Defense Against DoS and Brute Force Attacks
Implementation consists of a defense mechanism at the application layer level to mitigate the risk of brute force attacks. Specifically, after a certain number of failed authentication/enrollment attempts, the application layer will automatically block further attempts from the combination of user and IP.
This proactive approach helps prevent malicious actors from repeatedly attempting to gain unauthorized access to the application by rapidly trying different combinations of credentials. By implementing this feature, the security of the application will be enhanced and the likelihood of successful brute force attacks will be reduced.
This feature targets the authentication process as well as the enrollment process.
Settings
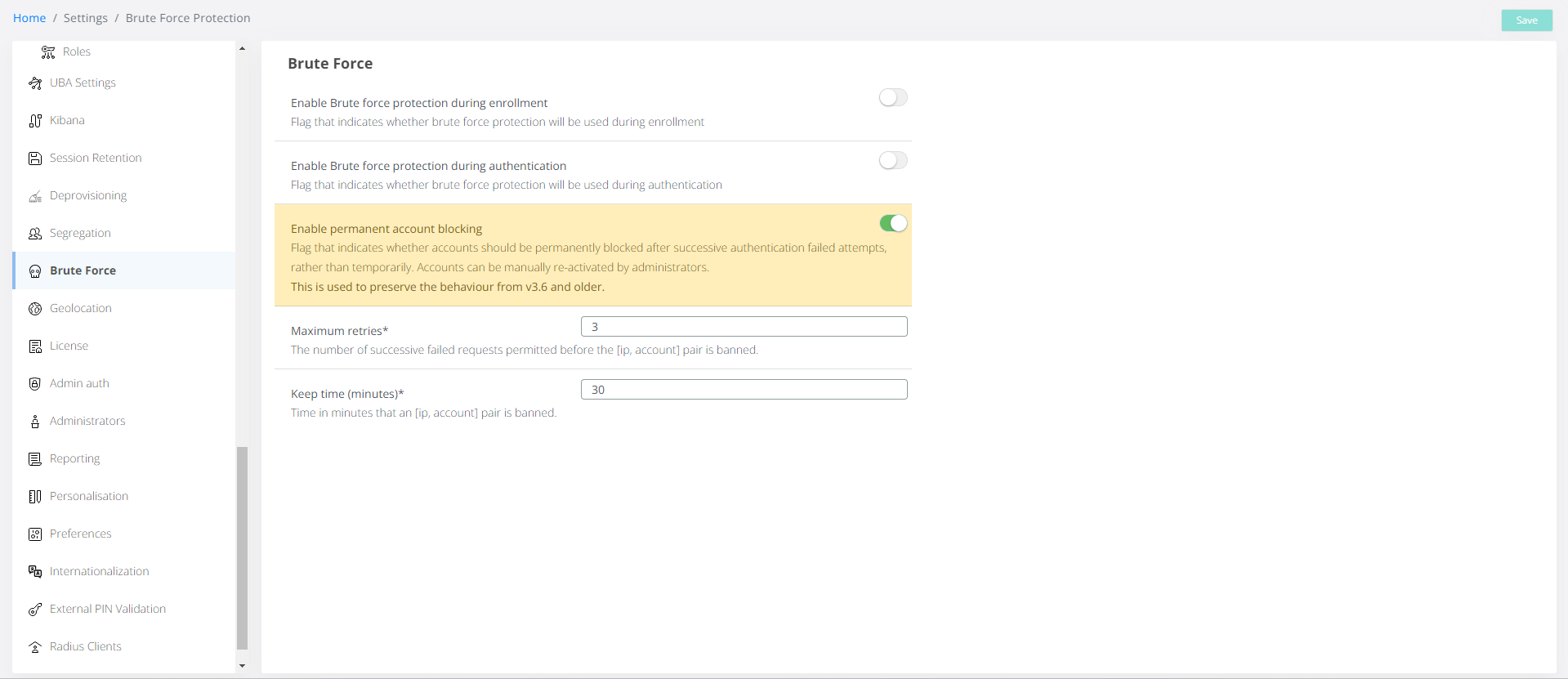
Maximum retries → This setting determines the maximum number of consecutive failed authentication/enrollment attempts allowed for an account originating from a specific IP address before it is automatically blocked. By configuring this parameter, administrators can enhance security measures by mitigating the risk of brute force attacks and unauthorized access attempts. Setting an appropriate threshold for the maximum number of retries helps maintain the integrity and confidentiality of user accounts and sensitive information within the system.
Keep Time (Minutes) → This setting defines the duration, in minutes, for which an account is flagged as a potential brute force attacker on the specific IP address after exceeding the maximum number of retries. During this designated period, the account remains temporarily blocked from further authentication attempts from the same IP address. By specifying a suitable time interval, system administrators can effectively deter and mitigate brute force attacks while minimizing disruption to legitimate users.
Enable Brute force protection during enrollment → This flag indicates whether brute force protection will be enabled during the enrollment process. When activated, this feature adds an additional layer of security by applying brute force protection mechanisms to enrollment procedures.
Enable Brute force protection during authentication → This flag determines whether brute force protection will be activated during the authentication process. When enabled, this feature applies robust defense mechanisms to thwart brute force attacks targeting authentication attempts.
Enable permanent account blocking → This flag determines whether the existing account blocking mechanism, triggered upon authentication after a certain number of failed attempts, will be utilized. While this mechanism can operate concurrently with brute force protection, it's important to note that simultaneous activation may increase the risk of denial-of-service incidents, potentially rendering the protection mechanism less effective.
For example, if an attacker will try multiple accounts and the block flag of an account is active, this can lead to a denial of service, and those legitimate users may not even be able to use the application.
If protection against brute force is chosen, the legitimate user can still have access to the services even if an attacker tries to compromise his identity, because the attacker will be blocked on all the IPs with which he tries to compromise the identity.
Administration
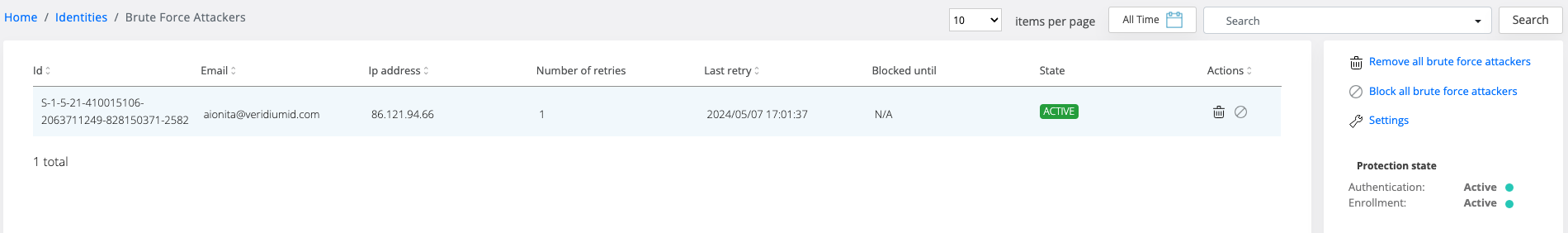
The administration page offers actions such as:
Remove all brute force attackers, action that will delete all users and IPs marked as attacker
Block all brute force attackers, action that will block all IPs present on the left table section, and also the protection status on the application layer.
In the left table section, entries marked as attackers are listed. The row in the table provides information about the user, IP, the number of failed attempts, the last attempt, until it is blocked and its status.
In the photo above, the status is ACTIVE because the user-IP combination has not reached the maximum number of failed attempts.
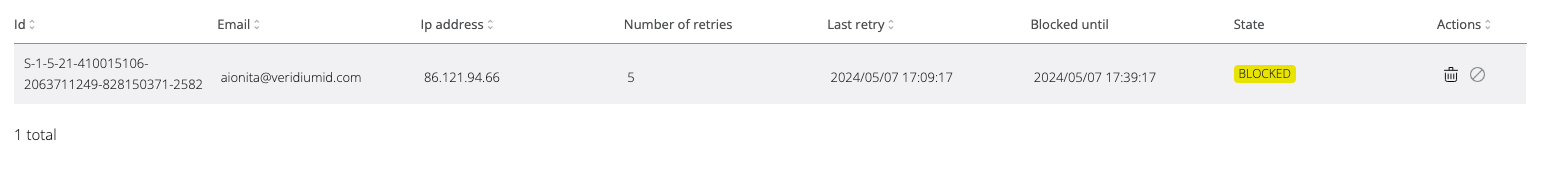
After reaching the maximum number of failed attempts, the user-IP combination will be blocked for a certain time (configurable).
