(v3.7)Microsoft Entra as PRT authority
This feature provides SSO when Veridium Windows Credential Provider is enabled and used in during logon session.
This document will provide a short procedure in order to enable and configure stage rollout feature along with Microsoft CBA (certificate based authentication using an internal CA). The stage rollout feature allows to enable different authentication methods for certain users, thus preparing the migration of internal users to the cloud.
In order to achieve this, you must perform the following steps:
Export your internal CA and import it in Microsoft Entra ID
Access your internal PKI server and open the Certification Authority management console (Start->type certification authority and click enter):
Right click the CA name and select Properties:
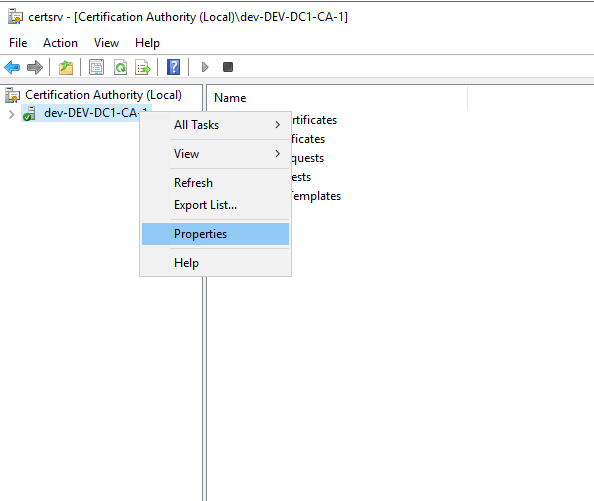
In the next window click on View Certificate:
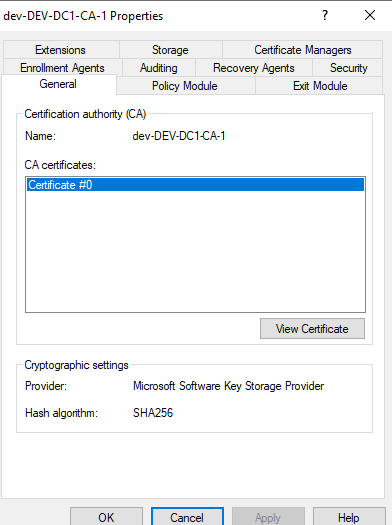
In the Certificate window, switch to Details tab and click on Copy to File:
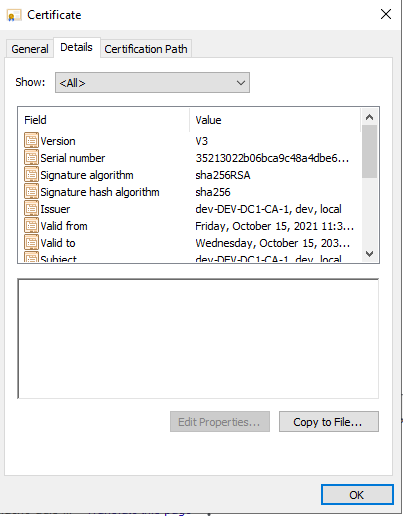
In the following window click on Next.
Select Base-64 as format and click Next:
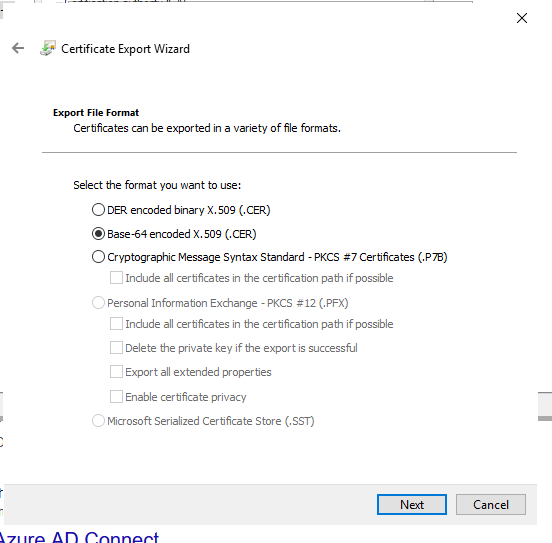
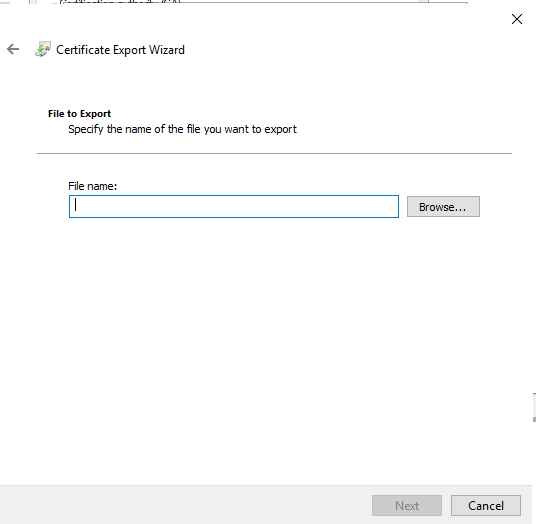
Type in a file name and save the exported file.
