Sign in with passkey
Introduction
This document outlines an enhancement to the VeridiumID authentication platform that introduces a more streamlined sign-in experience using passkeys. By leveraging FIDO Discoverable Credentials, users can now initiate authentication and be identified without needing to enter their username upfront, simplifying the login process.
Key Terminology
Passkey: A digital credential based on public/private key cryptography that replaces traditional passwords. Passkeys can be device-bound (stored on a specific device) or synced across a user's devices via their account provider (e.g., Google, Apple).
Discoverable Credential (Resident Key): A type of passkey where the private key and associated user information (metadata) are stored directly on the authenticator (e.g., a security key, smartphone, or computer's secure hardware). This enables the authenticator to identify the user to a Relying Party (like VeridiumID) without the Relying Party needing to know the username beforehand or send any credential identifiers to the authenticator.
Websec Client: Client applications that integrate with Veridium's Websec API to provide user authentication. Examples include the Veridium Windows Credential Provider and the Veridium Identity Provider.
Relying Party (RP): The service (in this context, VeridiumID) that relies on the FIDO authenticator and passkey to verify a user's identity.
FIDO Assertion: The cryptographic proof generated by the authenticator after a user successfully authenticates with their passkey. This assertion is then validated by the Relying Party.
Feature Overview: Username-less Sign-In with Passkeys
Previously, using a passkey for VeridiumID authentication required the user to first input their username to initiate the FIDO (Fast IDentity Online) authentication workflow.
This enhancement leverages VeridiumID's existing FIDO Relying Party support for Discoverable Credentials. It allows the system to identify the user after they have successfully presented their passkey and a FIDO assertion has been generated. This eliminates the preliminary username entry step, offering a more intuitive and faster login experience.
How "Sign in with a passkey" Works
User Interaction: When a user accesses a service protected by VeridiumID via a supported Websec Client, they will be presented with a "Sign in with a passkey" option.
Initiation: Selecting this option directly starts the FIDO authentication workflow. The browser or operating system will prompt the user to use any passkey previously registered for this service that supports Discoverable Credentials.
Authentication & Identification: Upon successful validation of the passkey by the authenticator and subsequent validation of the FIDO assertion by VeridiumID, the user's identity is determined from the Discoverable Credential. The authentication challenge is then resolved, granting access.
System Implementation Details
Veridium Session Lifecycle:
This feature utilizes an initial Veridium Session state called "Opportunity." An "Opportunity" session is created without an associated user identity.
Previously used primarily for QR Code engagement (where a registered device is later attached to the session), this "Opportunity" state can now also facilitate the "Sign in with a passkey" flow.
Configuration and Orchestration (Websec and Administration):
The "Sign in with a passkey" option is configured as a user engagement method within the VeridiumID Orchestrator Selector, alongside other methods such as QR code, username input, or certificate-based authentication.
When this passkey engagement is enabled, new "Opportunity" sessions will automatically include all necessary data for WebAuthn API integration. This includes the
clientDataJSONand any security policies enforced by the configured Relying Party.After the FIDO assertion is received and validated by the Veridium FIDO service, the Websec service updates the session. It binds the user's identity (retrieved from the Discoverable Credential) and the attestation result to the session. The authentication flow then proceeds according to the orchestration logic.
If the FIDO assertion fails validation, the "Opportunity" session will be marked as "Terminated."
Websec Client Behavior:
Websec Clients will display the "Sign in with a passkey" option if the "Opportunity" session data indicates support for WebAuthn (i.e., contains the necessary WebAuthn data).
The visual presentation of the "Sign in with a passkey" option must adhere to the FIDO Alliance Style Guidelines for user interface consistency.
When a user selects this option, the Websec Client initiates the WebAuthn authentication ceremony, prompting the user to present their passkey.
If the authentication with the passkey is successful locally, the resulting FIDO assertion is sent to the Websec service for server-side validation and session binding.
Benefits
Improved User Experience: Faster and more convenient login by removing the need for initial username entry.
