On-prem deployment using VeridiumInstaller (RHEL8 - 9.5.14)
The following procedure will describe how to deploy VeridiumID on RedHat 8 using the VeridiumInstaller.
1) Pre-requirements
1.1) OS level requirements
All nodes need to have firewall stoped : run with sudo : systemctl stop firewalld
All nodes used in the deployment procedure will need to have the same user name that needs to:
Have SSH connectivity to all nodes using SSH keys
## generate key (can be generated on all servers)
ssh-keygen
## take the key (id_rsa.pub) from on server, from where the installation will take place, and put it on all other servers (including himself) in .ssh/authorized_keysSudo permissions (at least until the end of the deployment)
1.2) Domain certificate
During the deployment a domain certificate will need to be used, either a wildcard ( *.client_domain.com) or one for the specific FQDN on which the deployment will be available from outside the network ( for example: veridium.client_domain.com).
The certificate must be either in PKCS12 format of PEM format (public certificate and private key). The certificate must contain the full chain of certification authorities within it.
In case of not having a certificate we provide a script that will generate a self-signed certificate to be used during the deployment (see step 2.3.1).
1.3) Pre-required RPMs
The following list of packages must be installed from official repositories on all nodes in order to be able to use VeridiumID, the following command can be run as root or an username with sudo:
sudo yum -y install vim apr-devel openssl-devel libstdc++-devel curl unzip wget zlib zlib-devel nc openssh-clients perl rsync chrony python39 python39-pip net-tools dialog jq rng-tools tmuxIf VeridiumID release 3.5.x or older, install Java 8, using the following command as root or an username with sudo:
sudo yum -y install java-1.8.0-openjdkIf VeridiumID release 3.6.x or newer, install Java 11, using the following command as root or an username with sudo:
sudo yum -y install java-11-openjdkOn RedHat to activate the official repositories, the nodes will need to subscribe. Please use the following command as root:
sudo subscription-manager register --username <username> --password <password> --auto-attachIn case of there being multiple python 3 versions installed on the node ( the command python3 --version does not respond with Python 3.9.X ), use the alternatives command as root user to change it to python 3.9.x:
alternatives --config python3
2) Deployment steps
2.1) Getting the VeridiumInstaller archive on the node
Using SCP copy the VeridiumInstaller archive to the home directory of the user previously mentioned on the node from where the installation will be started and unarchive the file.
tar xvf veridium-installer-rhel8-9.5.14.tar.gz2.2) Run Pre-requirements checks, to check if components are installed
Run the script with the user that created the keys. This needs to be executed on one machine.
./check_prereqs_rhel8.sh -r -w IP1,IP2 -p IP3,IP4,IP52.3) Running the pre-reqs script to install required packages
From the current directory run the pre-reqs-rhel8.sh script providing the internal IP addresses of all nodes that will be part of the deployment.
The script can be run in the following ways:
running the script with the list of IP addresses as a parameter:
./pre-reqs-rhel8.sh IP1,IP2,IP3,IP4,IP5
Where the list of IP addresses will be delimitted by commas and no spaces.The pre-reqs-rhel8.sh script will do the following:
check the SSH connectivity from the current node to all nodes provided in the list
install all packages required
install Python 3.9 and all its required modules
install the VeridiumID layout including the veridiumid user (which will be used further in the installation)
configure SSH connectivity and sudo permissions for the veridiumid user (both can be removed after the installation has been completed)
move all installation packages to veridiumid user’s home directory (/home/veridiumid)
check if all nodes have dates synced using an NTP server
Please configure chrony with your local NTP server, so there will be no issues with the time.
sudo vi /etc/chrony.conf
sudo systemctl status chronyd
sudo systemctl enable chronyd; sudo systemctl start chronyd
date
sudo chronyc -a sources
## check also if localzone is defined fine
timedatectl
## also set timedate zone
timedatectl list-timezones | grep Bucharest
## sudo timedatectl set-timezone Europe/Berlin
##Also, if the instalation is done in /u01, the following needs to be executed; this is for specific clients, with different defualt user home.
##sudo semanage fcontext -a -e /home /u01/users
##sudo restorecon -vR /u01/users
2.4) Run the VeridiumInstaller
All further steps will be performed using the veridiumid user and from the user’s home directory (/home/veridiumid).
2.4.1) Optional: Create a self-signed domain certificate
In case of not having a domain certificate (required for the deployment) we provide a script that will generate a self-signed certificate that can be used until one generated from internal or external Certification Authorities will be provided.
From veridiumid user’s home directory run the following script as veridiumid user:
./create_domain_cert.sh -d FQDN -p PASSWORD
Where:
- FQDN will be the domain of the server that will be used for accessing link and API calls, for example: test.client_domain.com
- PASSWORD will be the password of the certificates
After running this script the following files will be generated:
Private Key: /home/veridiumid/certs/privateKey.key
Public certificate: /home/veridiumid/certs/publicCert.crt
PKCS12 certificate: /home/veridiumid/certs/domain.p12
Password file: /home/veridiumid/certs/pass.txtThe generated certificate (either in PKCS12 format of PEM format) will be used in the next steps.
2.4.2) Running the VeridiumInstaller script
Run the following script as veridiumid user to start the configuration of VeridiumID:
./veridium-installer-rhel8.shThis script will start the installation and Configuration of the VeridiumID deployment and guide the user through the installation wizard.
2.4.3) Provide deployment details using the Installation Wizard
When the installation wizard will start the following screen will be seen in the terminal:
Press Enter to proceed.
Select Advanced using the right arrow key and press Enter to continue.
All steps from the Menu will be detailed in the following steps.
2.4.3.1) Set VeridiumID FQDN
When selecting Set VeridiumID FQDN the following screen will be shown:
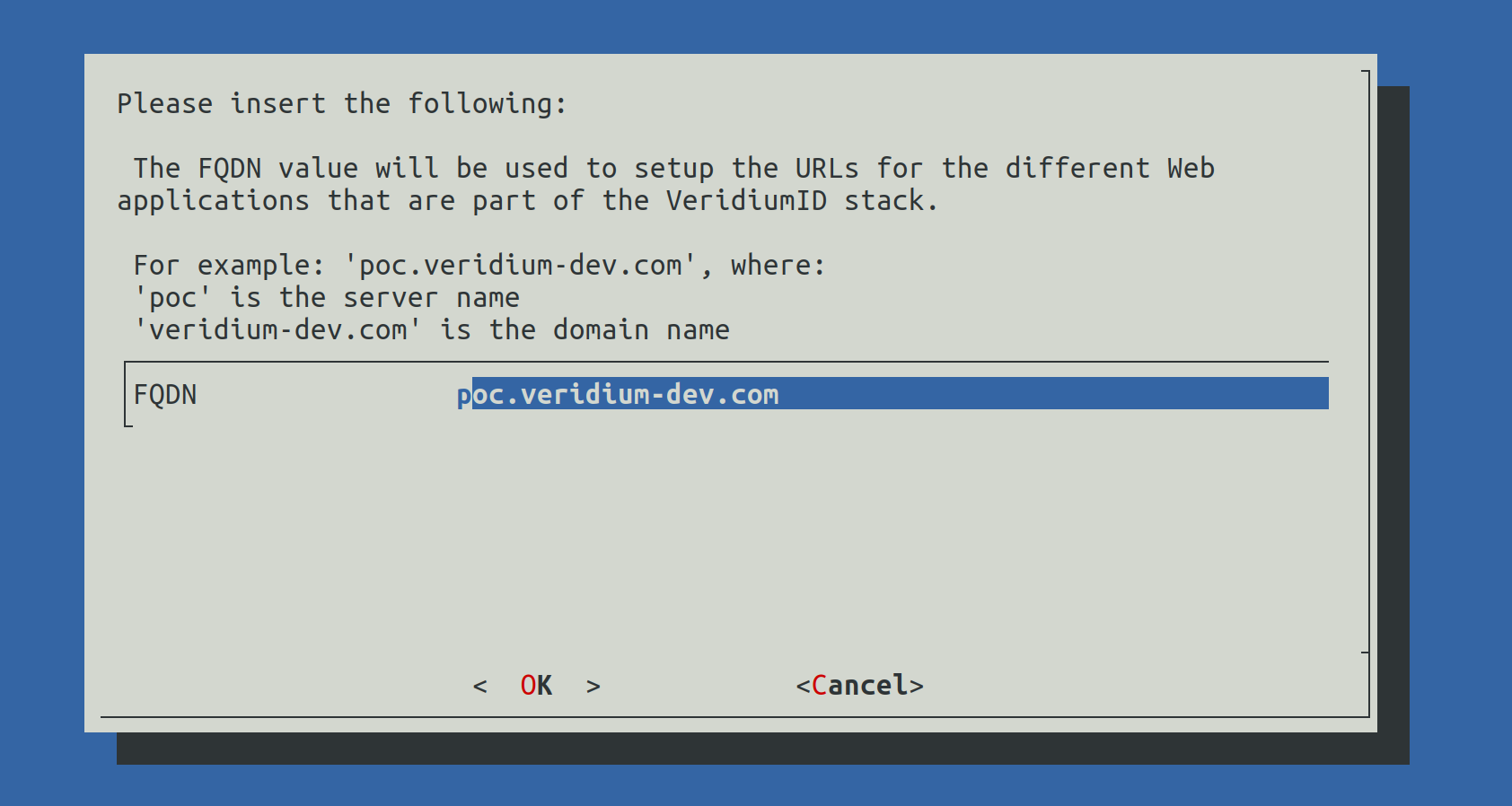
Write the correct FQDN in place of poc.veridium-dev.com and press the TAB key to go to OK and press Enter to continue.
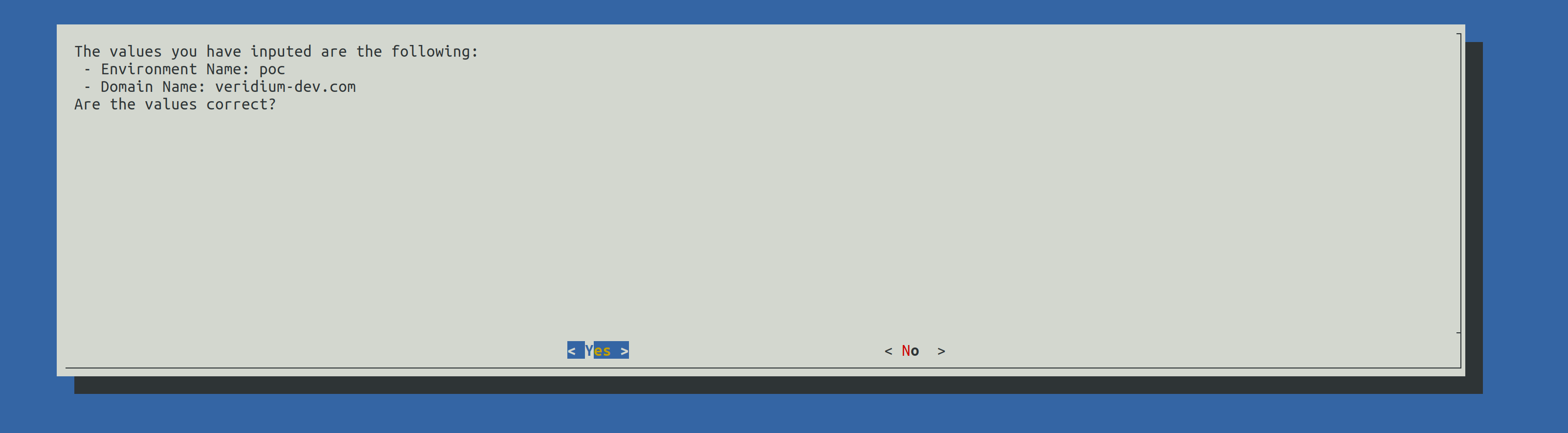
A validation of the FQDN will be prompted. Press Enter to continue.
