FIDO Service Configuration
This document provides an overview for FIDO setup using VeridiumID Server version 3.x.
Please note that default and recommended values are specified for parameters that can work with them, while other parameters need configuration specific to deployment environment and infrastructure requirements on a case-by-case basis.
Configure FIDO Server
Upon deployment the FIDO server must be configured in VeridiumID Server using the Admin Dashboard
Navigate to Settings/General/FIDO Settings
Fill in the configuration with proper values
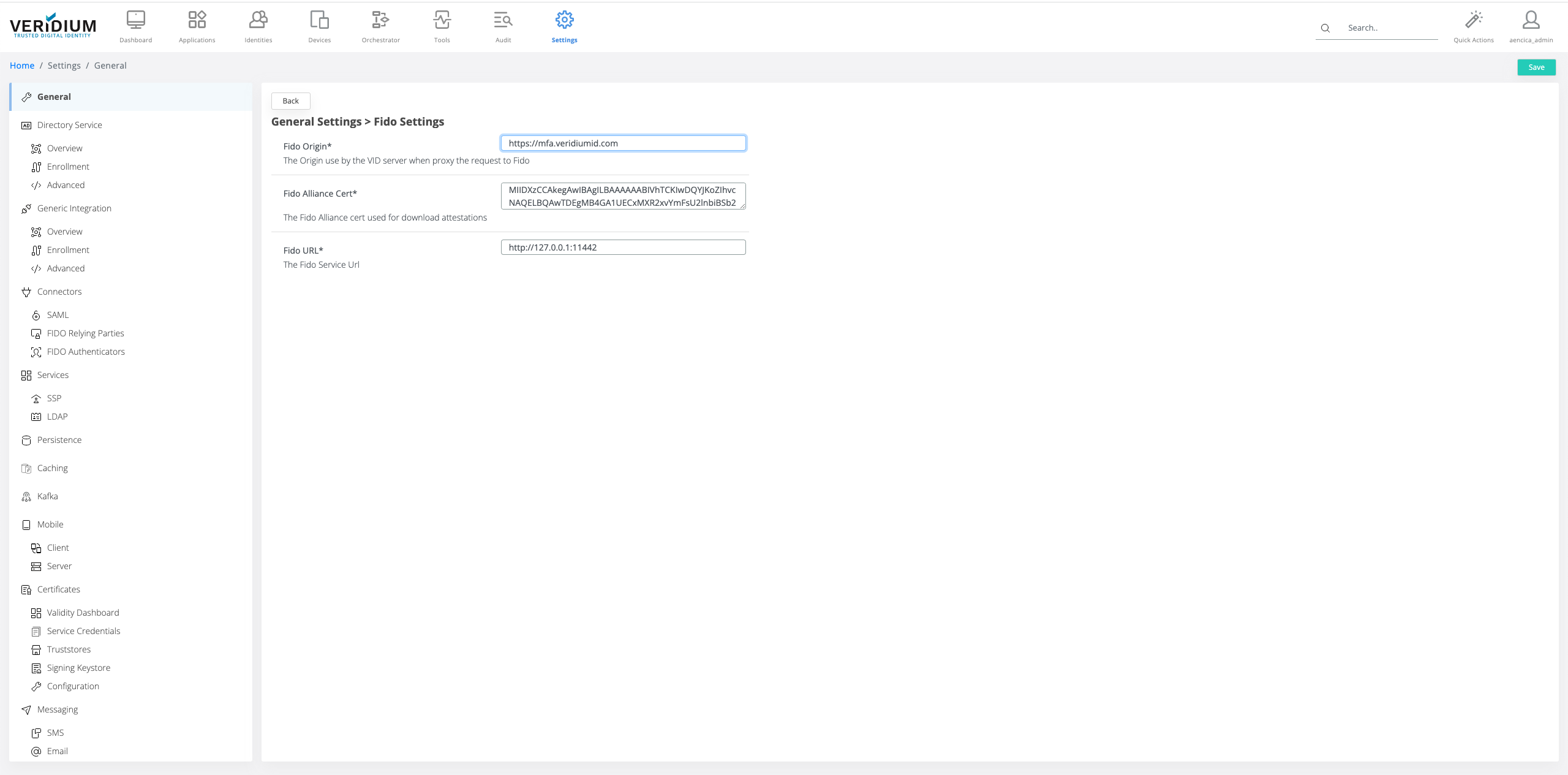
fidoOrigin: the FQDN for the Veridium authentication server.
fidoAllianceCert: the certificate used for FIDO Alliance MDS2 communication that retrieves the list of certified FIDO authenticators.
fidoUrl: the internal URL used for communication between VeridiumID Server and FIDO Server.
Configure FIDO Authenticators
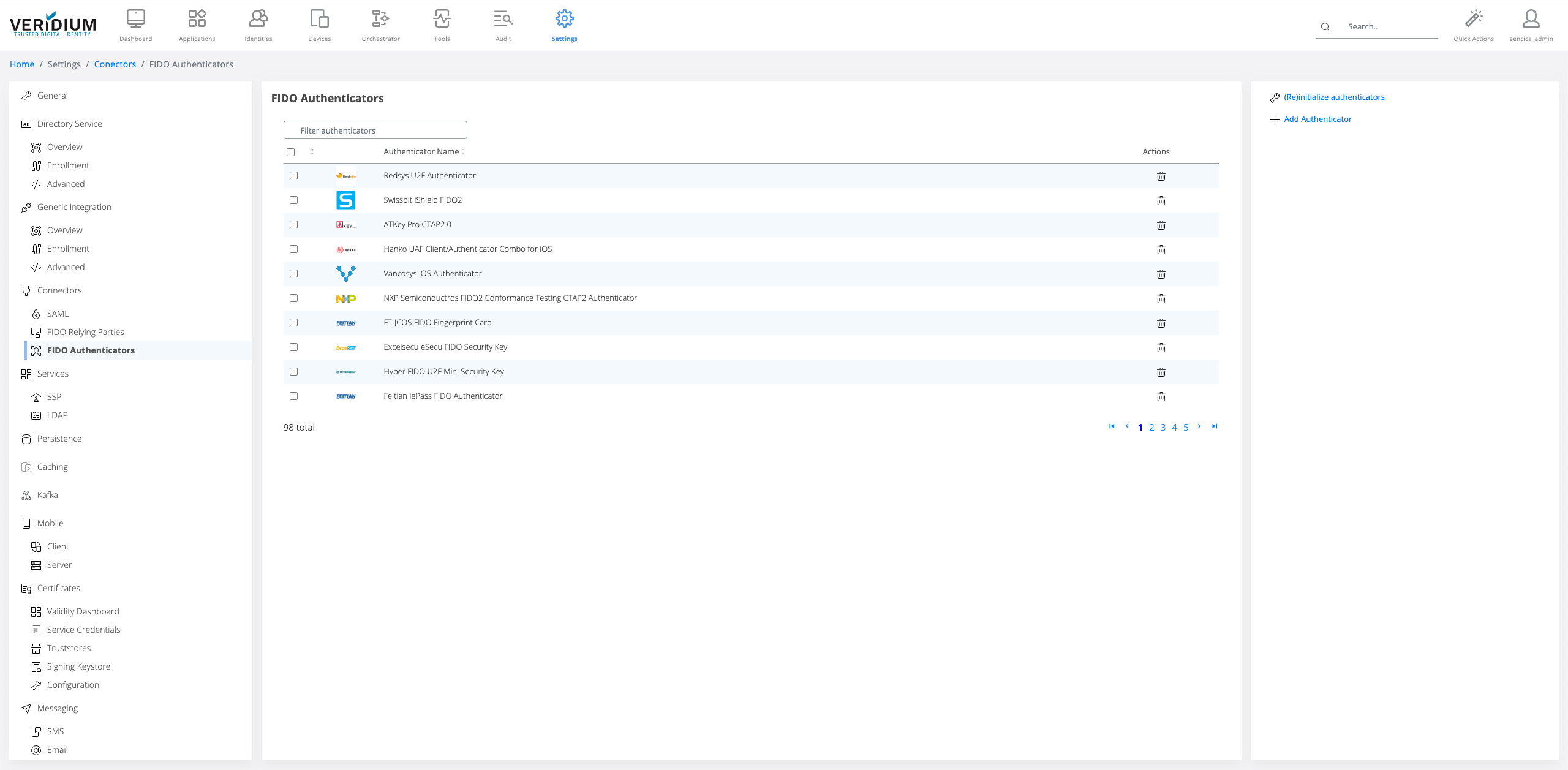
The list of trusted FIDO authenticators can be configured in the Admin Dashboard in FIDO: Authenticators
NOTE: The ability to enforce restrictions on FIDO Authenticator enrollment requires proper attestation configuration of the FIDO Relying Party.
FIDO certified authenticators can be downloaded from MDS3 service automatically and the list is refreshed when (Re)Initialize authenticators.
