How to create a relying party trust for SSP (use ADFS as IDP)
Veridium Self Service portal offers the possibility of using a different IDP from Shibboleth. In this article we’ll be focusing on using ADFS as an identity provider. In order to achieve this, you must define a relying party trust in the ADFS server by performing perform the following procedure:
Access the ADFS management console by right clicking on Start Menu, then select Run:
In the following window type mmc and hit Enter:
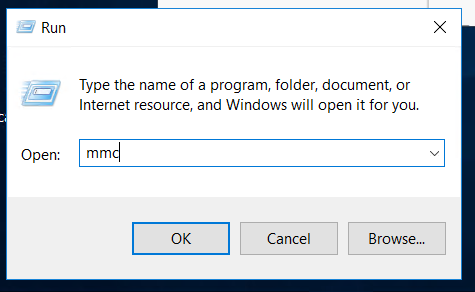
In the Microsoft managemeng console window click on File, then select Add/remove snapin:
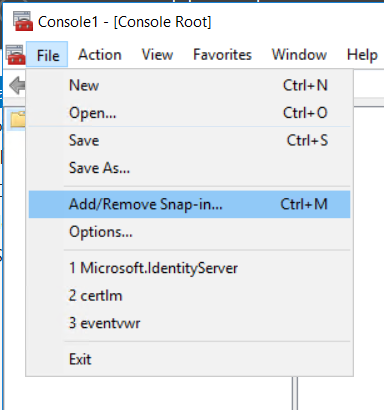
Select AD FS Management snapin, then click on Add and then OK:
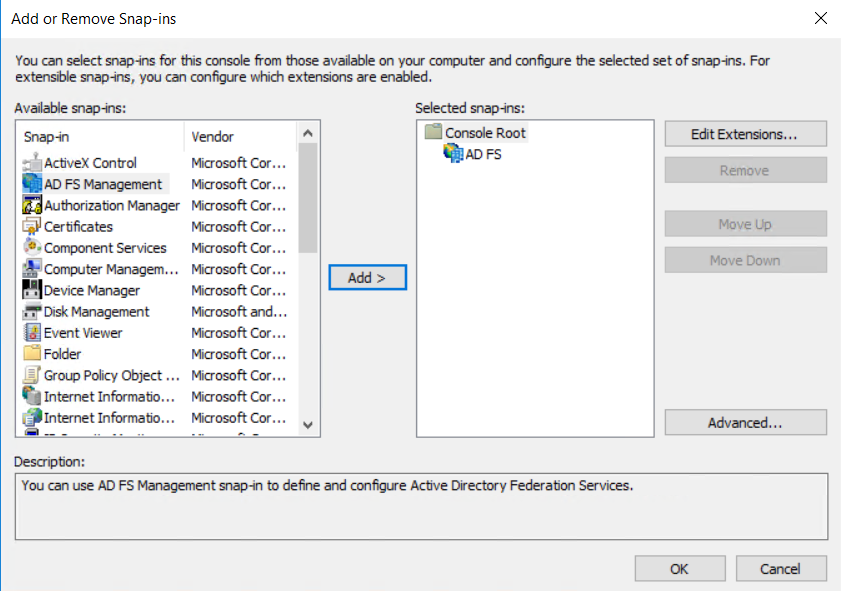
Expand AD FS, then right click on Relying Party Trusts and select Add Relying Party Trust:
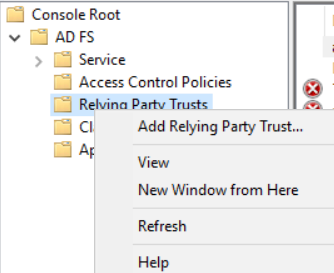
Select Claims aware option and then click on Start:
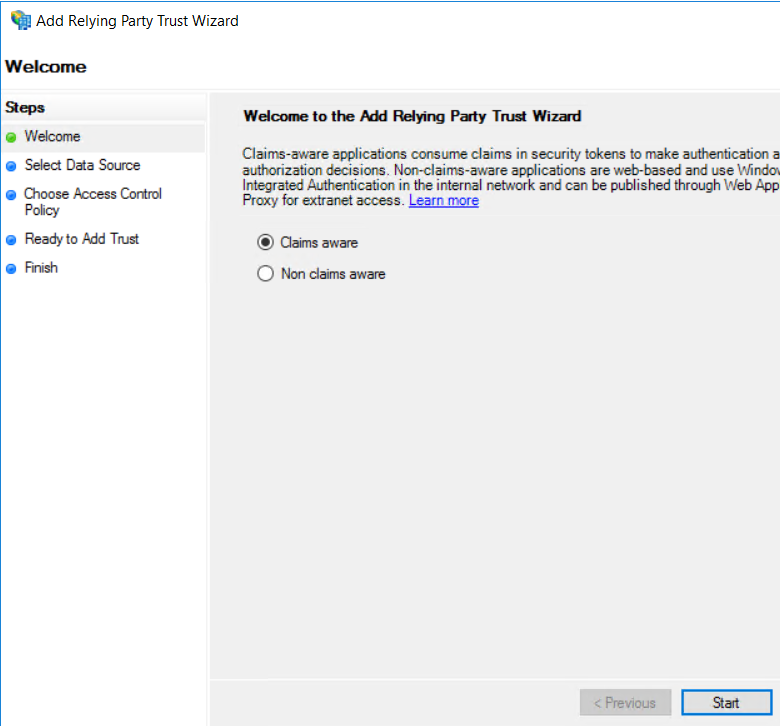
Extract the SSP metadata by going to Veridium manager in Settings->Services->SSP and select Download SSP Metadata. Select the file in the AD FS Management console and then click on Next:
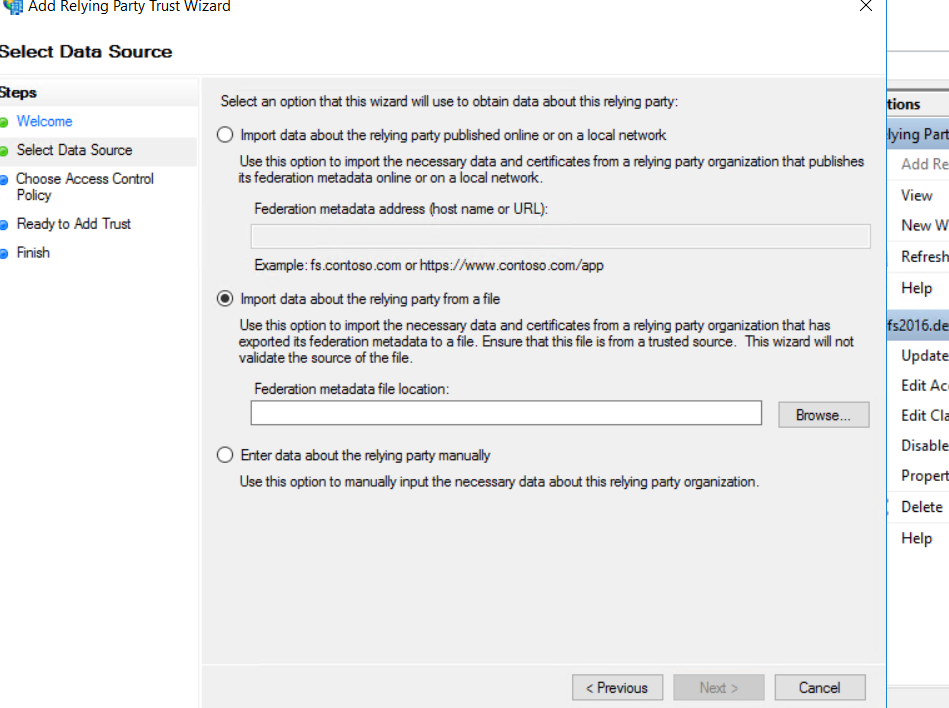
Enter a name and then click on Next:
Select Permit everyone as an access control policy and click on Next:
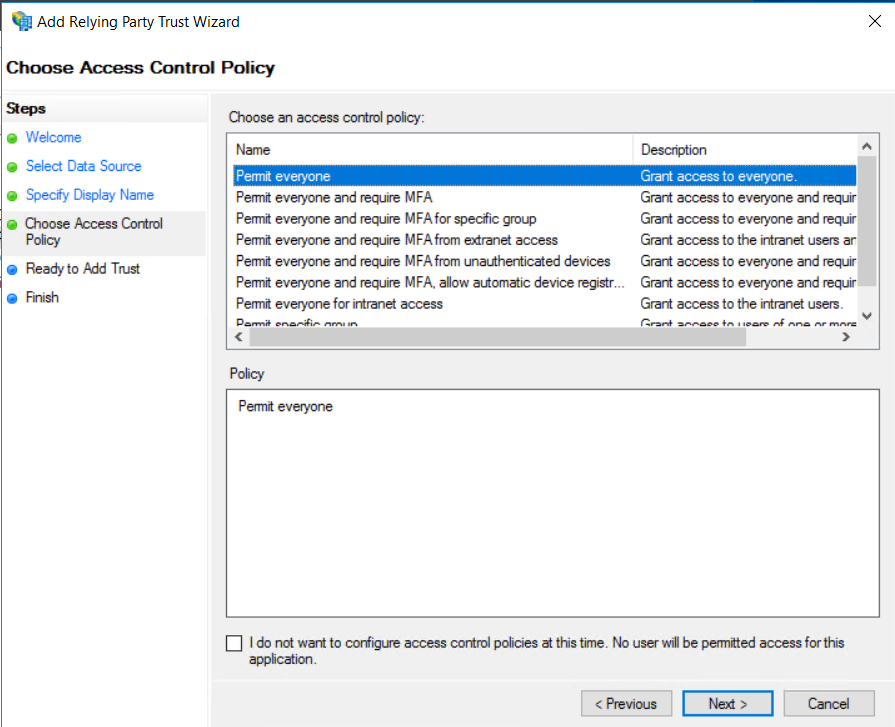
Select Configure claims issuance policy for this application and then click on Close:
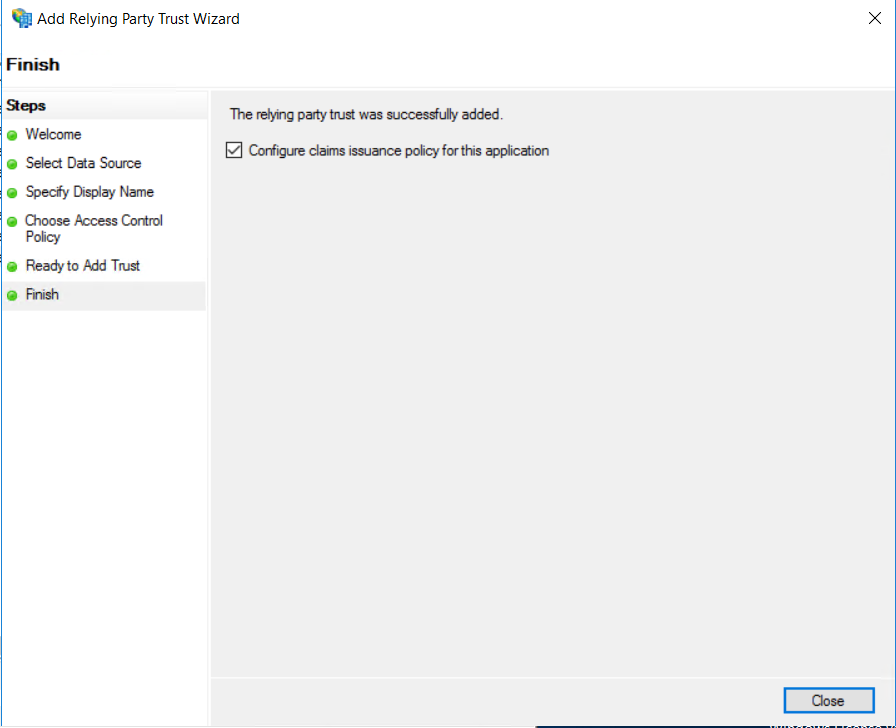
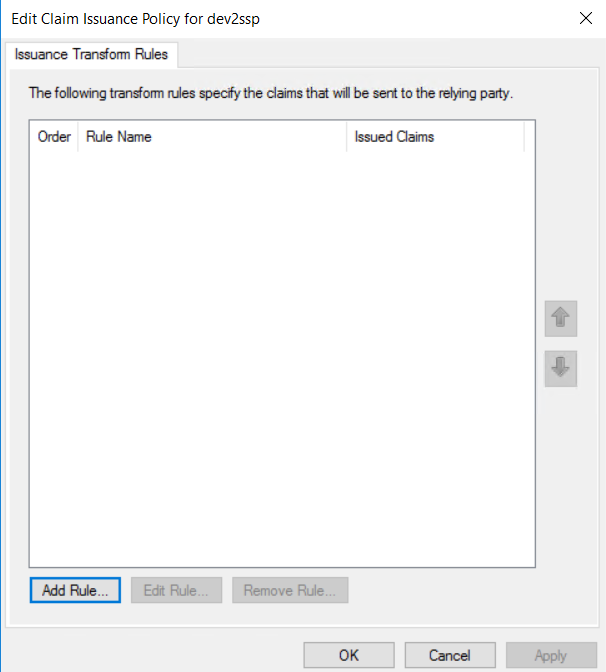
In order for the authentication to work, we need to pass the user principal name as NameID. This can be done by creating a transform rule. In the Edit Claim Issuance Policy for dev2ssp window click on Add Rule:
In the Add Transform Claim Rule Wizard window select Send LDAP Attributes as Claims then click on Next:
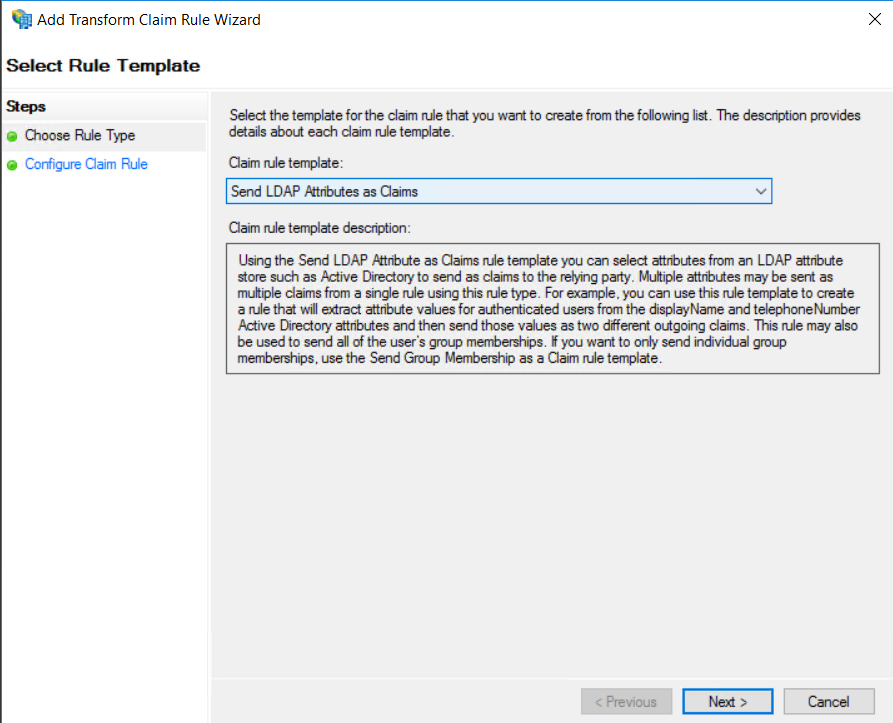
Set a name for the rule, then select Active Directory in the Attribute store section. Map the User-Principal-Name attribute to the Name ID outgoing claim type and click on Finish:
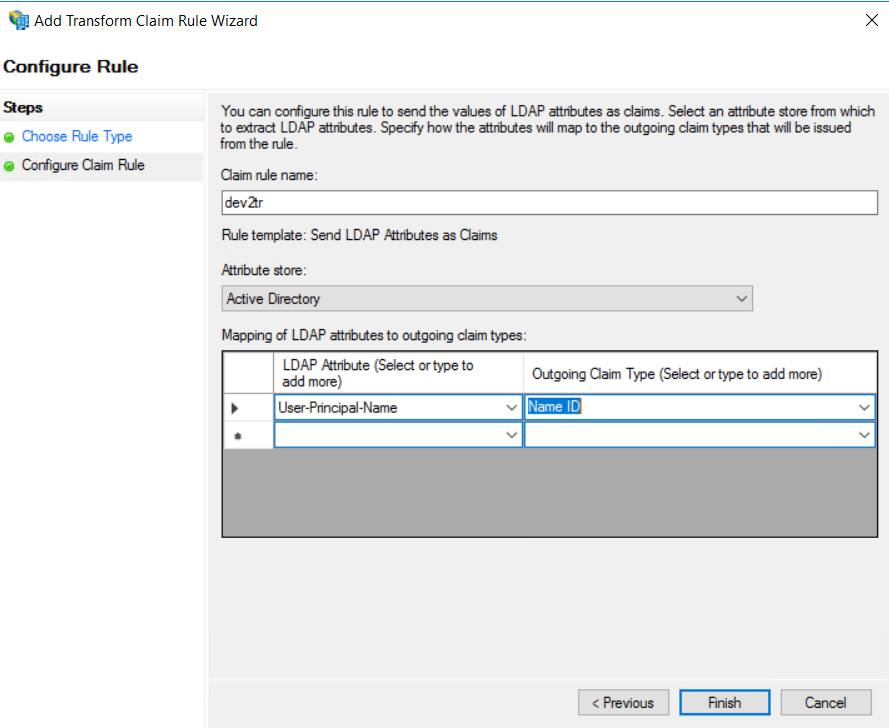
In the next window click on Apply and then OK:
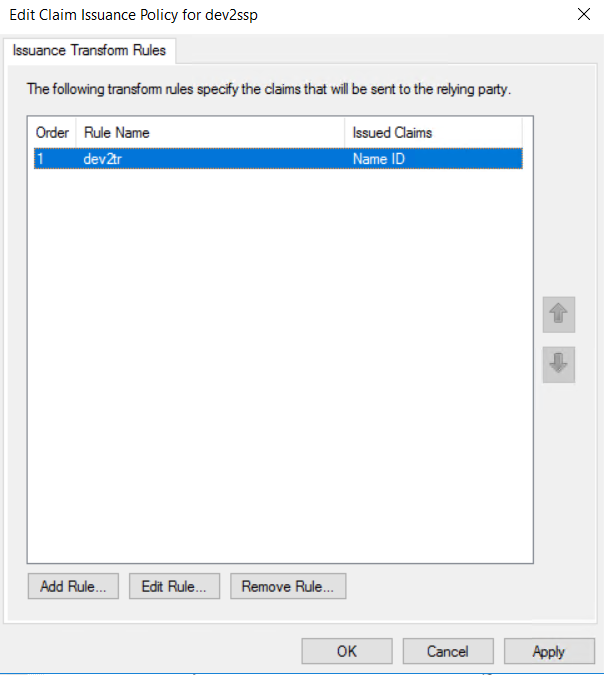
Right click on the newly created relying party trust and select Properties:
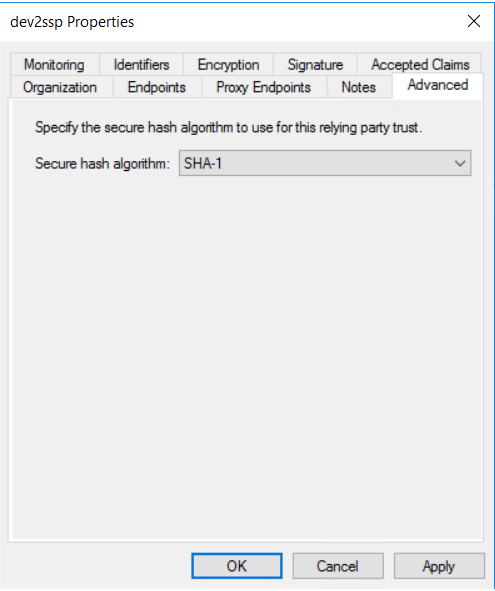
