MSCHAPv2
Starting public release 3.4 MSCHAPv2 protocol was integrated in the VeridiumID Freeradius module. The module enables support for using PUSH or OTP authentication methods.
Compared to the other protocols (chap or pap), in order to activate PUSH authentication method, the provided user input should be push.
Modes supported:
MSCHAPv2
EAP-MSCHAPv2
PEAP-MSCHAPv2
Configuration
MSCHAP MPPE Policy
The MPPE policy may be configured from the Veridium Manager:
Navigate to Settings / Advanced / freeradiusconfig.json
Update the
mschap_mppe_policyvalue that uses a bitmask as follows:The 1st bit controls the MPPE key creation
The 2nd bit controls the Encryption policy (required or optional)
The 3rd bit controls the Encryption methods (allow 128-bit or 56-bit encryption using RC4)
mschap_mppe_policy | |
|---|---|
0x000 | No MS-MPPE-Recv-Key/MS-MPPE-Send-Key are created |
0x001 | MS-MPPE-Recv-Key/MS-MPPE-Send-Key keys are created and the encryption is optional |
0x011 | MS-MPPE-Recv-Key/MS-MPPE-Send-Key keys are created and the encryption is required. |
0x111 | Enforces encryption using 128-bit, otherwise 56-bit encryption is also allowed |
https://www.rfc-editor.org/rfc/rfc2548
MSCHAPv2
This method is configured out of the box starting version 3.4.
The configuration steps listed bellow should only be followed to validate or create a custom configuration.
Edit the
/opt/veridiumid/freeradius/etc/raddb/sites-enabled/defaultRemove the mschap from
authenticateandauthorizesections.Update the
Auth-Type MSCHAPblock with:CODEAuth-Type MSCHAP { rest_orchestrator }
EAP-MSCHAPv2
The steps from MSCHAPv2 configuration are required as prerequisites. Follow the next steps aftwerwards:
Edit
/opt/veridiumid/freeradius/etc/raddb/mods-enabled/eapand updateeap.default_eap_typetomschapv2.CODEeap { ... default_eap_type = mschapv2 ... }
PEAP-MSCHAPV2
This method is configured out of the box starting version 3.4, and only certificates in /opt/veridiumid/freeradius/etc/raddb/certs should be updated with valid CA and valid Radius Server certificate.
The steps from MSCHAPv2 configuration are required as prerequisites. Follow the next steps afterwards:
Edit
/opt/veridiumid/freeradius/etc/raddb/mods-enabled/eapand updateeap.default_eap_typetopeapandeap.peap.default_eap_typetomschapv2.CODEeap { ... default_eap_type = peap ... peap { ... default_eap_type = mschapv2 ... } }Make sure the certificates are properly configured in
/opt/veridiumid/freeradius/etc/raddb/certs/. The default TLS configuration is managed in the/opt/veridiuid/freeradius/etc/raddb/mods-enabled/eapin thetls-config tls-commonblock.
Optional for specific veridium customers
/opt/veridiuid/freeradius/etc/raddb/mods-enabled/default introduce attribute filtre based on groups
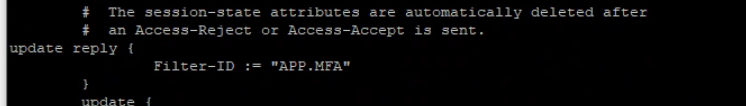
example for group filter https://deangrant.me/2014/02/07/freeradius-forward-filter-id-as-a-variable-to-post-authentication/
Radius Authentication method - Orchestration Matrix
The main difference between the other Radius authentication protocols, on MSCHAPv2 we can no longer relay on the password length or format.
Authentication Method | Input expected | Behavior |
|---|---|---|
none | N/A | Authentication refused |
PUSH | “push“ | A push is sent to device and trigger |
PIN + OTP Code | any passphrase distinct from the reserved value (“push“) |
|
PIN + TOTP
PIN validation requires unsafe storage to be enabled for MSCHAP login validation when PIN + OTP authentication method is used. The PIN is stored in the database
Navigate to Orchestrator / Authentication / Methods
Edit PIN authentication method
Enable “Allow Unsafe Storage'
Enrolled users must reset PIN from Self Service Portal or Mobile Application to activate this feature on their identity.
