(v3.7)Microsoft ADFS as PRT authority
This document will describe the necessary steps you need to perform in order to obtain a single sign-on experience across Azure AD applications (in this case Office 365 apps but the SSO extends also to custom defined apps). SSO is achieved through a PRT (Primary Refrash Token) issued, in this case, by the intenal ADFS server. Single sign-on is possible on hybrid joined machines, meaning they are joined to an internal Active Directory domain as well as to an Azure AD one.
The procedure is as follows:
Federate the authentication to the ADFS server
This can be done in two ways:
Via powershell command:
POWERSHELL# Obtain authorization for Microsoft Entra Connect-MsolService (to connect to the Microsoft tennant) # Configure federation using AD FS Set-MsolDomainAuthentication –DomainName creativeast-sw.com -FederationBrandName <adfs-url> -Authentication Federated -PassiveLogOnUri https://<adfs-url>/adfs/ls/ -MetadataExchangeUri "https://<adfs-url>/adfs/services/trust/mex" -SigningCertificate <base64_certificate> -IssuerUri "https://<adfs_host>/adfs/services/trust/" -ActiveLogOnUri "https://<adfs-url>/adfs/services/trust/2005/usernamemixed" -LogOffUri "https://<adfs-url>/adfs/ls/" -PreferredAuthenticationProtocol WSFED
The above command is just an example. You should adjust all the parameters according to your environment.
Using the Azure AD Connect tool:
Open Azure AD Connect and select configure:
In the next window select Manage Federation:
Select Federate Azure AD domain:
Enter your Microsoft tennant credentials:
Next enter your ADFS admin credentials:
Select the domain you want to federate, then click Next:
On the AzureAD Trust page click Next:
Click on Configure to proceed:
After the configuration process is done, click on Finish.
Open the Azure AD Connect application again. click on Configure.
Select Change user sign-in and click Next:
Enter your Azure AD credentials and click Next:
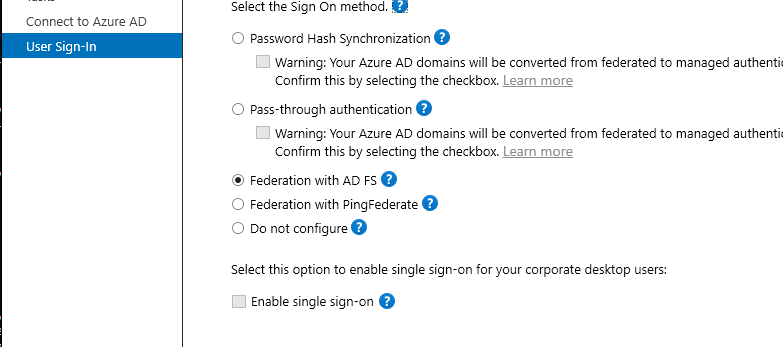
Choose Federation with ADFS and complete the wizard:
Configure Hybrid Azure AD join and device writeback
Open the Azure AD Connect tool and click on Configure:
Select Device options and click Next:
In the Overview window click on Next.
