Microsoft Entra ID & Hybrid Integration
Universal User Model & Intelligent Merging
VeridiumID has transitioned from siloed directory management to a Unified User Model.
Single Identity Representation: Regardless of whether a user exists in a local Active Directory, a cloud-based Entra ID, or both, they are represented as a single object within the system.
Conflict Resolution: When a user is discovered in multiple sources, the system applies a "Hybrid" merge strategy where LDAP acts as the authoritative primary source for core identity data.
Source Attribution: Each identity is explicitly tagged as Active Directory, Entra ID (Cloud-Only), or Hybrid User, allowing for granular security policies based on the user's origin.
Extended Attribute Mapping: Secondary attributes from Entra ID (like specific cloud-only metadata) are preserved within an
extendedAttributescontainer, enriching the primary LDAP profile without overwriting it.
Multi-Tenant Entra ID Architecture
Organizations can now scale their cloud identity footprint by connecting to multiple tenants simultaneously.
Independent Configuration: Each Entra connector maintains its own unique Client IDs, Tenant IDs, and attribute mappings.
Domain Pattern Matching: To optimize performance and accuracy, administrators can define simple string patterns (e.g.,
*@company.onmicrosoft.com) to dictate which connector handles specific user domains.
Expanded User Classifications
The system now explicitly categorizes users into three distinct types for better administrative visibility:
Active Directory (On-Prem): Standard LDAP users with full password management capabilities.
Entra ID (Cloud-Only): Users existing solely in Microsoft Entra. These users utilize Entra-native identifiers but currently do not support Veridium-based password changes.
Hybrid User: The most robust model, linking an on-prem
objectSidto a cloudobjectIdvia a stable "Microsoft Login ID".
Configuration: The Hybrid Binding Process
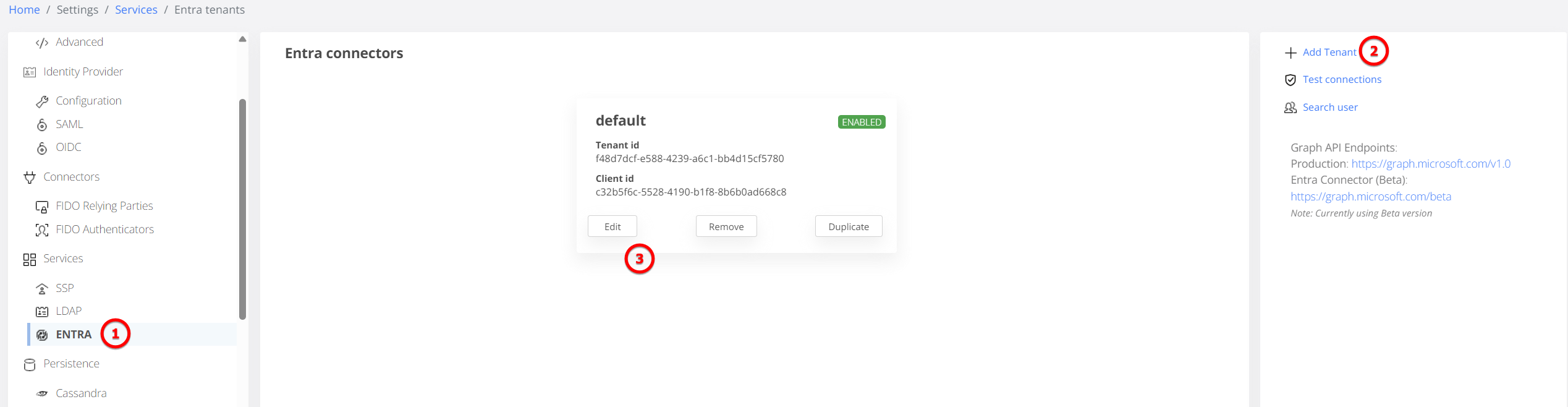
Step 1: Entra ID Connector Setup
Navigate to Admin Manager > Settings > Directory Services > Entra ID to define the cloud interface:
General Settings: Enter the Tenant Unique Identifier, Client ID, and Tenant ID provided by your Azure/Entra App Registration.