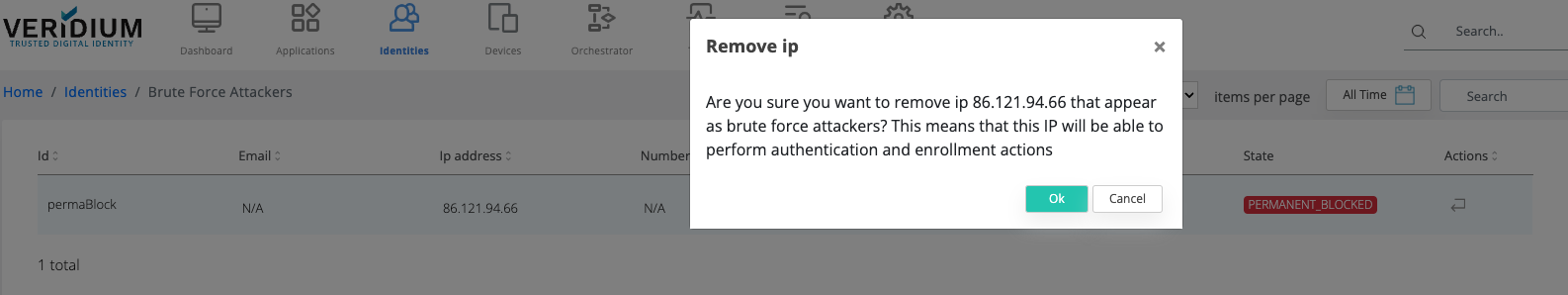
The administrator can delete an IP marked as an attacker.
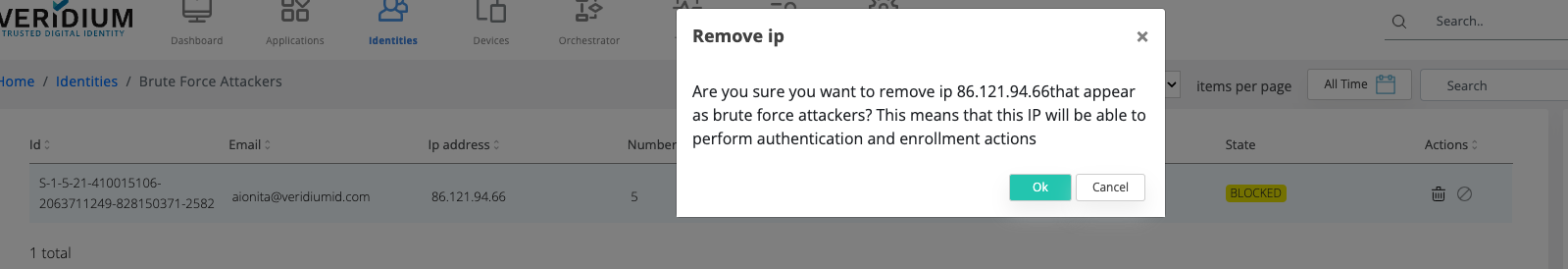
The administrator can permanent block an IP.
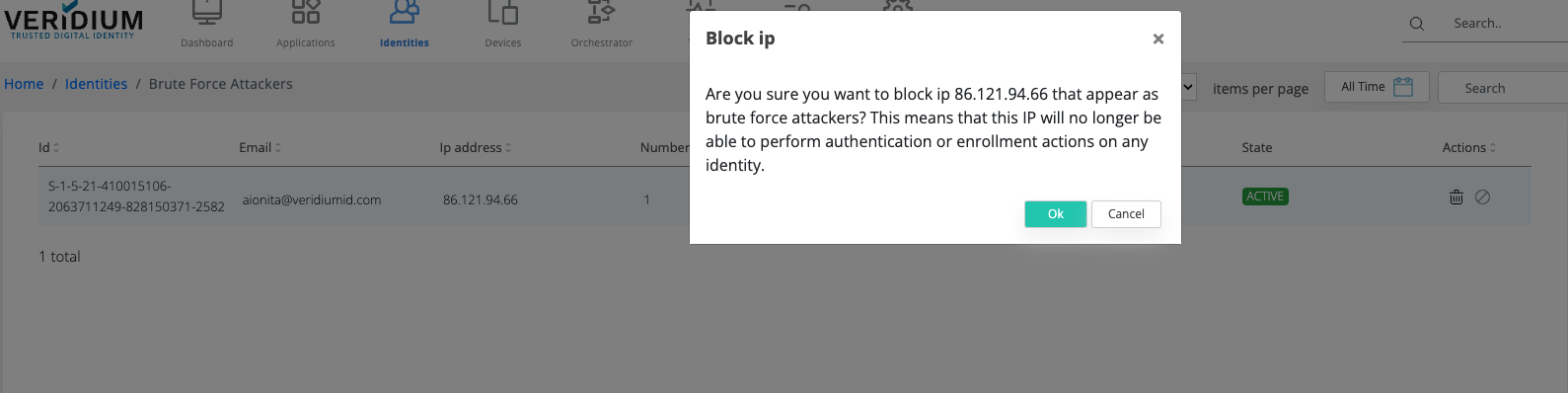
This action will block that IP for all present identities, and no identity will be allowed for enrolment/authentication coming from that IP address.

