Configuration Multiple Servers
Veridium Credential Provider (CP) version 3.2.4 and higher introduces a significant enhancement to high availability and failover capabilities. This feature allows administrators to configure primary and secondary connection strings, providing redundancy and ensuring uninterrupted authentication services in case of server outages or network disruptions.
Feature Overview
Primary and Secondary Connection Strings:
The new version of the CP allows for the configuration of two sets of connection strings: primary and secondary.
Each set includes a unique name for identification.
This enables the CP to connect to a secondary Veridium server if the primary server becomes unavailable.
HDX Connection Logic:
During HDX session validation, the CP first attempts to connect to the primary Veridium server.
If the validation fails, the CP automatically switches to the secondary server.
If the secondary server successfully validates the session, the CP designates it as the new default server.
Device Authentication Certificates:
The Bops logon service retains both device authentication certificates (from the primary and secondary servers).
It returns the appropriate certificate based on the current default server preference.
Unlock scenario:
CP will allow use same instance as was used on HDX initial logon (described as “Default” in previous text).
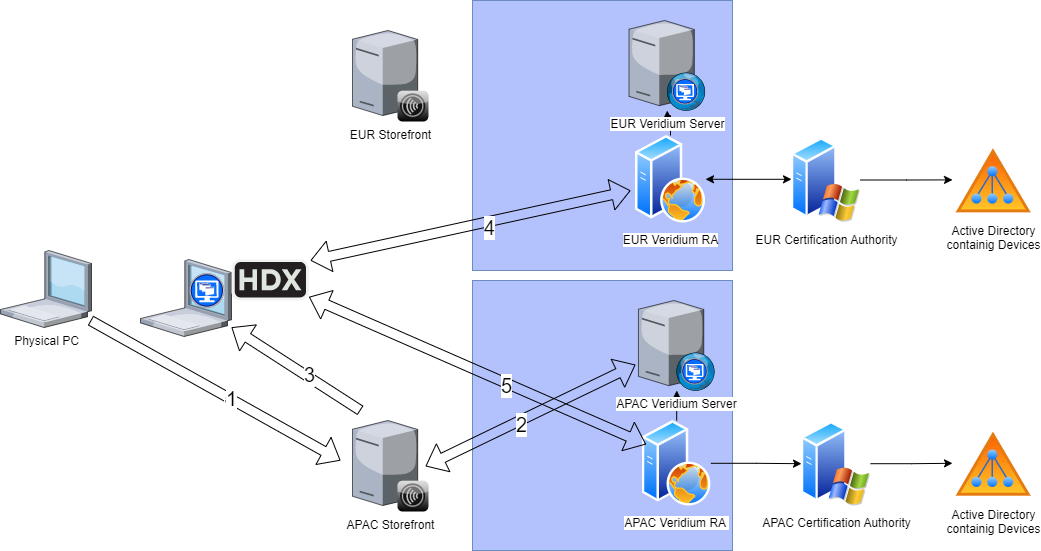
User on host authenticates on APAC Storefront (first time).
StoreFront does SAML authentication using APAC Veridium Server
VDI is started, HDX interface is called. Session ID is transferred to HDX
HDX tries to verify on EUR Veridium RA. Veridium RA verifies request on EUR Veridium Server. Since Session ID was not generated on this server, it will fail.
HDX tries to verify on APAC Veridium RA. Veridium RA verifies request on APAC Veridium Server. Since Session ID was generated on this server, it will succeed, authentication token will be returned. Since this moment, APAC instance will be set as default.
Settings:
All settings are stored on registry keys:
HDX entry:
[HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Citrix Virtual Desktop Agent\Authentication\HdxCredentialSelectorPlugins]
"VeridiumAuth"="{B311C8B4-73F2-4C2F-bC92-fAfC00ACDC5B}"Veridium CP settings (example):
[HKEY_LOCAL_MACHINE\SOFTWARE\VeridiumID\VeridiumAD]
"EnableSecondaryURLs"=dword:00000001
"SecondaryURLsSuffix"=""
"BOPS_URL"="https://develop.veridium-dev.com/websec/rest/enterprise/"
"BOPS_URL_EXTERNAL"="https://develop.veridium-dev.com/websec/rest/enterprise/"
"ENROLL_URL"="https://dev-dc1.dev.local/BopsEnroll/BopsEnroll.svc/"
"RA_URL"="https://dev-dc1.dev.local/RaWebApp/api/"
"BOPS_URL2"="https://dev1.veridium-dev.com/websec/rest/enterprise"
"BOPS_URL_EXTERNAL2"="https://dev1.veridium-dev.com/websec/rest/enterprise"
"ENROLL_URL2"="https://dev-dc2.dev.local/BopsEnroll/BopsEnroll.svc/"
"RA_URL2"="https://dev-dc2.dev.local/RaWebApp/api/"Registry key description:
Environment | Key | Value | Description |
|---|---|---|---|
Global |
| 1 | To enable multiple servers support, needs to be set to “1”. Default is “0”. |
EUR instance connection details |
|
| Internal VeridiumID server (EUR) |
|
| Externally available VeridiumID server (EUR) | |
|
| Veridium EP URL (EUR) | |
|
| Veridium RA URL (EUR) | |
APAC instance connection details |
|
| Internal VeridiumID server (APAC) |
|
| Externally available VeridiumID server (APAC) | |
|
| Veridium EP URL (APAC) | |
|
| Veridium RA URL (APAC) |