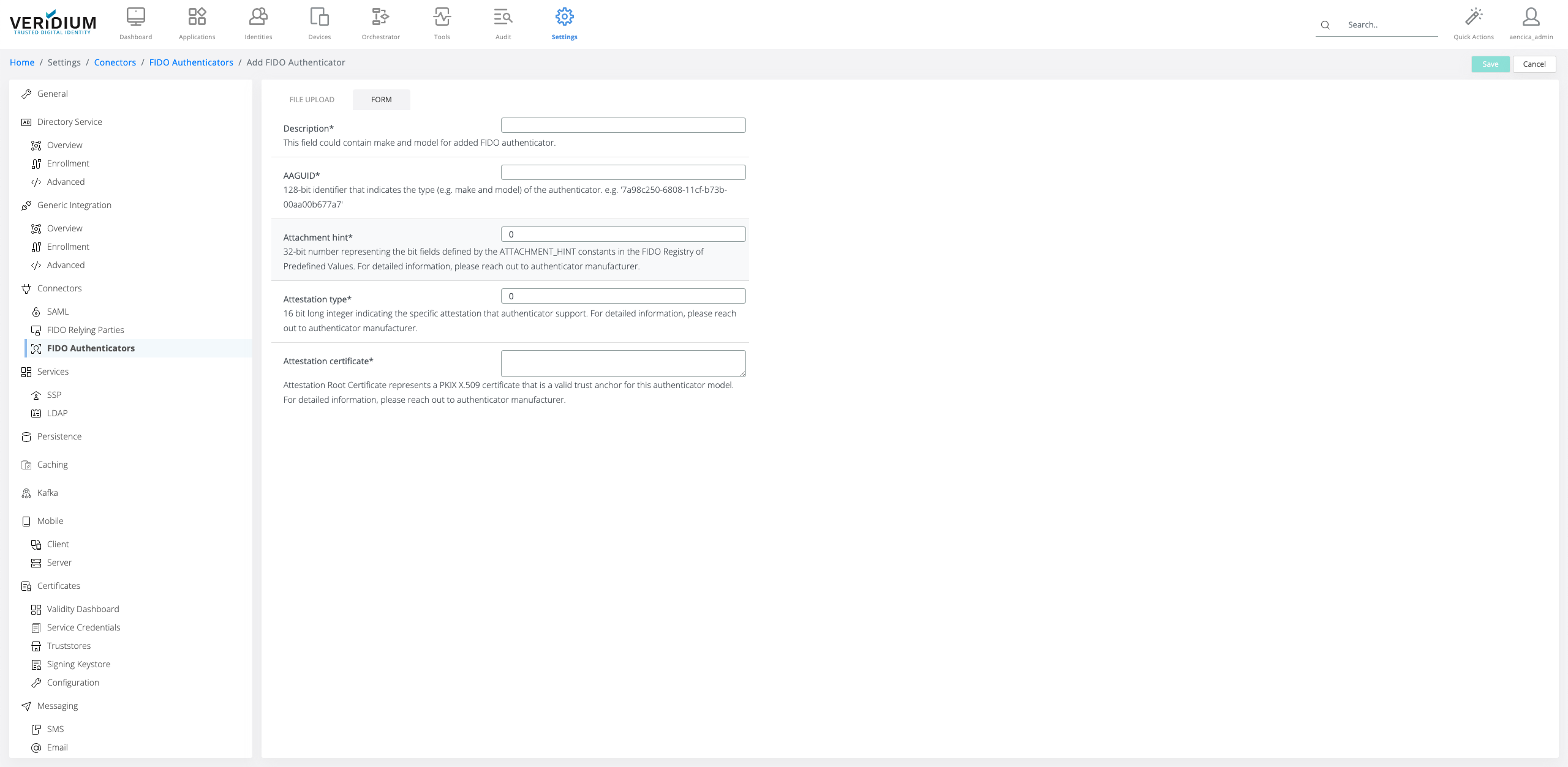
Authenticators can be also added manually by using Add Authenticator. An authenticator can be imported via Metadata statement provided by the FIDO authenticator vendor, or by manually filling the required information that should be provided by the FIDO authenticator vendor.
Configure FIDO Relying Party
The relying party provides information for the service that allows FIDO authentication and the configuration regarding FIDO authenticator constraints.
From this point on, Relying Party will be referred as “RP” in the documentation.
A default RP party configuration is automatically created when (RE)Initialize default FIDO Relying Party based on the configuration made around the system and may serve as a starting point.
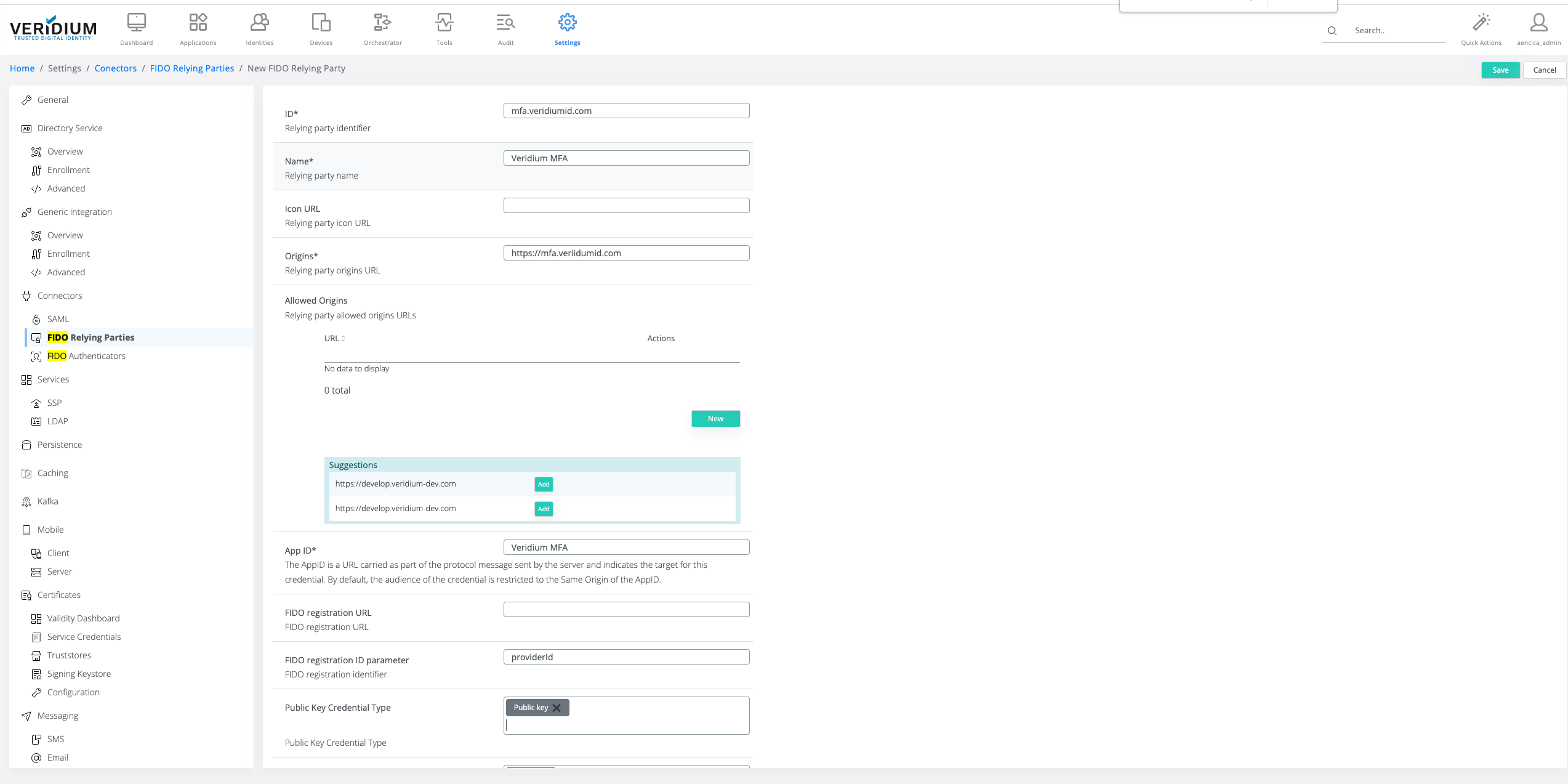
ID: represents the FIDO RP id. This should be the base FQDN for the VeridiumID server deployment (e.g. “mfa.veridiumid.com”)
Name: name of the RP that provides easy identification. This will be presented for the user on authenticators that have display support.
Icon: icon for RP. This will be presented for the user on authenticators that have display support.
Origins: If multiple RP are defined and used, this field allows filtering the RP during enrollment and authentication.
Application ID: this field is mainly used for FIDO UAF/U2F.
FIDO registration URL: Veridium allows enrollment delegation for FIDO key. Leave blank if FIDO enrollment delegation is not used (see Configure FIDO Authenticator Enrollment)
FIDO Registration Id Param Name: During FIDO enrollment delegation, the delegated service requires the origin of the service providing the registration. When using Veridium IdP for FIDO authenticator enrollment, the value is providerId. Leave blank if FIDO enrollment delegation is not used. (see Configure FIDO Authenticator Enrollment)
Public Key Credential Type: Currently, all FIDO authenticators use Public Key credential type.
COSE Algorithms: The list of supported algorithms for key signature. This is strongly related with the FIDO Authenticator supported algorithms and should be set considering the security constraints provided by the internal Security Advisory team.
Allow Unknown Extension: allows FIDO authenticators to provide other extensions than the RP configured extensions. Recommended value is false.
Allow Missing Attestation: allows FIDO authenticators that do not provide attestation. Recommended value is false, if this is set to true the list of allowed authenticators will not be enforced.
Signature Counter Validation: during FIDO authentication, the authenticator keeps an internal counter that is provided to the RP for verify. Recommended value is true.
Authenticator Attachment Type: informs the FIDO client during enrollment and authentication regarding the FIDO authenticator allowed communication protocol (e.g. USB, BLE, NFC, Platform), providing a mechanism to filter nearby authenticators.
User Verification Requirement: informs the FIDO client and FIDO authenticator if the user verification is preferred, required or discouraged.
Attestation Conveyance Preference: informs how the FIDO attestation is provided to the Veridium Server:
None: This value indicates that the Relying Party is not interested in authenticator attestation and will accept any authenticator with or without attestation statement.
Direct: This value indicates that the Relying Party wants to receive the attestation statement as generated by the authenticator.
Indirect: This value indicates that the Relying Party prefers an attestation conveyance yielding verifiable attestation statements, but allows the client to decide how to obtain such attestation statements. The client MAY replace the authenticator-generated attestation statements with attestation statements generated by an Anonymization CA, in order to protect the user’s privacy, or to assist Relying Parties with attestation verification in a heterogeneous ecosystem.
Resident Key Required: Informs the FIDO authenticator to store information that allows discoverable keys during authentication. This should be strictly used in conjunction with Resident Key Requirement.
Resident Key Requirement: Specifies the extent to which the Relying Party desires to create a client-side discoverable credential.