In the Connect to Azure AD window enter your Azure AD credentials and click Next:
Select Configure Hybrid Azure AD join and click Next:
Select Windows 10 or later and click Next:
In the next window, tick the domain name, then click on Add next to Enterprise Admin and enter enterprise admin credentials. After entering the credentials, click on Next:
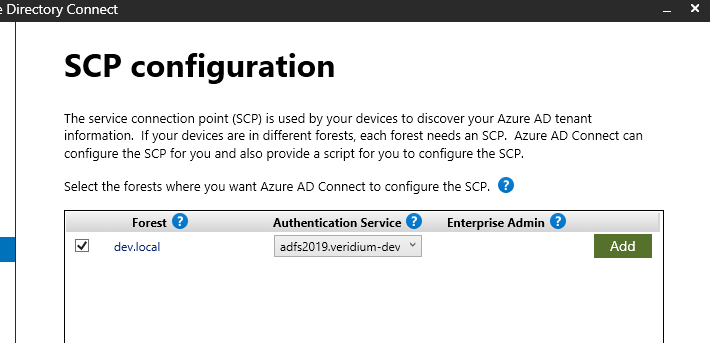
Next enter ADFS admin credentials and complete the wizard:
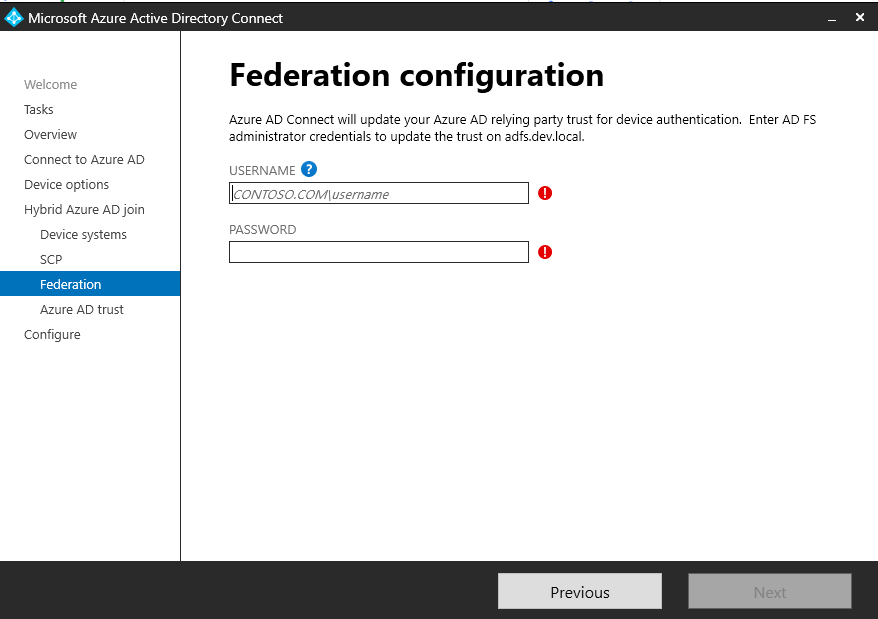
Run the installation wizard again. Select Configure device options from the Additional Tasks page and click Next.
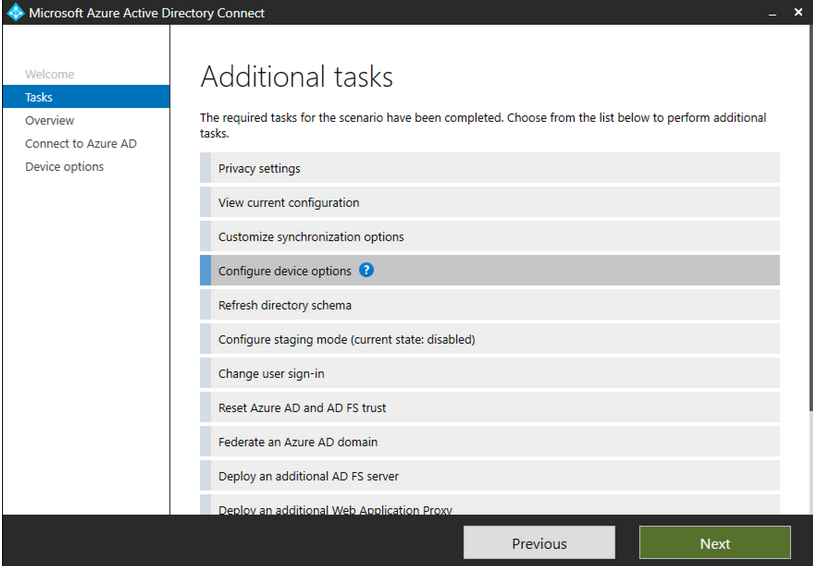
On the device options page, select Configure device writeback. Click on Next to move to the next page in the wizard.
