Enhanced audit action and event log
Overview
In this release, Action Log section in the Admin platform and Event Log files were improved to capture important user-driven activities. Previously, only actions performed from the Admin manager platform were logged, which meant certain actions performed by the users—like blocking an account after multiple incorrect PIN attempts—were not recorded.
To address this gap, a new “User activity logs” view was introduced in the Action Log section. You can now track and review critical user activities, and see which identity (if any) was the target of that action.
Key Changes
Search/Filter logs
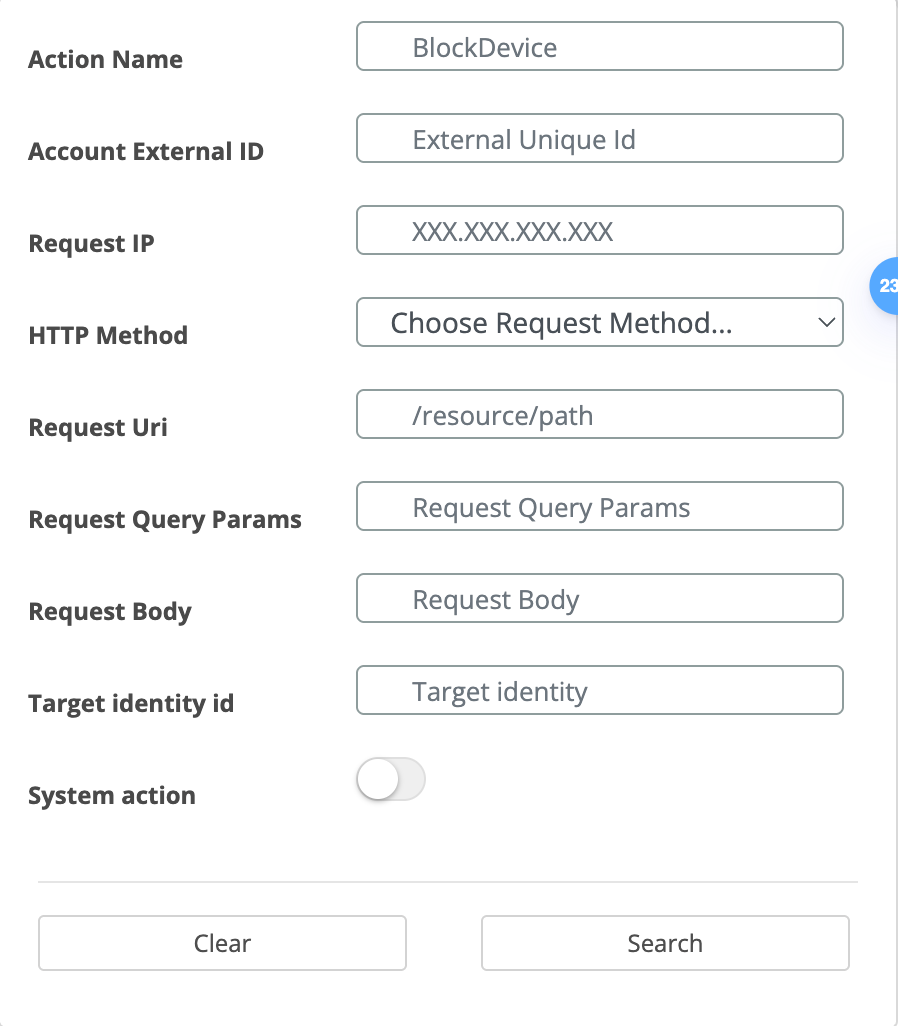
In the Audit → Action Logs page, open the Search dropdown.
Select the System Action toggle to display all user-generated records.
Filtering by Target Identity ID
The Target Identity ID filter was introduced within the search bar dropdown, allowing you to narrow down the logs to a particular identity. This is especially useful when investigating a specific user or troubleshooting issues related to a single identity.
List of Recorded User Actions
The following events (previously unlogged or partially logged) are now captured as User Activity Logs:
Initiate Enrollment
Enroll Account
Delete Identity
Block Account
Delete Device
Block Device
Unblock Device
To make it clear which identity each action was performed on, the target identity ID is now included in the logs. This field is populated for most actions and allows you to quickly identify the exact identity affected.
Benefits
Improved Audit Trail: Quickly trace user actions, such as device deletions or account blocks, back to the responsible identity.
Clearer Accountability: The addition of the target identity ID enhances accountability by showing exactly who or what was affected by each action.
Streamlined Investigations: If security or compliance issues arise, having these user activities logged in one place accelerates auditing and troubleshooting.
Cases like blocking a device can not detect for what identity is this action made because a device (phone for example) can be linked to the multiple identities.