Login to portal.azure.com and select Entra ID:
In the left menu scroll down until you find the Security menu and click on it:

In the Security menu select Certificate Authorities:
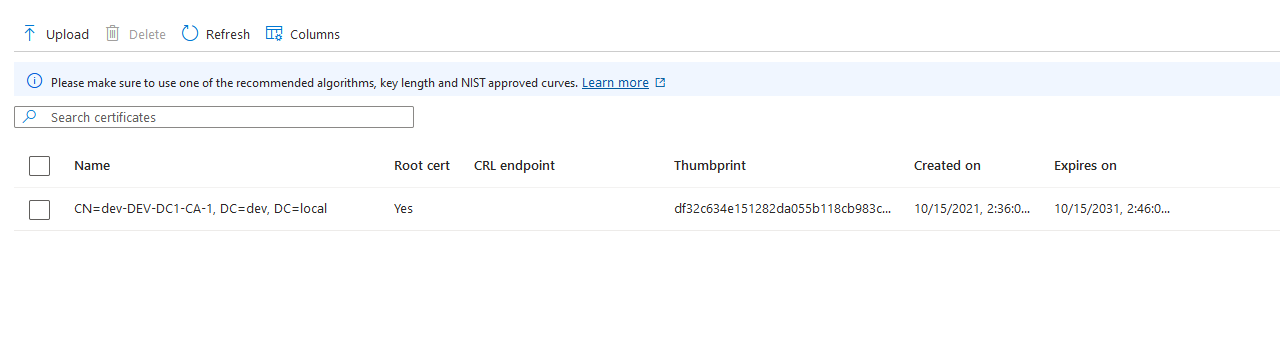
Click on Upload and import the exported CA:
Enable stage rollout feature
Login to entra.microsoft.com and, in the lef menu, click on Hybrid management->Microsoft Entra Connect:
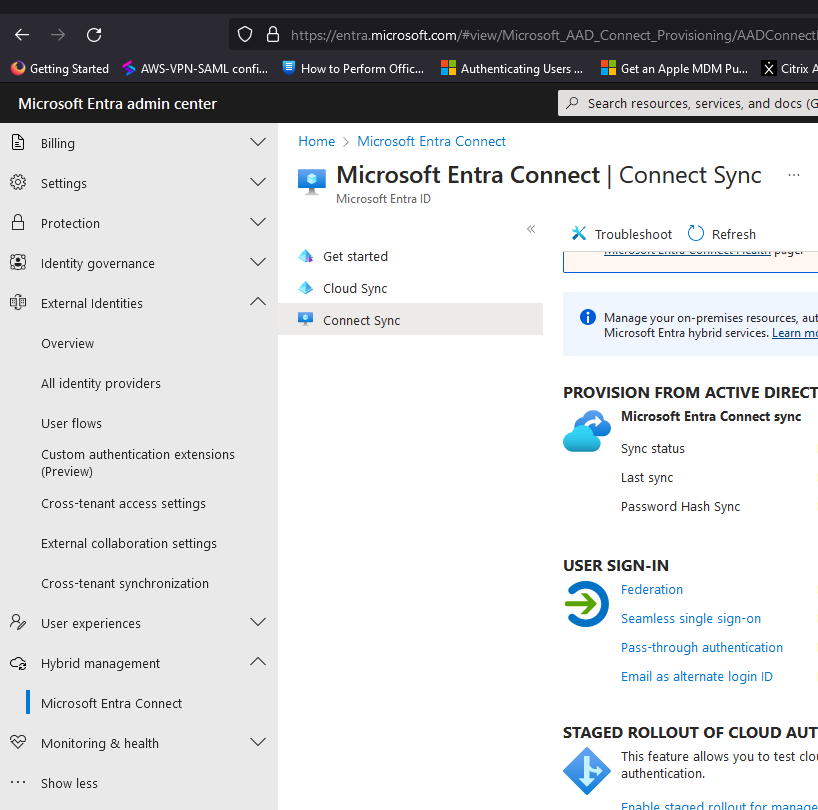
On the right side of the page scroll down until you find the STAGED ROLLOUT OF CLOUD AUTHENTICATION section, then click on Enable staged rollout for managed user sign-in:
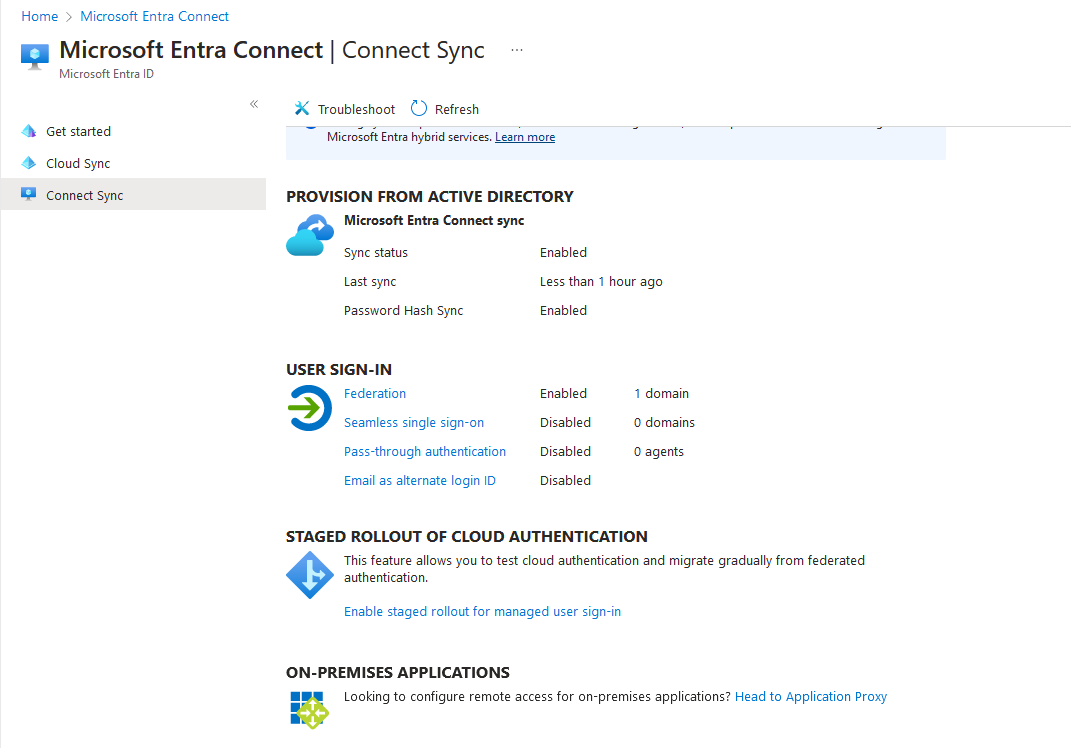
In the Enable staged rollout features window, set Password Hash Sync and Certificate-based authentication to On:
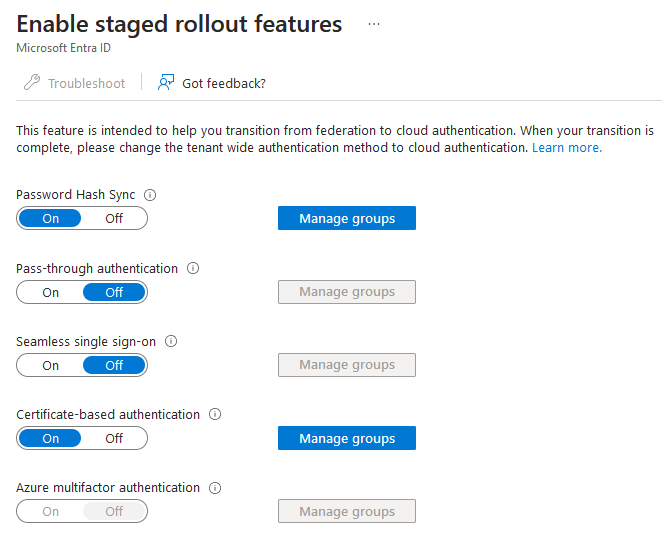
Click on Manage groups for both options and select a group containing the users for which you want to enable these features by clicking on Add Groups:
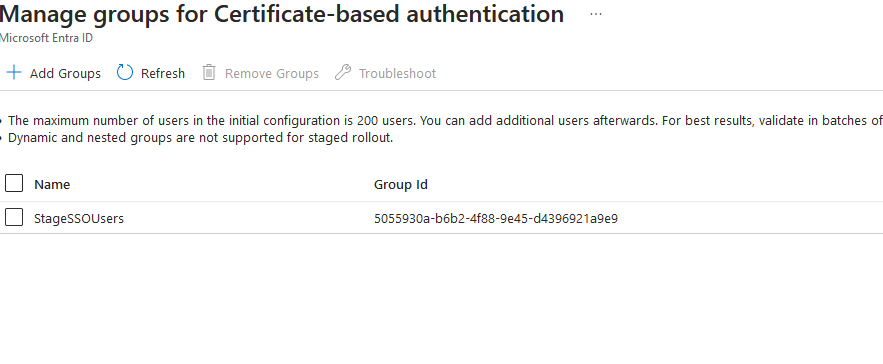
Enable certificate based authentication at tennant level
Access portal.azure.com and then Microsoft Entra ID:
Scroll down in the menu on the left and then click on Security:
In the Security page click on Authentication Methods:
In the Authentication Methods select Certificate based authentication:
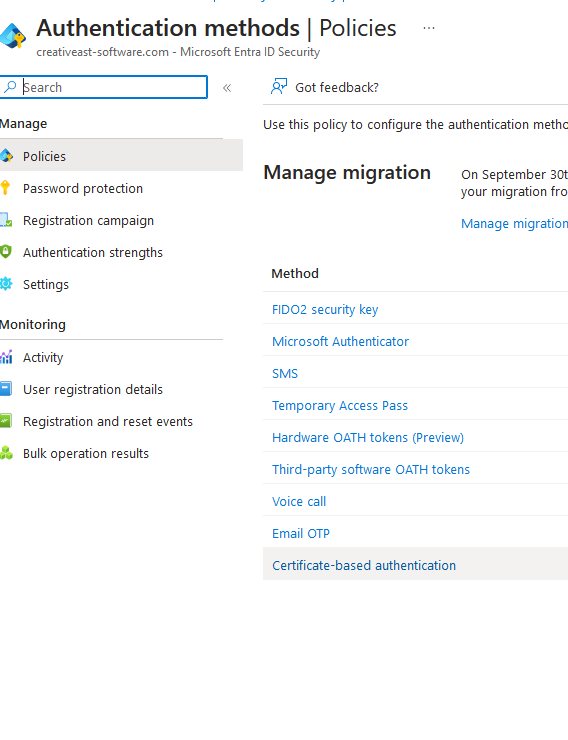
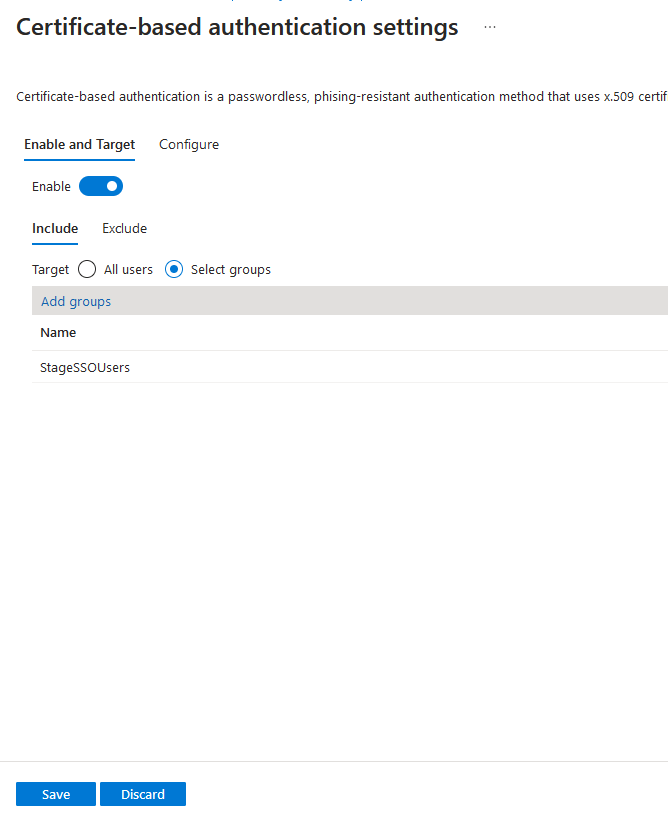
In the Certificate-based authentication settings window click on the radion button to enable the feature, then click on Select groups and add the group of users for which you want the enable this method. After performing all modifications, click on Save:
Test the configuration
Login to the hybrid joined machine with a user which is a member of the group configured in the staged rollout feature. From a command prompt window, run the command dsregcmd /status . If everything is ok, the output should look l
+----------------------------------------------------------------------+
| Device State |
+----------------------------------------------------------------------+
AzureAdJoined : YES
EnterpriseJoined : NO
DomainJoined : YES
DomainName : DEV+----------------------------------------------------------------------+
| Device Details |
+----------------------------------------------------------------------+
DeviceId : 0db6819e-e5c4-4420-852a-554aa9f464e1
Thumbprint : 18DD637241D491E03D08CCEE2137E3EC59670BF6 DeviceCertificateValidity : [ 2023-11-23 14:00:57.000 UTC -- 2033-11-23 14:30:57.000 UTC ]
KeyContainerId : 20e7aa08-549c-4cda-9d3d-8c94c6d47c14