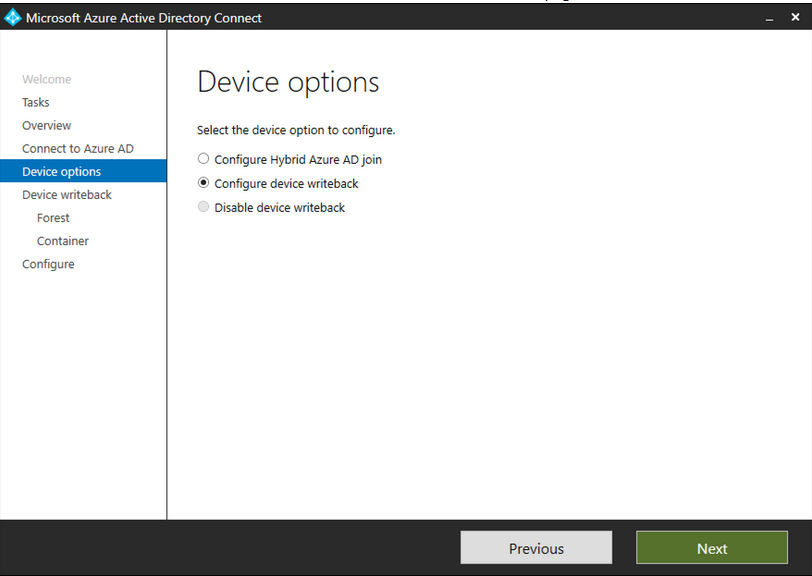
On the writeback page, you'll see your domain as the default Device writeback forest. Click Next:
In the next window, provide Enterprise Admin credentials and click on Next:
Finish the configuration wizard.
ADFS configuration
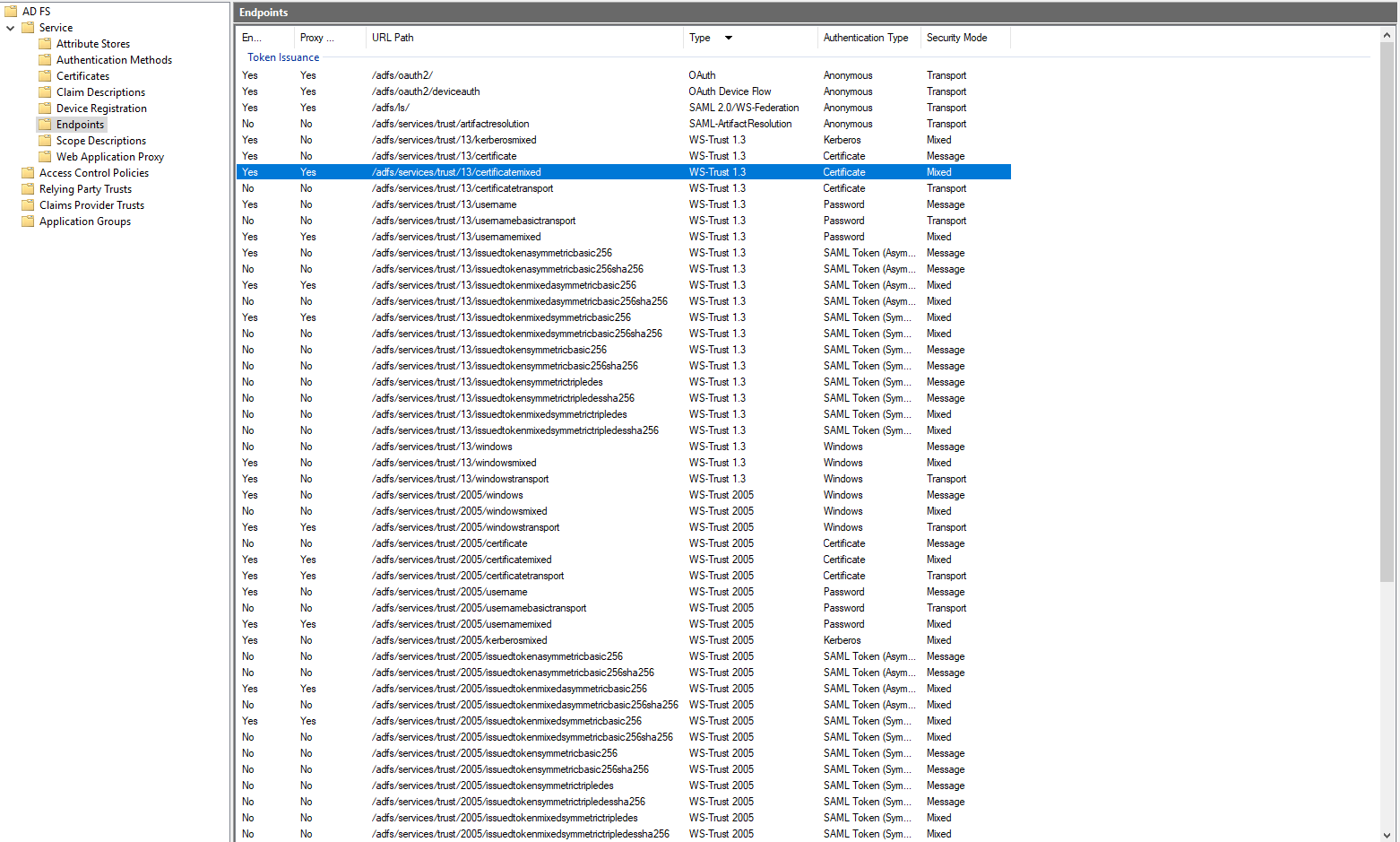
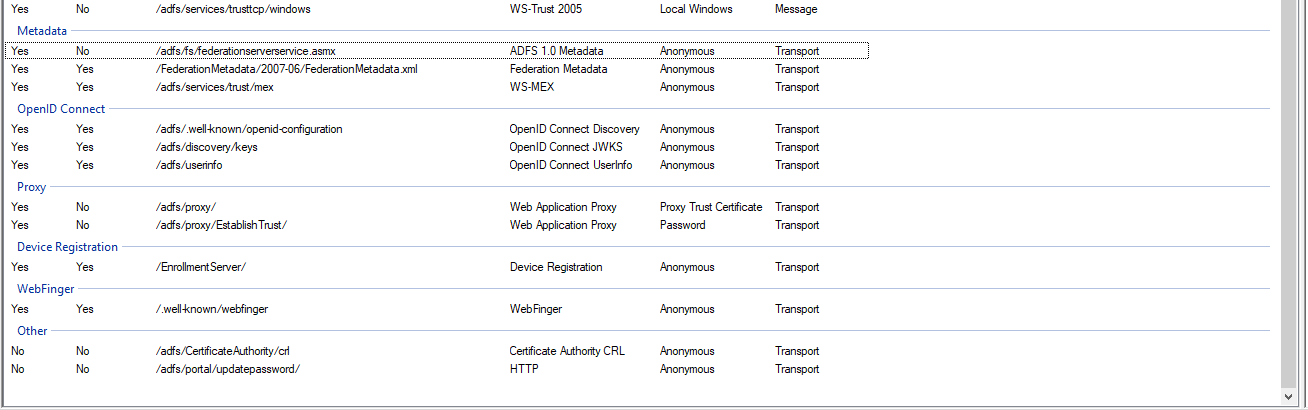
Access AD FS Management console, go to Endpoints container and make sure you have the following configuration:
Enable Device authentication and Windows Authentication for the intranet/extranet. For this go to Service, Authentication Methods and click on Edit Primary Authentication Methods:
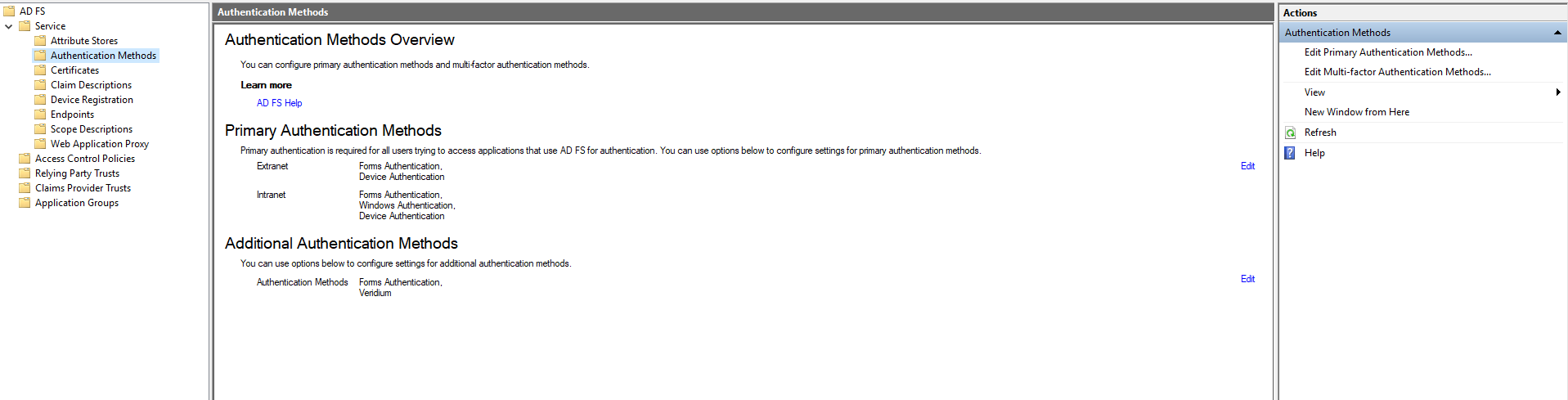
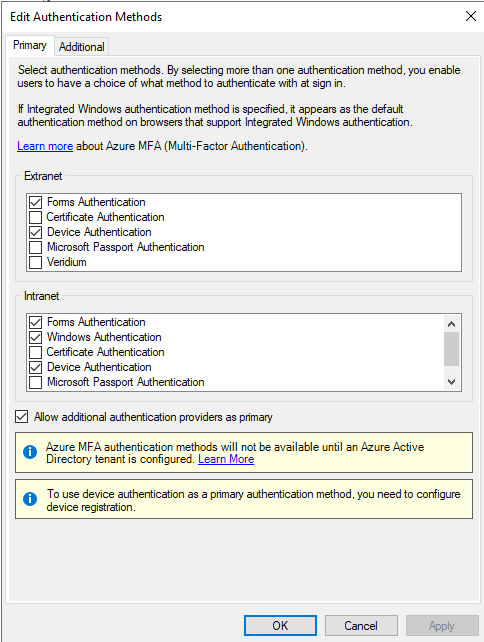
In the next window select Device Authentication from the lists, then click Apply and Save:
Hybrid joined machine settings
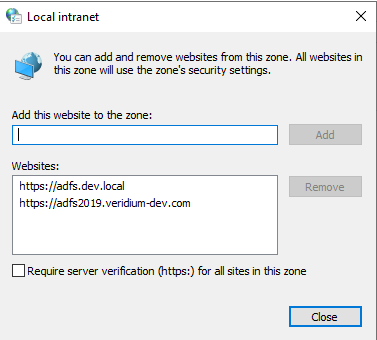
The ADFS server has to be added to the local intranet zone on the hybrid joined machine. For this, access Control Panel->Internet Options->Security->Local Intranet->Sites:
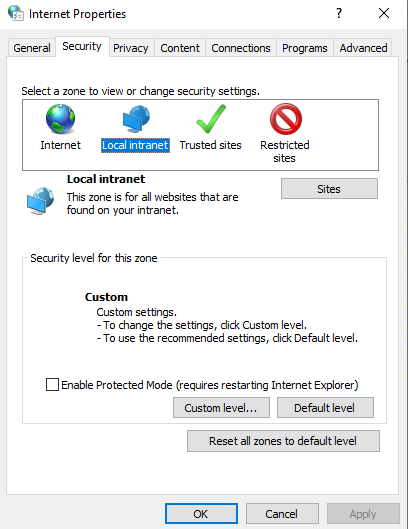
Click on Advanced:
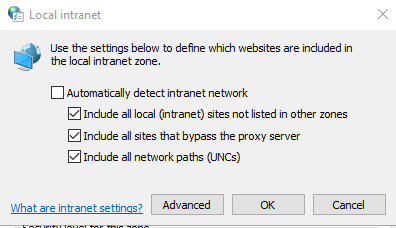
Add the fqdn of the adfs server to the list:
Test the configuration
Log in to a hybrid joined machine with a user which is a part of the local domain and also synchronized to Azure AD through the Azure Ad Connect application. To check if everything is working as it should, in a command prompt window run the command dsregcmd /status . If there aren’t any issues, the output should look like this:
CODE+----------------------------------------------------------------------+ | Device State | +----------------------------------------------------------------------+ AzureAdJoined : YES EnterpriseJoined : NO DomainJoined : YES DomainName : DEV +----------------------------------------------------------------------+ | Device Details | +----------------------------------------------------------------------+ DeviceId : 0db6819e-e5c4-4420-852a-554aa9f464e1 Thumbprint : 18DD637241D491E03D08CCEE2137E3EC59670BF6 DeviceCertificateValidity : [ 2023-11-23 14:00:57.000 UTC -- 2033-11-23 14:30:57.000 UTC ] KeyContainerId : 20e7aa08-549c-4cda-9d3d-8c94c6d47c14 KeyProvider : Microsoft Software Key Storage Provider TpmProtected : NO +----------------------------------------------------------------------+ | Tenant Details | +----------------------------------------------------------------------+ TenantName : creativeast-software.com TenantId : f48d7dcf-e588-4239-a6c1-bb4d15cf5780 Idp : login.windows.net AuthCodeUrl : https://login.microsoftonline.com/f48d7dcf-e588-4239-a6c1-bb4d15cf5780/oauth2/authorize