2.4.3.2) Configure Certificates
When selection Configure Certificates the following screen will be shown:
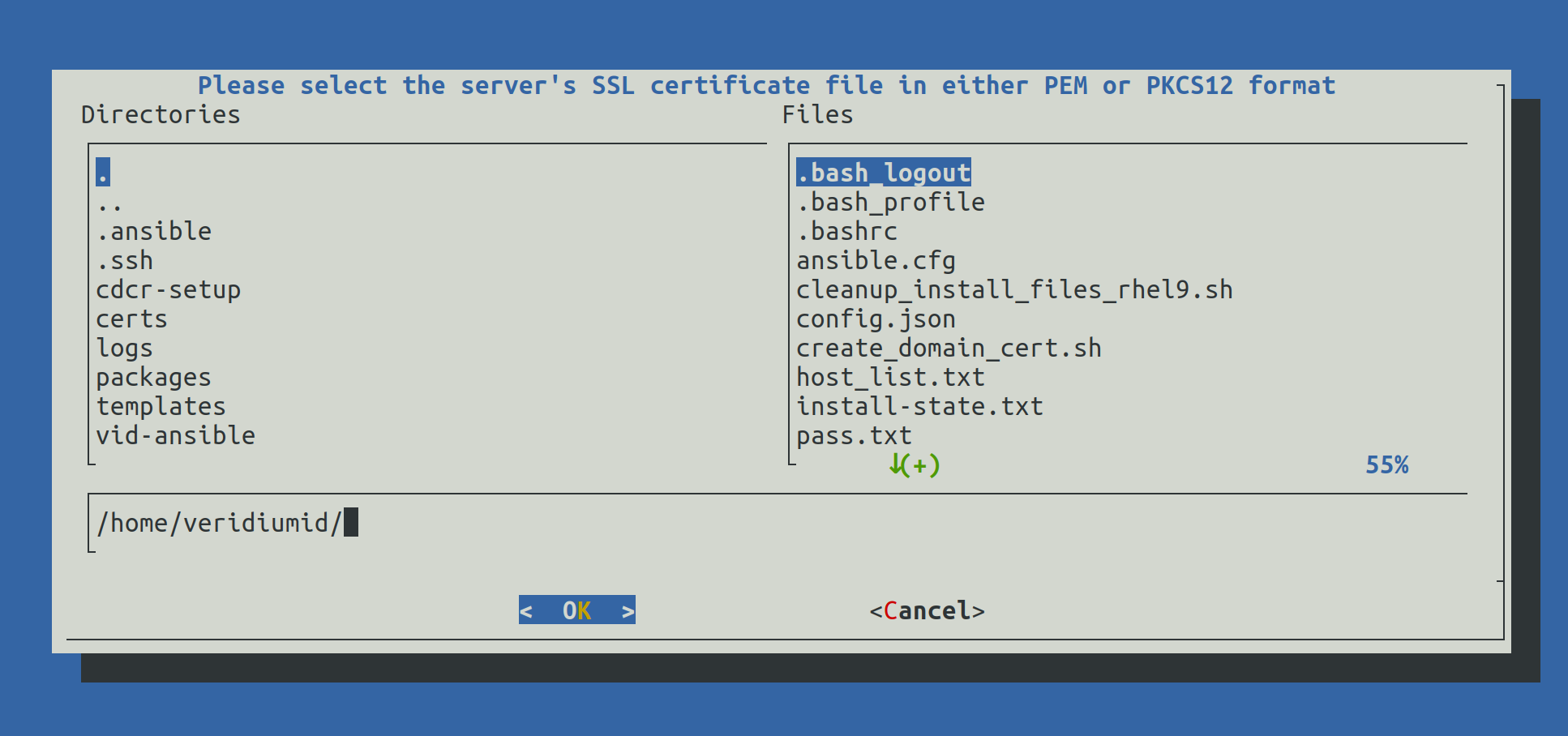
Write the full path of the certificate (for example: /home/veridiumid/certs/domain.p12) and press Enter to continue.
Another prompt for the password will be shown.
