Certificate Based Authentication
In version 3.6 Certificate Based Authentication was introduced in the Veridium IdP using mutual TLS validation for the Veridium Identity Provider.
Our goal is to further extend the Certificate Based interactions for Mobile Application registration during identity validation and enable the Certificate Based Authentication for Veridium Credential Provider and Veridium Authenticator.
The Veridium Platform is composed by multiple actors that may take part in the enrolment or the authentication workflow:
Veridium Windows Credential Provider (CP)
Windows component that enables the Veridium authentication for Windows logon.
Veridium Authenticator
Android/iOS mobile application that uses Veridium Mobile SDK to provide strong authentication using biometrics or pin.Veridium Self Service Portal (SSP)
Web application portal used for user self enrolment of the authenticators.Identity Provider (IdP)
The SSO component that enables the Veridium authentication for web applications. The Veridium IdP is based on Shibboleth and using the Veridium Web SDK other Identity Providers are natively supported:Microsoft AD FS
Ping Federate
ForgeRock Access Management
Keycloak
Oracle Access Manager
Authentication
The common policies that may be applied to the Certificate Based Authentication:
Username binding - in order to validate that certificate is bound to the user, this policy may be configured to extract the username from:
Principal Name - field inside Subject Alternative Name
Email - RFC822Name field inside Subject Alternative Name
Subject - extract from Certificate Subject Name
Issuer
Validates the User Certificate was emitted by a certain Certificate Authority
Validates the User Certificate against revocation using CRLs
Allows authentication using Veridium Authenticator PIV support
CRL Refresh Frequency - configure the refresh interval for CRL caching.
Veridium Authenticator
Using Veridium Authenticator for Certificate Based Authentication may be used to authenticate the user on a Web Application using the Identity Provider, to logon to a device or establish a VPN tunnel via RADIUS protocol. This approach provides an unified user experience across different integrations.
The following policies may be configured:
Enforce PIV smart card usage via NFC or USB
Specify Certificate Issuer for filtering the user certificates
Identity Provider
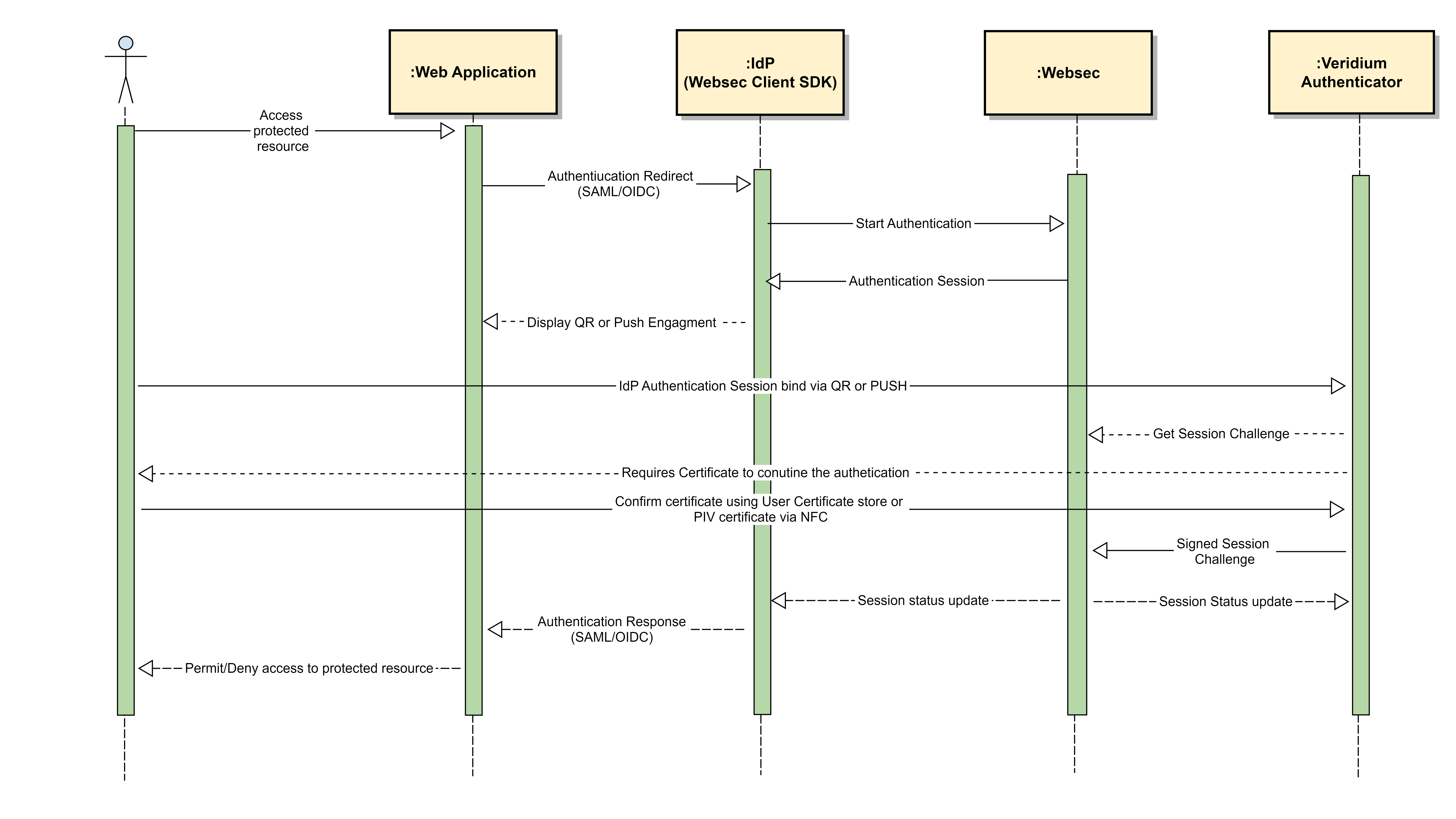
The identity provider may ask directly for Certificate Based Authentication to the user acting by call. This integration may provide the option to use the PIV certificate as logon credentials.
