CERTIFICATE authentication method
Certificate Based Authentication is integrated in the Veridium Orchestrator and may be used as an alternative for SPNEGO/Kerberos authentication providing enhanced configuration and flexibility of the authentication workflow.
Overview
CBA requires client certificate validation during the TLS connection and this should be configured on the service that provides SSL termination. The client certificate should be forwarded in base64 encoding using the X-SSL-Client-Der to the IdP connector.
Since the every browser will reuse the TLS connections if already setup, new IdP endpoints may be required to provide optional certificate validation. We recommend to use distinct connectors/hostnames to integrate for certificate based authentication to enforce certificate validation on the SSL Termination service. (if the idp is set on https://idp.veridiumid.local we may set the CBA service on https://cert.idp.veridiumid.local)
HAProxy Configuration
Uncomment the following areas in file /opt/veridiumid/haproxy/conf/haproxy.cfg and restart ver_haproxy:
frontend-shibboleth-cert-https-int
backend-shibboleth-cert-http-int
frontend-shibboleth-cert-https-ext
backend-shibboleth-cert-http-ext
Modify the file /opt/veridiumid/tomcat/conf/server.xml and restart ver_tomcat:
uncomment the 2 connectors: SHIBBOLETH EXT CERT and SHIBBOLETH INT CERT.
Configure the proper
proxyNameandproxyPortthat represents the name of the balancer that terminated the traffic.
Most probably, the SSL termination traffic is done on a different layer, in front of Veridium Services. If this is the case, please terminate there the traffic and validate the certificate against the CA. Also fill in the following header:
X-SSL-Client-Der. An example for the HAProxy may be found below:
frontend frontend-https-shib-certs
mode http
bind *:8946 accept-proxy ssl crt /etc/haproxy/server.pem ca-file /etc/haproxy/client-ca-shib.pem verify required
http-request set-header x-ssl-termination-proxy-secret PRROXYSECRET
http-request set-header X-SSL-Client-Der %{+Q}[ssl_c_der,base64]
default_backend backend-shib-https-certs
backend backend-shib-https-certs
mode http
cookie SRVNAME insert
server server-shib1 10.0.0.248:8946 cookie S10.0.0.248 check ssl verify none
server server-shib2 10.0.0.181:8946 cookie S10.0.0.181 check ssl verify none
server server-shib3 10.0.0.122:8946 cookie S10.0.0.122 check ssl verify none
IdP Configuration
After SSL Termination service configuration was completed, the next steps should be followed, either by altering the configuration file or using the GUI:
Configuration file:
In Veridium Manager navigate to Settings / Advanced / shibboleth / veridium-integration.json and complete the following fields:
In
internalServiceUrlset internal FQDN service url of the Shibboleth IdP. (e.g. https://idp.veridiumid.local)In the
externalServiceUrlset external FQDN service url of the Shibboleth IdP. (e.g. https://idp.veridiumid.com)Set the
userCertificateAuthnconfigurationinternalServiceUrl- internal FQDN service url of the Shibboleth IdP connector responsible for SSL Termination (e.g. https://cert.idp.veridiumid.local)externalServiceUrl- external FQDN service url of the Shibboleth IdP connector responsible for SSL Termination (e.g. https://cert.idp.veridiumid.com)proxySecret- if the SSL termination service uses a proxy secret, set it to this value.
"userCertificateAuthn": {
"externalServiceUrl": "https://cert.idp.veridiumid.local",
"proxySecret": "this_is_just_a_secret",
"internalServiceUrl": "https://cert.idp.veridiumid.com"
},
"internalServiceUrl": "https://idp.veridiumid.local"
"externalServiceUrl": "https://idp.veridiumid.com"Using Veridium Manager admin dashboard:
Parameters detailed above in the configuration file have a GUI controller also, found in Settings / Identity Provider / Configuration / Authentication tab:
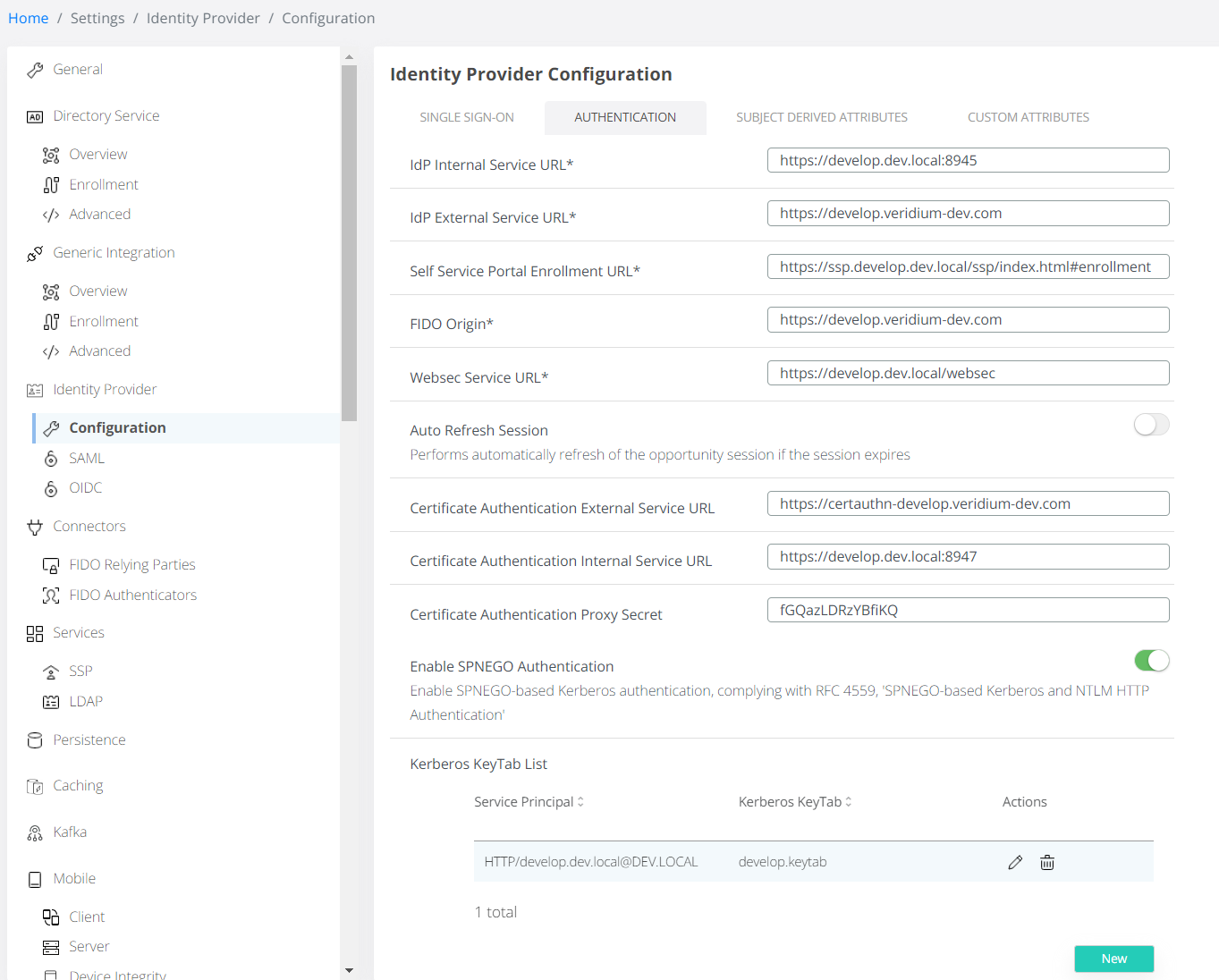
Authentication Method Configuration
In Veridium Manager navigate to Orchestrator / Authentication / Methods / Certificate and setup the following fields:
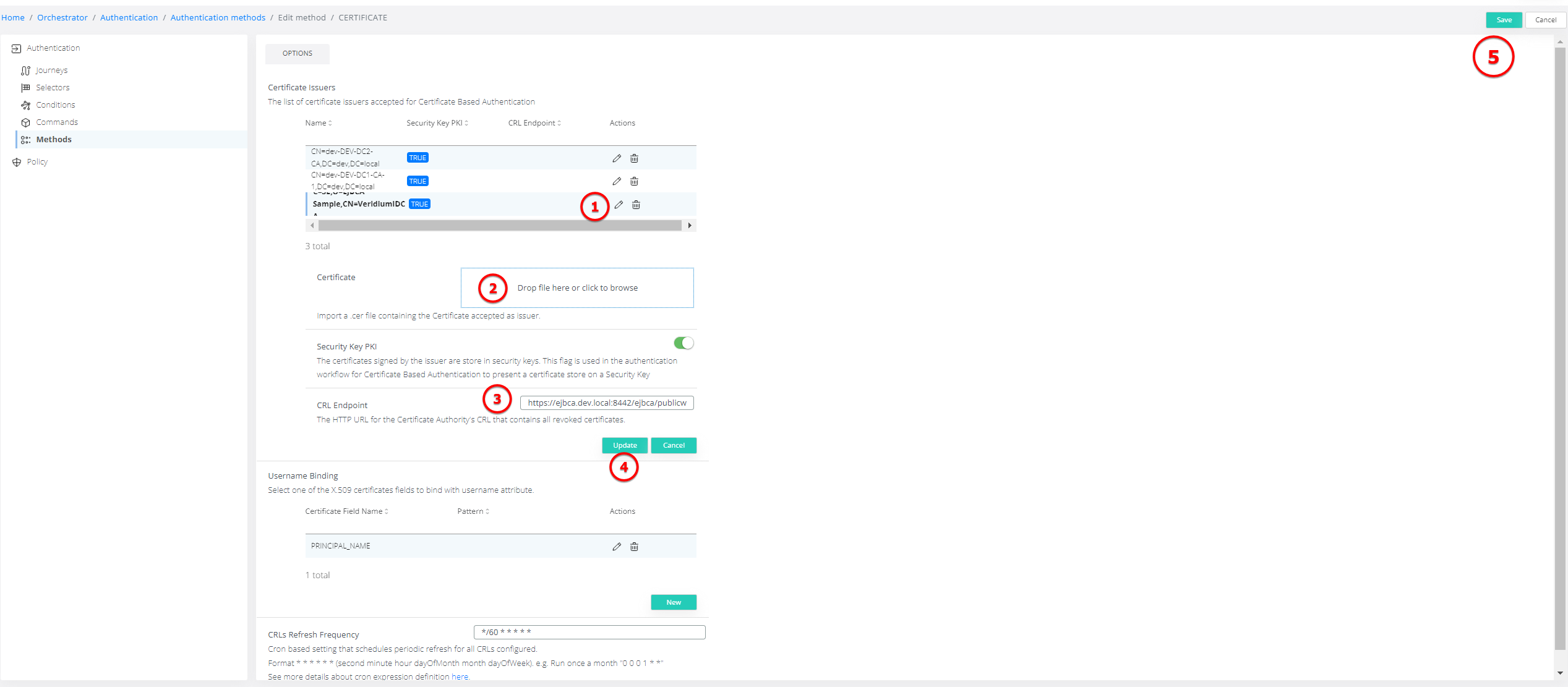
Certificate Issuer
PEM encoded Certificate Issuer of the User Certificates.
Security Key PKI - configures if the issuer is used for certificates stored on the Security Keys for Certificate Based Authentication. This flag allows the Veridium Authenticator to be used for authentication and use a security key for completion (e.g. Yubikey with PIV configured)
CRL Path - the CRL path URI used for certificate revocation. Only HTTP(S) is supported. The CRL server certificates must be imported in the Veridium Truststore.
Username Binding
Provides binding between the certificate field and the username. The username will be used further for identity lookup in the configured Directory Service. We recommend to use Principal Name or RFC822 Name
Principal Name - extract from Subject Alternative Names from the Other Name field. In general this is configured in the PKI to user principal name.
RFC822 Name - extract from Subject Alternative Names using RFC822 Name field. In general this is configured in the PKI to email address of the user.
Subject- extract from the certificate’s Subject field. Also a pattern (Regular Expression) to extract the username (e.g.
CN=([^,\\\\/]+).
CRLs Refresh Frequency
The CRLs are cached in Veridium Datalayer and are used during the authentication to validate the certificate revocation status. This filed allows configuration for the refresh intervals.
Change of CRL cache refresh frequency requires either application restart for websecadmin service. If the CRL cache refresh frequency is already configured, the new frequency is taken into consideration for the next cache refresh execution.
Orchestration
Certificate Based Authentication may be used at any time in the authentication workflow as single factor or as a second factor in an MFA journey. Based on this the following configuration orchestrator configuration were introduced:
CBA as single/first factor
When using CBA as Single Factor or as First Factor, the Veridium Orchestrator Selector has now the option to use Certificate as User Engagement. Also in the Journey, the first challenge should contain certificate method.
Auto select client certificate policy
https://chromeenterprise.google/policies/?policy=AutoSelectCertificateForUrls
