Support for adding custom claims in the OIDC access token
Context
There is a need to have custom claims in the access token generated by the OIDC plugin. For this new UI fields were added in the OIDC applications in order to allow users to choose what custom attributes to add.
Configuration in Veridium server
From the OIDC application page (either edit or create new), go to the Advance tab.
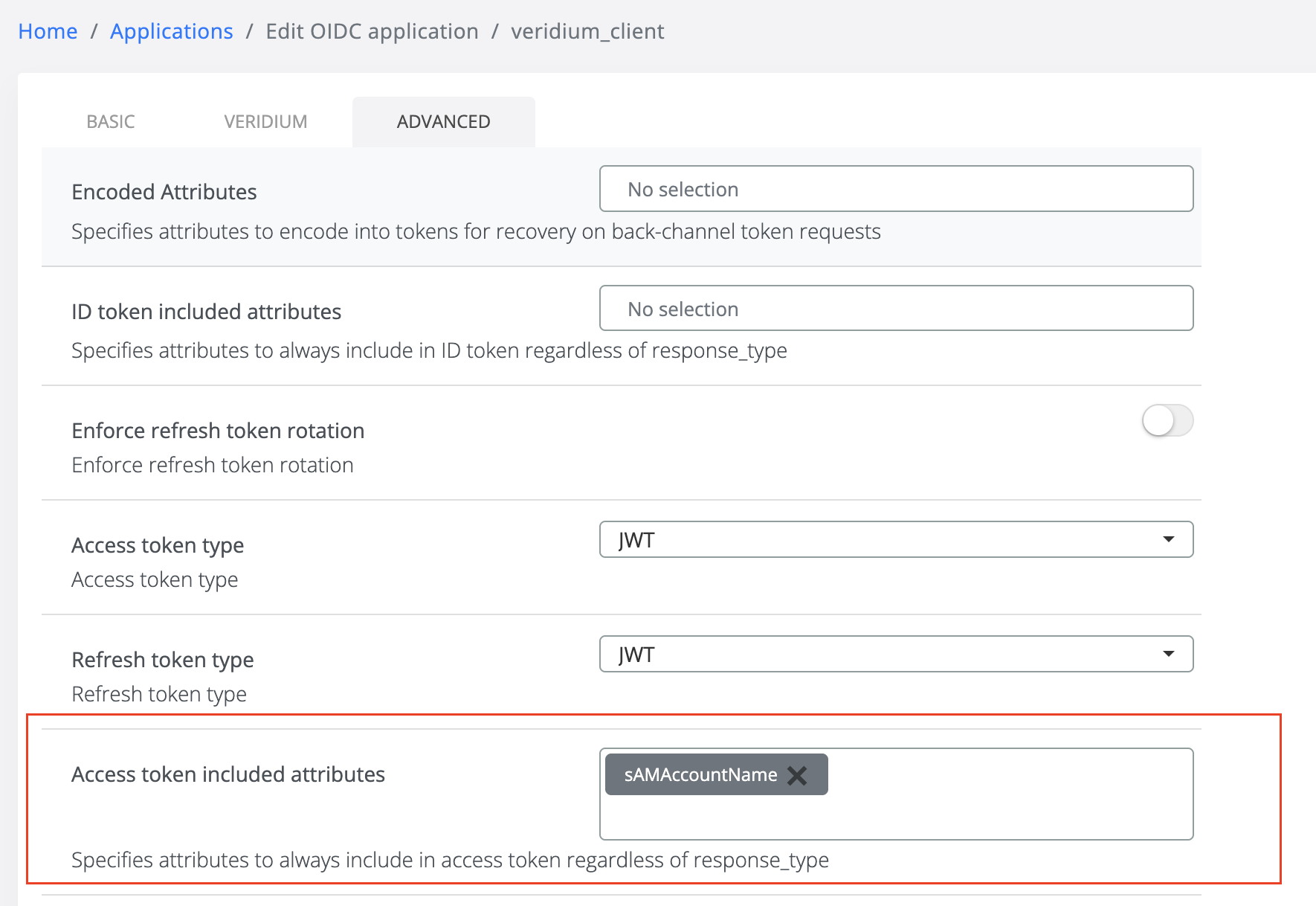
With this selection, we can specify what kind of attribute to be present in access token as a claim directly.