Debugging: Enable "Http Debug Enabled" during initial setup to capture detailed logs of the communication between VeridiumID and Microsoft Graph.
FIDO2 Configuration: Set the "FIDO2 Creation Options challenge timeout" (default is 5 minutes) to define the window for cloud-based biometric registration.
Step 2: Attribute Mapping & Extended Attributes
Proper mapping is essential for identity resolution and JWT token generation
Standard Mapping: Ensure the
Internal Attributelist correctly points to Entra fields:Username →
userPrincipalNameID →
idGroups →
memberOf
This table defines which Entra attribute maps to which internal model attribute.
Internal Attribute | Entra Attribute |
|---|---|
ID | id |
Mobile | mobilePhone |
Groups | memberOf |
User Account Control | accountEnabled |
Username | userPrincipalName |
Line Manager | manager |
First Name | givenName |
Last name | surname |
Microsoft Login ID |
Extended attributes allow admins to map additional Entra fields not included in the standard model, as the example below.
Internal Attribute | Entra Attribute |
|---|---|
entraId | id |
userPrincipalName | entraUpn |
userPrincipalName | userPrincipalName |
Critical JWT Mapping: You must map
entraUpnto theuserPrincipalNamein the Extended Attributes section. This field is specifically required to populate theentraUpnclaim in JWT tokens used by downstream applications.
Step 3: Enabling Hybrid Directory Sync (LDAP Binding)
To link on-premises users to their cloud counterparts, you must modify your LDAP configuration:
Toggle Hybrid Sync: Enable the "Enable Hybrid Directory Sync" option in the LDAP settings.
