Splunk authentication through VeridiumID
This is an example with a splunk running in a docker.
Open a docker
docker pull splunk/splunk:latest
docker run -d -p 8000:8000 -e SPLUNK_START_ARGS='--accept-license' -e SPLUNK_PASSWORD='TestPassword!-1' splunk/splunk:latestConnect to veridium websecadmin and download metadata.
Download the metadata if not already done → Settings → Identity Provider → Download Internal Metadata.
Connect to splunk on http://localhost:8000 with admin and TestPassword!-1.
Go in splunk Settings → Authentication Methods → SAML → Configure Splunk to use Saml and:
SAML Configuration
Select file → upload veridium metadata.
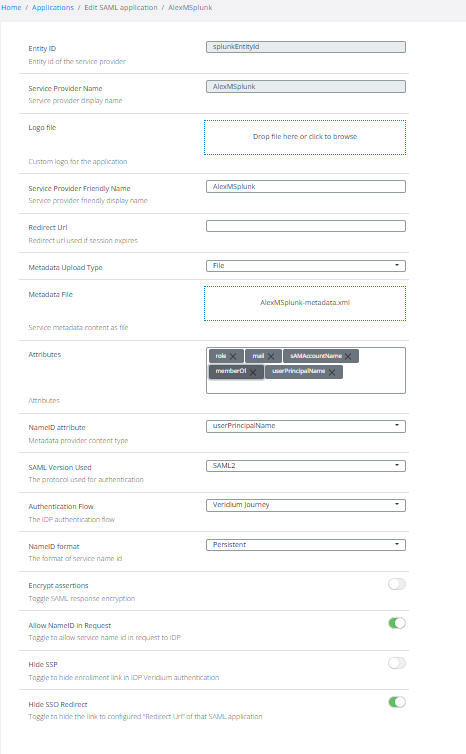
On EntityID set the Entity ID taken from splunk Metadata.
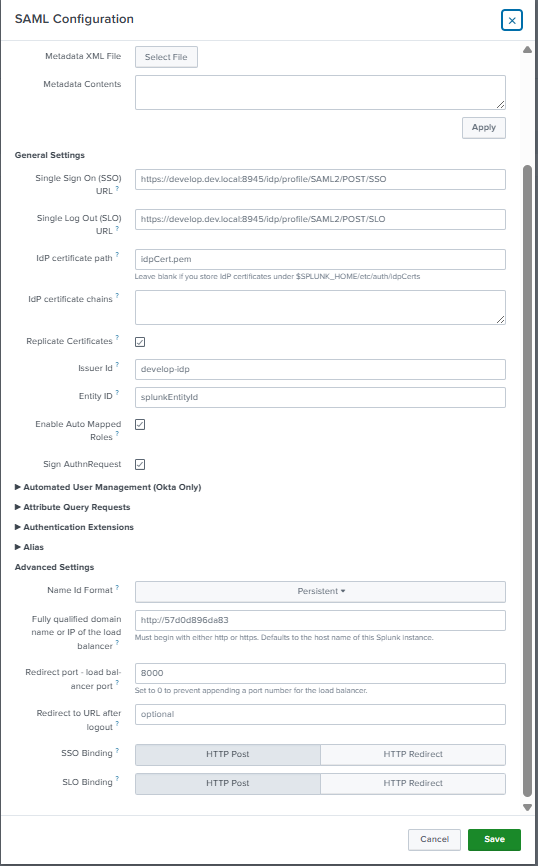
Choose in Advanced Settings Persistent and set the FQDN of LB. See printscreen 1.
Download metadata file for later use in veridium.
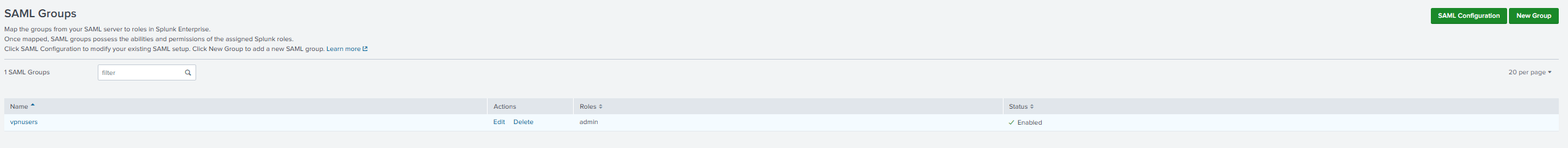
Add group mapping between LDAP groups and local Roles. See printscreen 2.
Login to websecadmin and do the followings:
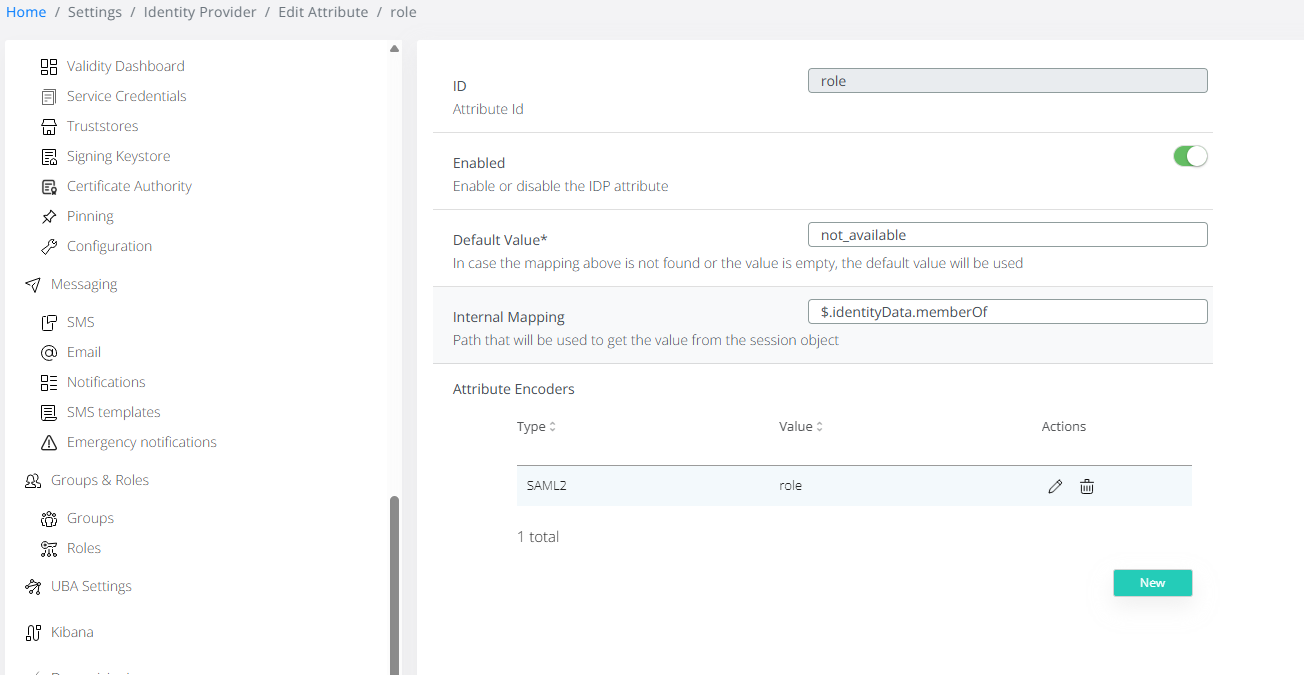
define a new attribute called role - small letters - very important (taken from splunk documentation). → Settings → Identity Provider→ Configuration → subject Derived Attributes → Add subject derived Attribute → Printscreen 3.
internal mapping should be $.identityData.memberOf
enable the attribute in Settings → Identity Provider → SAML → Attributes → Enable for role.
Create a new application → Applications → Add Saml app. See printscreen 4 for more details.
if necessary, please also enable single Logout, by going to Settings → Identity Provider → Configuration → Enable Single Logout.
After this, the login and logout in Splunk should be functional.
Prinstscreen 1:
Printscreen 2:
Printscreen 3:
Printscreen 4: