Proxy auth
Another mechanism in place for authenticating and authorization in Veridium Manager is by using an external Single Sign-On Service that will forward specific custom headers to the admin application in order to identify, validate and authorize the user. This is done via internal operations by querying the repository connected via an LDAP connection and further apply logic to compute the user assigned permissions.
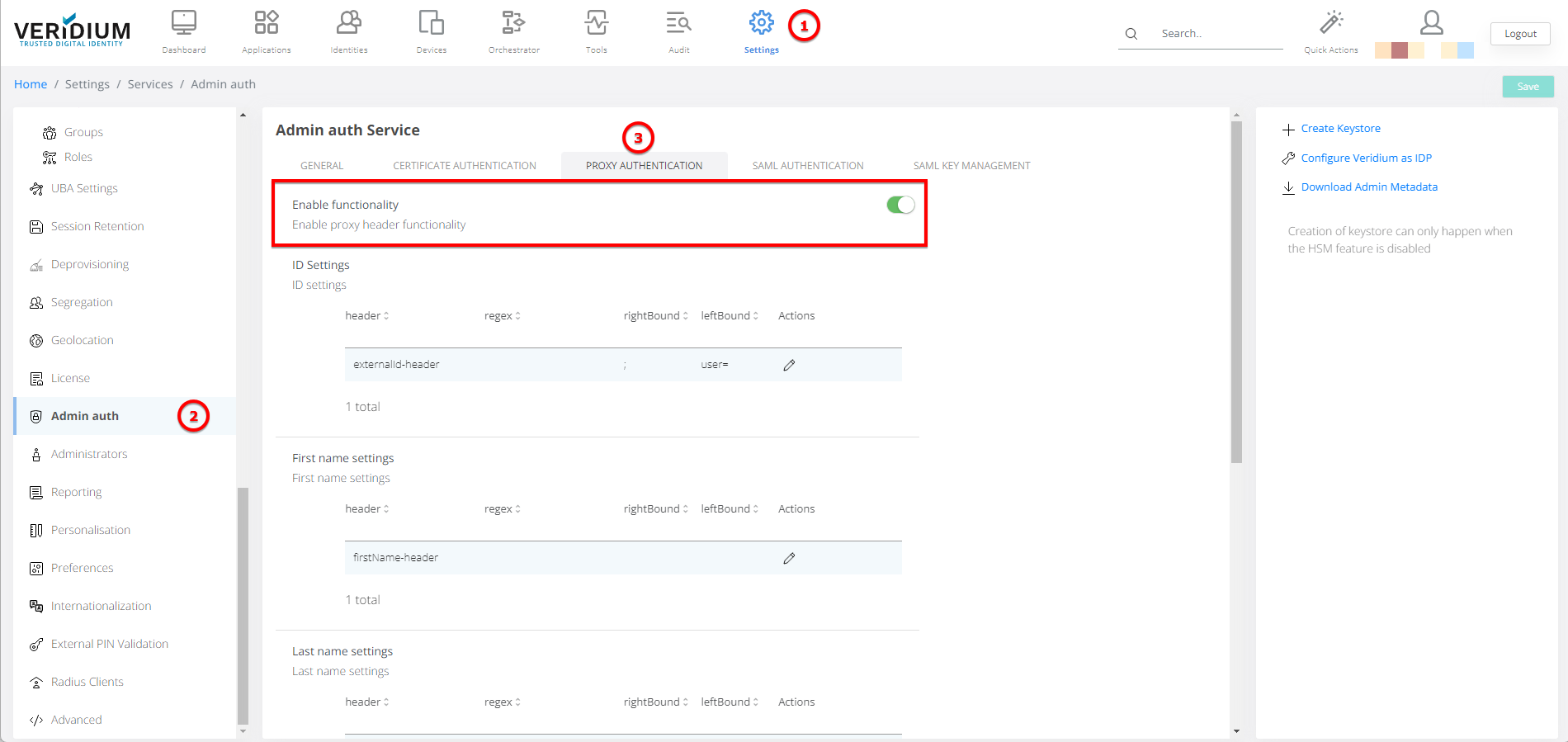
By default, this mechanism is disabled upon initialization, but can be enabled and configured by going to Veridium Manager / Settings / Admin Auth and by checking the following configuration:
Enable functionality flag must be set to enabled
The desired authentication setting should match the one set in SSO service
When accessing the Veridium Manager application, the system will lazy check the user identified via headers, automatically create an administrator entry if none exist, compute and apply the permissions based on the configure group mapping.
Note that for this scenario, the single point of administration for users becomes the user repository and not VeridiumID. That means in order to restrict access or change assigned permissions for a specific administrator, that specific entry should be directly managed in the user repository (i.e. changing the user groups or removing the user in Active Directory will have an immediate effect in identifying the user/computing permissions in Veridium Manager).