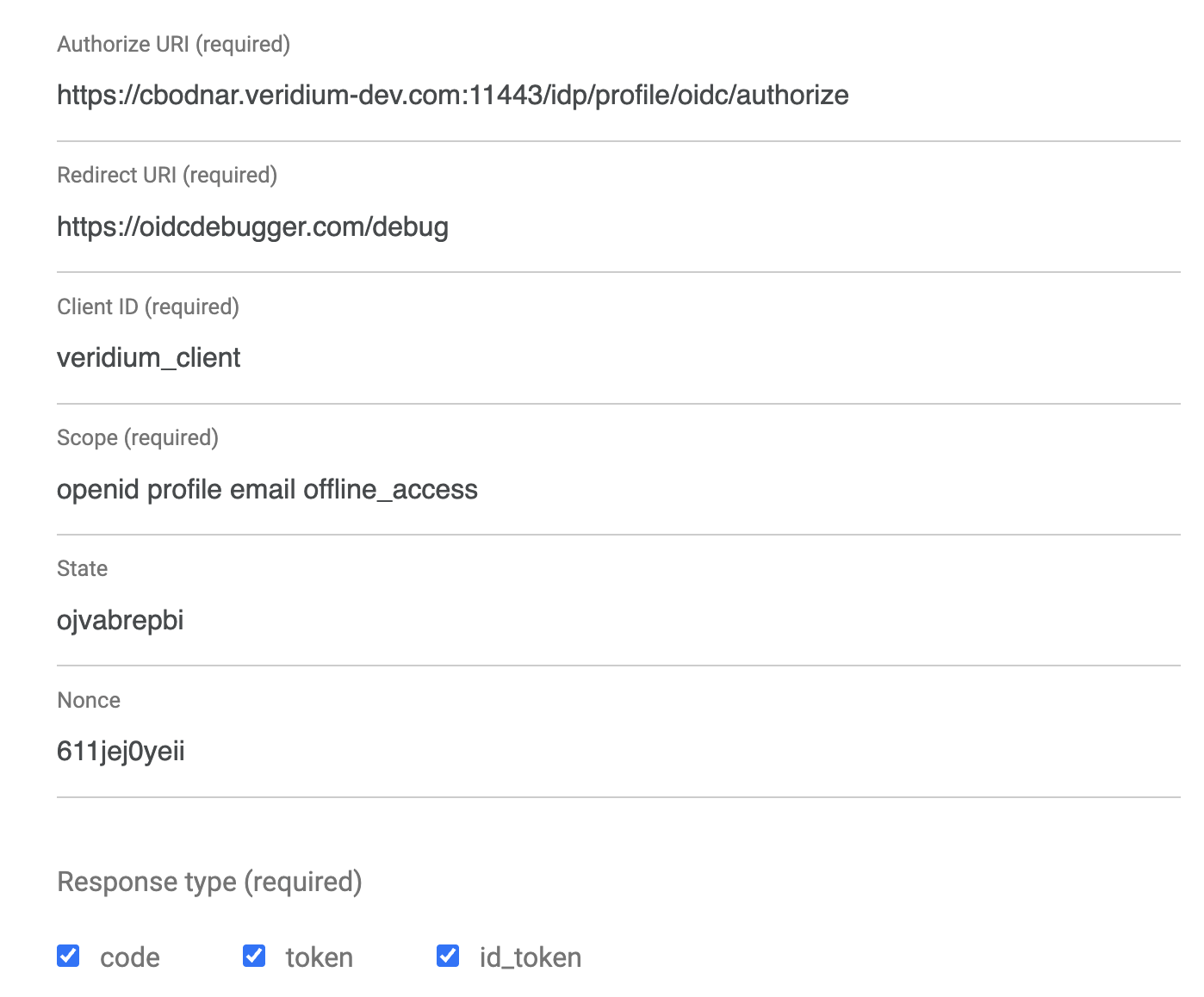
Having this set, we can start an OIDC authorization flow code and verify if the access token will have the requested attribute:
With a client of OIDC, for example OIDC debugger, we can start a OIDC flow like authorization flow:
Sending this request and successfully authenticate it will redirect to OIDC debugger page where we can see the access token, in the decode JWT from access token we can spot the requested custom claim from admin side:
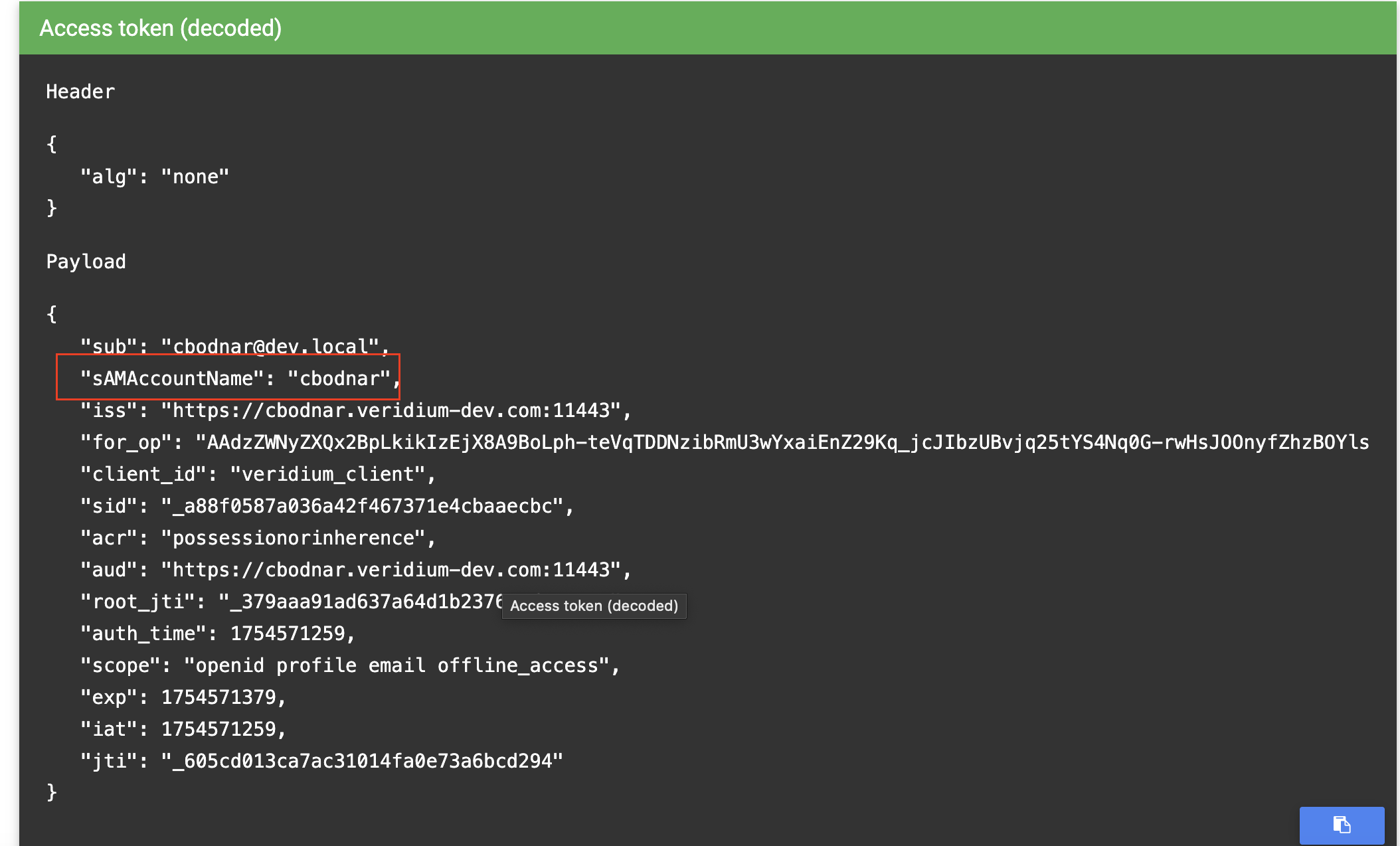
This is for SSO part, however the client wants this custom claim to be present in the next token:
Copying the authorization code from OIDC debugger response and make a postman call with it for exchanging the tokens, then we will see the custom claim in the OAuth.Token step.
https://cbodnar.veridium-dev.com:11443/idp/profile/oidc/token?grant_type=authorization_code&client_id=veridium_client&client_secret=secret&redirect_uri=https://oidcdebugger.com/debug&code=AAdzZWNyZXQxVpVYHy9sgtGRkfDT-HaxWQNfQXV9AVcAfiCP_amUyMMA0xHlqeArDd9dYD7Obyry5ywnSCDiMRYgtcf0fUei1h2FfHQR0WIK-9MzBcpvU4HtJXpg55A1PHHwIslDfAl75TvDSXTxWvyi67Eu0E_qz7LId162c07Q2YePy9_IQPU7Apz6iSxyK6fDlckHZZN5qPxZFE466rNHMbVjQnb5X9iNZwIElglKK6PGPvWpBd5YI1pJKDbhNHONXIxGllzgVMPaPLdu-CqofBm-P8NuoTAyVr6D7yCl2lLFAa1rxXQ5f5UmcQQpuW_a6lBxrce4AkItC5j2cq1kD49KihHrDPLQ1lgZK6IJ9M3WONW-zq7Rtlg_5A1ymAM7RfQAnBu-YveWbg93-hgf3ExfM-73Bc-19rd6QHVQeax00NrCoCOGGCH-67iIQOX7aPGYhp8s_2sc_buveagEAVfa2qzS_qkQR8JXXJGB4kiHeEQI_xkv0U069etZg5xJ6Caw7ZPON_51GJB_kMzsNzD2BmoSf6BgvDIHKu4YLJvA2LNRty9n52IF1ELyQq0TSbBrA5YPn6Ph_r87NCLrqQrNA7qFvd-c-vKGnww9NBPX2W-mjUdzvQwill result in
"access_token": "eyJraWQiOiJaR1ZtWVhWc2RGSlRRVk5wWnc9PSIsInR5cCI6ImF0K2p3dCIsImFsZyI6IlJTMjU2In0.eyJzdWIiOiJjYm9kbmFyQGRldi5sb2NhbCIsInNBTUFjY291bnROYW1lIjoiY2JvZG5hciIsImlzcyI6Imh0dHBzOi8vY2JvZG5hci52ZXJpZGl1bS1kZXYuY29tOjExNDQzIiwiZm9yX29wIjoiQUFkelpXTnlaWFF4Y2pDMm8xa3pZVXJXbW1DaDlGVFM0MG5kYmVQbm9aTkVCdVNjQW02bGJxa3k2VVZNLUJlVG45OEFQLThEb1Zud2FnVV9CNzVaNXIydnBybHNnN0tqV2h5bklIazZ4UTJTd1V2RUJpbVNsb1YyX01VekVTbVVNb0VFNnZ2OHFXelR1NHpld1JJSTZLeWo4dU5xZ0RJYTJnZkxqd3lKaVFkU05aaTFNSDJYUFRqWS1YaUtHODZOdW13OTN1WWVYRHM3QlA3VVFQU2tVbklkUHBPc0dqX0FubGllNk1vVDE5Y2VMMHI3Y2l3M19uNFcxV01uanlIRVduR2MtakZUNTQwV19DVlk2MkhGcFpJX3Y3Z3F1ZnFMR05tNHBycUY1YzlOcXN2RnFHYjNqOU1CUS1QcXdlWllBWWFEZjFJQkFTejdaWlpSU293NXdWRG9qX0VIIiwiY2xpZW50X2lkIjoidmVyaWRpdW1fY2xpZW50Iiwic2lkIjoiX2E4OGYwNTg3YTAzNmE0MmY0NjczNzFlNGNiYWFlY2JjIiwiYWNyIjoicG9zc2Vzc2lvbm9yaW5oZXJlbmNlIiwiYXVkIjoiaHR0cHM6Ly9jYm9kbmFyLnZlcmlkaXVtLWRldi5jb206MTE0NDMiLCJyb290X2p0aSI6Il8zNzlhYWE5MWFkNjM3YTY0ZDFiMjM3NjRlZDQ4YzAzNCIsImF1dGhfdGltZSI6MTc1NDU3MTI1OSwic2NvcGUiOiJvcGVuaWQgcHJvZmlsZSBlbWFpbCBvZmZsaW5lX2FjY2VzcyIsImV4cCI6MTc1NDU3MTUyNywiaWF0IjoxNzU0NTcxNDA3LCJqdGkiOiJfZWZkYjRkMTkwMDNlZTUwOWU2ZDQyNzhlNjQxZDkxODkifQ.olB8B4orvHxYpQgNkLdZIzdSd0e2Nn6IGDPQepZ-u_SZNnWqe7tQYQ27csfRTzr-WQXsfm8TSRnLZi3l6Id6B7GVYh-CNYTXTBborTrpWa9XvVY-IXZCwmy5i16_Y_xXyHQopNephterD_NVtJzCvYJbb5k0zpHpYvCQZ7v65M0X2UcmWmU37iEcvDGk-t0xyH8lMae54Cm2KRo6vxgUQ7KpTqKGlNgdX4N6W2-CpJQRYopAVrLmAvUV579Jzv0Kdgd_Ln5GmF1FHULTAbKGl2AtpRDiozj2kR3XY51x6ZgTe-5JhyF696bqUytJ-rsv5zu1g1dCVsH_RNRVuCXrUQ"and decoding this will have same result as above.
