Certificate pinning usage guide
Configure certificate pins
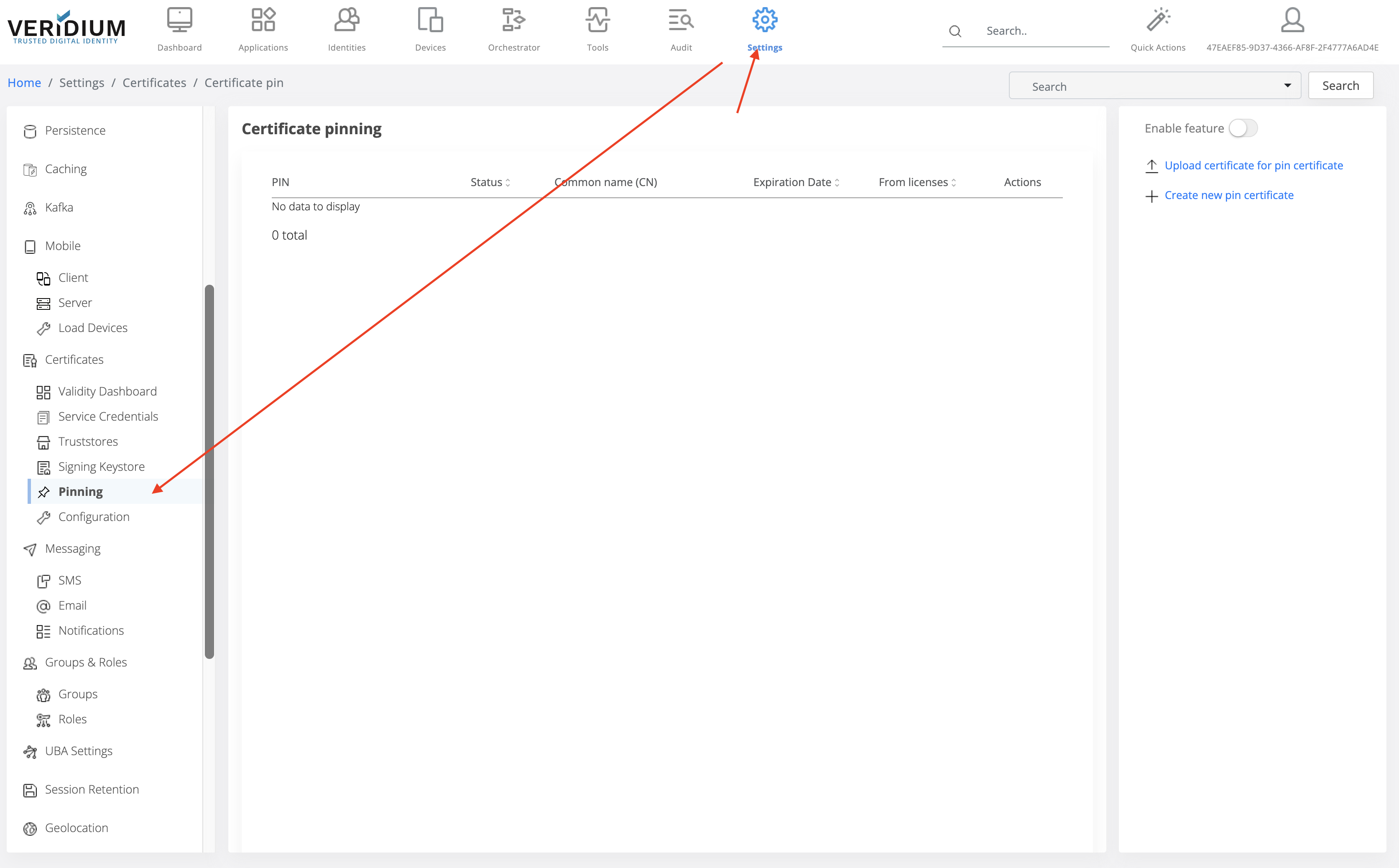
In order to configure certificate pins from administration page go to Settings / Certificates / Pinning
By default, the certificate pin table will be empty. You can upload a certificate pin using the actions on the right side of the screen or by enabling the feature and the table will be populated with the entries found.
The Enable feature button will upload all the pins from licensing into the certificate pins. Also, you can manually add a certificate pin, or you can import a .cer file or type the certificate content.
Note: the existing data visible after the feature is enabled and data is imported from licensing will not have CN, Expiration date, and will display Unknown status due to differences in format.
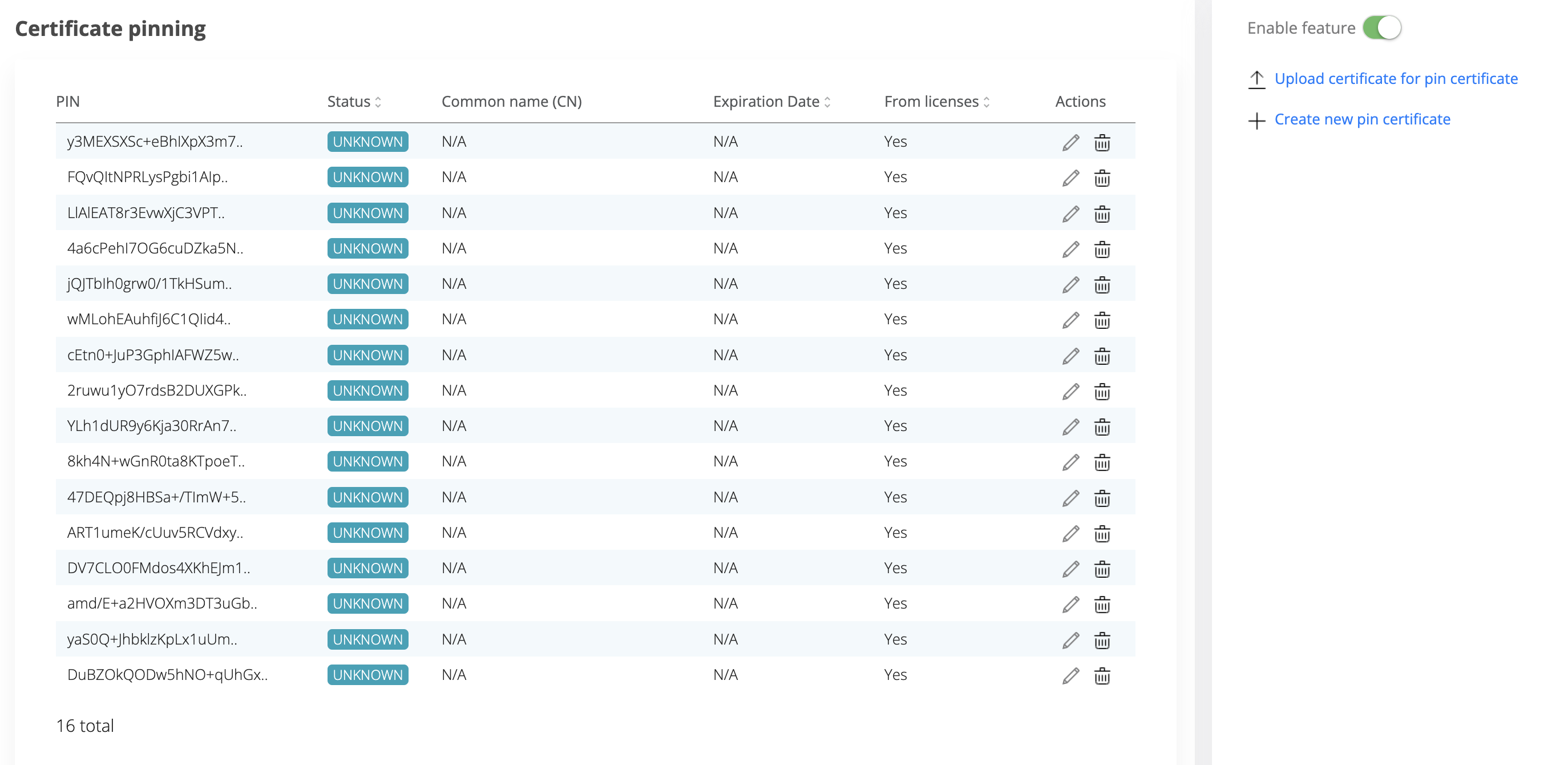
As you can see, after enabling this feature, the pins that are available in the licenses, are imported in the certificate pinning table.
Using the Upload by certificate flow
There are two options, pinning by certificate (you have to upload a .cer certificate) or by certificate content.
Method 1 (Upload .cer file)
After uploading the .cer file, press on Get certificate info
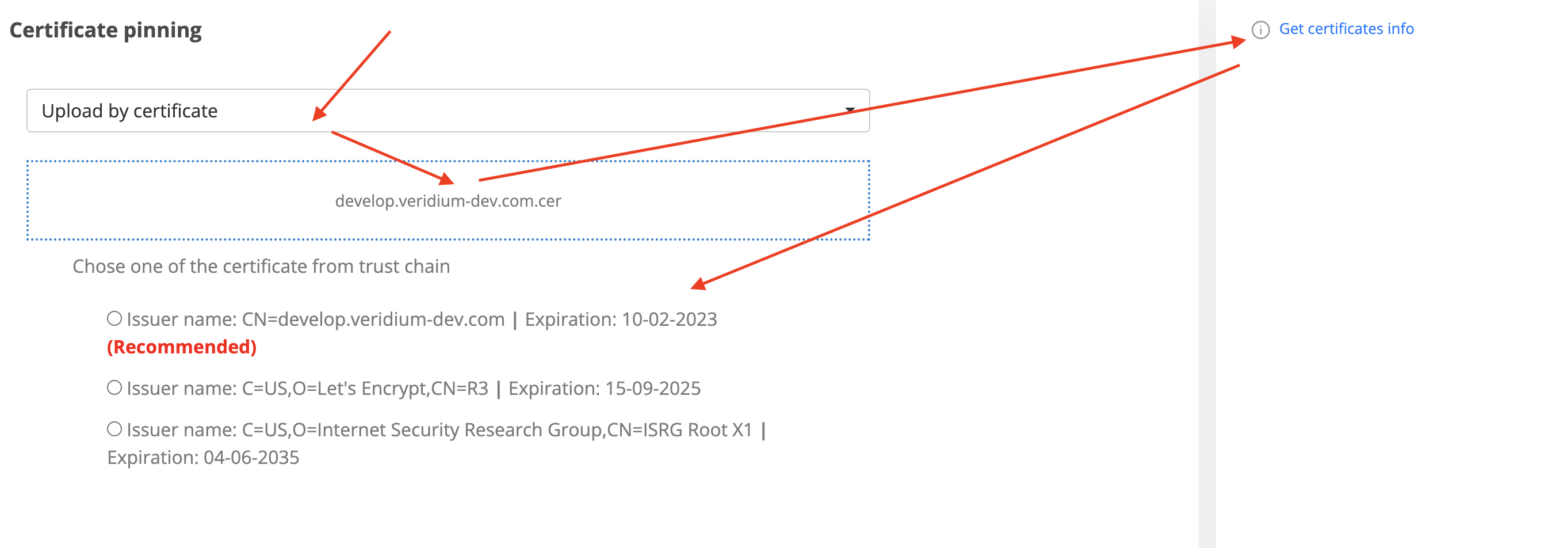
After getting the certificate information, we have 3 results with one of them that is recommended. The reason is that, the API return the trust chain of the uploaded certificate and the recommended one is the leaf option.
See https://sectigostore.com/blog/what-is-an-ssl-certificate-chain-how-does-it-work/
Method 2 (Type the certificate content)
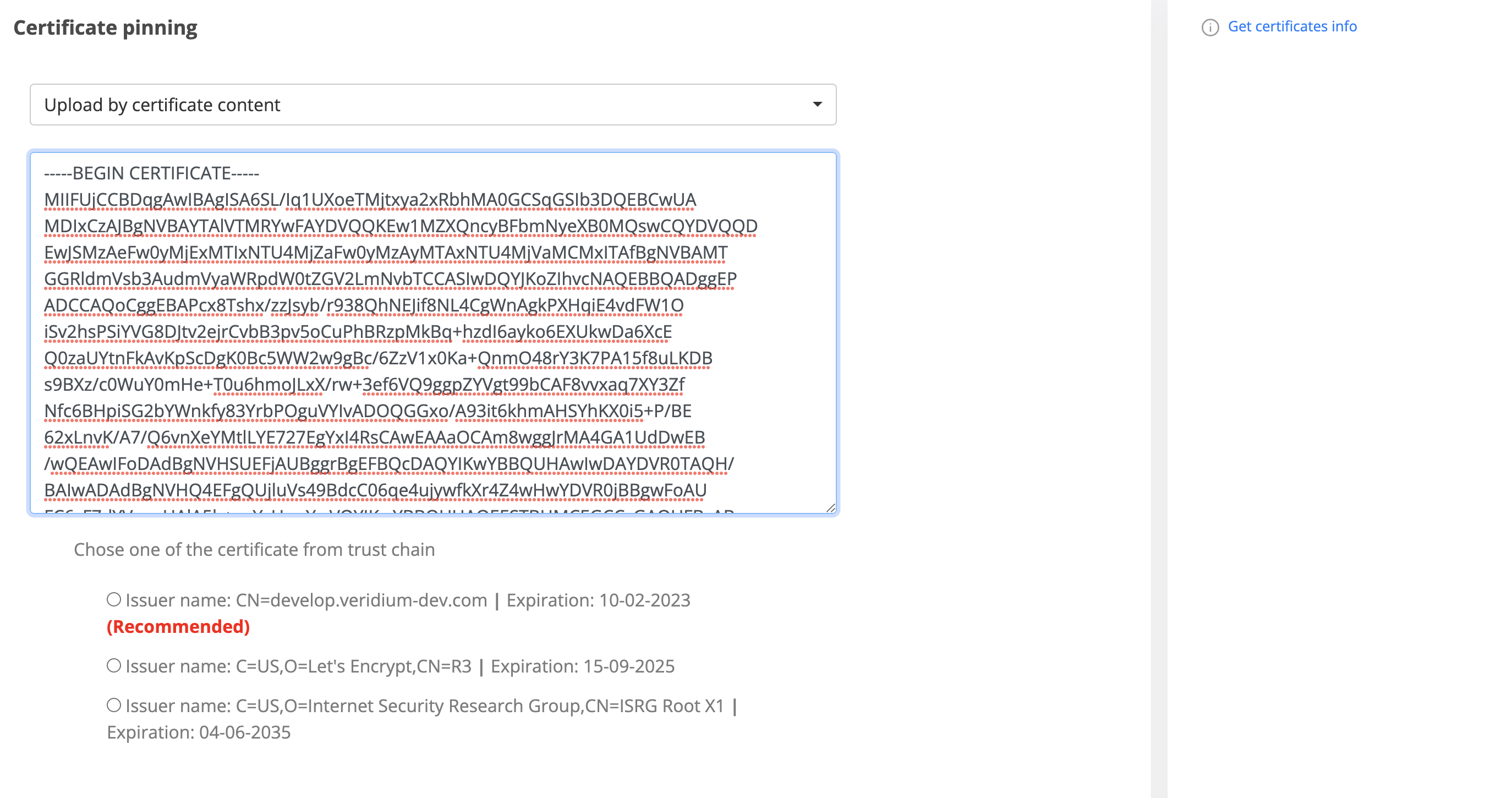
After typing the certificate content, the process is the same as for the first method.
There is another mechanism that verifies if the selected certificate is present or not in the truststore. If is not present, you have the option to add it to truststore, as detailed below.
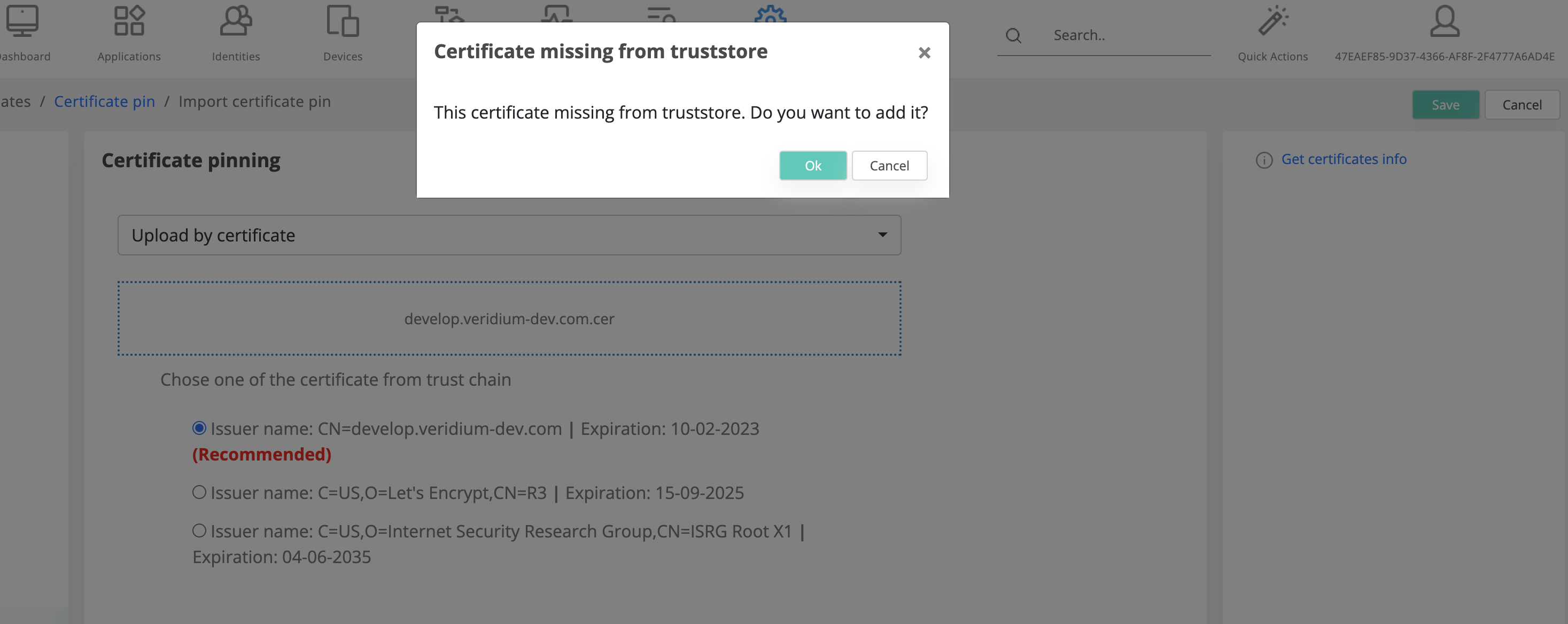
Choosing the Create new pin certificate
You can add new pin certificate manually, without any certificate or certificate content.
