FIDO Platform Authenticators
This document provides an overview for the FIDO Platform Authenticators supported by Veridium Server.
Apple TouchID, FaceID or Passcode
Apple uses different attestation statements depending of the OS version and the browser used during enrollment and authentication.
Apple Passkeys Attestation
Starting iOS/iPadOS 16 and macOS 13, the Apple uses only passkeys (credentials are synchronized on iCloud for all the devices under the iCloud account). Currently the attestation of these credentials cannot be verified and during enrollment the attestation statement is None.
In order to allow these credentials the FIDO Relying Party should be configured to accept missing attestation. Please keep in mind that this also allows other authenticators that do not provide attestation information to be enrolled.
Chrome does not yet provide support on Apple Passkeys on MacOS, but they state that it is planned in the near future. Chrome on iOS already supports this as of Oct. 2022.
For updated information on this topic, check: https://developers.google.com/identity/passkeys/supported-environments.
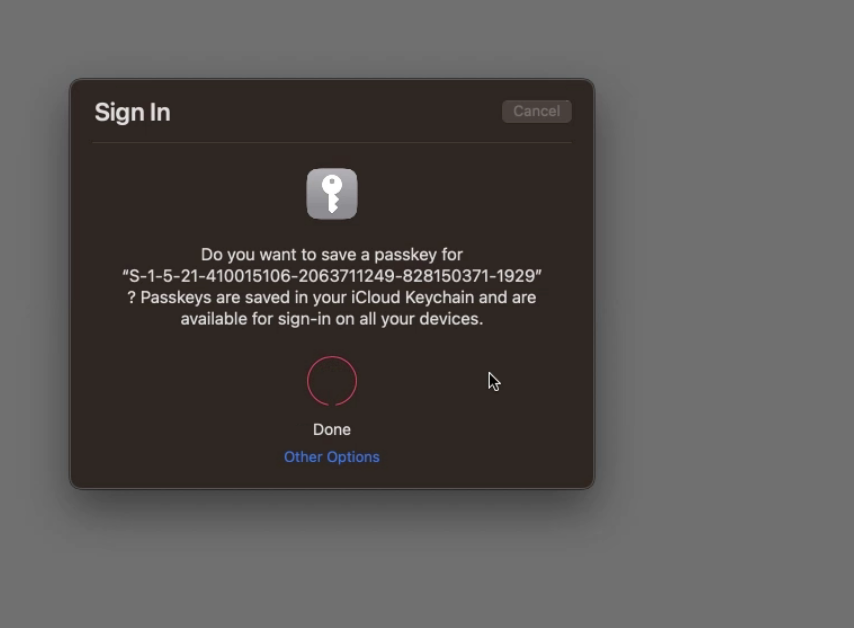
Sample FIDO enrolment with passkey and TouchID on iOS:
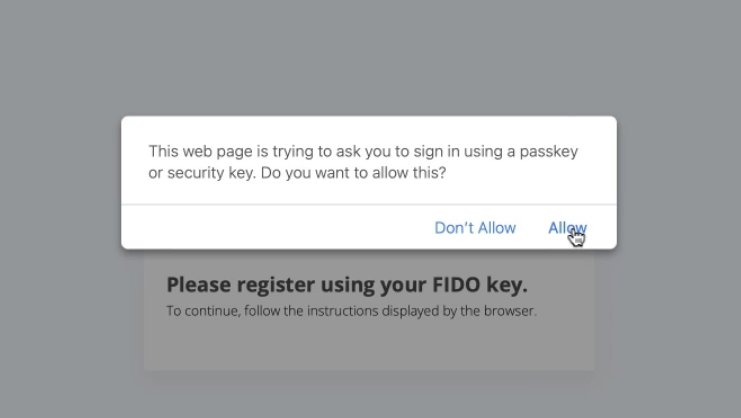
Sample FIDO enrolment with passkey or security key on MacOS with Safari:
WebAuthN Privacy CA:
Support for Apple Attestation CA verification was introduced in Veridium 3.2.2 release
On iOS/iPadOS < 16 and macOS < 13 Apple uses a privacy Attestation CA that is only supported by Safari. Since this was not included in the FIDO MDS service, the authenticator attestation should be manually imported in the Veridium Manager > Settings > FIDO Authenticators > Add FIDO Authenticator and upload the following attestation statement (if upload is not possible use the form to fill in the details).