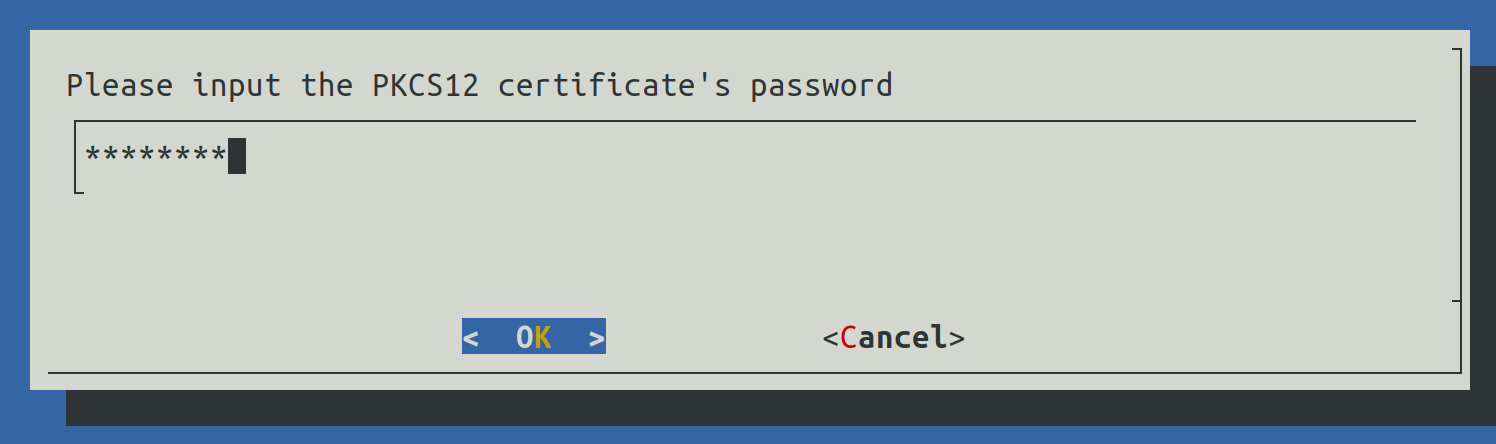
2.4.3.3) HaProxy configuration
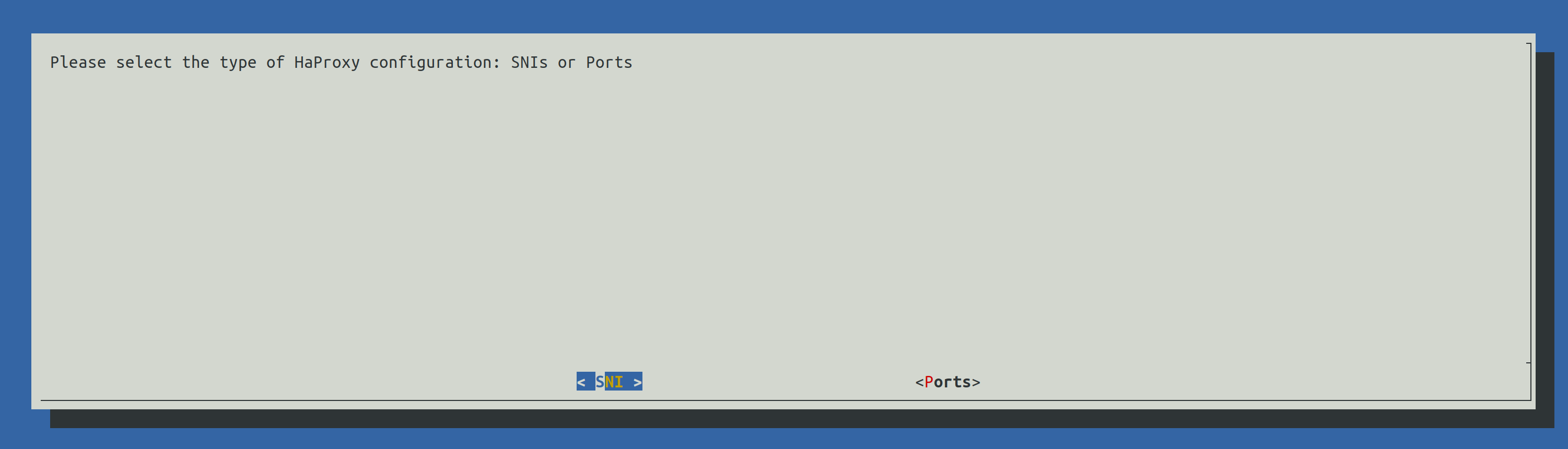
There are two configuration for HaProxy:
SNI: all component URLs will be composed from the base FQDN (the one provided during step 2.3.3.1) along side the components name, for example:
for the Admin Dashboad : admin-baseFQDN
for the Self Service Portal: ssp-baseFQDN
for the Websec API: baseFQDN
for Shibboleth (Identity Provider): shib-baseFQDN
Ports: all component URLs will be composed from the base FQDN and a different port for each component, for example:
for the Admin Dashboard: baseFQDN:9444
for the Self Service Portal: baseFQDN:9987
for the Websec API: baseFQDN:443
for Shibboleth (Identity Provider): baseFQDN:8944
2.4.3.4) Set Ansible Hosts
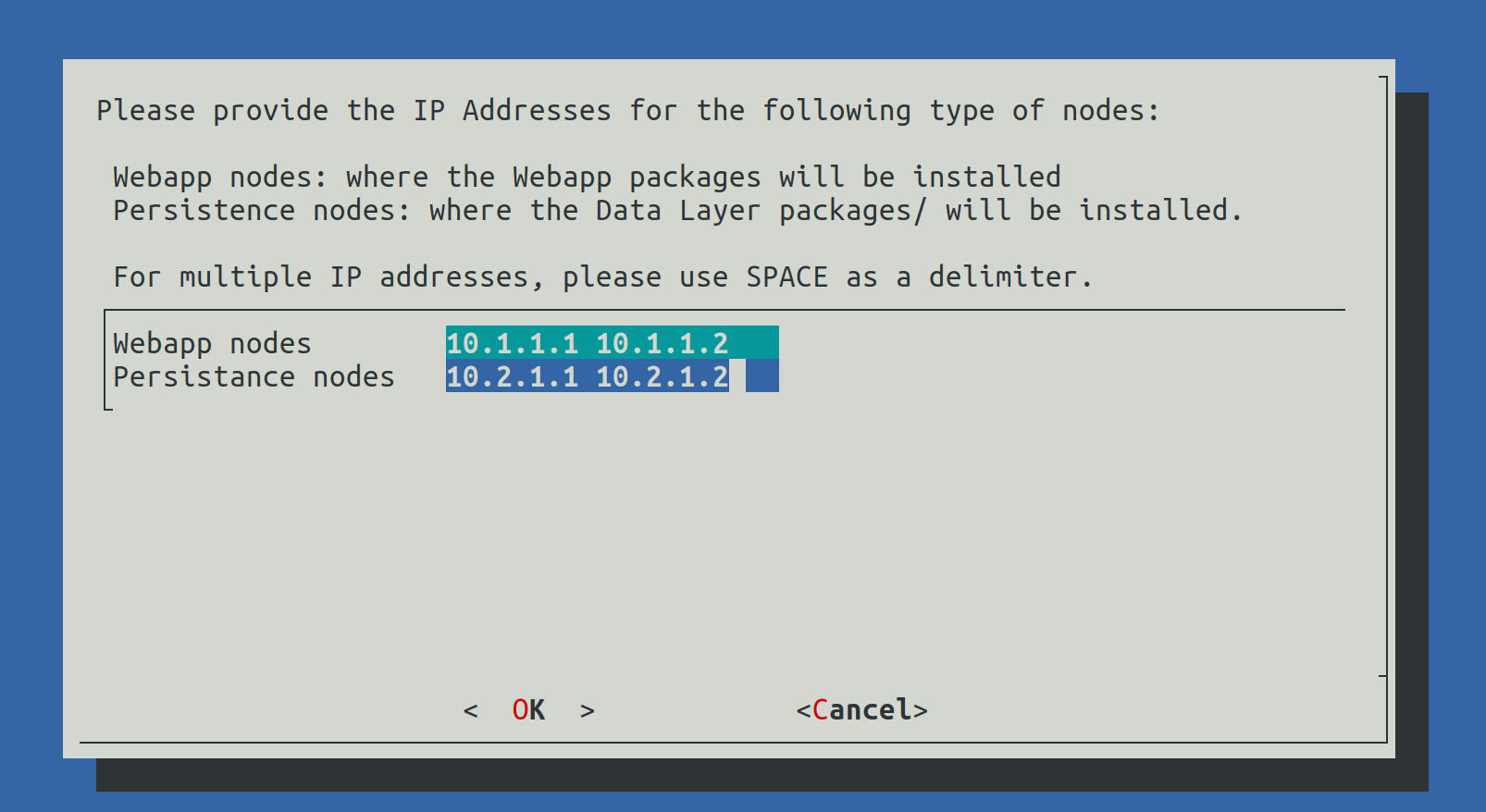
In this step the select from the list of IP addresses which will be Webapplication nodes and which will be Persistence node (Data nodes).
The list of nodes must be delimitted by Spaces.
2.4.3.5) Set RAM values
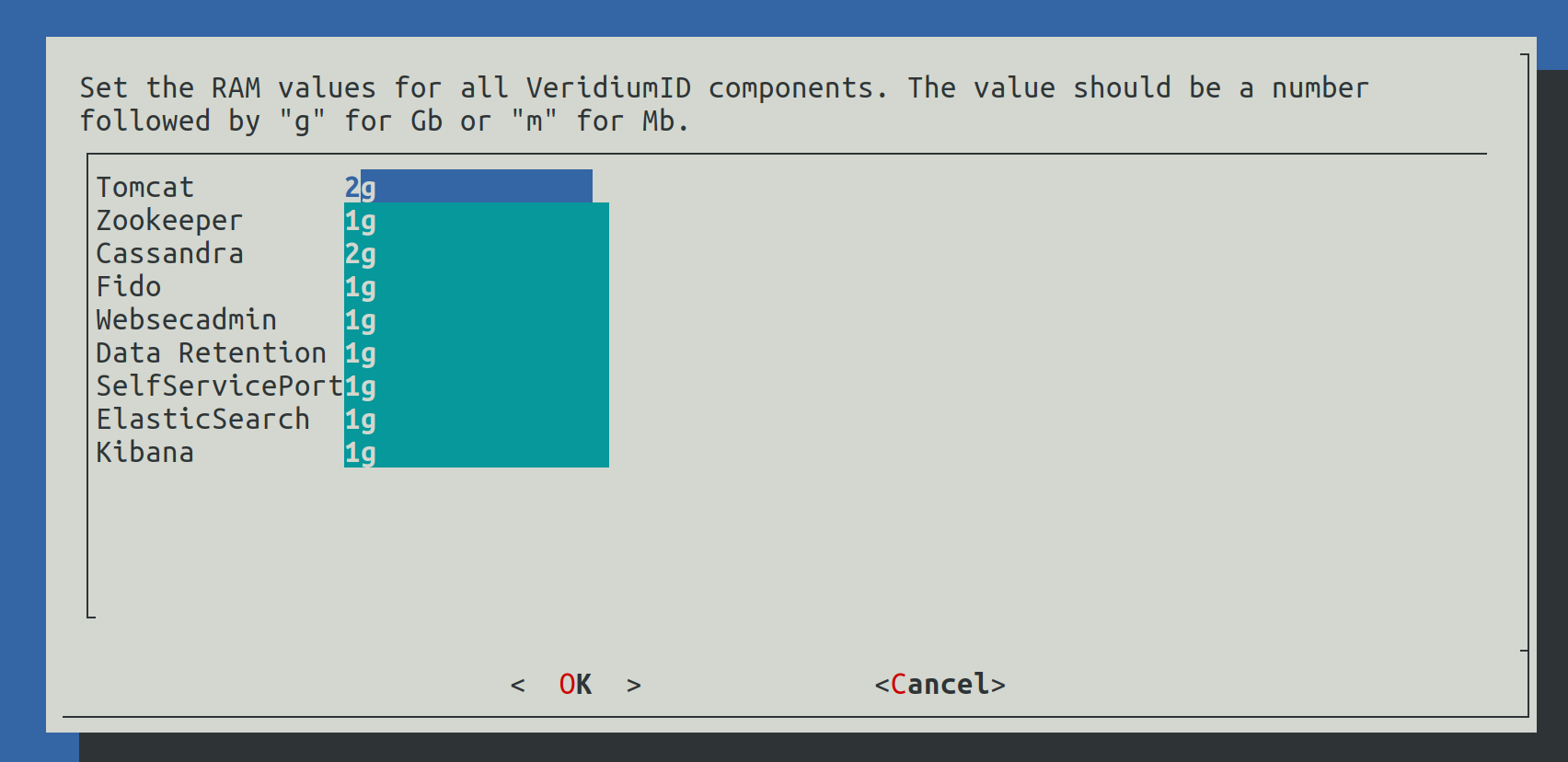
In this step the RAM values for different components will be configured. The value must contain a number followed by g for Gb or m for Mb.
