Active Directory Password Self-Service
This feature allows Veridium users to reset or renew their Active Directory account passwords from within the Self Service Provider flows, in order to help in easing the helpdesk workload and to provide better convenience.
To benefit from this feature, the user must first login at least once with the LDAP password via Veridium to create the authenticator in the list of authenticators.
This check is done after each authentication and the user information is updated. After an authentication is validated, the presence of the LDAP password authenticator is checked against the database and created/updated as needed.
The feature can be enabled from the admin page. There will be two new flags that will enable different functional flows as described below.
Go to Settings → General → Ad Password Self Manage
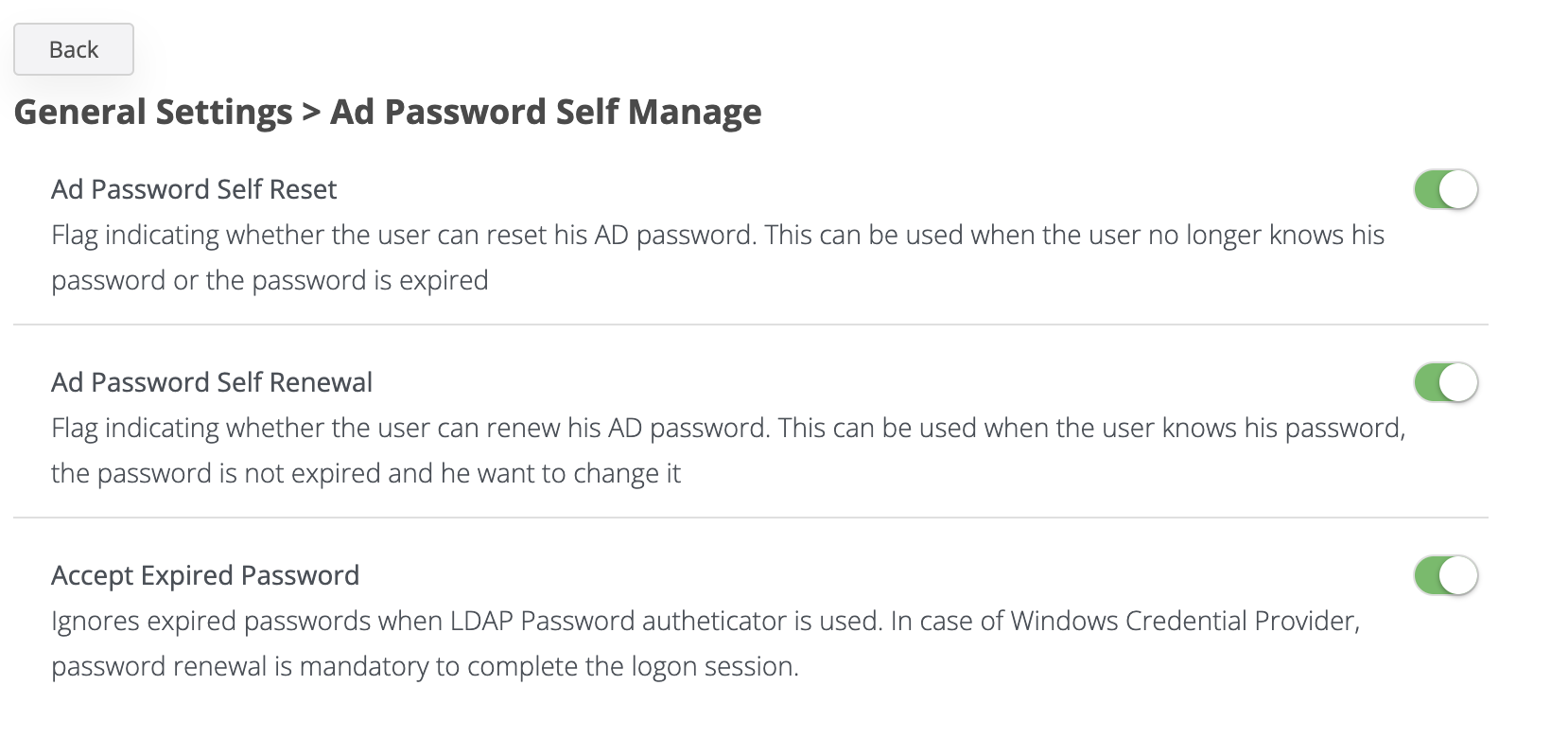
Active Directory password self-reset
This flag is used to activate the password reset function, that is, if the user no longer knows his password and wants to change it.
Active Directory password self-renewal
This flag is used for the password renewal function, that is, the user has an active password and knows it, but wants to change that password.
Accept Expired Password
This flag is used on the server to accept expired passwords or not. it is useful in case of CP because CP has its own password reset method
If those flags are set on true, the user will have the options to reset/renew the password from the SSP.
In the SSP page, under authenticators, we will see the new LDAP authenticator and the Reset/Renew action.
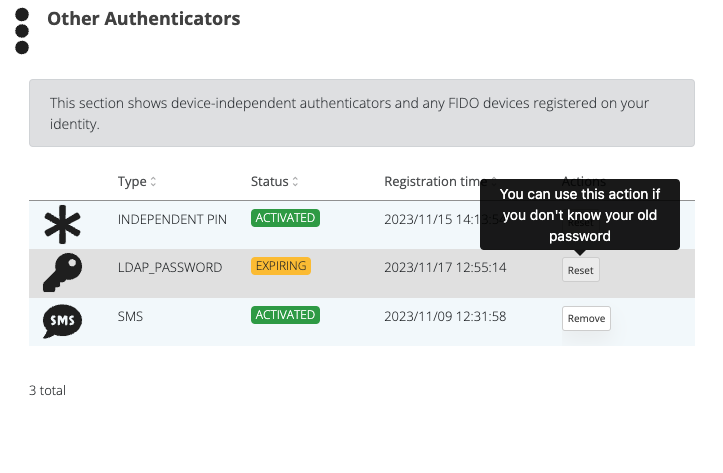
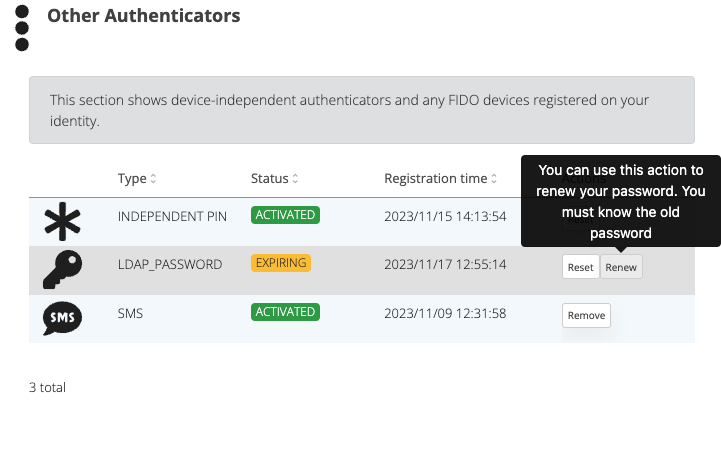
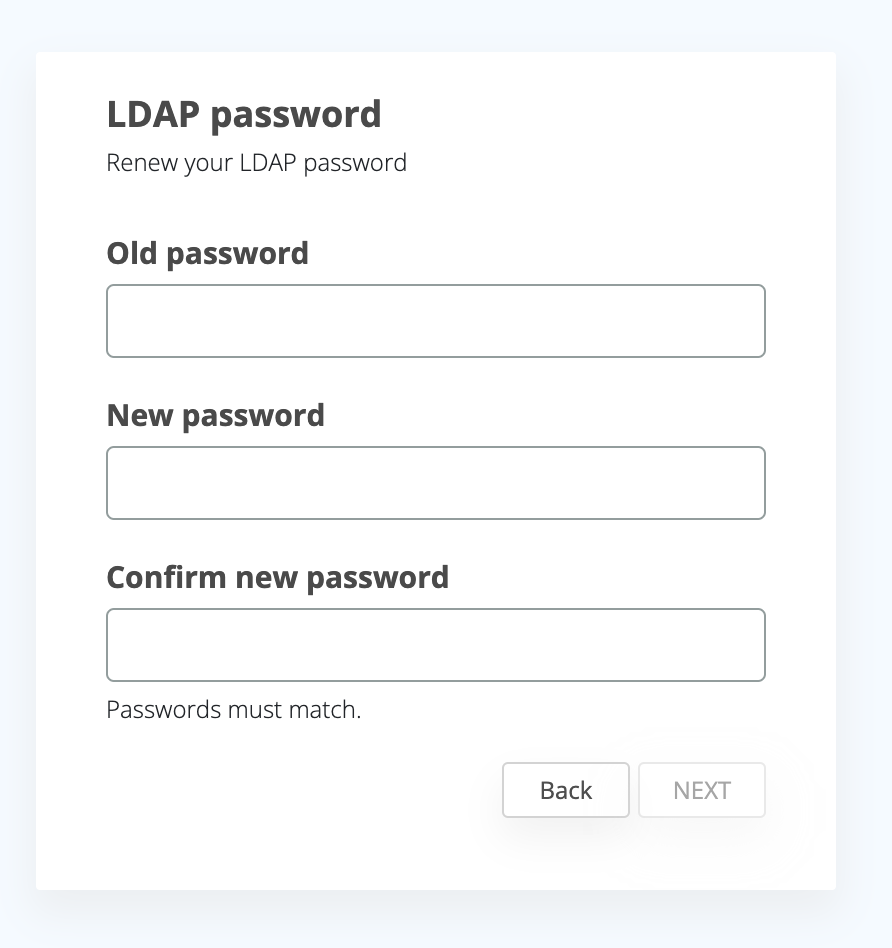
These actions follow the standard enrollment steps, similar to PIN reset action for example, meaning that the user will have to provide a code validation also, if so configured in the integration..
Security
As I said above, the flow of resetting the LDAP password will be the same as in the case of resetting the PIN. The user will have to follow security steps to be able to reset the LDAP password (this includes code validation)
Configuration
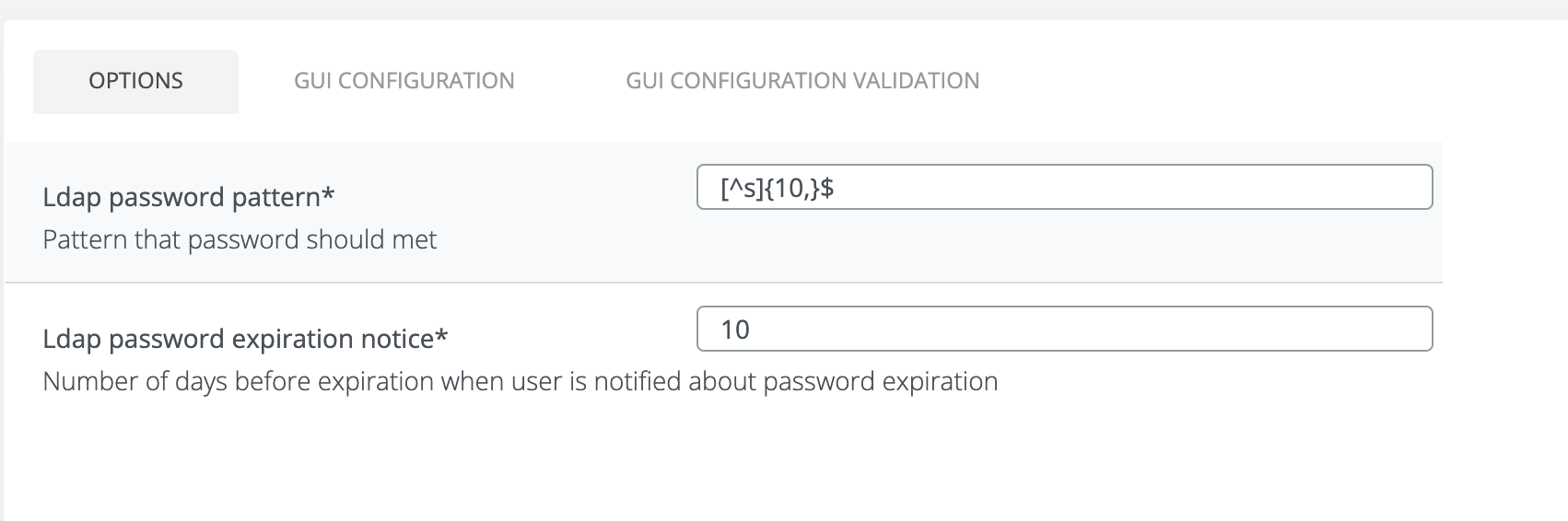
LDAP password pattern
LDAP password pattern is used to force the user to use a certain pattern. This format is regex type.
Please keep in mind that the password pattern configured in VID must be at least as restrictive as the AD password policy. The parameter does not sync automatically between AD and Veridium.
LDAP password expiration notice
This field indicates when to notify the user about the password that is about to expire.
Example: the following configuration is active: "LDAP password expiration notice" = 11.
If the difference between the expiration date given by LDAP and the day of authentication is less than 11 days, the user will be proposed to change his password inside the Veridium flow.
Renew the password when it is about to expire or expired
If the self-renewal/self-reset setting is activated, after authentication, the system will check the difference between the expiration date provided by LDAP and the authentication date. If the difference between them in days is smaller than the days configured from when the user will be notified, the system will propose the user to change his LDAP password.
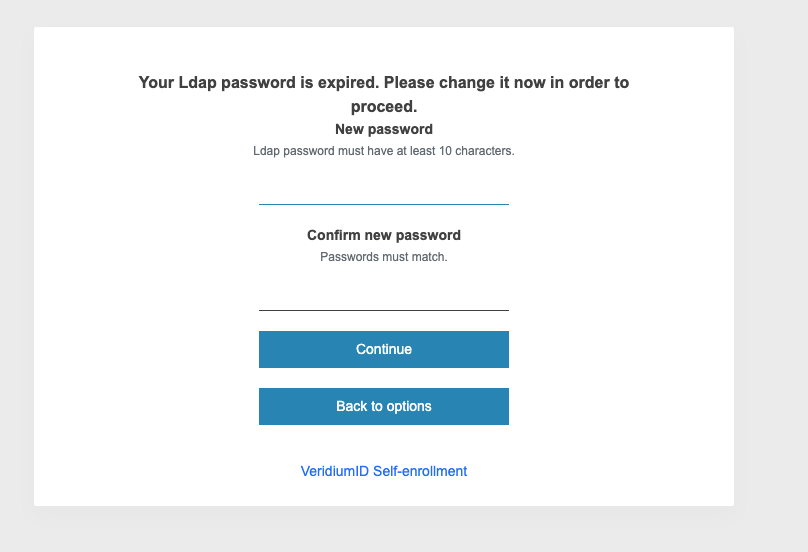
If the password has expired, the system will offer you to reset your password without the possibility to proceed further
If the password is about to expire, the system will offer you to change your password, with the possibility of continuing without changing it.
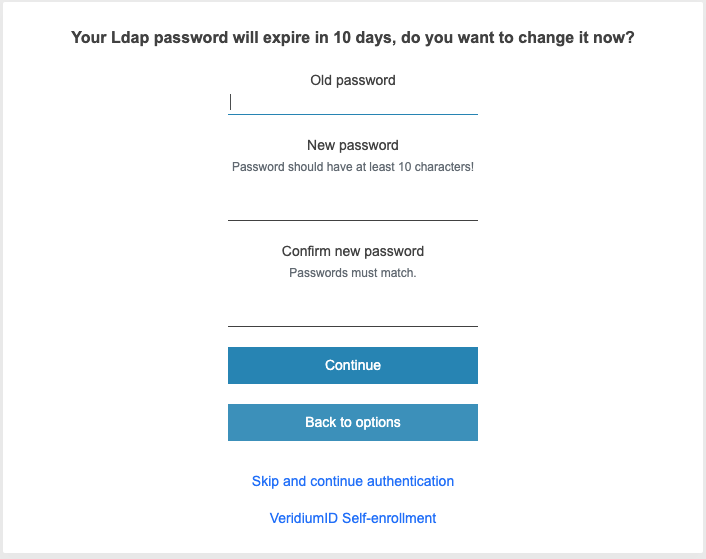
In order for the system to suggest changing the password, authentication must be done with LDAP_PASSWORD
Technical aspects and key takeaways
The LDAP authenticator will be created/updated during identity synchronization after authentication
The LDAP authenticator will be created only if the feature is active (reset password/renew password flag is activated)
Password reset can only be done if the feature is enabled from admin (see above) and will be done in shibboleth only if the password is already expired.
Password renew can only be done if the feature is enabled from admin (Renew password flag) and will be done in shibboleth only if the password is about to expired. In this case, old password will be requested.
To change the password, the LDAP connection must be secured.
In order to renew AD user password, the user must know the old password and it must be active.
If needed, the timeout on the http client configuration can be increased.
Some Active Directory attributes that can affect password policy if configured in Active Directory, such as “pwdINHistory” and “pwdLockout” do not return explicit error messages for the user in this release. This means that for cases in which the new user password does not meet these criteria, the flow will fail with no relevant error in GUI.