{
"description": "Apple TouchID, FaceID or Passcode",
"aaguid": "f24a8e70-d0d3-f82c-2937-32523cc4de5a",
"protocolFamily": "fido2",
"assertionScheme": "FIDOV2",
"attestationTypes": [
15882
],
"attachmentHint": 1,
"attestationRootCertificates": [
"MIICEjCCAZmgAwIBAgIQaB0BbHo84wIlpQGUKEdXcTAKBggqhkjOPQQDAzBLMR8wHQYDVQQDDBZBcHBsZSBXZWJBdXRobiBSb290IENBMRMwEQYDVQQKDApBcHBsZSBJbmMuMRMwEQYDVQQIDApDYWxpZm9ybmlhMB4XDTIwMDMxODE4MjEzMloXDTQ1MDMxNTAwMDAwMFowSzEfMB0GA1UEAwwWQXBwbGUgV2ViQXV0aG4gUm9vdCBDQTETMBEGA1UECgwKQXBwbGUgSW5jLjETMBEGA1UECAwKQ2FsaWZvcm5pYTB2MBAGByqGSM49AgEGBSuBBAAiA2IABCJCQ2pTVhzjl4Wo6IhHtMSAzO2cv+H9DQKev3//fG59G11kxu9eI0/7o6V5uShBpe1u6l6mS19S1FEh6yGljnZAJ+2GNP1mi/YK2kSXIuTHjxA/pcoRf7XkOtO4o1qlcaNCMEAwDwYDVR0TAQH/BAUwAwEB/zAdBgNVHQ4EFgQUJtdk2cV4wlpn0afeaxLQG2PxxtcwDgYDVR0PAQH/BAQDAgEGMAoGCCqGSM49BAMDA2cAMGQCMFrZ+9DsJ1PW9hfNdBywZDsWDbWFp28it1d/5w2RPkRX3Bbn/UbDTNLx7Jr3jAGGiQIwHFj+dJZYUJR786osByBelJYsVZd2GbHQu209b5RCmGQ21gpSAk9QZW4B1bWeT0vT"
]
}
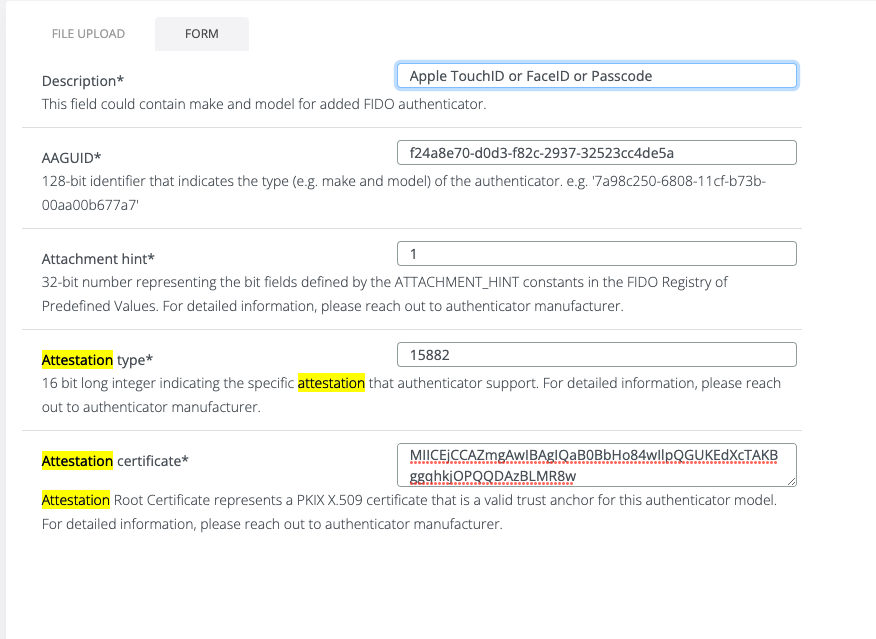
The Attestation Root Certificate may be downloaded for verification from Apple’s website: https://www.apple.com/certificateauthority/Apple_WebAuthn_Root_CA.pem and the values for attestation type and attestation hint from FIDO Registry.
Android
Android SafetyNet Authenticator
Support for enrolling and authentication was introduced in Veridium 3.2.2. An issue was fixed in Veridium Server 3.2.2 that prevented attestation validation, if the FIDO Relying Party was configured to verify the attestation (Attestation conveyance preference: DIRECT/INDIRECT).
Using Android device as a FIDO authenticator is possible with Android SafetyNet Attestation via Google PlayServices WebAuthN client (https://developers.google.com/identity/fido/android/native-apps ). This enables support for FIDO2 platform and roaming authenticator for Android devices running at least Android 8.0, that pass the SafetyNet attestation (https://developer.android.com/training/safetynet/attestation ).
The verification method may phone biometrics or screen lock (password, pattern etc.)
Android SafeyNet Authenticator attestation is a certified FIDO authenticator and the attestation statement may imported from FIDO MDS service.
Google Passkeys
Google works closely with FIDO Alliance alongside Microsoft and other participants to provide support for passkeys and include them in the WebAuthN standard. The Passkeys are synchronized in the Google Password Manager for the active Google User.
Currently the Passkeys support is only under Google Chrome Canary and Google Play Services Beta https://android-developers.googleblog.com/2022/10/bringing-passkeys-to-android-and-chrome.html.
Windows
Using Windows (10 or 11), the WebAuthN support is ensured by the Windows implementation of FIDO client, that is used by all the supported browsers. Starting Windows 11, TPM became a mandatory requirement for the update, forcing all the manufactures to provide out-of-the-box TPM.
Windows Hello - TPM
An issue was fixed in Veridium Server 3.2.2 that prevented attestation validation, if the FIDO Relying Party was configured to verify the attestation (Attestation conveyance preference: DIRECT/INDIRECT).
Windows Hello - Software
There are device that do not have TPM, however the Windows Hello authenticator provides certified support for them.
Both Software and TPM Windows Hello are certified FIDO authenticators and the attestation statement may be imported from the FIDO MDS Service.