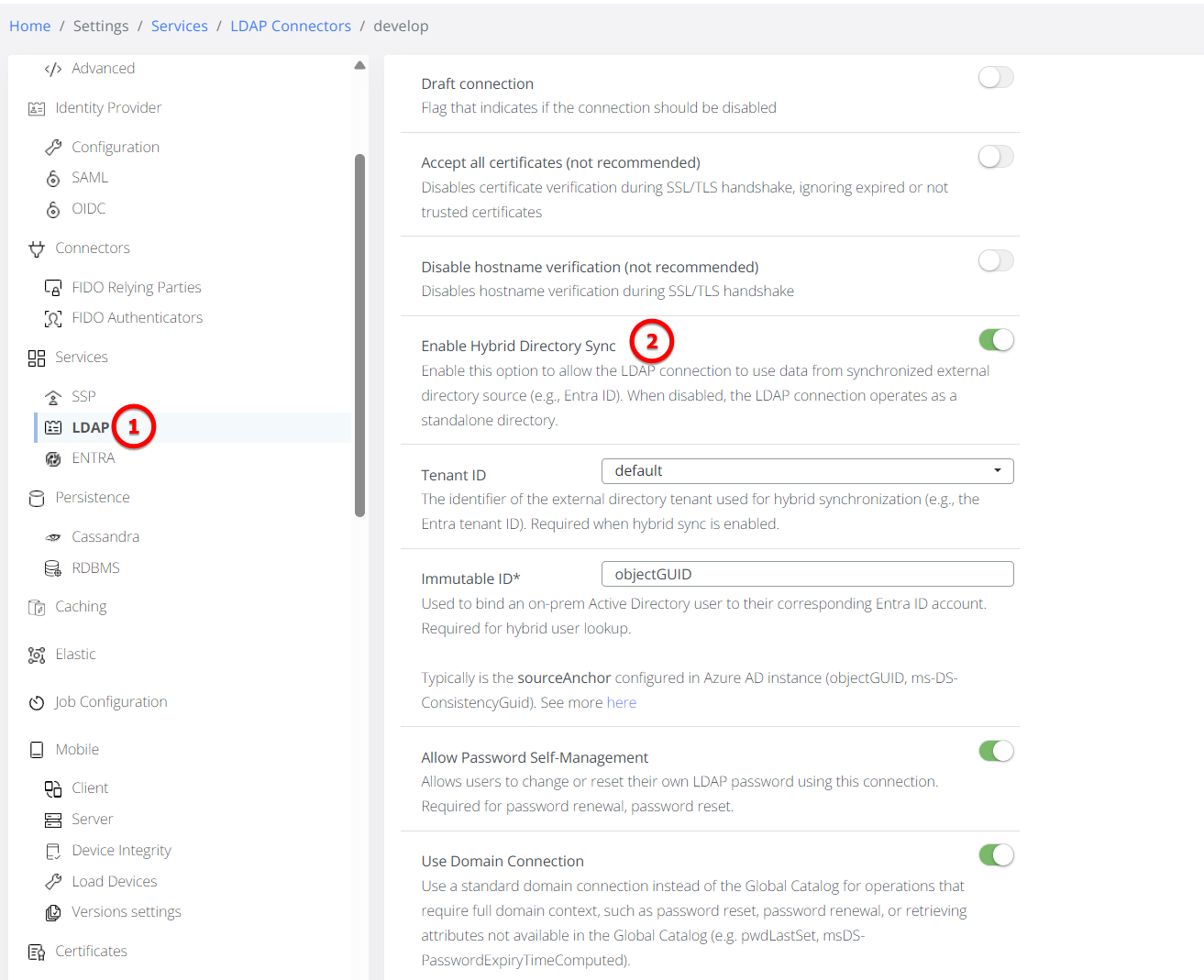
Select Tenant: Choose the corresponding Tenant ID from your configured Entra connectors.
Immutable ID Definition: Use
objectGUIDto bind the on-prem AD user object to the Entra account. This ensures a stable link even if a user's email or name changes.
Critical Technical Requirements & Limitations
NameID Attribute Mapping: When configuring SAML or OIDC applications, the NameID attribute must be mapped to
userPrincipalName. Microsoft Entra ID does not support searching bymailorsAMAccountNamefor these lookups.LDAP Dependency: For Hybrid users, the system treats LDAP as the authoritative primary source. If LDAP connectivity is down, hybrid users will face enrollment and authentication failures, as the system cannot verify the primary data source.
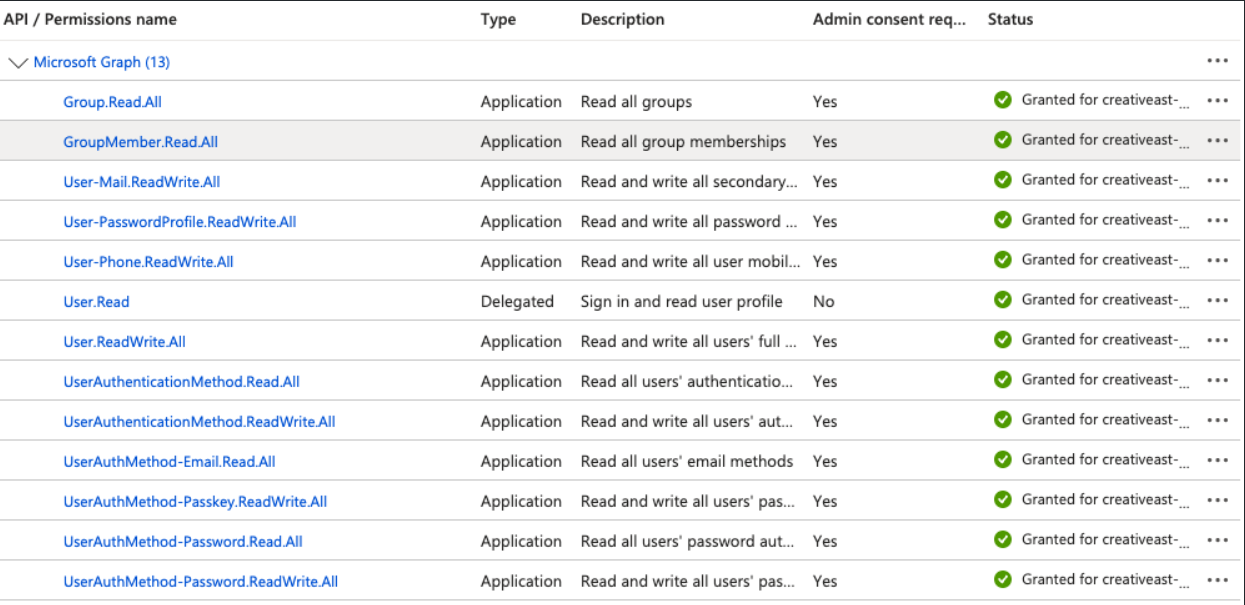
API Permissions: The Entra App Registration requires exactly 12 Microsoft Graph API permissions (e.g.,
User.Read.All,Group.Read.All,UserAuthenticationMethod.ReadWrite.All) with granted Admin Consent.Password Management limitationsz:
Entra-Only Users
⚠️ Cannot Authenticate with Entra Password: Entra-only users cannot use their Entra ID password for authentication in the system
⚠️ No Self-Service Password Reset: Cannot reset passwords through the self-service portal
⚠️ No Password Change: Cannot change passwords via the system
Hybrid Users
✅ Can authenticate using Active Directory password
✅ Can use self-service password management (when LDAP is available)
⚠️ Entra password is not used for authentication
Active Directory Users
✅ Full password management capabilities
✅ Self-service password reset available
