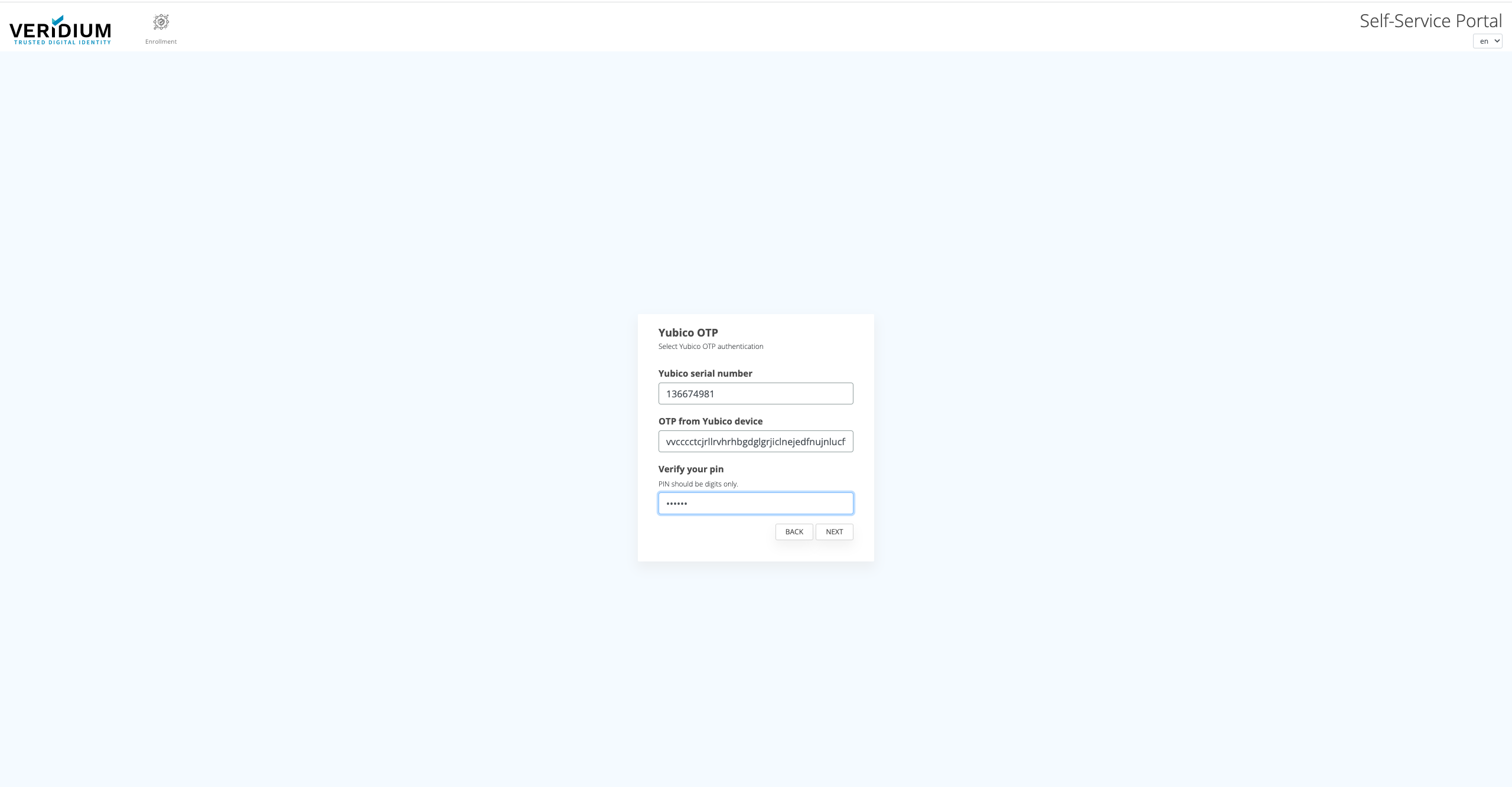
Authentication
After the desired OTP method has been enrolled, using it for authentication is integrated seamless in the VeridiumID flows, in accordance with Policies and the journeys configured in Orchestrator.
For using HOTP key, choose OTP authentication method.
For using OTP key, choose Yubico OTP authentication method.