KeyProvider : Microsoft Software Key Storage Provider
TpmProtected : NO
+----------------------------------------------------------------------+
| Tenant Details |
+----------------------------------------------------------------------+
TenantName : creativeast-software.com
TenantId : f48d7dcf-e588-4239-a6c1-bb4d15cf5780
Idp : login.windows.net
AuthCodeUrl : <https://login.microsoftonline.com/f48d7dcf-e588-4239-a6c1-bb4d15cf5780/oauth2/authorize>
AccessTokenUrl : <https://login.microsoftonline.com/f48d7dcf-e588-4239-a6c1-bb4d15cf5780/oauth2/token>
MdmUrl : <https://enrollment.manage.microsoft.com/enrollmentserver/discovery.svc>
MdmTouUrl : <https://portal.manage.microsoft.com/TermsofUse.aspx>
MdmComplianceUrl : <https://portal.manage.microsoft.com/?portalAction=Compliance>
SettingsUrl :
JoinSrvVersion : 1.0
JoinSrvUrl : <https://enterpriseregistration.windows.net/EnrollmentServer/device/>
JoinSrvId : urn:ms-drs:enterpriseregistration.windows.net
KeySrvVersion : 1.0
KeySrvUrl : <https://enterpriseregistration.windows.net/EnrollmentServer/key/>
KeySrvId : urn:ms-drs:enterpriseregistration.windows.net
WebAuthNSrvVersion : 1.0
WebAuthNSrvUrl : <https://enterpriseregistration.windows.net/webauthn/f48d7dcf-e588-4239-a6c1-bb4d15cf5780/>
