On-Prem deployment using veridium-installer 3.5.4 - Rhel7 (9.5.13)
This article will describe the deployment procedure using the veridium-installer script.
1) Prerequisites
1.1) Node requirements
All nodes used in the deployment procedure will need to have SSH connectivity between them ensured by SSH keys on a single user, for example:
all nodes will have a user name centos that has ssh connectivity to all nodes
CODE## generate key (can be generated on all servers) ssh-keygen ## take the key (id_rsa.pub) from on server, from where the installation will take place, and put it on all other servers (including himself) in .ssh/authorized_keysThe default user will require admin (sudo) privileges (at least until the end of the deployment).
1.2) Dependencies
To have VeridiumID deployed in a client’s infrastructure the following dependencies must be installed (on all nodes):
sudo yum -y install apr-devel openssl-devel libstdc++-devel curl unzip wget zlib zlib-devel nc openssh-clients perl rsync zipIn order to run the Veridium installer deployment scripts the following packages must also be installed:
sudo yum -y install createrepo yum-utils vsftpd dialog net-tools1.3) Installing docker and docker-compose (on the node from where the installation will be done)
For more information on installing these two dependencies please check the following links:
For RHEL & CentOS:
#RHEL
sudo yum-config-manager \
--add-repo \
https://download.docker.com/linux/rhel/docker-ce.repo
#CENTOS
sudo yum-config-manager \
--add-repo \
https://download.docker.com/linux/centos/docker-ce.repo
#COMMON
sudo yum -y install docker-ce docker-ce-cli containerd.io
sudo systemctl enable --now docker.service
sudo curl -L "https://github.com/docker/compose/releases/download/1.29.2/docker-compose-$(uname -s)-$(uname -m)" -o /usr/local/bin/docker-compose
sudo chmod +x /usr/local/bin/docker-compose
sudo ln -s /usr/local/bin/docker-compose /usr/bin/docker-compose
docker-compose --version
1.4) Set selinux to permissive
Please run bellow command. It is not necessary to restart the server:
sudo setenforce 02) Deployment steps
This section will describe the deployment steps.
## download veridium-installer and put it on server, with centos user.
wget --user <user> --password <password> https://nexus.veridium-dev.com/repository/VeridiumInstaller/veridium-installer-9.5.13.zip
unzip veridium-installer-9.5.13.zip2.1) Running the pre-requisites script
After uploading the Veridium archive to one of the nodes and unarchiving it, using the default user (for example: “centos“) run the following command:
./pre-reqs.shThis script is in charge of the following:
Copy and install the VeridiumID layout and Python 3 packages on all nodes
Move all deployment files to veridiumid’s home directory
Configure veridiumid’s SSH connectivity using the SSH key used by the default user
Setting admin privileges (sudo) for the veridiumid user in order to ease the installation of VeridiumID
Adding veridiumid user to Docker’s list of allowed users
After running the script (as shown above) the user will be prompted for the following:
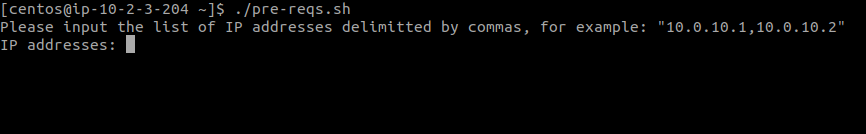
The user will need to add the list of IP addresses of all nodes including the current one, from which the installation will take place, for example:
Let’s say we have three nodes on which we wish to install VeridiumID with the following IPs: 10.0.10.1, 10.0.10.2 and 10.0.10.3
The node where the SE-Tools archive has been added to has the IP: 10.0.10.4
The user will need to add the following input to the script: 10.0.10.1,10.0.10.2,10.0.10.3,10.0.10.4
Afterwards, press the ENTER key
After providing the list of IP addresses the script will start copying the Layout and Python3 RPMs to all nodes and also install them, copying the deployment files to the current machine’s veridiumid home directory and add veridiumid to the list of users allowed to use the Docker service.
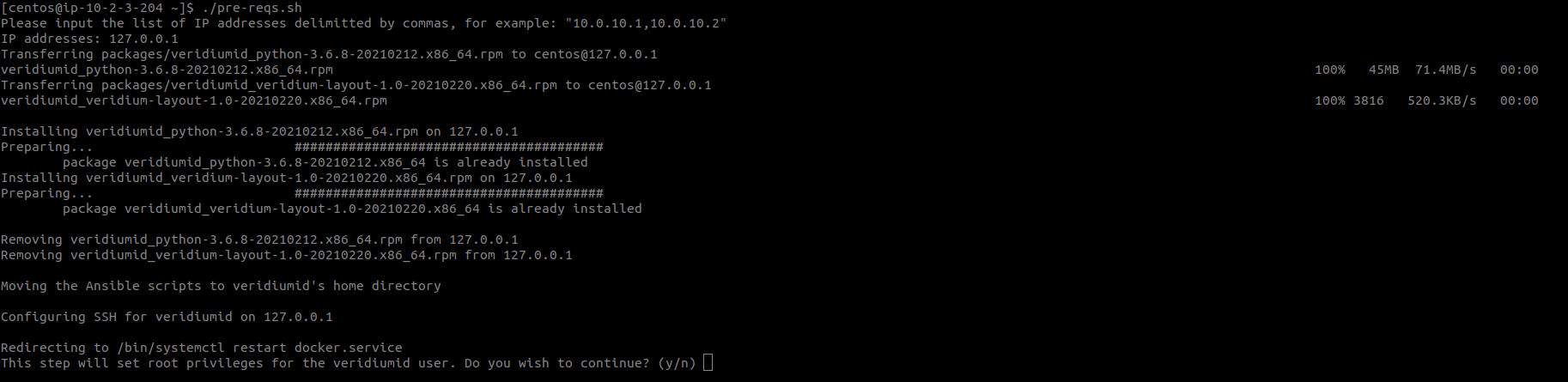
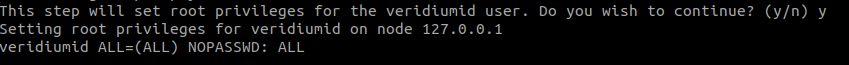
After finishing the above steps the script will ask the user if he wishes to allow the script to add root privileges to the veridiumid user. If giving “y“ as the response the following privileges will be added:
Providing “n“ as the input to the above prompt will print the following message to the standard output:
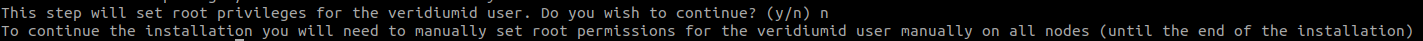
Root privileges for the veridiumid user are required in order to ease the installation phase and can be removed after finishing the deployment.
2.2) Running check_prereqs.sh
this script checks pre installation checks, meaning:
port connectivity with wget and nc
checks if prerequisites are installed
checks if ntp is in sync
checks RAM and disk
This script contains the following commands and provides instructions about how it can be used such as - r remote nodes, -r -w -p :
Usage: ./check_prereqs.sh <args>
Args: -l -> Run on local node
-r -> Run on remote nodes
-w IPS_LIST -> webapp node ip list delimitted by commas, for example: '10.0.0.1,10.0.0.2'
-p IPS_LIST -> persistence node ip list delimitted by commas, for example: '10.0.0.1,10.0.0.2'
Examples:
## local server
./check_prereqs.sh -l
## one server, checks remote
./check_prereqs.sh -r -w 10.109.20.133 -p 10.109.20.133
## 2 webapps and 3 persistance
./check_prereqs.sh -r -w 10.109.20.133,10.109.21.164 -p 10.109.50.171,10.109.51.185,10.109.52.72
2.3) Starting the installation
2.3) Starting the installation
Before proceeding with this step, on the installation node, copy the domain certificate to veridiumid’s home directory.
After finishing the above steps connect as the veridiumid user and go to its home directory (/home/veridiumid).
sudo su - veridiumidFrom here, start the installation by running the following script:
./veridium-installer.shThis will start the Python Installation Wizard and the user will have to select between Simple and Advanced mode:
Simple mode will be used for POC deployments since it will automatically set the Ansible hosts to 127.0.0.1 and HaProxy to ports configuration.
Advanced mode will allow the user to configure every parameter configured by the VeridiumID installer.
For more information regarding the two deployment modes click on the following links:
2.3) Deployment
After exiting the Python Installation Wizard the deployment will start.
During this step please don’t close the terminal from which the script has been executed.
In case of any error during the deployment, a message will be shown in the terminal that points to the step’s log file.
All log files can be found in the following path: /home/veridiumid/logs
In case of needing to start the deployment from the beginning please run the following commands from the installation node:
# To remove local files:
bash /home/veridiumid/cleanup_install_files.sh -l
# To remove the previously generated CA (in case the install-ca step has been completed) and the local files
bash /home/veridiumid/cleanup_install_files.sh -l -c3) Post-deployment steps
After the installation has succeeded to cleanup docker and local repository files (including vsftpd) please run the following on all nodes:
docker system prune -a
yum -y remove docker-ce docker-ce-cli containerd.io
rm -f /usr/local/bin/docker-compose
rm -rf /usr/bin/docker-compose
ip link delete docker04) Set a signed certificate for the installation
Replace the self signed certificate with a proper one, delivered by client. If the client has a p12, the following script can be executed to extract the certificates. It will be generated a in conversion_result, the private key and the public certificate. Please copy, as per instructions, the file in haproxy and restart the service. Also in websecadmin, remove the selfsigned certificate and import the correct one.
/etc/veridiumid/scripts/convert_haproxy_cert.sh certificate.p12
#To change the Haproxy domain certificate please use the following command as root user:
# cp conversion_result/server.pem /etc/veridiumid/haproxy/server.pem; chown ver_haproxy:veridiumid /etc/veridiumid/haproxy/server.pem
# To restart the server after changing the certificate use the following command as root:
# service ver_haproxy restart