User segregation
This feature allows Veridium Admins granular access to Active Directory users according to their permissions and it is strongly related to “Administrators managed by Active Directory” feature introduced in previous version.
For example a Support role may be configured to only see users from a specific AD group (such as “End Users”), while an Admin role may be configured to access all AD groups found (other Admins, End users, Support etc. ).
This feature impacts Identities and Sessions views. Devices are not affected by segregation and their views are not restricted by the new “View all users” permission. They are controlled from the original role assigned to the Veridium User (i.e. “TechSupport”, “Admin”).
Overview
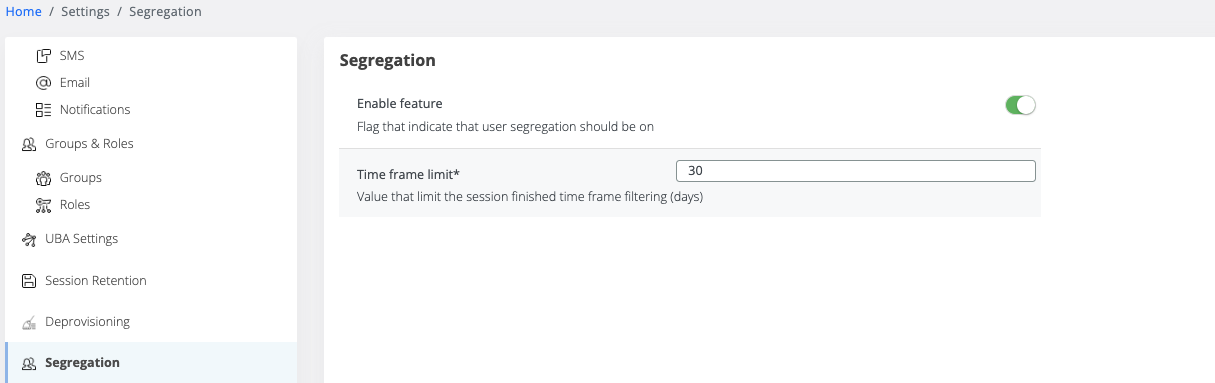
A new configuration has been added in Veridium Manager - Settings - Segregation tab to turn the feature ON or OFF:
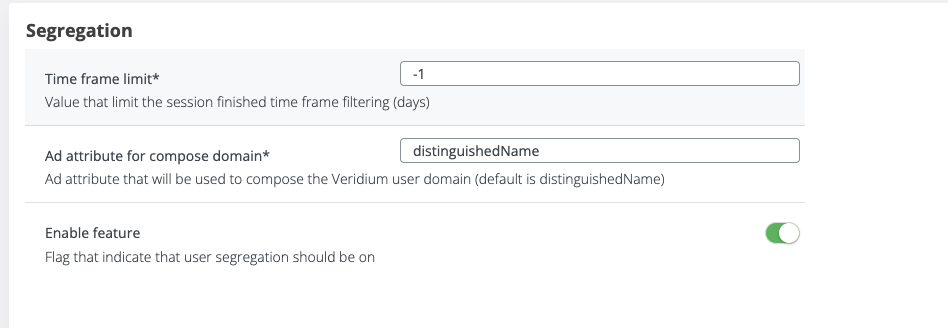
If this feature is enabled, the server will check the “View all users” permission availability for the current user. If the permission is assigned for the current user, then all AD users will be listed & available for operations.
If the permission is not found for the current user, then the view will be restricted to the current user organization.
This new permission (“View all users”) is designed to only work together with system access permissions. Using it standalone for a role/group will not produce desired results, because permissions to access the Veridium Manager UI are also needed.
Example: for a user to be able to use the functionality, its role/group needs to have “View all users” + “TechSupport” permissions set.
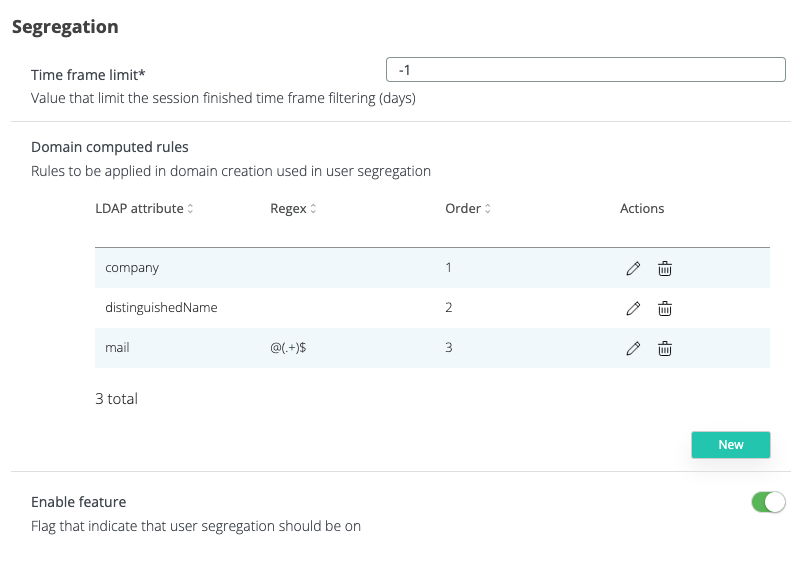
Time frame limit refers to limitation on Audit → Authentication sessions. If value is greater than 0, the finished sessions are not segregated but a time limit is imposed with the value from the configuration. This is implemented because migrating large data sets (such as sessions from a large past timeframe) consumes a lot of resources and does not provide justified advantages compared to processing costs.
Domain computed rules is a list of LDAP attributes that our system should search for in order to compute user domain. This is an elastic mechanism for those who have a not well defined structure in LDAP. For example, our server will search first for company attribute, if the attribute is found and it’s not empty, the user domain will be computed based on that attribute. If that attribute is not found or has an empty value, the server will search for the next attribute, distinguishedName and so on. The order is given by the Order field in that list of attributes.
For example, a specific AD attribute with a specific value can be added to desired accounts and filtering will be made according to it.
Example:
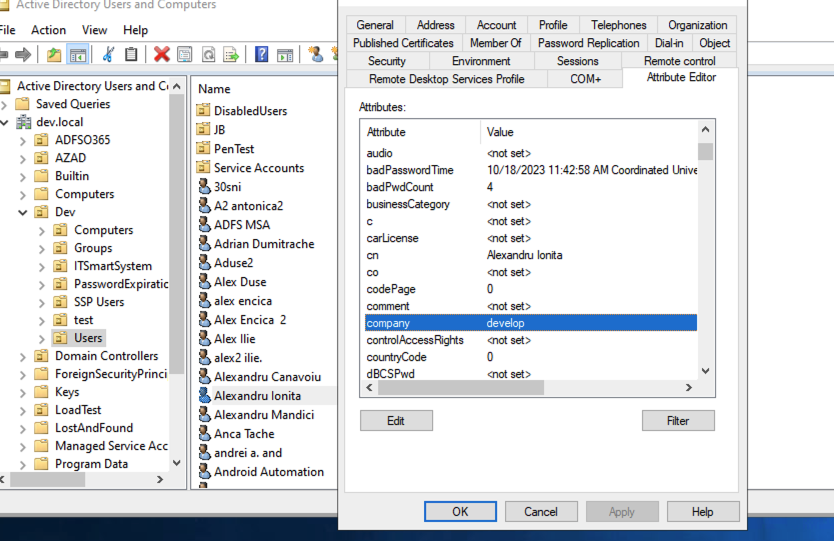
We will use a new AD attribute for domain, called company, having develop value.
Next step, we have to make sure that we have the AD attribute in our custom extended attributes. For this, we have to go to Settings → Services → LDAP → Extended Attributes tab → Manage extended attributes.
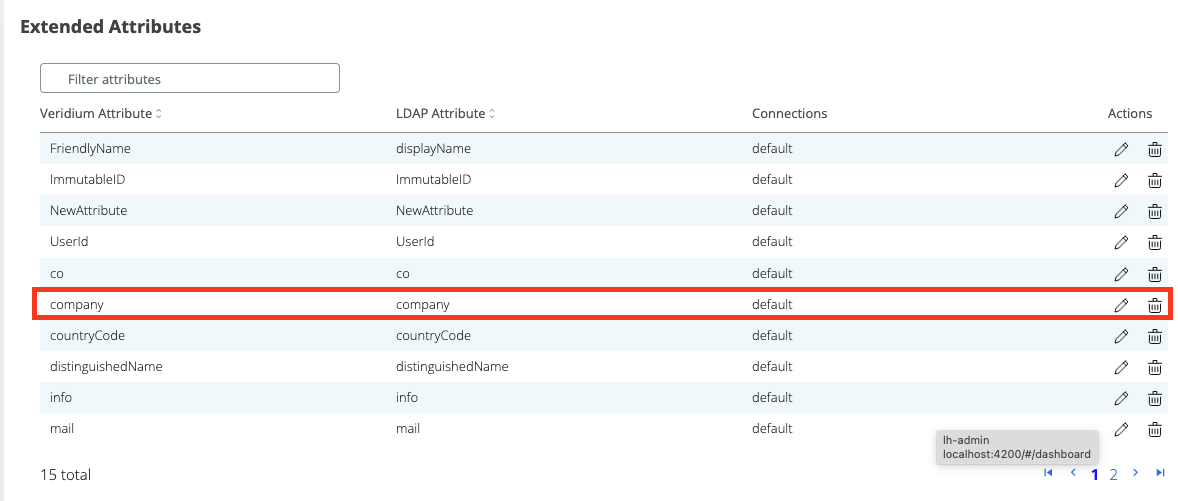
If the new custom attribute is not present in the table, you have to create it.
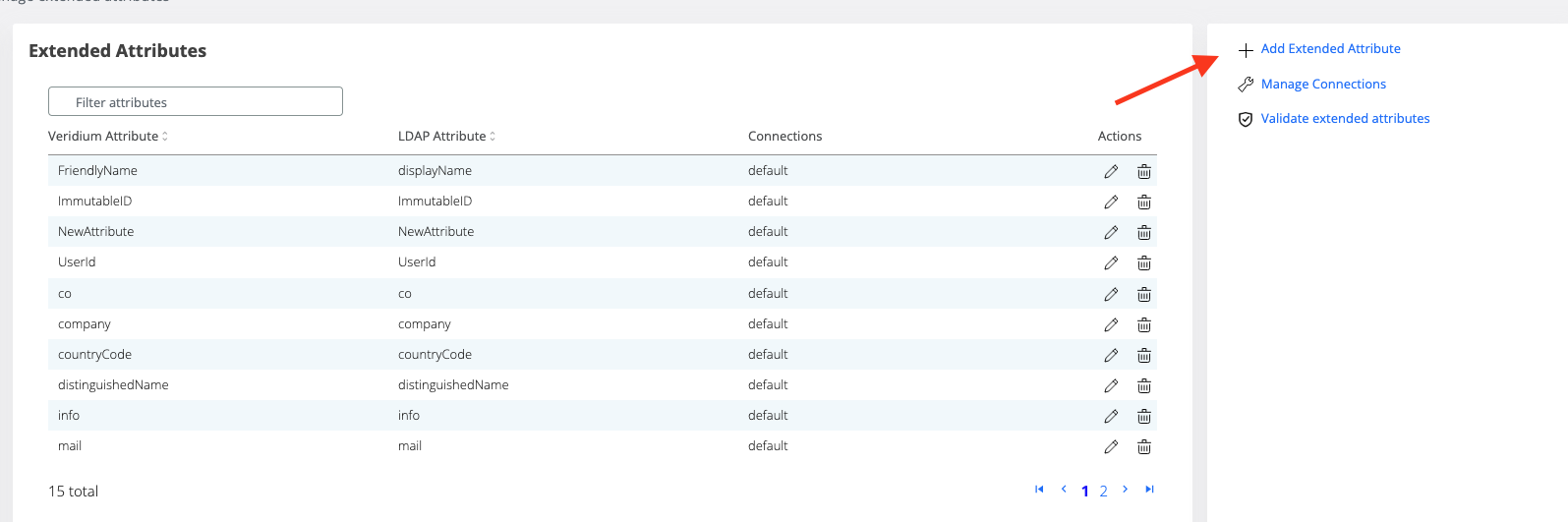
Next step, we go again in Settings → Services → LDAP → Extended Attributes tab and we will have to do the mapping between the AD attribute and the Veridium attribute.
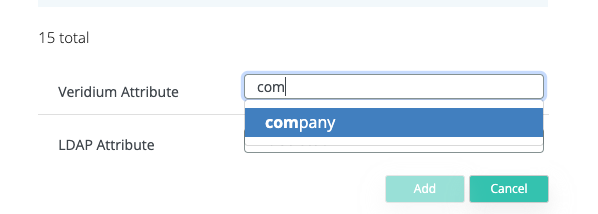
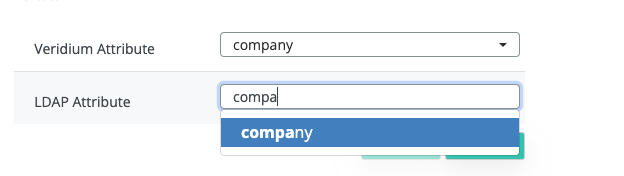
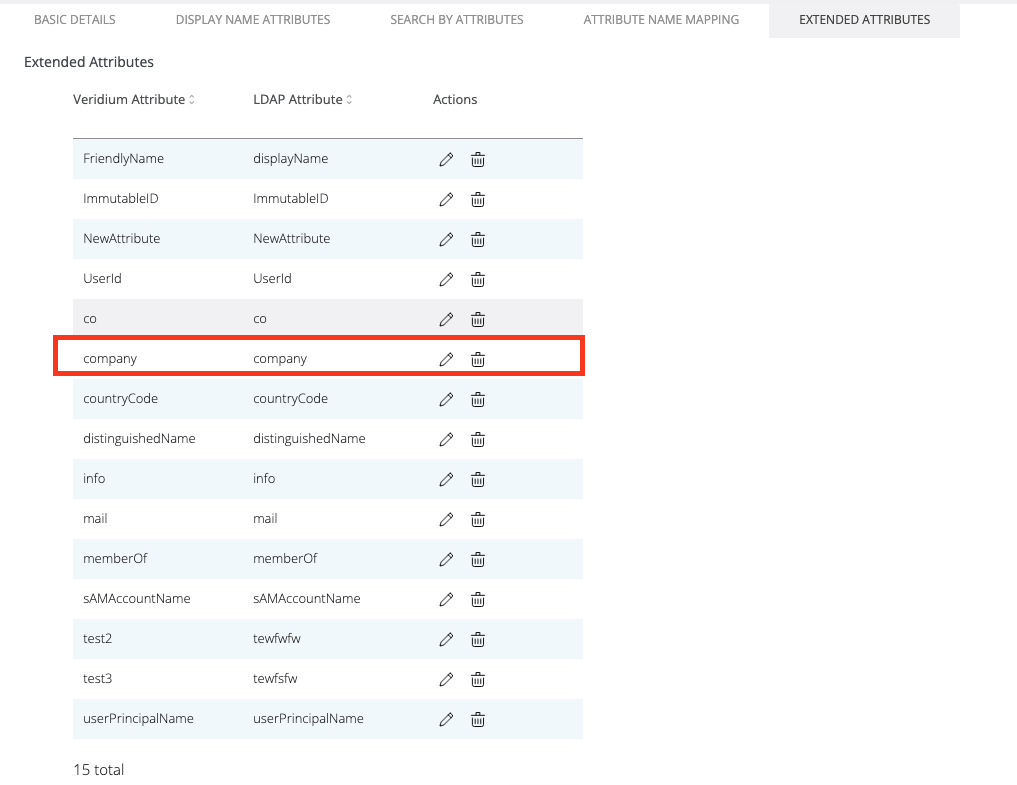
Next step is to go to Settings → Segregation and set the new attribute in the Ad attribute for compose domain.
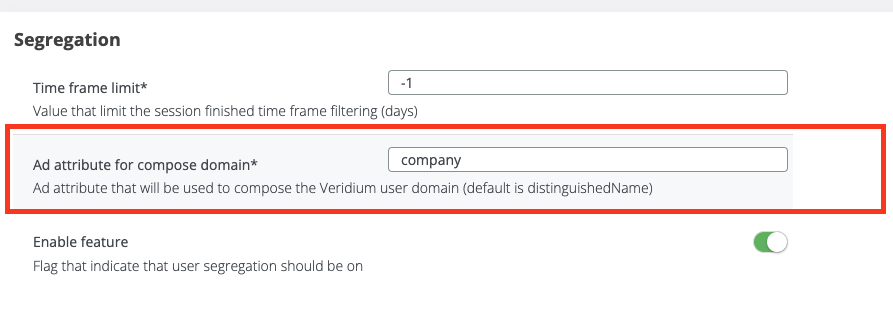
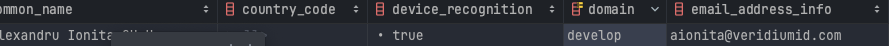
As you can see, the new domain is set on the account and the filtering will be done according to it.
Migrate existing data
In order to benefit from user segregation, profiles, accounts and sessions should have the domain.
For identities, there is a new internal tool that synchronize every existing identity with the AD information.
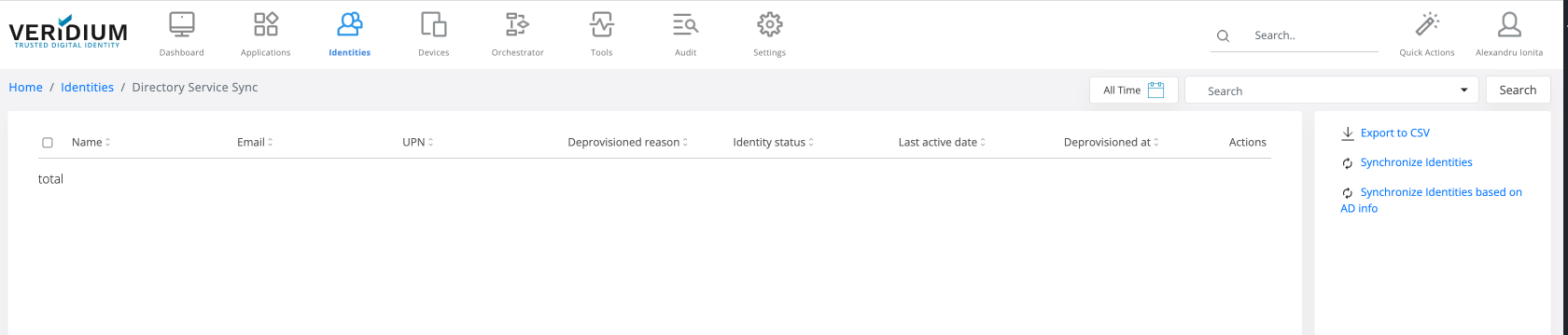
Every enrolment/authentication that identity made, will update information with the new values (domain and distinguishedName) from AD.
For accounts, there is a filter on Veridium Server that, for every request made, the admin will be updated based on AD. However, we added a time threshold to avoid multiple AD calls, calls that make the system slower.
For sessions, there is no action to migrate every old session to add the new domain, but, we added the time threshold (Time frame limit parameter described above) on the audit sessions, to not see sessions older than X (configured value) days.
Permission
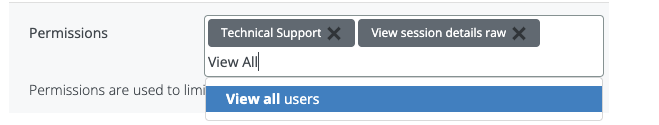
This feature added a new permission “View all users”, permission that gives the admin the power to see all users in the system.
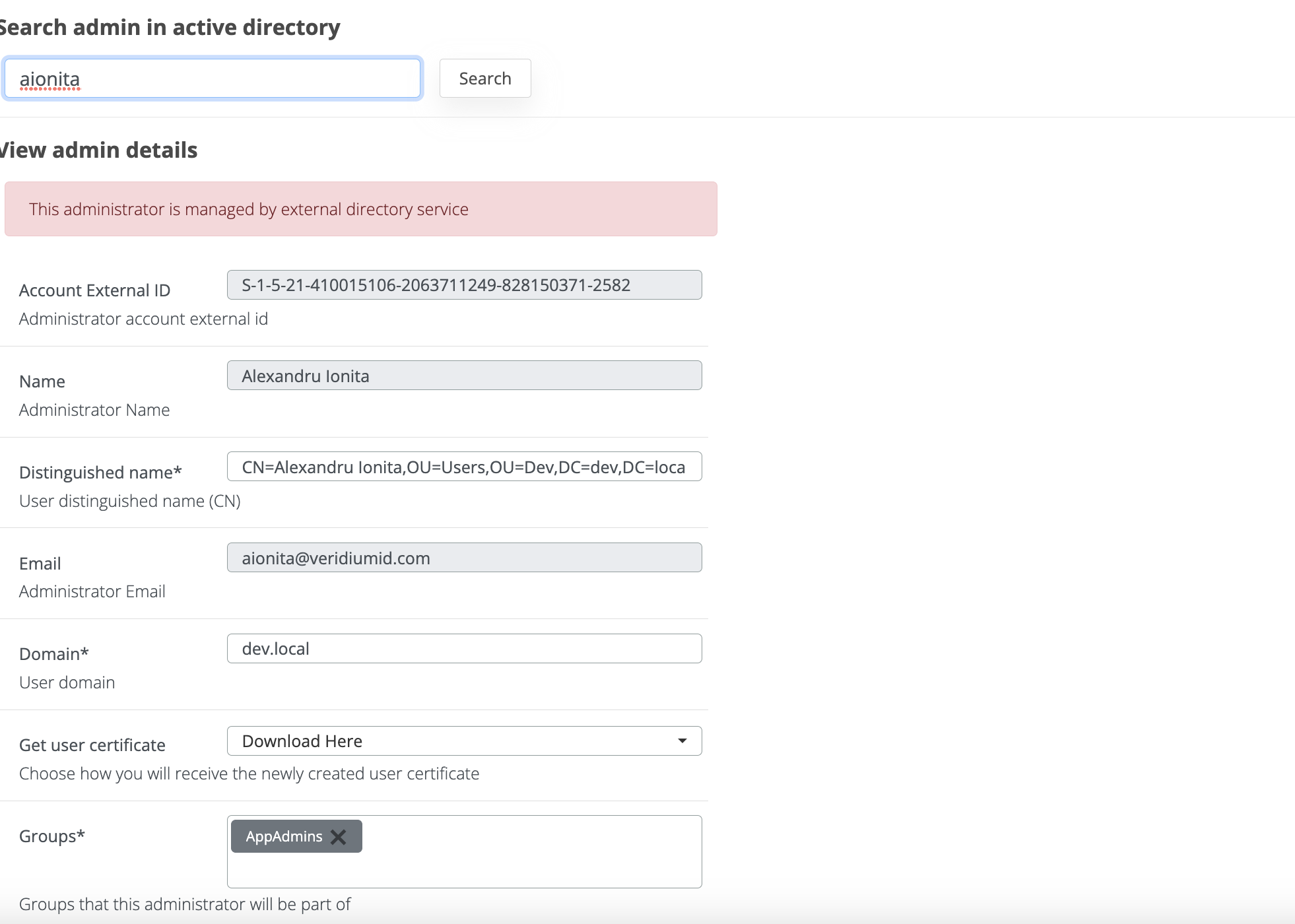
Account
Changing the Identity data model was not enough to be able to do this feature working. For that, we added in the Account data model the domain field.
Every admin should have a domain based on that we can filter the users.
For existing administrators, the domain field will be updated on the login step in Veridium Admin.
For new administrators, there are two options:
→ Administrator created using the AD import, then the domain will be automatically imported from the AD information.
→ Administrator created without that AD feature, then user will need to specify what is the administrator’s domain.
Session and Session Finished
For the segregation feature, we have to segregate also the sessions of an user.
Because of the risk of inconsistency for old sessions, if the user segregation is enabled and the user does not have the permission to view all users, there will be a limitation of the time frame filtering for the sessions, limitation which can be configured.
The purpose of this limitation is to avoid possible data inconsistency.