Administrator can revert the permanent block as well.
Functional aspects
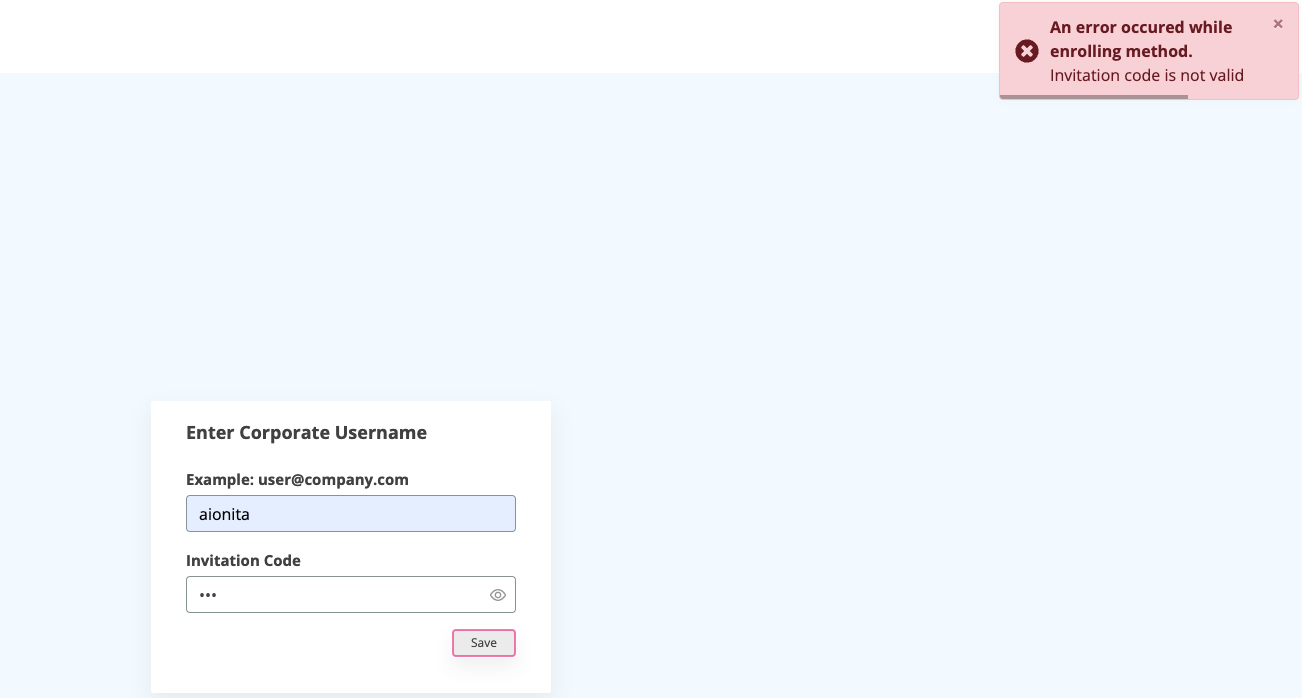
After N failed attempts on enrollment, the account will be blocked. At the enrollment step, the identity may or may not exist. In this case, the user's input will be blocked, i.e. aionita with the IP combination.

If an attempt to enroll the account is done again, it will fail when coming from the marked IP.
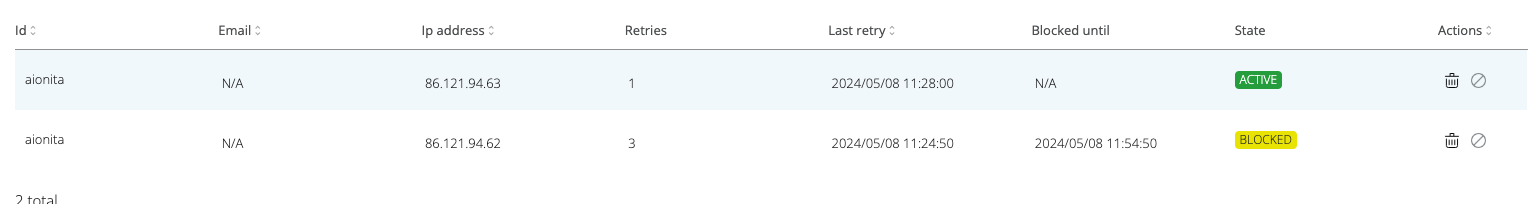
This only affects User+IP combinations. A user blocked from an IP will be allowed to resume flows from a different IP.