AccessTokenUrl : https://login.microsoftonline.com/f48d7dcf-e588-4239-a6c1-bb4d15cf5780/oauth2/token MdmUrl : https://enrollment.manage.microsoft.com/enrollmentserver/discovery.svc MdmTouUrl : https://portal.manage.microsoft.com/TermsofUse.aspx MdmComplianceUrl : https://portal.manage.microsoft.com/?portalAction=Compliance SettingsUrl : JoinSrvVersion : 1.0 JoinSrvUrl : https://enterpriseregistration.windows.net/EnrollmentServer/device/ JoinSrvId : urn:ms-drs:enterpriseregistration.windows.net KeySrvVersion : 1.0 KeySrvUrl : https://enterpriseregistration.windows.net/EnrollmentServer/key/ KeySrvId : urn:ms-drs:enterpriseregistration.windows.net WebAuthNSrvVersion : 1.0 WebAuthNSrvUrl : https://enterpriseregistration.windows.net/webauthn/f48d7dcf-e588-4239-a6c1-bb4d15cf5780/ WebAuthNSrvId : urn:ms-drs:enterpriseregistration.windows.net DeviceManagementSrvVer : 1.0 DeviceManagementSrvUrl : https://enterpriseregistration.windows.net/manage/f48d7dcf-e588-4239-a6c1-bb4d15cf5780/ DeviceManagementSrvId : urn:ms-drs:enterpriseregistration.windows.net +----------------------------------------------------------------------+ | User State | +----------------------------------------------------------------------+ NgcSet : NO WorkplaceJoined : NO WamDefaultSet : YES WamDefaultAuthority : organizations