WebAuthNSrvId : urn:ms-drs:enterpriseregistration.windows.net
DeviceManagementSrvVer : 1.0
DeviceManagementSrvUrl : <https://enterpriseregistration.windows.net/manage/f48d7dcf-e588-4239-a6c1-bb4d15cf5780/>
DeviceManagementSrvId : urn:ms-drs:enterpriseregistration.windows.net+----------------------------------------------------------------------+
| User State |
+----------------------------------------------------------------------+
NgcSet : NO
WorkplaceJoined : NO
WamDefaultSet : YES
WamDefaultAuthority : organizations
WamDefaultId : <https://login.microsoft.com>
WamDefaultGUID : {B16898C6-A148-4967-9171-64D755DA8520} (AzureAd)+----------------------------------------------------------------------+
| SSO State |
+----------------------------------------------------------------------+
AzureAdPrt : YES
AzureAdPrtUpdateTime : 2023-12-14 10:50:03.000 UTC
AzureAdPrtExpiryTime : 2023-12-28 10:50:24.000 UTC
AzureAdPrtAuthority : <https://login.microsoftonline.com/f48d7dcf-e588-4239-a6c1-bb4d15cf5780>
EnterprisePrt : NO
EnterprisePrtAuthority : Note that the SSO section stated that AzureAdPrt has been issued and the authority is login.microsoftonline.com. At this point, SSO is in place for Office 365 apps and any/if configured AzureAD custom apps.