2.4.3.6) Set CA variables
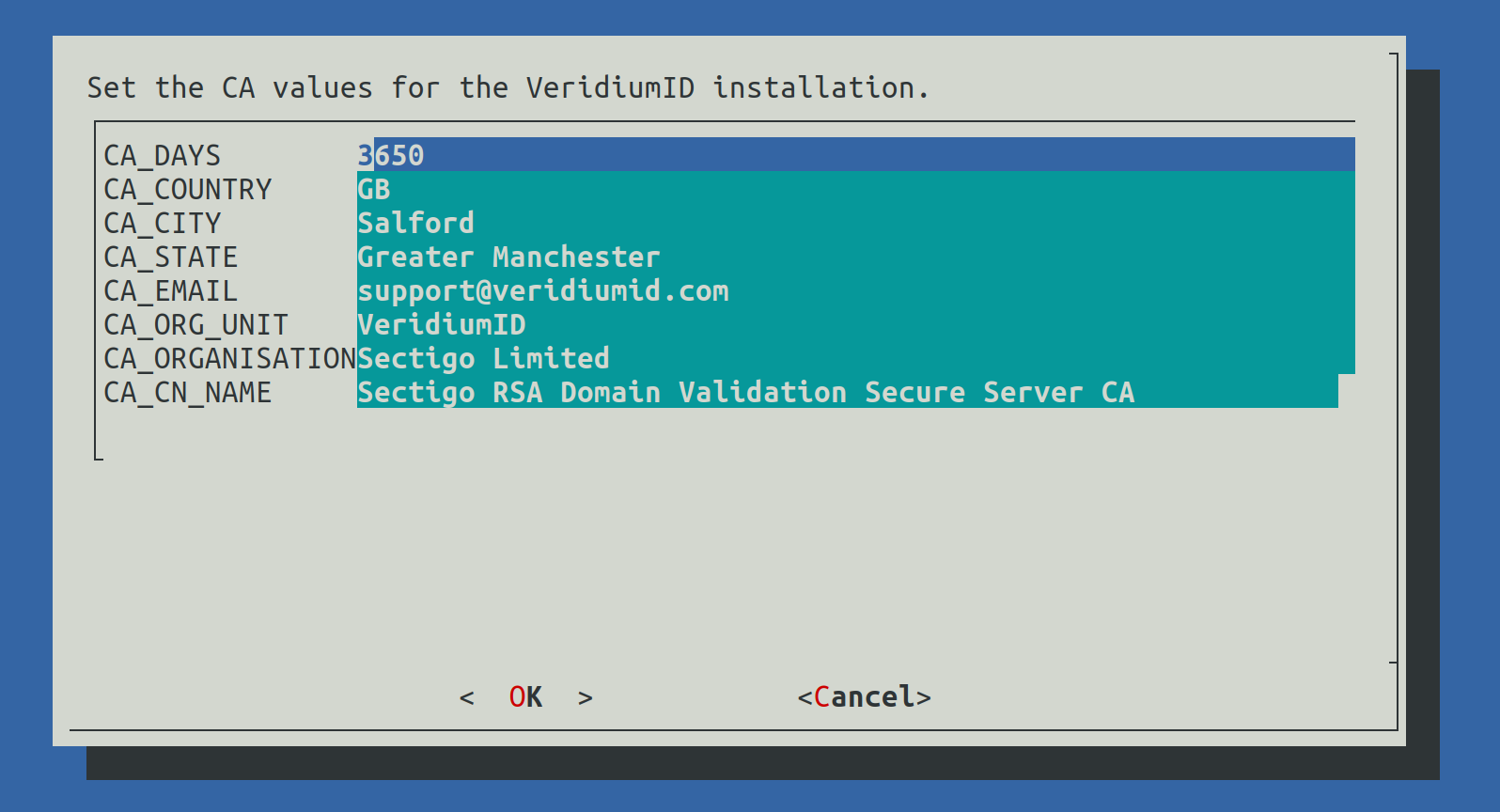
This step will configure the values used for the internal Certification Authority of the VeridiumID deployment (used to generate internal certificates).
2.4.3.7) Set Data Center Tag
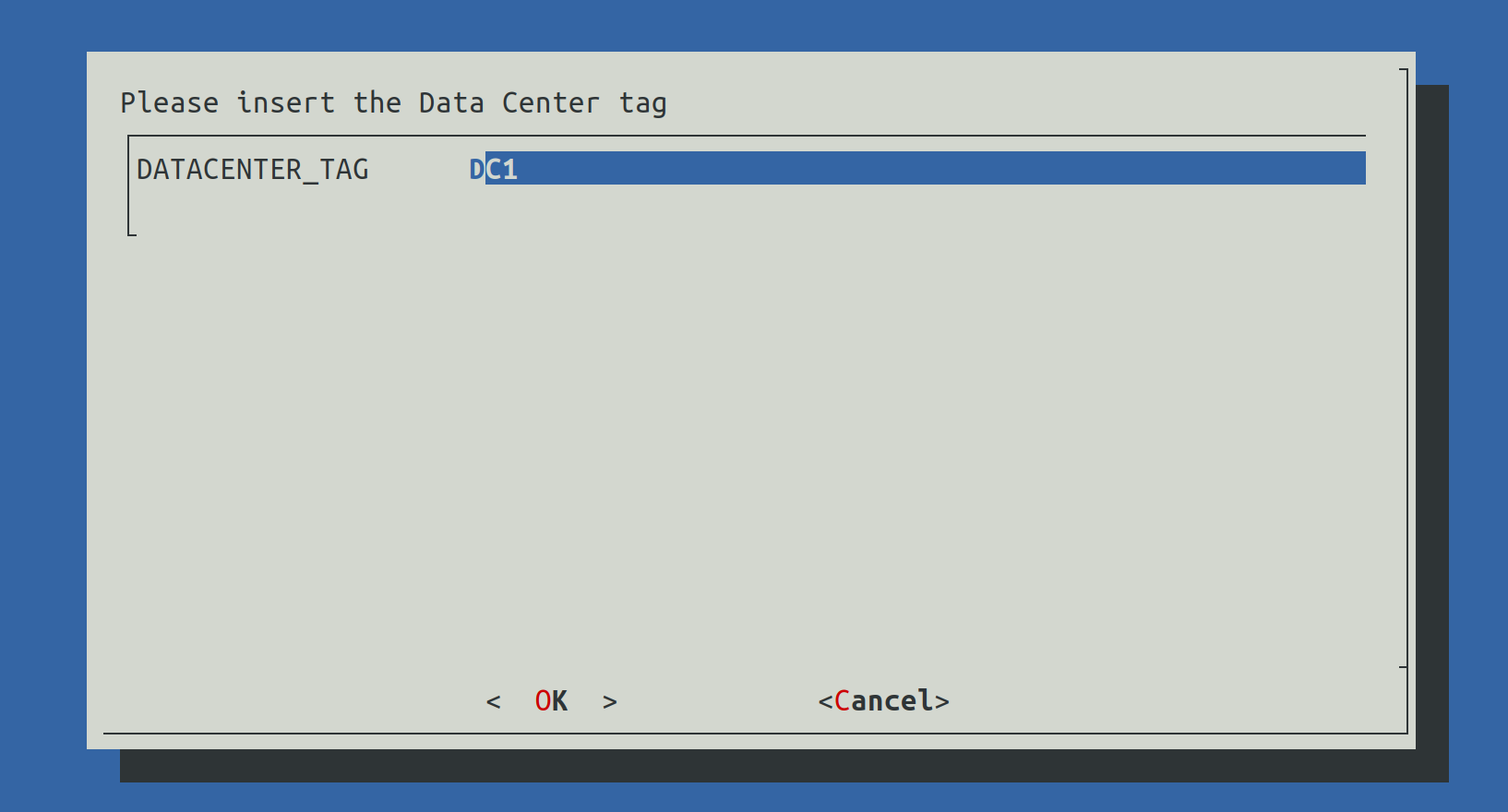
This value will be used to define the name of the current data center.
2.4.3.8) Show configuration
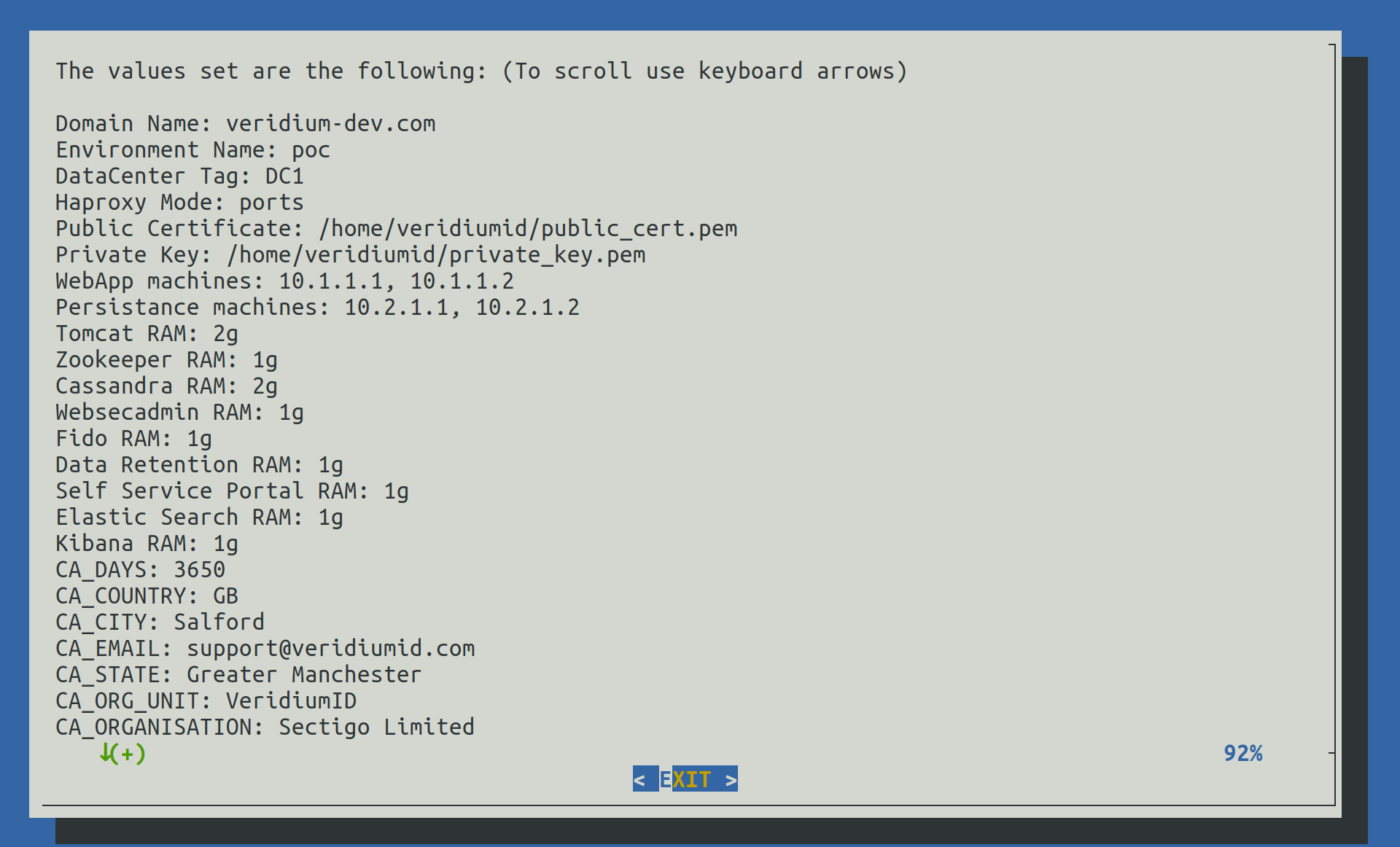
In this step we can verify all value provided earlier to validate them.
2.4.3.9) Start deployment
This step will close the Installation Wizard and provide the list of FQDNs:
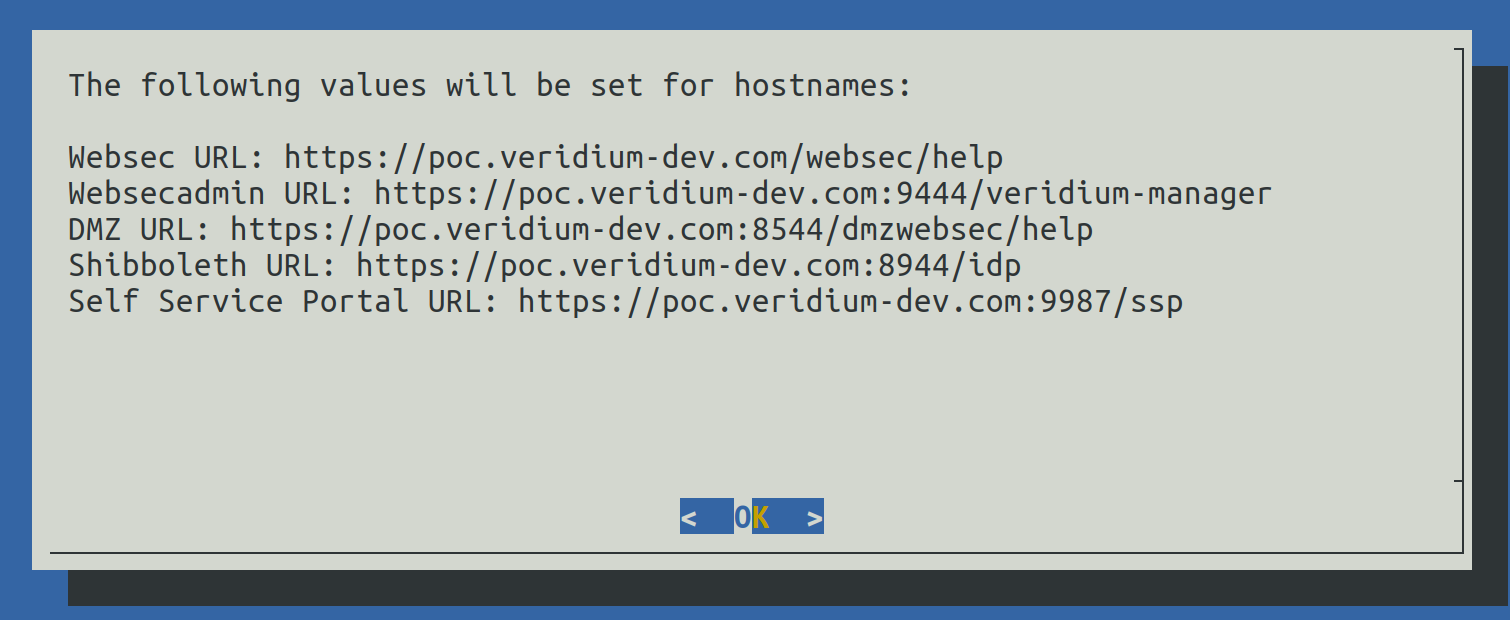
The values can be viewed later in the following file: /home/veridiumid/host_list.txt
After exiting the Installation Wizard, the deployment process will start by:
Checking the SSH connectivity from this node to all other nodes
Install specific VeridiumID components for Webapplication and Persistence nodes
Start the Ansible configuration
2.5) Cleanup installation files
In veridiumid user’s home directory the following script will take care of cleaning up installation files (in case of needing the same machine to deploy another environment or redeploying the environment).
Run the following command as veridiumid user:
# To remove local installation files (in order to deploy on a new environment):
./cleanup_install_files_rhel8.sh
# To redeploy the same environment (requires to remove the deployment's CA directory)
./cleanup_install_files_rhel8.sh -cIn order to redeploy the same environment, after using the cleanup command (with CA directory included) the following must be performed as well:
Connect to all webapp nodes and stop all services running the following command as root:
- BASH
bash /etc/veridiumid/scripts/veridium_services.sh stop
Connect to a persistence node and do the following:
Remove Zookeeper data using the following command as root:
- BASH
/opt/veridiumid/zookeeper/bin/zkCli.sh # And after accessing the Zookeeper command line deleteall veridiumid # To exit quit
Remove Cassandra keyspace using the following command as root:
- BASH
/opt/veridiumid/cassandra/bin/cqlsh --cqlshrc=/opt/veridiumid/cassandra/conf/veridiumid_cqlshrc --ssl -e 'drop keyspace veridium;' #(even it received timeout, it should be deleted; check with the following command; the veridium keyspace should not exists) /opt/veridiumid/cassandra/bin/cqlsh --cqlshrc=/opt/veridiumid/cassandra/conf/veridiumid_cqlshrc --ssl -e 'desc keyspaces;'
Connect to all persistence nodes and stop all services running the following command as root:
- BASH
bash /etc/veridiumid/scripts/veridium_services.sh stop
3) Set a signed certificate for the installation
Replace the self signed certificate with a proper one, delivered by client. If the client has a p12, the following script can be executed to extract the certificates. It will be generated a in conversion_result, the private key and the public certificate. Please copy, as per instructions, the file in haproxy and restart the service. Also in websecadmin, remove the selfsigned certificate and import the correct one.
/etc/veridiumid/scripts/convert_haproxy_cert.sh certificate.p12
#To change the Haproxy domain certificate please use the following command as root user:
# cp conversion_result/server.pem /etc/veridiumid/haproxy/server.pem; chown ver_haproxy:veridiumid /etc/veridiumid/haproxy/server.pem
# To restart the server after changing the certificate use the following command as root:
# service ver_haproxy restart