In the Advanced section, select SHA-1 as secure hash algorithm, then click on Apply and OK:
The final step is to disable certificate checking by ADFS. Go to a Powershell window an execute the following command(type in the appropriate relying party trust name):
CODEGet-AdfsRelyingPartyTrust "dev2ssp" | Set-AdfsRelyingPartyTrust -SigningCertificateRevocationCheck none -EncryptionCertificateRevocationCheck noneNow you must set ADFS as idp for Self Service Portal. First you need to extract the ADFS metadata file. This is available at the following link: https://<adfs-fqdn>/FederationMetadata/2007-06/FederationMetadata.xml (type the correct fqdn of your adfs server). After downloading the metadata file, go to VeridiumID manager in Settings->Services->SSP and load the file in the IDP Metadata File section. Click on Save to finish:
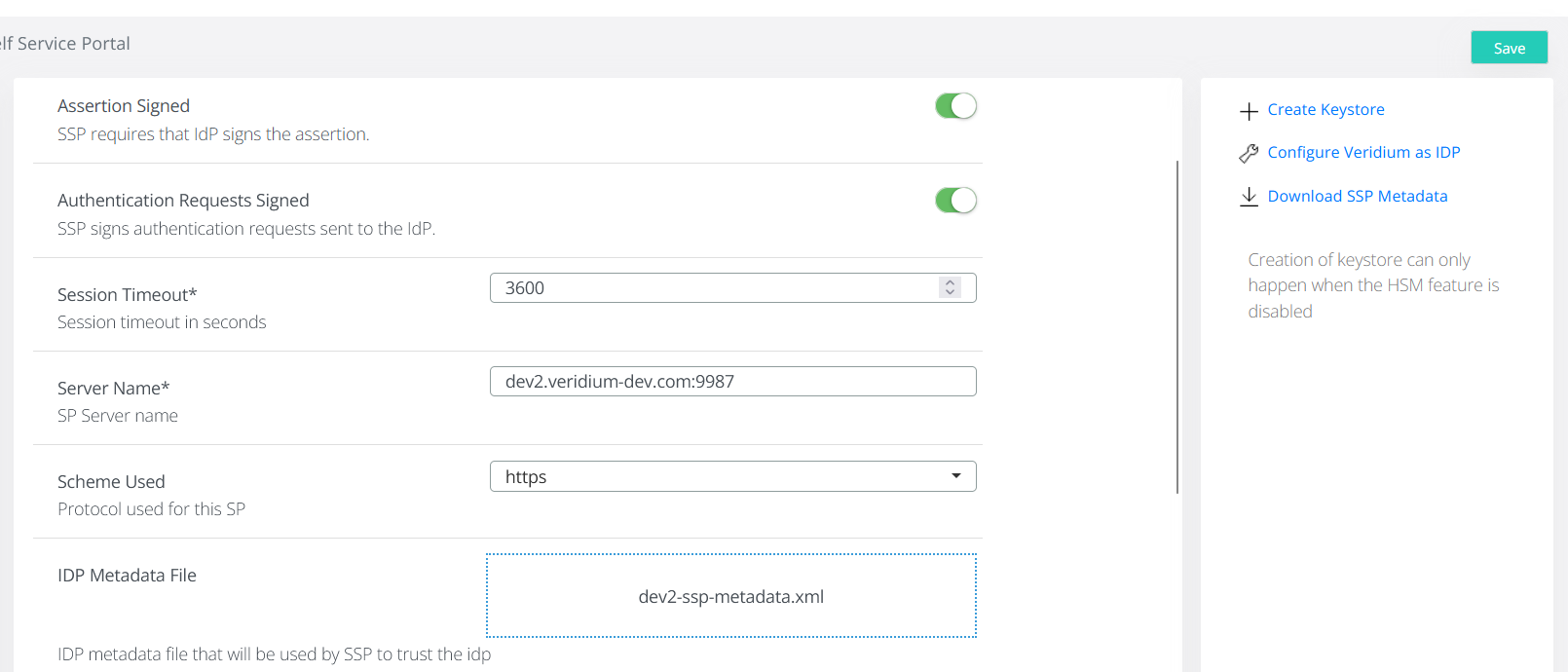
Next time you’ll access SSP, the request will be redirected to the ADFS server and you will be prompted with the authentication method configured in the ADFS management console. To revert the settings and use Shibboleth as IDP, click on Configure Veridium as IDP option (the 18th Step screenshot).
