Configuring External Elasticsearch and Kibana Integration in Veridium Manager
Veridium Manager provides the flexibility to integrate with external Elasticsearch and Kibana instances, allowing clients to leverage their existing infrastructure. This document outlines the configuration process and the resulting changes within the Veridium Manager administration console.
This feature enables administrators to:
Integrate Veridium Manager with client-managed Elasticsearch and Kibana deployments.
Redirect users to external dashboards and statistics pages.
Streamline the build process by skipping internal Elasticsearch migrations when external systems are in use.
Configuration:The integration is configured through a new setting in the Settings / Advanced /
elasticsearch.jsonfile.Setting Name:
useExternalElasticDefault Value:
falsePurpose: Determines whether to use an external Elasticsearch and Kibana system.
Configuration Steps:
Configure Elasticsearch connection
add to Websecadmin → Settings -> Truststore the certificate from Elasticsearch connection.
#this is how the certificate can be taken, or can be taken from the browser.
#it is important to add the intermidate certificate.
openssl s_client -connect IP1:9200modify in Websecadmin → Settings / Advanced / elasticsearch.json
{
"useExternalElastic": true,
// ... other settings ...
"keyspace" : "veridium", ##default value veridium, used for prefixing all elastic indexes used by application
"port" : 9200, ## default port is 9200
"hosts" : "IP1,IP2,IP3", ## can be the VIP or individual IPs of Elasticsearch cluster (e.g. elk.dev.local)
"apiKey" : "", ##if you want to use apiKey, you can populate this field, otherwise set it empty
"credentials" : {
"passwd" : "xxxxxx", ##password to external elasticsearch
"user" : "elastic" ##user for elasticsearch
},
}Configure kibana information: modify in Websecadmin → Settings / Advanced / kibana.json
the baseURL of Kibana, that will show in admin
set the apiKey to empty (e.g. ““)
Create objects in Elasticsearch: Download the archive from veridium repository (the one for a specific version) elasticsearch-templates-BUILDNO.zip and execute it on elasticsearch server.
unzip elasticsearch-templates-BUILDNO.zip -d veridiumData
#modify the script to set the number of replicas and schema name:
vim veridiumData/createElkKibanaObjects.sh
## execute the script by providing the ELK connection:
bash veridiumData/createElkKibanaObjects.sh ELASTIC_HOST ELASTIC_PORT ELASTIC_USER ELASTIC_PASS
Upload the dashboards in kibana:
Create a new space dedicated for veridium objects in kibana: Stack management-> kibana -> spaces -> create space
Switch the space in kibana admin to veridium one.
replace in kibana_dashboards.ndjson word “veridium.” with the schema you want to use, in case it was chosen a different schema
Import the attached dashboards: Stack management -> kibana -> saved objects -> Import
Assign users to see only this kibana space. So the dashboards about new onboarded users can be seen in admin.
User Interface Changes (When useExternalElastic is true):
Dashboard and Statistics Pages:
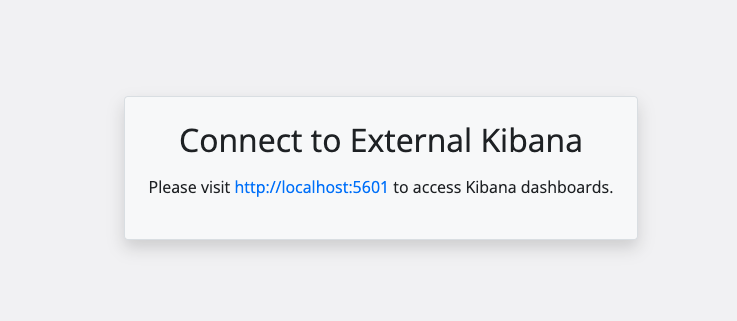
The Veridium Manager Dashboard and Statistics pages will be replaced with a redirect message.
This message will contain a link to the external Kibana dashboard.
All identities, accounts, sessions now will be now taken from Elasticsearch.
Please also check the Elasticsearch status in Websecadmin → Tools → monitoring → websecadmin → elastic.response.time.
Redirect Message: The message will clearly indicate that the user is being redirected to an external system.