CA certificate renew keeping issued certificates valid
This article will provide a step by step procedure to renew the Internal Certification Authority and keeping existing certificates valid.
In order to see when CA will expire, please go in WebsecAdmin → Settings → Certificates → Signing Keystore.
Script used for this procedure: /etc/veridiumid/scripts/renew_ca.sh
Usage: ./renew_ca.sh <args>
--create -> Creates the new CA from old one from old one present in Zookeeper configuration.
This step also uploades the new certificate to Zookeeper.
--renew -> Generates new certificates from the CA present in Zookeeper depending on the node
(HaProxy certificate for Webapp, Cassandra, Elastic or Kafka for Persistence
-h/--help -> The usage of the script
--days=NO_DAYS -> The validity of the certificates. The default value is 3650 days.
1) Renew Certificate Authority
On a single node run the following command as either veridiumid or root user:
bash /etc/veridiumid/scripts/renew_ca.sh --create
or in case of prefering a different valability of the certificate (default 10 years).
bash /etc/veridiumid/scripts/renew_ca.sh --create --days=NO_DAYS
Where NO_DAYS is the total number of days the CA and all other certificates will be valid, for example 365 for 1 year.2) Renew Persistence and Webapp certificates
2.1) Renew Persistence certificates
On all persistence nodes run the following command as either veridiumid or root user:
bash /etc/veridiumid/scripts/renew_ca.sh --renew
or in case of prefering a different valability of the certificate (default 10 years).
bash /etc/veridiumid/scripts/renew_ca.sh --renew --days=NO_DAYS
Where NO_DAYS is the total number of days the CA and all other certificates will be valid, for example 365 for 1 year.After the command has finished its execution the following services must be restarted by running the following commands as root user:
service ver_cassandra restart
# In case ElasticSearch is used
service ver_elasticsearch restart
# In case Kafka is still used
service ver_kafka restart2.2) Renew Webapp certificates
On each webapp nodes run the following commands as root user to stop services:
service ver_websecadmin stop
service ver_tomcat stop
service ver_fido stop
service ver_selfservice stop
service ver_opa stop
service ver_haproxy stop
service ver_freeradius stop
# In case statistics and notifications are still used
service ver_notifications stop
/opt/veridiumid/statistics/bin/statistics-manager.sh stopRun the following command as either veridiumid or root user:
bash /etc/veridiumid/scripts/renew_ca.sh --renew
or in case of prefering a different valability of the certificate (default 10 years).
bash /etc/veridiumid/scripts/renew_ca.sh --renew --days=NO_DAYS
Where NO_DAYS is the total number of days the CA and all other certificates will be valid, for example 365 for 1 year.On each webapp nodes run the following commands as root user to start services:
service ver_websecadmin start
service ver_tomcat start
service ver_fido start
service ver_selfservice start
service ver_opa start
service ver_haproxy start
service ver_freeradius start
# In case statistics and notifications are still used
service ver_notifications start
/opt/veridiumid/statistics/bin/statistics-manager.sh start3) Renew friend and default certificates
Access the Admin Dashboard and navigate to Settings → Service Credentials.
To renew friend certificates click on +Renew next to each entry under System Services.
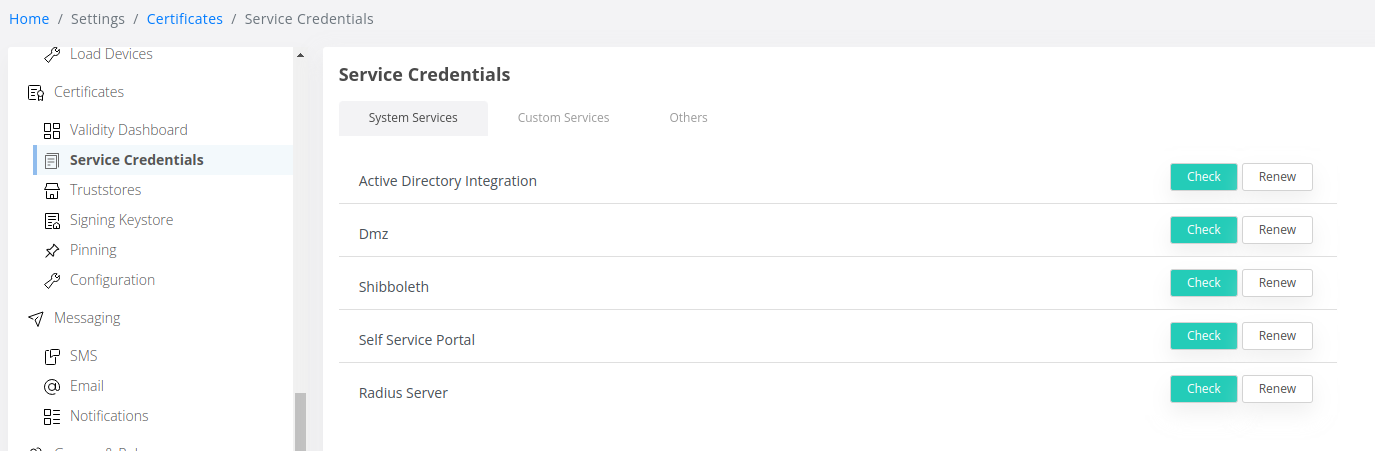
To renew Default certificates navigate to Settings → Service Credentials → Others:
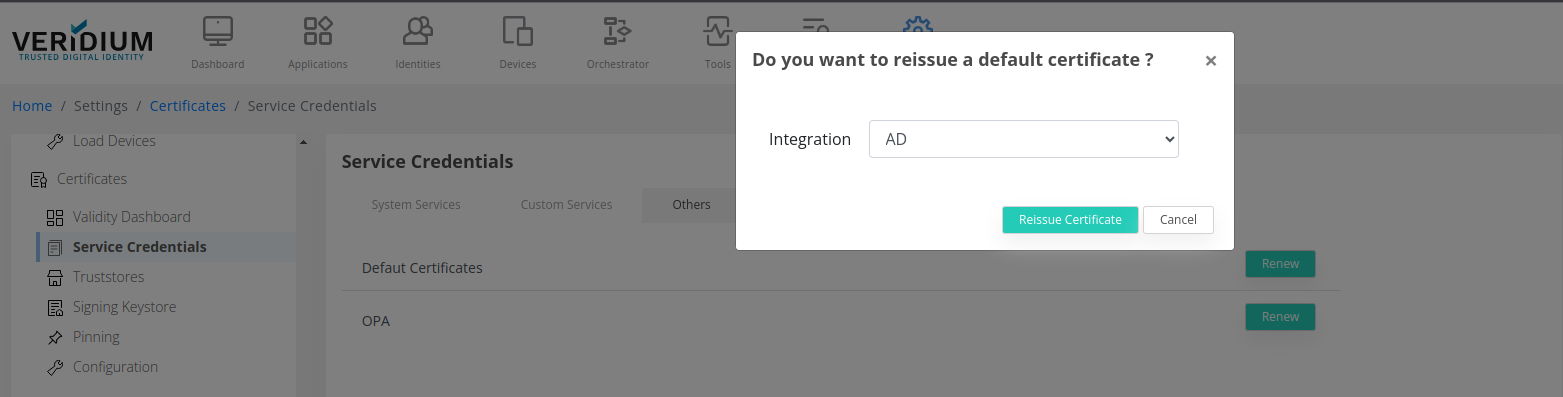
Click on Renew next to Default certificates and afterwards on Reissue Certificate in the new pop-up that appears.
To renew the OPA certificate in the same window click on Renew next to OPA entry and copy the archive to all webapp nodes.
On each webapp node run the following command as root user:
WEBSECADMIN_URL=`cat /opt/veridiumid/opa/conf/opa.yaml | grep url | cut -d"/" -f3 | tr -d [:space:]`
bash /opt/veridiumid/opa/bin/config-opa.sh -a ${WEBSECADMIN_URL} -c PATH_TO_COPIED_ARCHIVE
where PATH_TO_COPIED_ARCHIVE is the full path to the archive copied to the node, for example /tmp/opa-cert.zipAfter running this command restart the OPA service by running this command as root user:
service ver_opa restart4) In second datacenter
take from config.json certStore part from DC1 and copy to DC2 (from websecadmin)
take truststore.json from DC1 and copy to DC2.
run the following command on all servers
CODEbash /etc/veridiumid/scripts/renew_ca.sh --renewrestart first the persistence nodes and after that the webapp nodes.
CODEver_stop ver_startRegenerate certificate in second datacenter from websecadmin.