The following policies may be configured:
Use the PIV certificate as logon credentials
Specify Certificate Issuer for filtering the user certificates
Windows Credential Provider
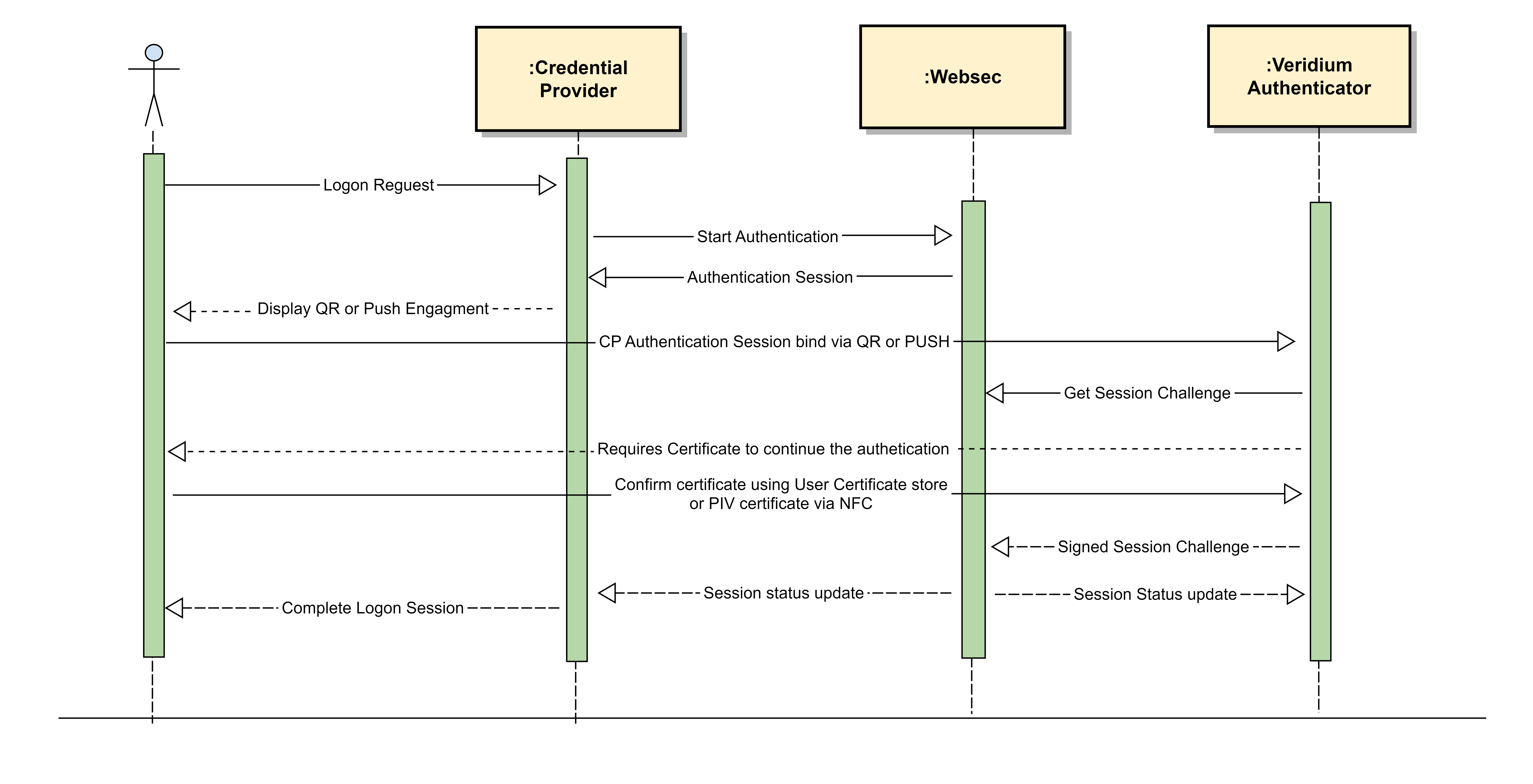
The credential provider may ask directly for Certificate Based Authentication to the user acting as a smart card logon. This integration may provide the option to use the PIV certificate as logon credentials.
The following policies may be configured:
Use the PIV certificate as logon credentials
Specify Certificate Issuer for filtering the user certificates
RADIUS
.png?inst-v=e06d4f32-3412-4bcb-9f3b-e67e23da25d7)