Enhanced Security: Leverages the strong cryptographic security of FIDO passkeys.
Streamlined Integration: Utilizes existing FIDO standards and VeridiumID session management capabilities
Functional flow UI samples for mobile app (for Admin configuration, please read (v3.8) Passkeys administration :
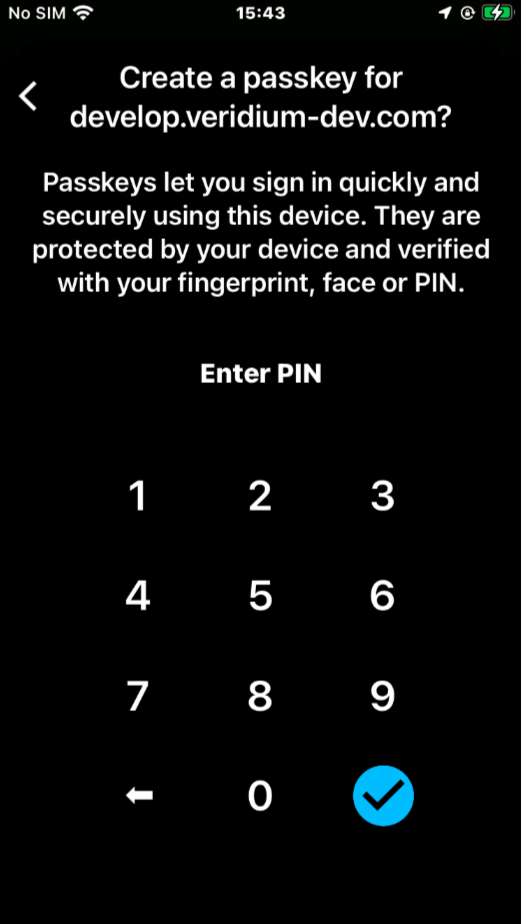
- passkey creation steps during enrolment: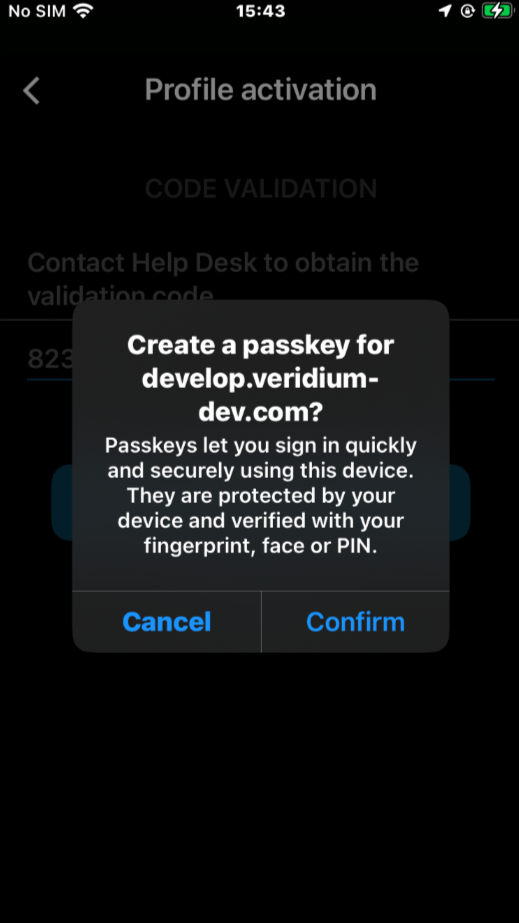
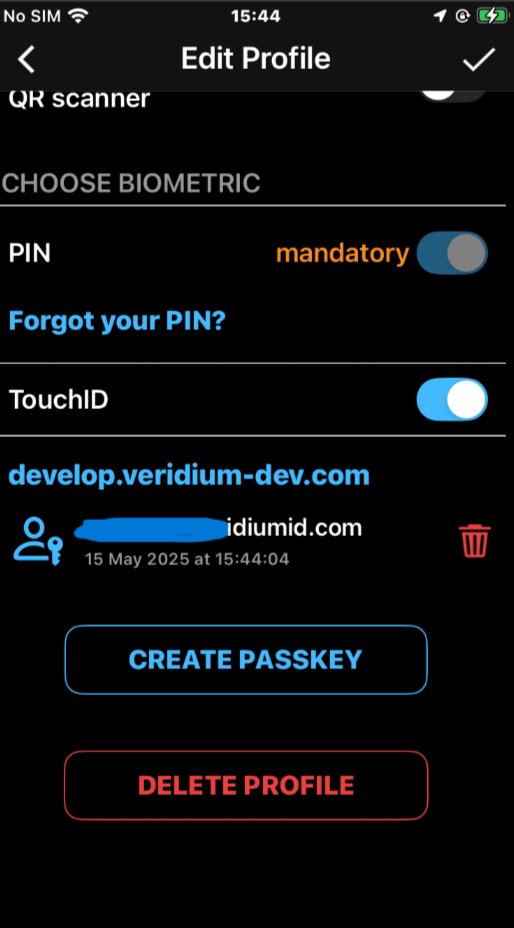
visibility in Edit Profile section of the mobile apps, for both Veridium and Entra enrolled passkeys:
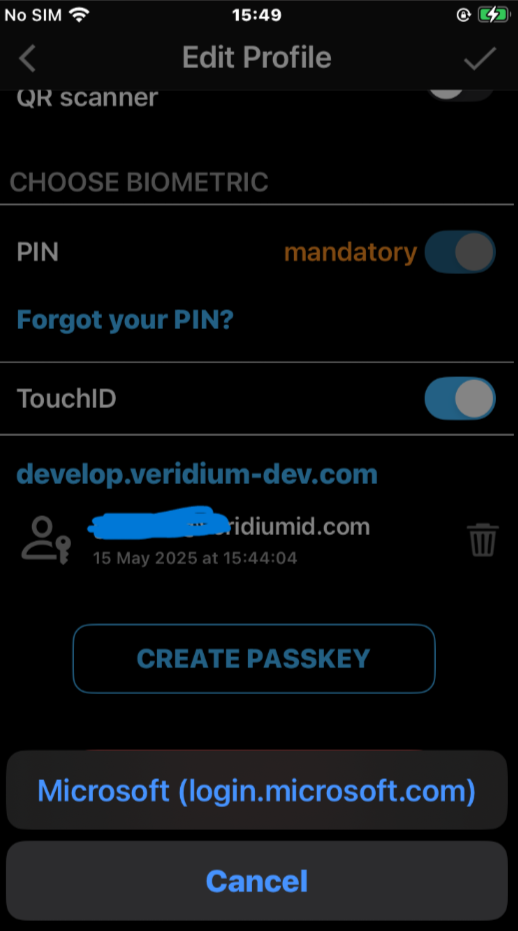
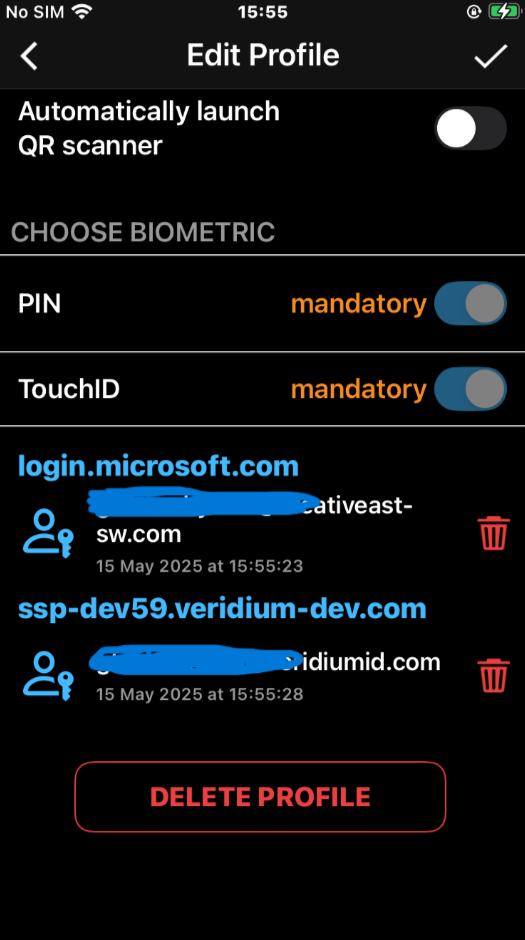
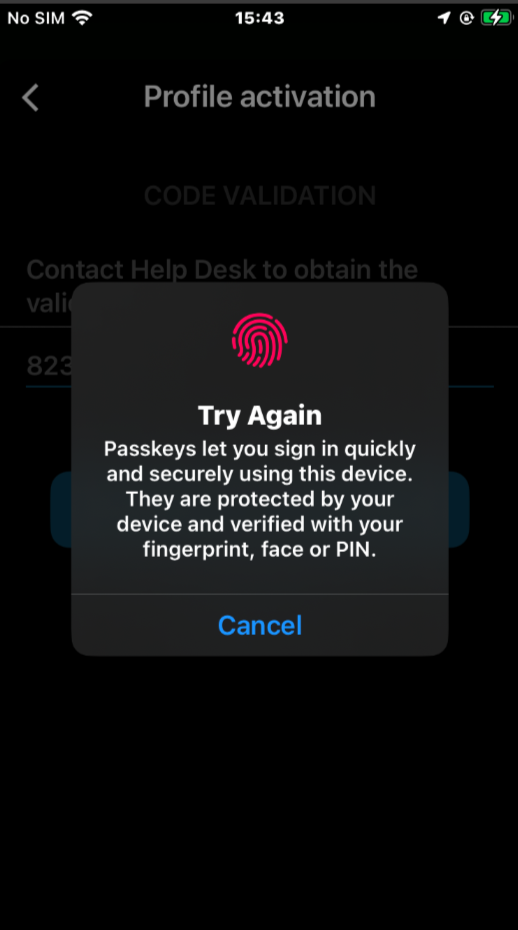
negative scenarios samples for deletion, wrong Admin configuration or access rights and biometric retry:
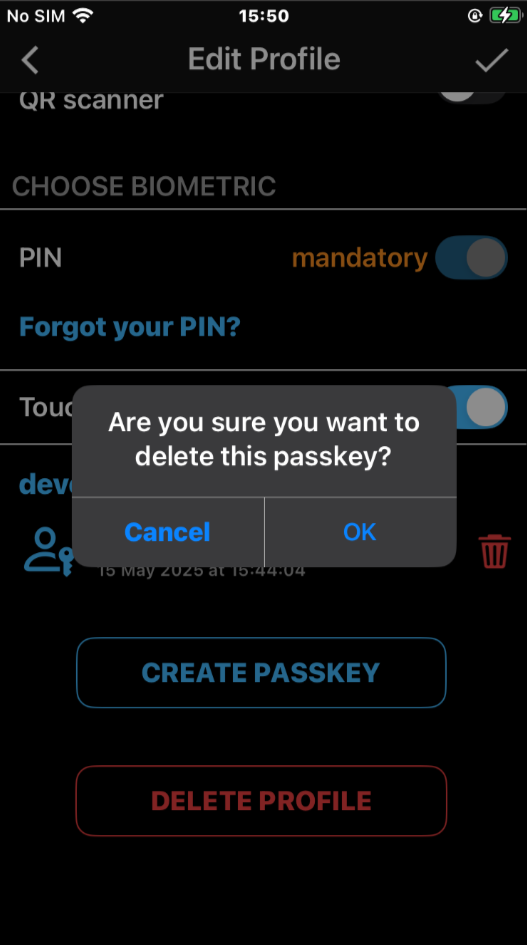
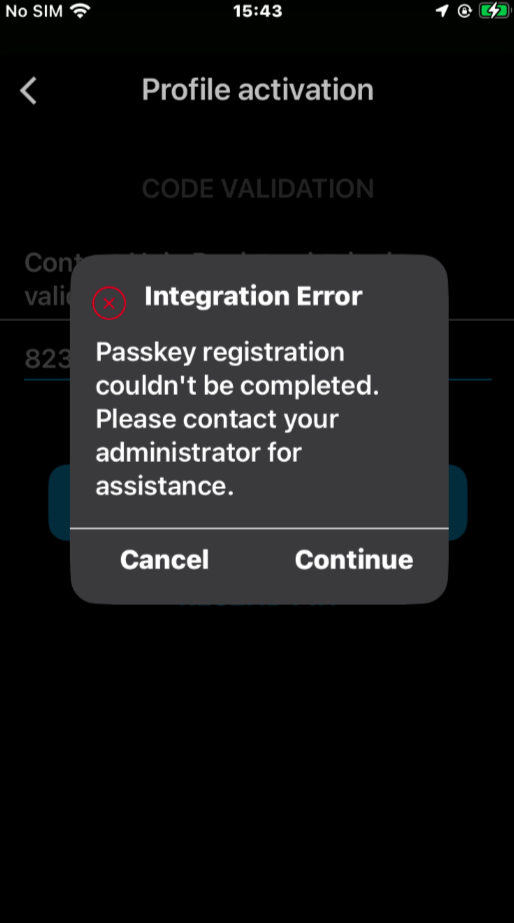