✅ Password change through portal
Authentication & Enrollment Behavior
Operation | User Type | Requires LDAP? | Requires Entra API? |
Enrollment | Hybrid | Yes (Authoritative) | Yes |
Enrollment | Entra-Only | No | Yes |
Authentication | Hybrid | Yes (Password source) | No (Attributes may fail) |
Password Change | Hybrid | Yes | No |
Scenario | LDAP Status | Entra Status | Result |
|---|---|---|---|
Hybrid Enrollment | Up | Up | Success: Merges data from both sources. |
Hybrid Re-enrollment | Down | Up | Failure: "No LDAP connection for hybrid user found".+1 |
Entra Authentication | Any | Up | Success: Uses Microsoft Graph API for validation. |
Hybrid Authentication | Up | Down | Partial Success: Authenticates via LDAP; cloud-specific extended attributes may be missing. |
UI Audit & Impact Analysis
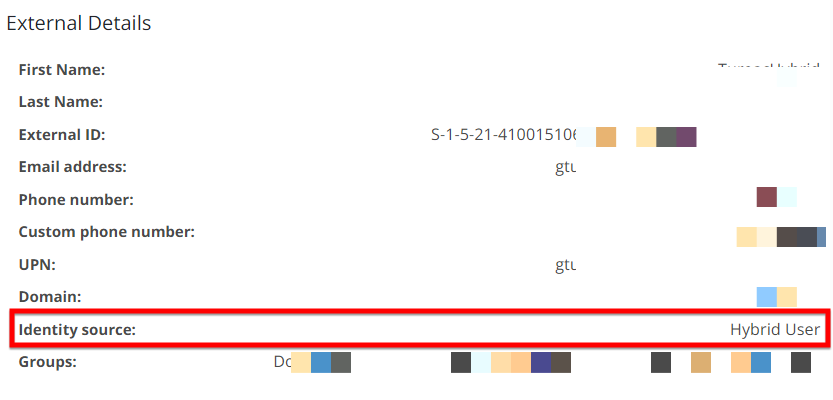
UI Clarity: The "Identity Details" screen has been updated to include a dedicated "External Details" panel. This allows helpdesk agents to immediately see the UPN, Domain, and Identity Source (Hybrid, EntraID or Active Directory), reducing mean-time-to-resolution (MTTR) for login issues.
Security Impact (High): Unified search prevents identity fragmentation. By merging cloud and on-prem data, security policies can be applied consistently to a single user identity rather than managing separate personas.
Technical Impact (Medium): Administrators must audit existing Entra App Registrations to ensure the 12 required Microsoft Graph API permissions (including
Group.Read.All,User.Read.All, andUserAuthenticationMethod.Read.All) are granted and have Admin Consent.