SAML auth
This method uses the existing Veridium enrollment and authentication flows' configuration for Veridium Manager admin login.
This requires an existing user in a Directory Service connected to Veridium via LDAP. Administrators would enroll via the Self-Service Portal and be assigned the corresponding permissions based on AD group membership mapping that is already present in previous versions. User attribute sync will be done during authentication, so when entering the Veridium Manager at the end of a successful authentication, the user will be presented with the appropriate permissions inside it.
Authentication is done through Shibboleth which is configured to consider Veridium as both the Service Provider and the IdP for this scenario.
To enable SAML authentication within Veridium Manager, it is imperative to initiate the process by confirming the existence of a well-configured application entry for "veridium-manager." This verification can be performed by navigating to the "Applications" section in the management console.
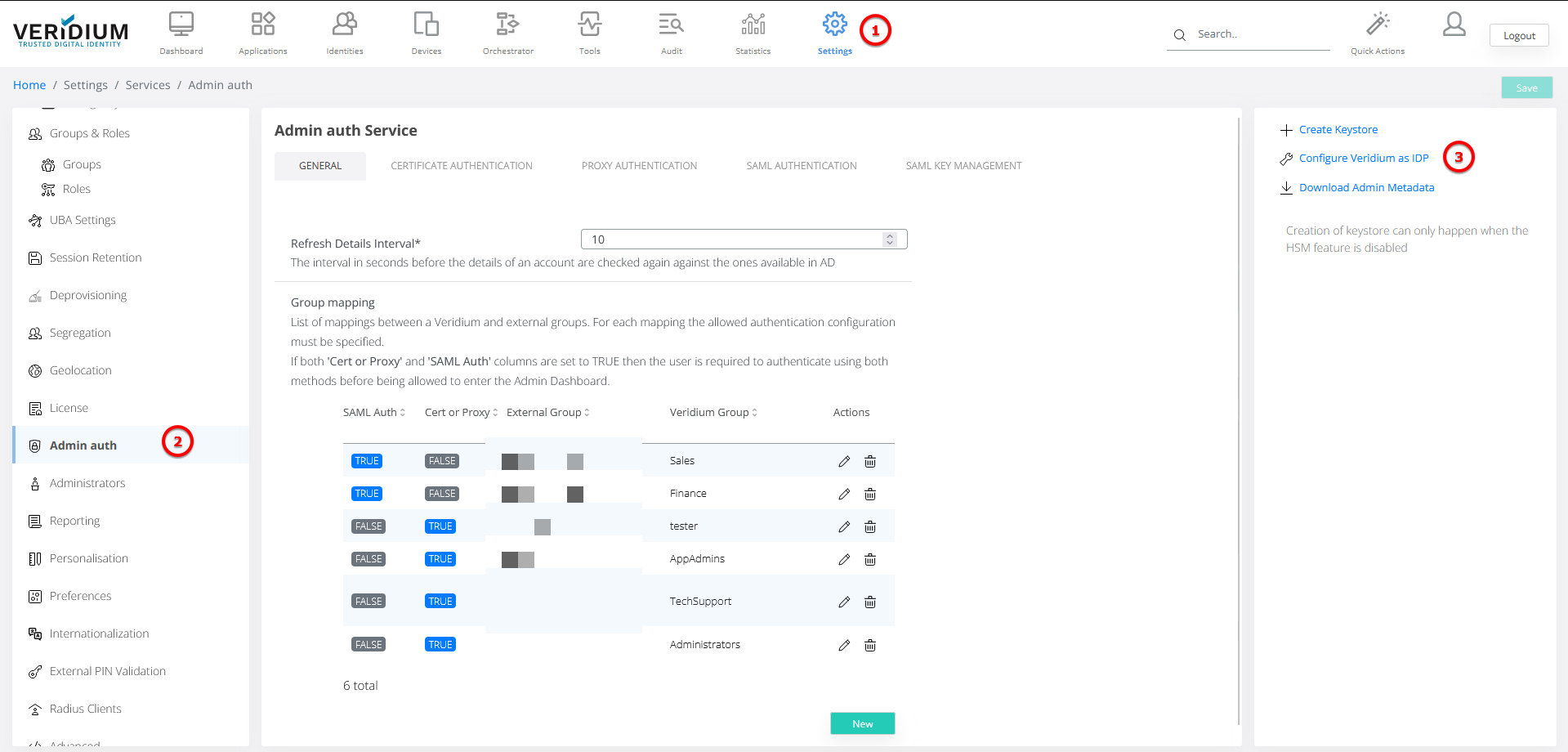
If the application setup is not in place, you can proceed by visiting the "Admin Auth Settings" page. Within the SAML submenu, the initial step involves thorough verification of the URL placeholders to ensure they are correctly updated. Following this crucial verification step, you can proceed to configure Veridium as the Identity Provider (IdP) by selecting the appropriate action from the menu on the right side of the page.