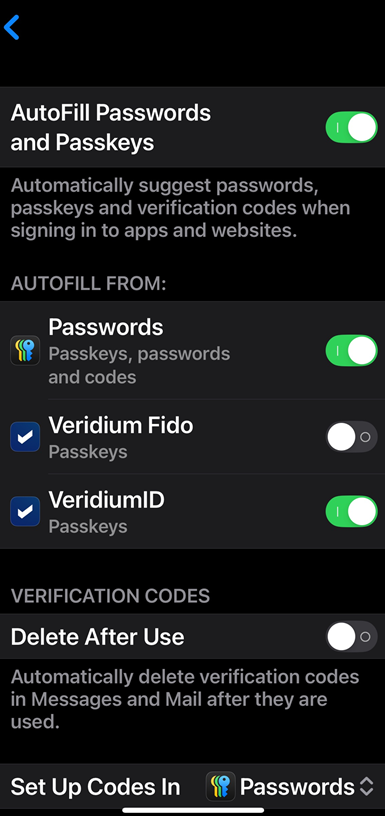
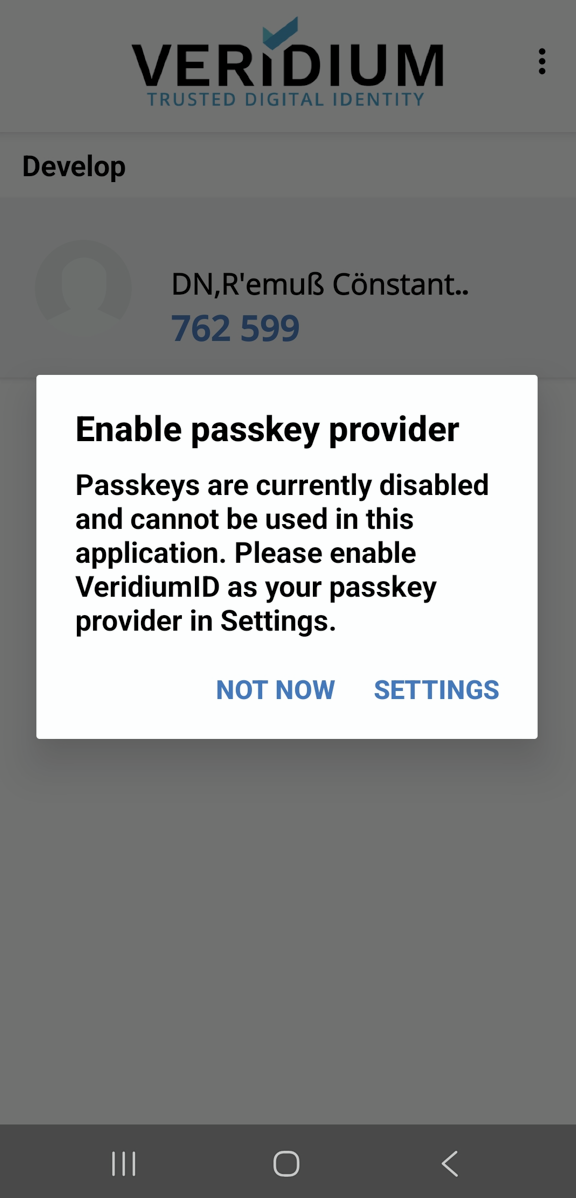
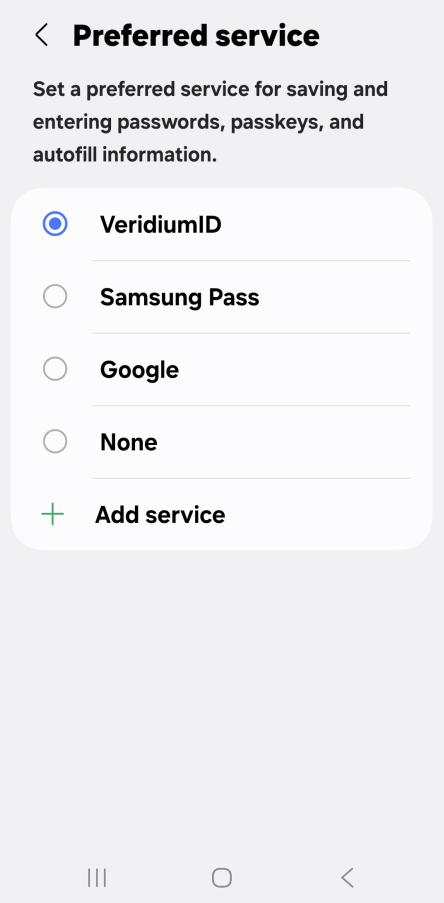
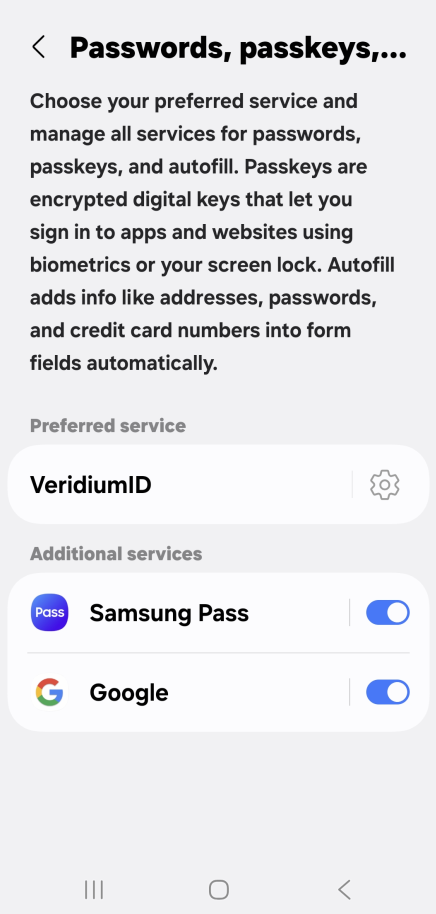
Both Android and iOS have settings to define accepted passkey providers. Please ensure that VeridiumID is enabled as a passkey provider:
1. Android: Settings → Security and privacy → More security settings → Passwords, passkeys, and autofill → enable VeridiumID (and if desired, choose it as the preferred provider too)
iOS: Settings → General → Autofill and Passwords → “Autofill from: VeridiumID”