Client Extension: Allowed 3rd party authenticator extensions.
minPinLength extension
The organizations using FIDO keys want to have the possibility to enforce the minimum PIN length. To achieve this, Veridium Server uses the minPinLenght extension to get the minimum PIN length configured on the key.
For extension configuration, in the Relying Party details, scroll down to minPinLength configuration section, as shown below:
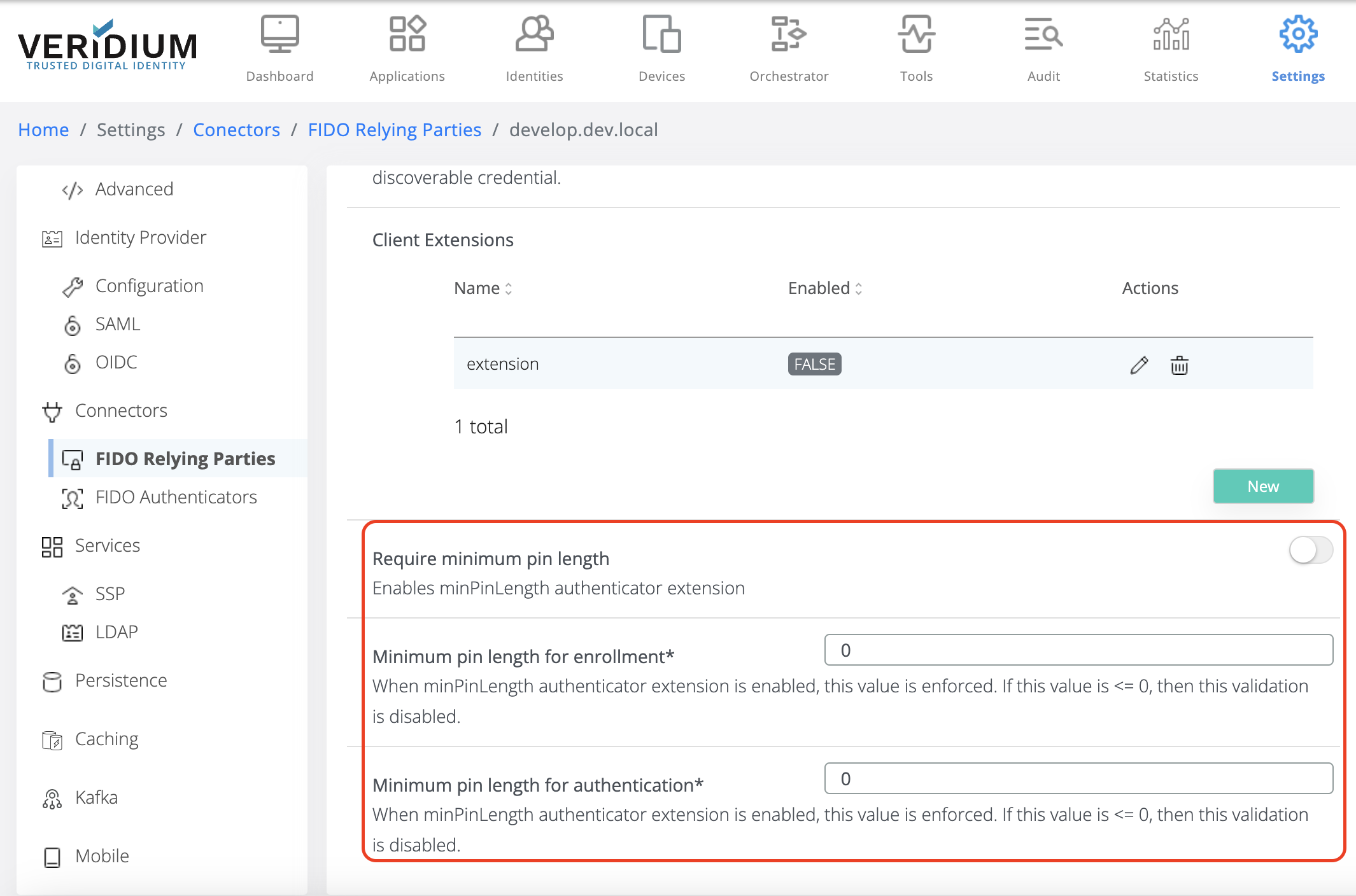
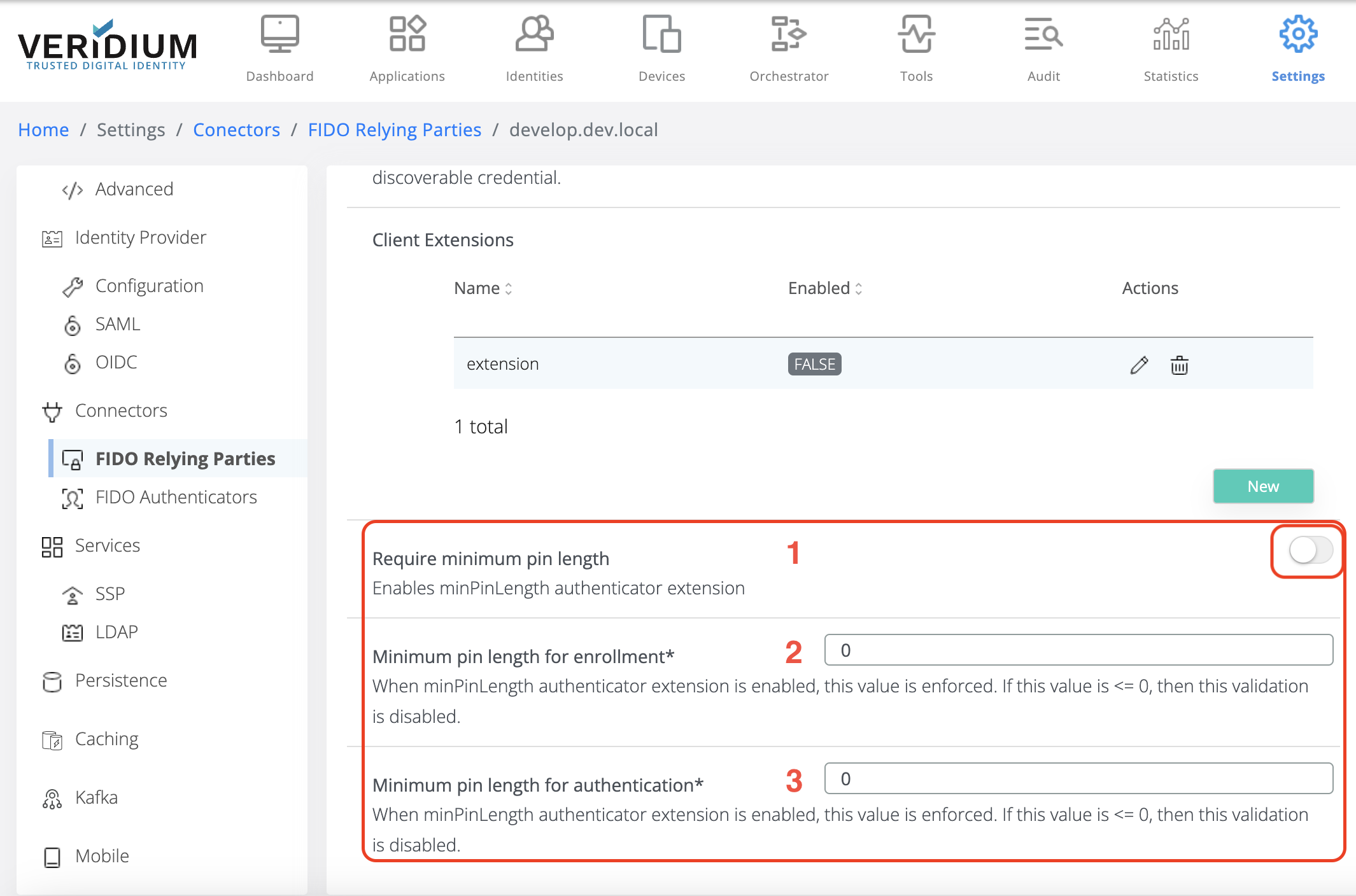
Configure the extension as indicated below:
Enable/disable minimum PIN length validation. This validation can be enabled/disabled by checking/unchecking the flag indicated below.
If it is enabled, then the following values are enforced at enrollment and authentication, respectively.
If the extension is disabled, then the validation is skipped, regardless of the values set for the following fields.
Minimum PIN length value for enrollment.
If this value is strictly positive, greater than 0 (zero), then this value is enforced at FIDO Enrollment, minPinLength value set on the device should be greater or equal to this value. If the device minPinLength is less than this value, then the enrollment fails with an error.
If this value is 0 (zero) or negative, then the validation is skipped for enrollment.
Minimum PIN length for authentication.
If this value is strictly positive, greater than 0 (zero), then this value is enforced at FIDO Authentication, minPinLength value set on the device should be greater or equal to this value. If the device minPinLength is less than this value, then the authentication fails.
If this value is 0 (zero) or negative, then the validation is skipped for authentication.
Device setup
For this extension to work, FIDO devices need to be instructed to share the minimum PIN length configuration with the desired relying party. This is a device specific/vendor specific operation, but for example, for Yubico Yubikey the following command sets the minimum PIN length to 8 and share this value with Relying Party, given by its ID local.veridium-dev.com,
ykman fido access set-min-length 8 -R local.veridium-dev.com
Configure FIDO Authenticator Enrollment
The FIDO enrollment is usually made via Self Service Portal (SSP) web application provided in the standard VeridiumID server deployment. Veridium also provides an alternative method to enroll the FIDO authenticator using Veridium IdP.
SSP FIDO Configuration
Using Veridium Manager: Settings/Services/SSP the following settings should be configured:
fidoOrigin: the FQDN for the VeridiumID server deployment.
delegateFidoEnrollment: configuration FIDO enrollment using delegation to IdP.
There are 2 options to configure FIDO enrollment in the VeridiumID:
A. FIDO Enrollment in SSP
This is the recommended option for integrating the FIDO enrollment with the VeridiumID server. The FIDO enrollment flow is completed within the SSP web application providing seamless integration.
fidoOrigin - this value should be the same as configured in the FIDO Relying Party ID
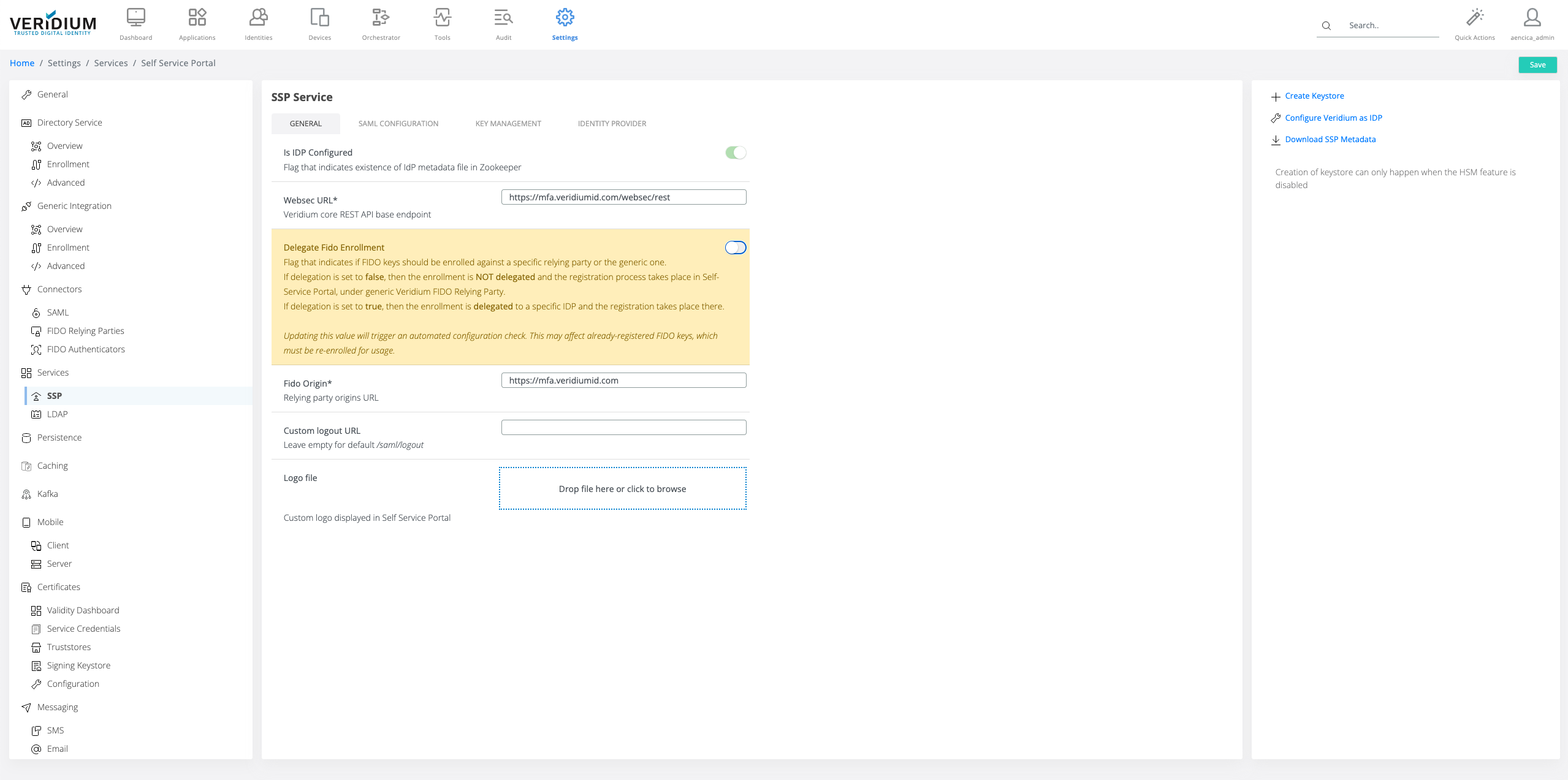
Save the configuration and click ok on the configuration change warning.
If any FIDO authenticators were previously enrolled before changing this configuration, they would have to be re-enrolled.
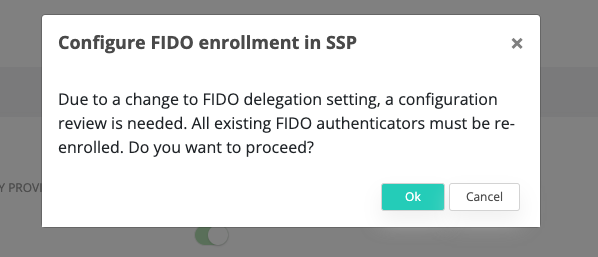
2. You’ll be presented the option to choose the RP party that is going to be used for FIDO enrollment and authentication. When the Relying parties are configured correctly, there should be a single item in the list that is allowed for selection.
B. FIDO Enrollment with delegation on external Self Service Portal reference
This option should be taken into consideration only when the internal infrastructure provides limitation for FIDO Authentication. The Self Service Portal enrollment and authentication is allowed only on internal infrastructure (internal FQDN), while the authentication using FIDO is allowed only on external FQDN.
e.g. internal FQDN - mfa.veridiumid.srv; external FQDN - mfa.veridiumid.com
When multiple FIDO Relying parties are configured, the user is prompted during enrollment to choose the FIDO Relying Party to enroll the FIDO key, and authentication with the enrolled credential is going to be possible only on that Relying Party.
Enable the FIDO delegation in the SSP Service configuration.
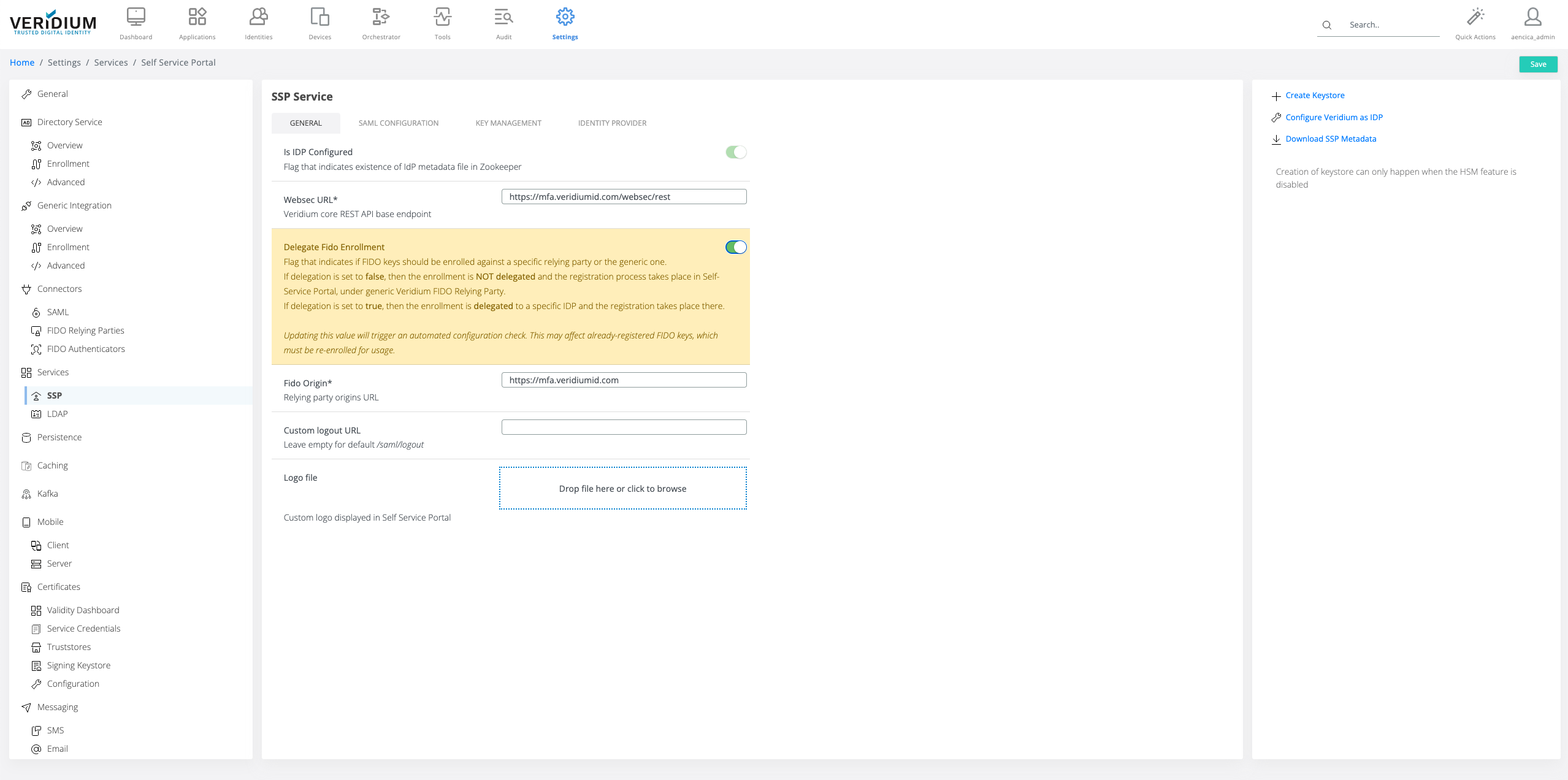
2. Save the configuration and click ok on the configuration change warning.
If any FIDO authenticators were previously enrolled before changing this configuration, they would have to be re-enrolled.

3. If multiple FIDO Relying Party are configured, you’ll be asked to choose a Relying Party that is going to be used for FIDO authentication in the Veridium IdP.
4. Configure FIDO Relying Party using Veridium SSP enrollment:
FIDO registration URL: https://<veridium-ssp-url>/ssp/index.html#enrollment
FIDO Registration Id Param Name: providerId