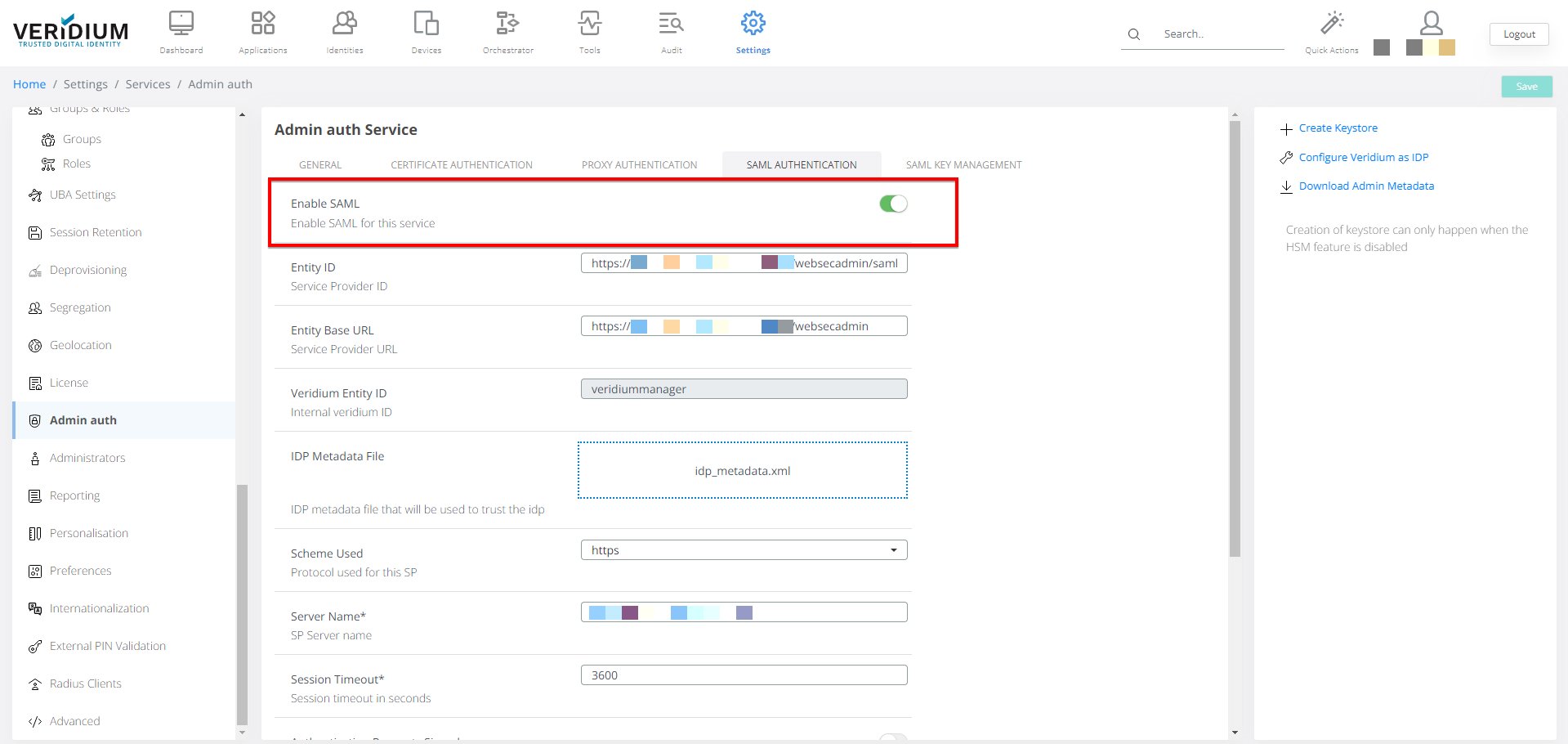
With all the necessary configurations in place, you can seamlessly activate SAML authentication by simply toggling the switch located within the "General" submenu of the "Admin Auth Settings" page and make sure that you groups are allowed to use SAML.
More information regarding SAML authentication can be found here