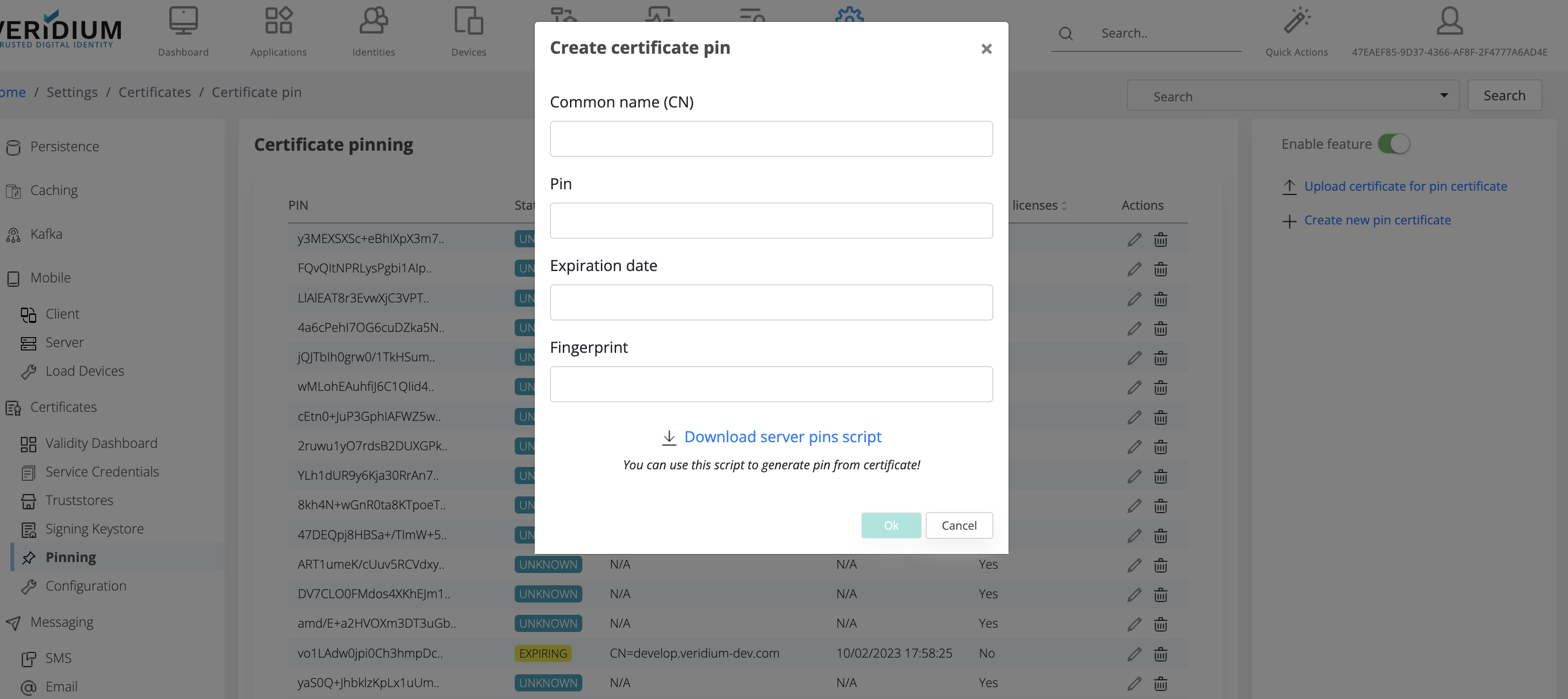
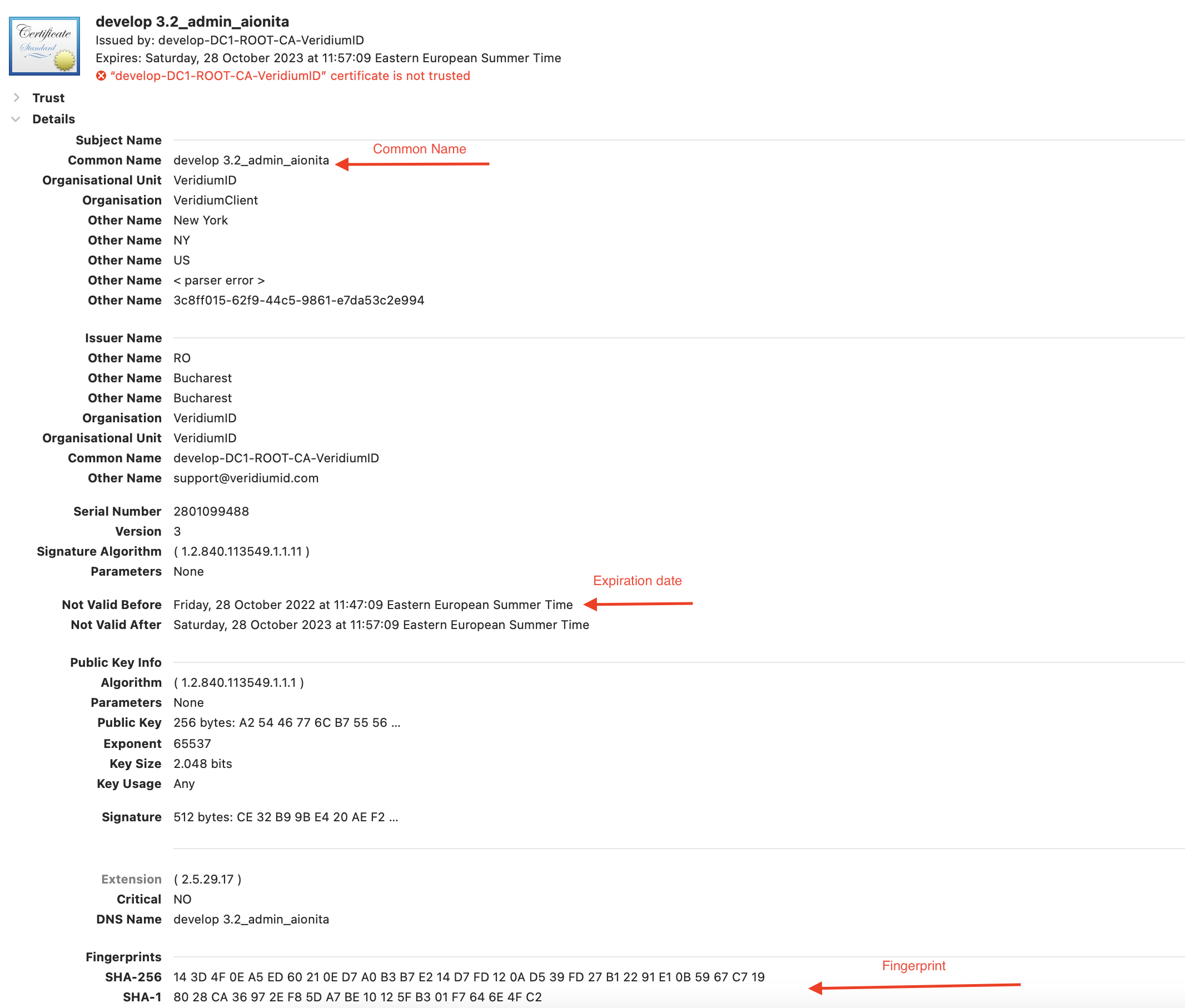
For the Common name (CN) you should chose the CN from the certificate, for pin you should use the script for pin generation, expiration date is taken from the certificate and fingerprint is also from the certificate, but it’s not mandatory.
Download server pins script will provide a script that offers you the possibility to generate the pin from a certificate that is already present on disk