WamDefaultId : https://login.microsoft.com WamDefaultGUID : {B16898C6-A148-4967-9171-64D755DA8520} (AzureAd) +----------------------------------------------------------------------+ | SSO State | +----------------------------------------------------------------------+ AzureAdPrt : YES AzureAdPrtUpdateTime : 2023-12-15 15:36:12.000 UTC AzureAdPrtExpiryTime : 2023-12-31 15:05:39.000 UTC AzureAdPrtAuthority : https://login.microsoftonline.com/f48d7dcf-e588-4239-a6c1-bb4d15cf5780 EnterprisePrt : NO EnterprisePrtAuthority : https://adfs2019.veridium-dev.com:443/adfs
Note that the device status is Domain joined and also Azure AD joined. The SSO section confirms that the Primary Refresh Token has been issued and the authority is the internal ADFS server.
Troubleshooting
In case of issues, you can use the following ways to perform troubleshoot:
dsregcmd command - allows to troubleshoot device joining issues and can confirm SSO is working or not;
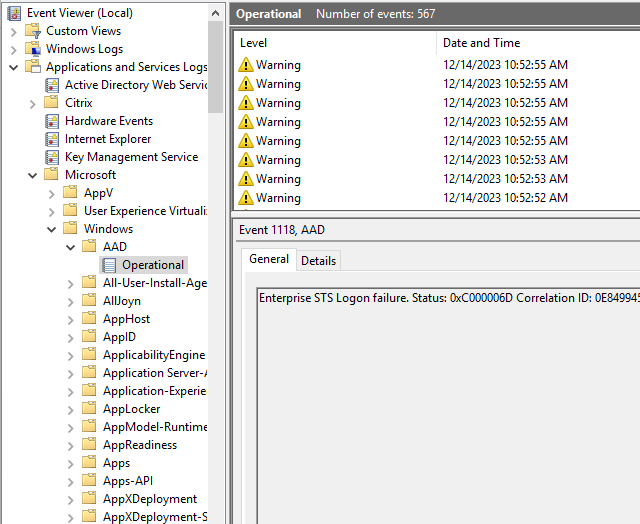
Event Viewer:
- on the ADFS server, you can check the log Custom Views->Server Roles->Active Directory Federation Services for any errors:
- on the hybrid joined machine, you can check Azure AD log located at Applications and Services Logs->Microsoft->Windows->AAD->Operational for any Azure authentication related errors: