Veridium RA - Special configuration - not to allow attributes in certificate request
Configuration
This feature is available in version 3.7 or later
In case there is no option to allow to supply attributes in certificate request, the following steps needs to be done:
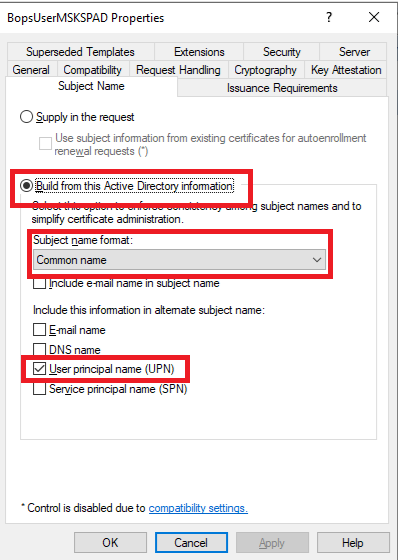
Configure certificate template to build Subject Name using Active Directory information. Minimally, you need to set following:
Open RA web.config - by default is is: C:\Program Files\VeridiumID\RAEPServer\RaWebApp\web.config
Set following keys:
Key name | value |
|---|---|
AddAccountName | needs to be set to true - to add requestor name into a request. |
ADShortDomain | short domain name - must be possible to redolve by DNS to get DC |
AD_LDAP_Domain | DN of the AD - see example |
Example:
<add key="AddAccountName" value="true" />
<add key="ADShortDomain" value="dev.local" />
<add key="AD_LDAP_Domain" value="LDAP://DC=dev,DC=local" />Configuration Verification
Take a event log from RA - dusing certificate enrollment the following keys can be found:
adding name to request: <domain>\\<sAMAccountName>
RequestorName1 <domain>\\<sAMAccountNAme>
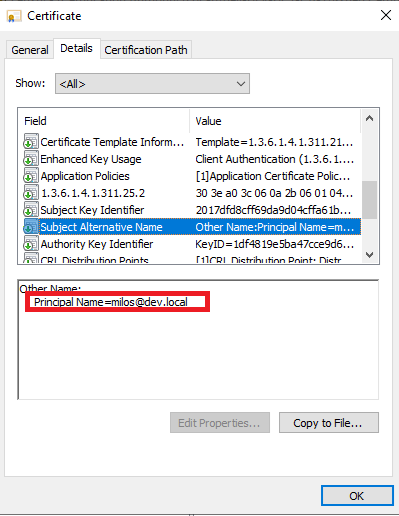
RequestorName2 <domain>\\<sAMAccountNAme>When certificate request will be parsed, the RequesterName: <domain>\<sAMAccountName> can be found (example):
================ Begin Nesting Level 1 ================
CMS Certificate Request:
Tagged Attributes: 3
Body Part Id: 4
1.3.6.1.5.5.7.7.8 CMC Extensions
Value[0]:
Data Reference: 0
Cert Reference[0]: 1
Extensions: 4
1.3.6.1.4.1.311.21.7: Flags = 0, Length = 2f
Certificate Template Information
Template=1.3.6.1.4.1.311.21.8.16126515.12376282.4737968.10783856.847026.134.1506958.12401871
Major Version Number=100
Minor Version Number=126
2.5.29.37: Flags = 0, Length = 18
Enhanced Key Usage
Client Authentication (1.3.6.1.5.5.7.3.2)
Smart Card Logon (1.3.6.1.4.1.311.20.2.2)
2.5.29.15: Flags = 1(Critical), Length = 4
Key Usage
Digital Signature (80)
1.3.6.1.4.1.311.21.10: Flags = 0, Length = 1c
Application Policies
[1]Application Certificate Policy:
Policy Identifier=Client Authentication
[2]Application Certificate Policy:
Policy Identifier=Smart Card Logon
Body Part Id: 3
1.3.6.1.4.1.311.10.10.1 CMC Attributes
Value[0]:
Data Reference: 0
Cert Reference[0]: 1
1 attributes:
Attribute[0]: 1.3.6.1.4.1.311.21.20 (Client Information)
Value[0][0], Length = 30
Client Id: = 5
ClientIdDefaultRequest -- 5
User: DEV\DEV-DC1$
Machine: dev-dc1.dev.local
Process: w3wp.exe
Body Part Id: 2
1.3.6.1.5.5.7.7.18 Reg Info
Value[0]:
RequesterName: DEV\milos
Tagged Requests: 1
CMC_TAGGED_CERT_REQUEST_CHOICE:
Body Part Id: 1In the resulting user certificate, correct user UPN must be visible: