Deployment using OVA file - Centos 7
As part of deployment resources, Veridium provides an out of the box OVA image which can be obtained from Veridium Sales Engineering team or Professional services.
This OVA image can be used for PoC's or Production.
The operating system is Centos7.
Note: VHD or VHDX format are also available. Please contact Veridium for getting this format.
After the OVA is imported, start the setup and installation of VeridiumID product. Make sure you have a FQDN for your VeridiumID server in DNS (bonus if you also have the PTR)
1. Connect ssh/scp and transfer HTTPS security certificate.
The certificate should be signed by a publicly trusted authority in p12 format with full chain included. Installation can be done also using a self signed certificate however that will make enrolling user devices difficult, vanilla iOS and Android devices need to trust the certificate in order to enroll.
1.1. Connect to the virtual console, authenticate, change default password, hostname and IP Address.
The default credentials are :
Login : veridiumid
Password: ChangeMe!123
Note : the default keymap is US
Use the ‘passwd’ command to change the password:

Note: In production it’s strongly recommended you vault this password, ideally installing a PAM agent and other host security controls at this point.
Use ‘ifconfig’ to display network configuration information:

Note: You may want to change to a static IP address, at a minimum make sure DHCP updates DNS for the hostname.
Change the ‘hostnamectl’ command to match the FQDN you have in DNS for your VeridiumID Server:
sudo hostnamectl set-hostname my.new-hostname.server
Edit the file sudo vi /etc/sysconfig/network-scripts/ifcfg-<ifname> (in the example above the <ifname> is ens32)
In order to check the interfaces, run ifconfig or ip a.
The things that needs to be modified:
BOOTPROTO=”static”
Below that line add the lines:
NETMASK=”<Subnet Mask in Bits>”
IPADDR=”<Desired Static Address>”
GATEWAY=”<IP of Default Gateway>”
DNS1=”<IP of Primary DNS Server>”
DNS2=”<IP of Backup DNS Server>”
example (please set properly your specific values):
TYPE="Ethernet"
PROXY_METHOD="none"
BROWSER_ONLY="no"
BOOTPROTO="static"
DEFROUTE="yes"
IPV4_FAILURE_FATAL="no"
IPV6INIT="no"
NAME="ens32"
DEVICE="ens32"
ONBOOT="yes"
IPADDR=192.168.0.180
GATEWAY=192.168.0.1
NETMASK=255.255.255.0
DNS1=10.120.120.1
DNS2=10.120.120.2Please restart interface:
sudo ifconfig en32 down
sudo systemctl restart network
sudo ifconfig en32 upReboot the VM (I like using the command line ‘reboot’, but you may also reboot using VMware as tools are installed)
Set the proper ntp server:
## edit /etc/ntp.conf and set ntp server IP
## examples:
## server 0.centos.pool.ntp.org iburst
## server IP iburst
sudo systemctl stop ntpd ; sudo ntpd -gq; sudo systemctl start ntpd
## also set timedate zone
sudo timedatectl list-timezones | grep Bucharest
sudo timedatectl set-timezone Europe/Berlin
## start the services
sudo systemctl enable ntpd ; sudo systemctl start ntpd1.2 Upload the certificate using WinSCP or use a self signed certificate. - it is recommended to do the installation with the same FQDN name as the service will be published.
If you cannot obtain a certificate signed by a public authority, a self signed certificate may be generated, by running the following command:
##Args:
## -d DOMAIN -> mandatory argument, the domain name for the certificate (for example: poc.example.com
## -p PASSWORD -> mandatory argument, the password that will be used for the generated certificate
/home/veridiumid/create_domain_cert.sh -d DOMAIN -p PASSWORD
## the certificate created, used for instalation is /home/veridiumid/certs/domain.p12If there is already a PCKS12 certificate file signed by a public authority, please copy it to /home/veridiumid/. Make sure the file contains ALL certificates in the chain and in the proper order, if you have separate certificate, chain and keyfiles skip to step 2 of this section
Use scp to transfer the PKCS12 certificate file to your VeridiumID server and skip the rest of this section.
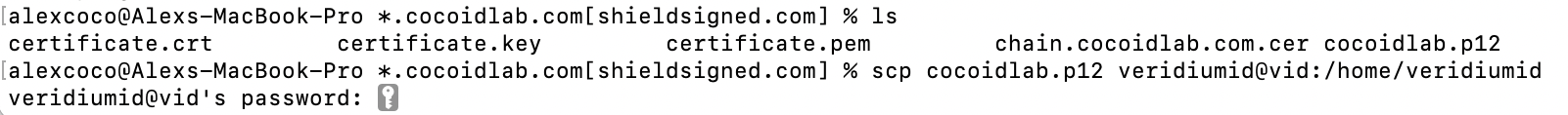
Note: Use whatever SCP client makes you comfortable, the example above is from the Darwin (MacOS) terminal
Use scp to transfer all the separate certificate files to /home/veridiumid on the server:

Note: In this example a wildcard certificate was created using the Shield Signed service with Let’s Encrypt as the Certificate Authority
Open an SSH terminal to the VeridiumID server and Generate a PKCS12 certificate file using the following ‘openssl’ command:
openssl pkcs12 -export -out <output filename>.p12 -inkey <private key filename> -in <certificate file containing full chain of authority>

Note: The private key should be handled appropriately as should the password you set protecting it within the p12. This could also have been done from the Darwin terminal or any system that has a recent release of openssl.
2) Starting the installation
Check the IP of the server, by running. Take the IPs configured already for the server (in case of single node, only one IP is used). This will be used during installation.
ip a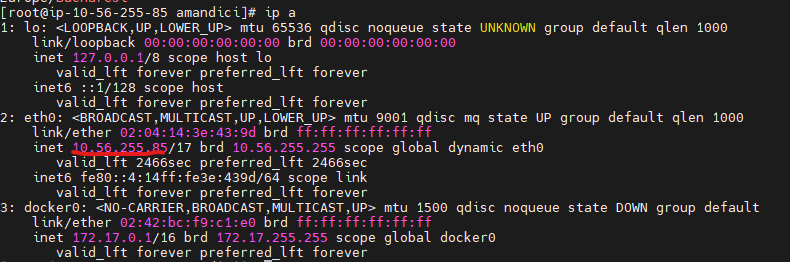
From here, start the installation by running the following script:
./veridium-installer.sh2.1) Provide deployment details using the Installation Wizard
When the installation wizard will start the following screen will be seen in the terminal:
Press Enter to proceed.
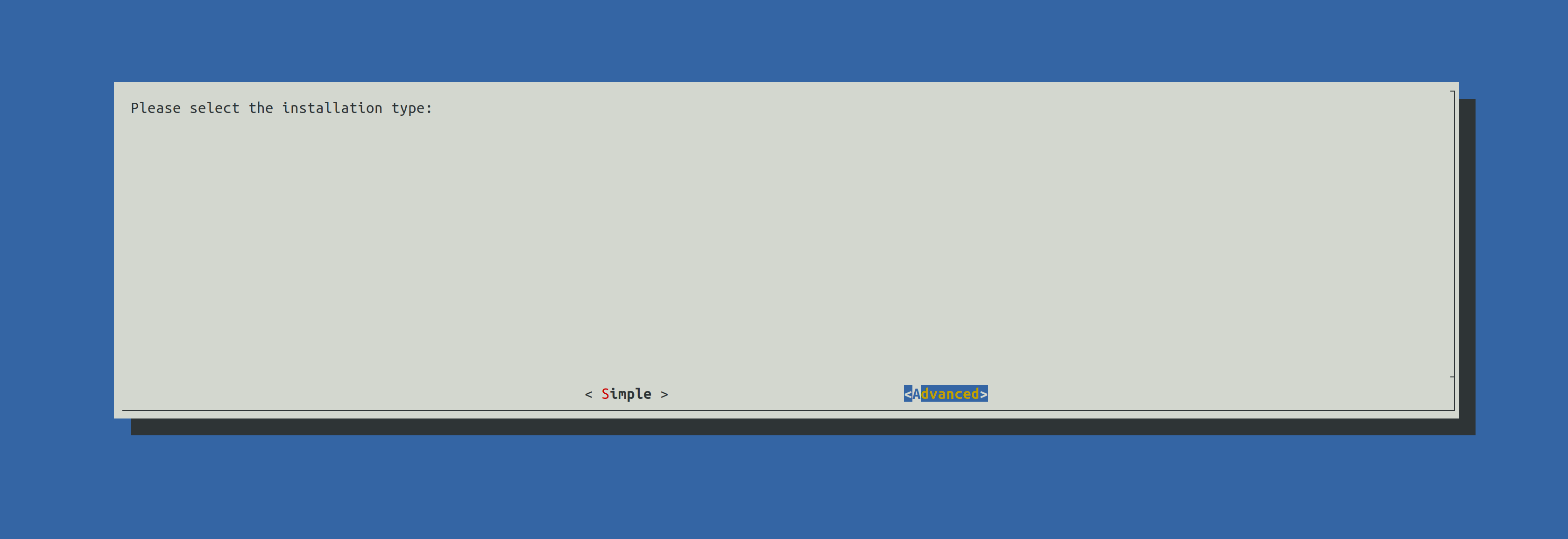
Select Advanced using the right arrow key and press Enter to continue.
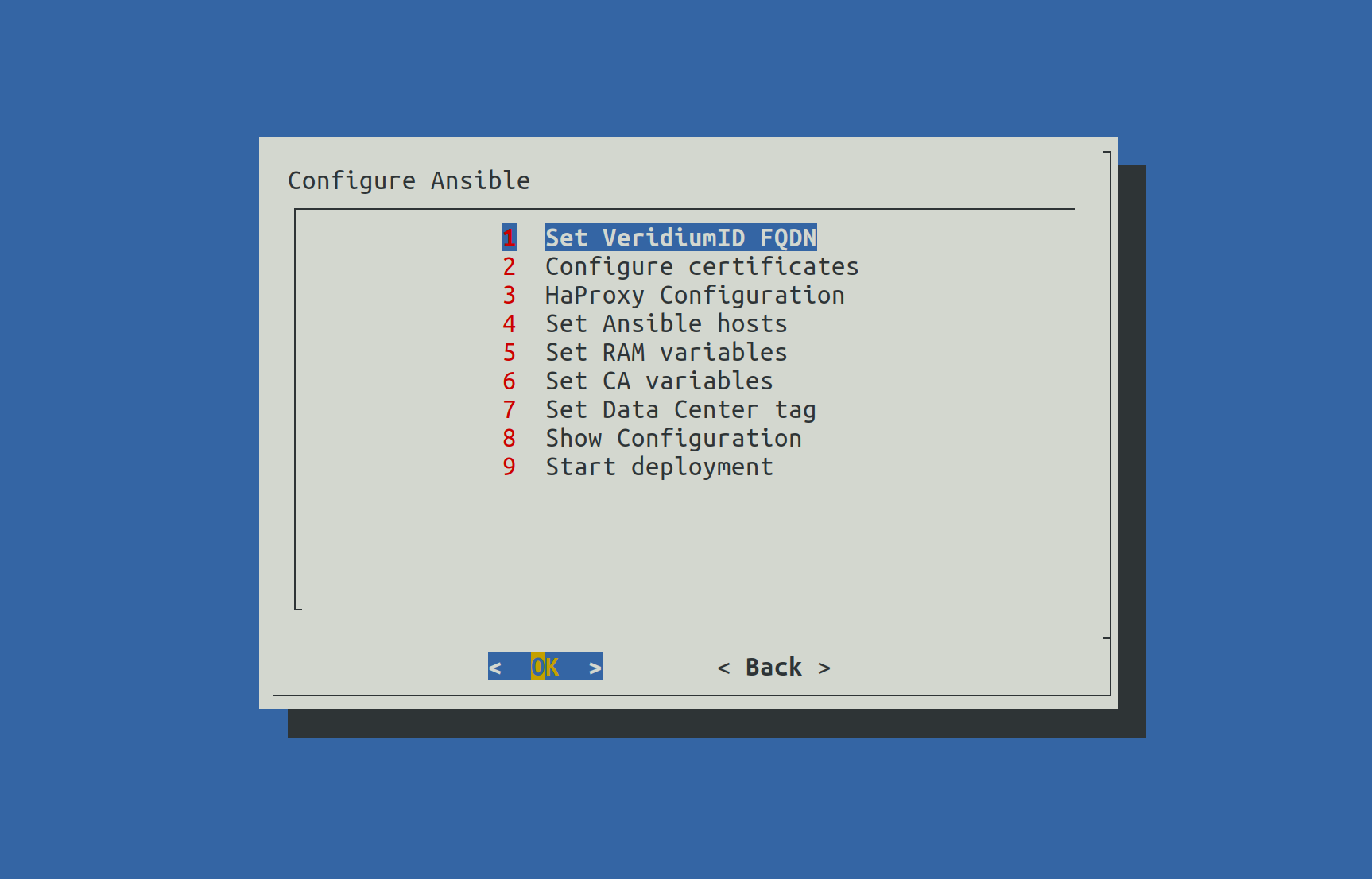
All steps from the Menu will be detailed in the following steps.
2.2) Set VeridiumID FQDN
When selecting Set VeridiumID FQDN the following screen will be shown:
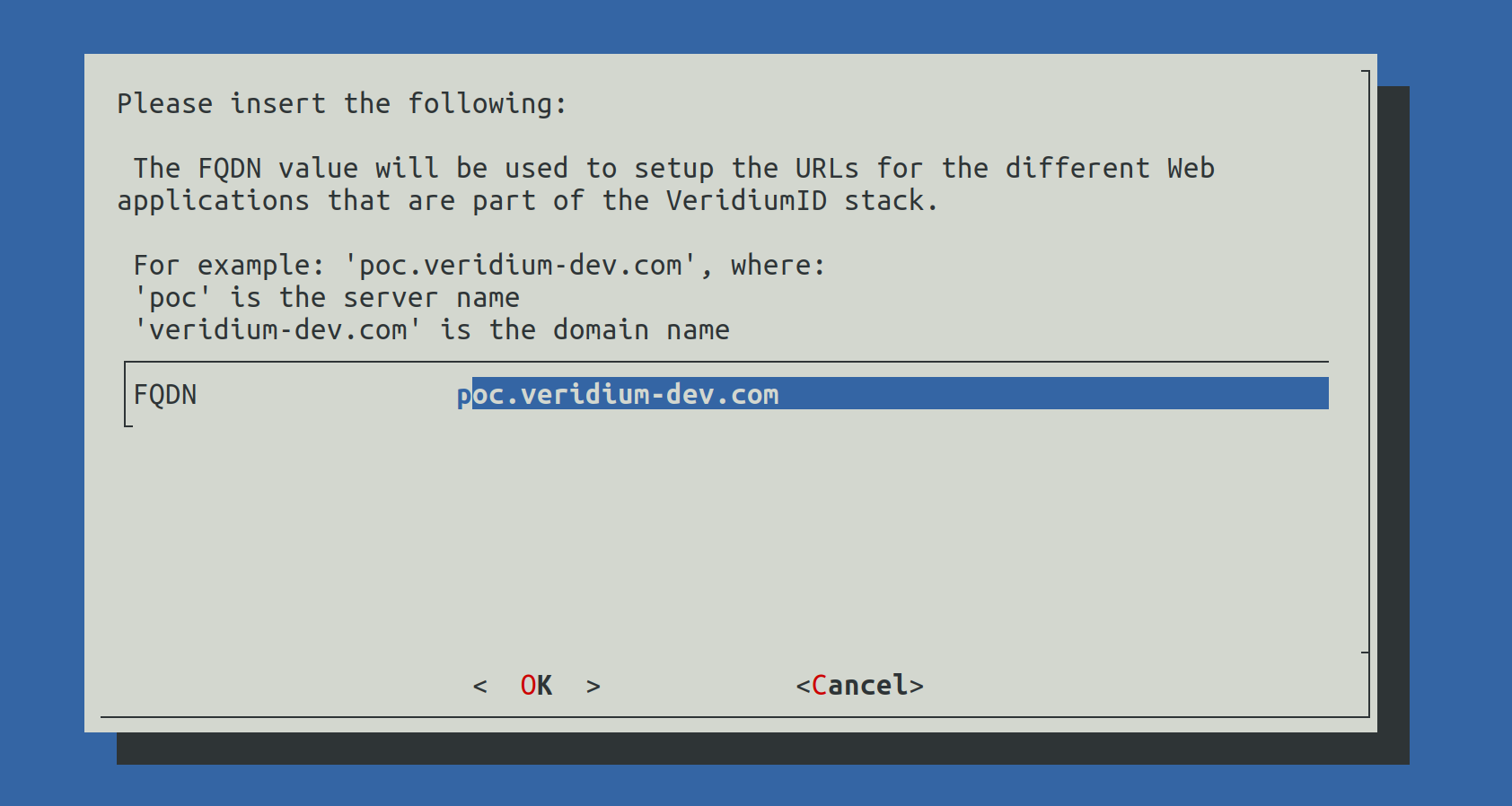
Write the correct FQDN in place of poc.veridium-dev.com and press the TAB key to go to OK and press Enter to continue.
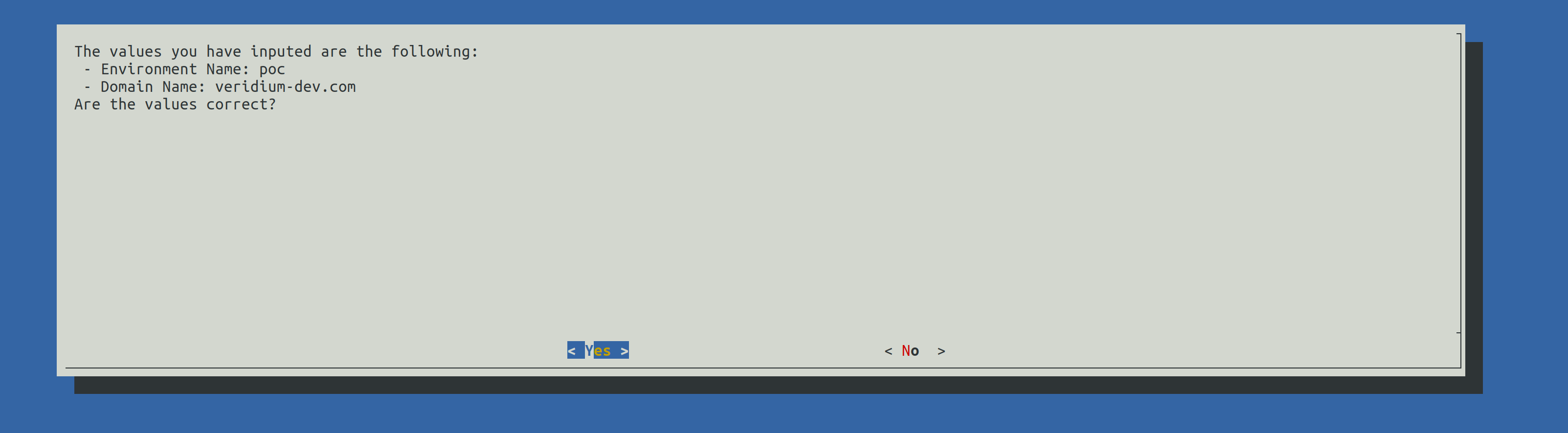
A validation of the FQDN will be prompted. Press Enter to continue.
2.3) Configure Certificates
When selection Configure Certificates the following screen will be shown:
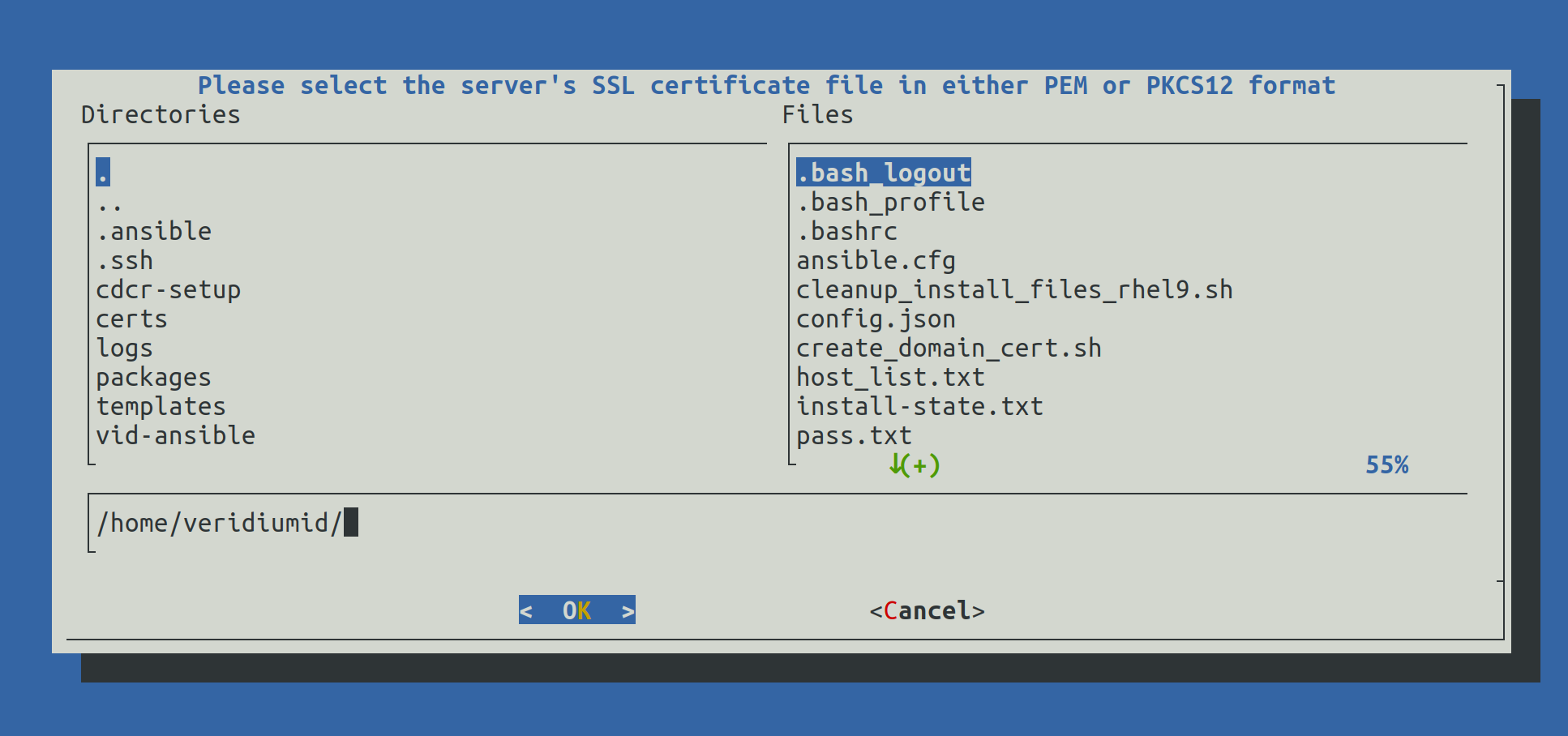
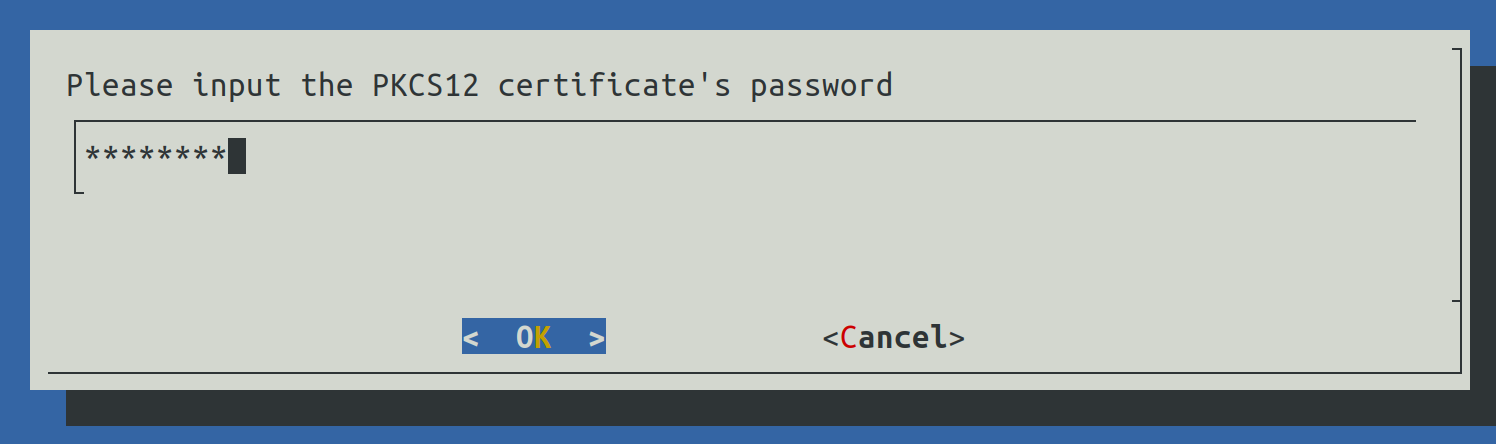
Write the full path of the certificate (for example: /home/veridiumid/certs/domain.p12) and press Enter to continue.
Another prompt for the password will be shown.
2.4) HaProxy configuration
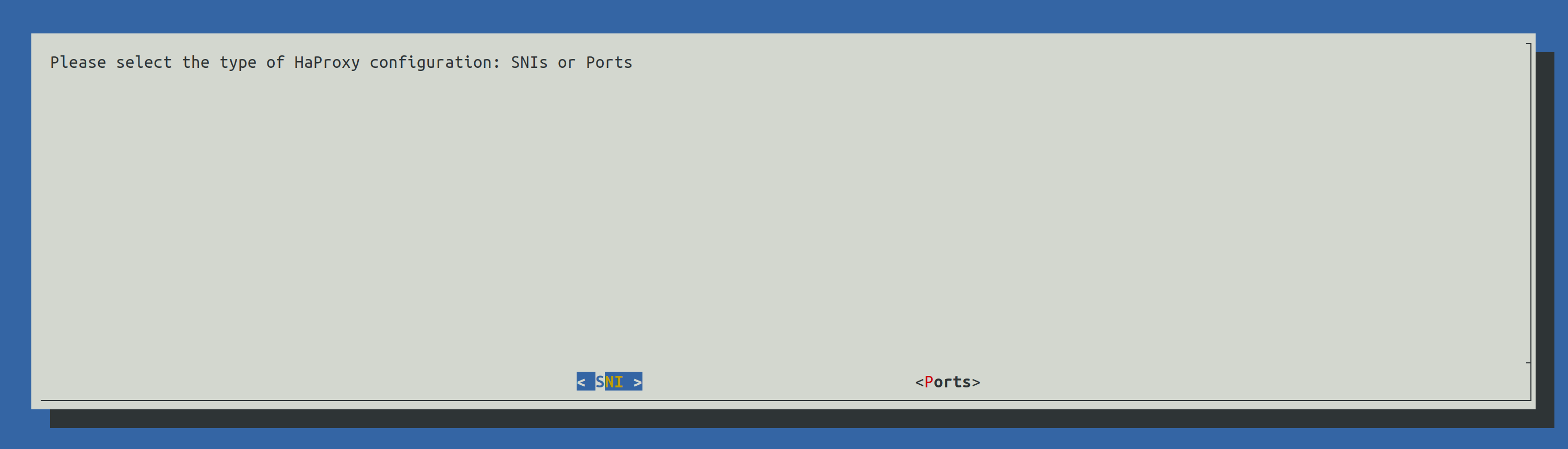
There are two configuration for HaProxy:
SNI: all component URLs will be composed from the base FQDN (the one provided during step 2.3.3.1) along side the components name, for example:
for the Admin Dashboad : admin-baseFQDN
for the Self Service Portal: ssp-baseFQDN
for the Websec API: baseFQDN
for Shibboleth (Identity Provider): shib-baseFQDN
Ports: all component URLs will be composed from the base FQDN and a different port for each component, for example:
for the Admin Dashboard: baseFQDN:9444
for the Self Service Portal: baseFQDN:9987
for the Websec API: baseFQDN:443
for Shibboleth (Identity Provider): baseFQDN:8944
2.5) Set Ansible Hosts
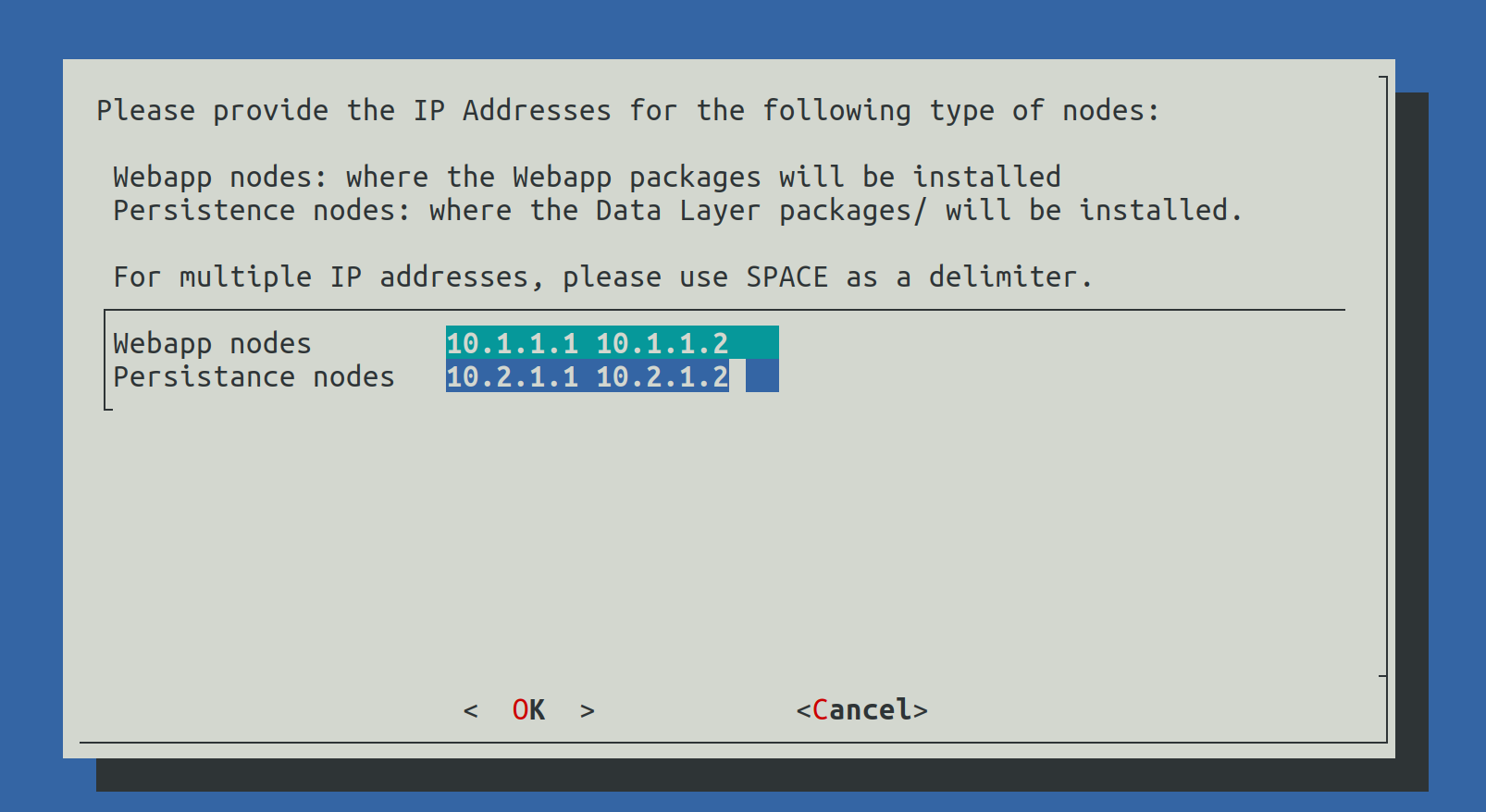
In this step the select from the list of IP addresses which will be Webapplication nodes and which will be Persistence node (Data nodes).
The list of nodes must be delimitted by Spaces.
2.6) Set RAM values
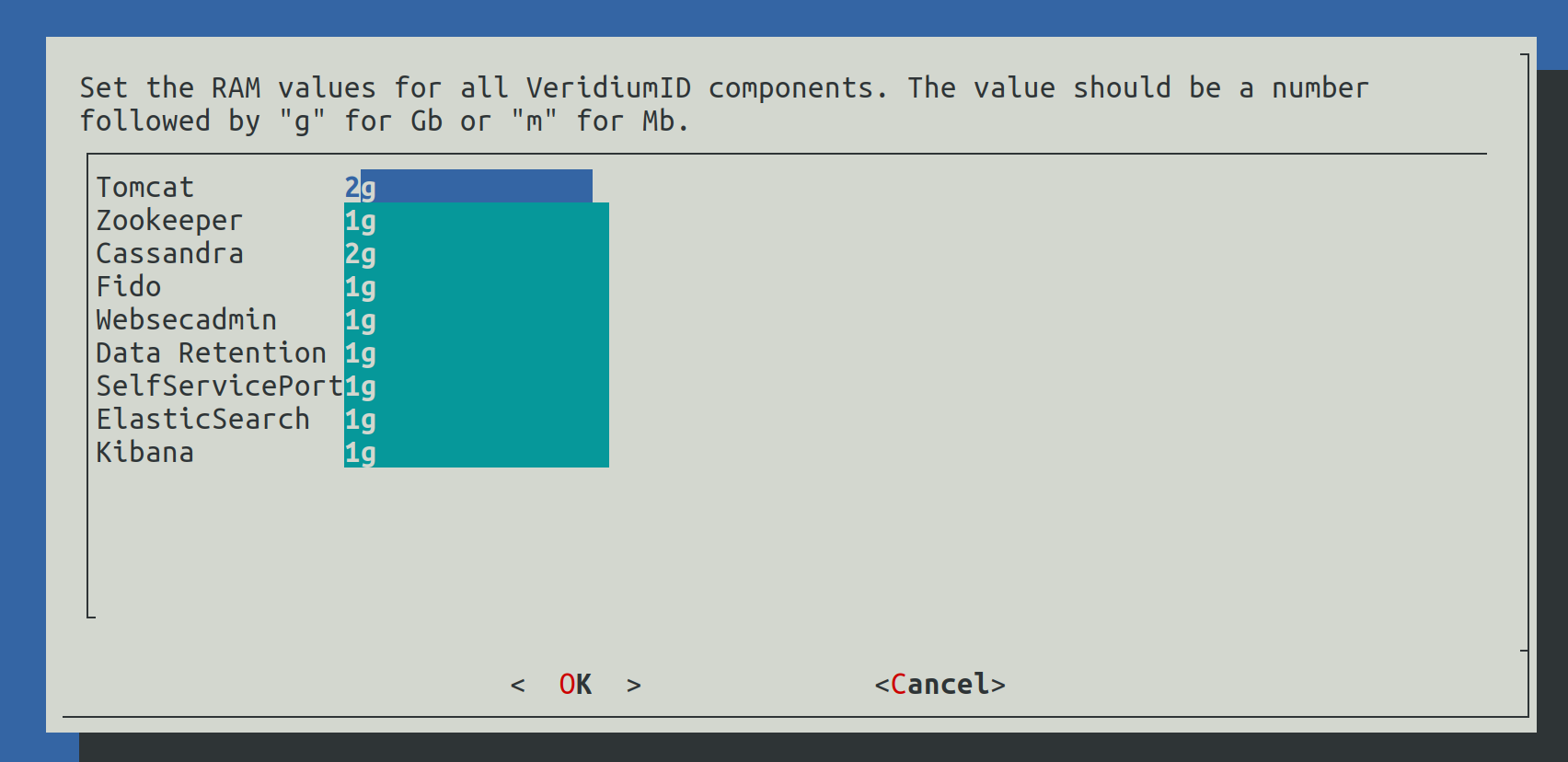
In this step the RAM values for different components will be configured. The value must contain a number followed by g for Gb or m for Mb.
2.7) Set CA variables
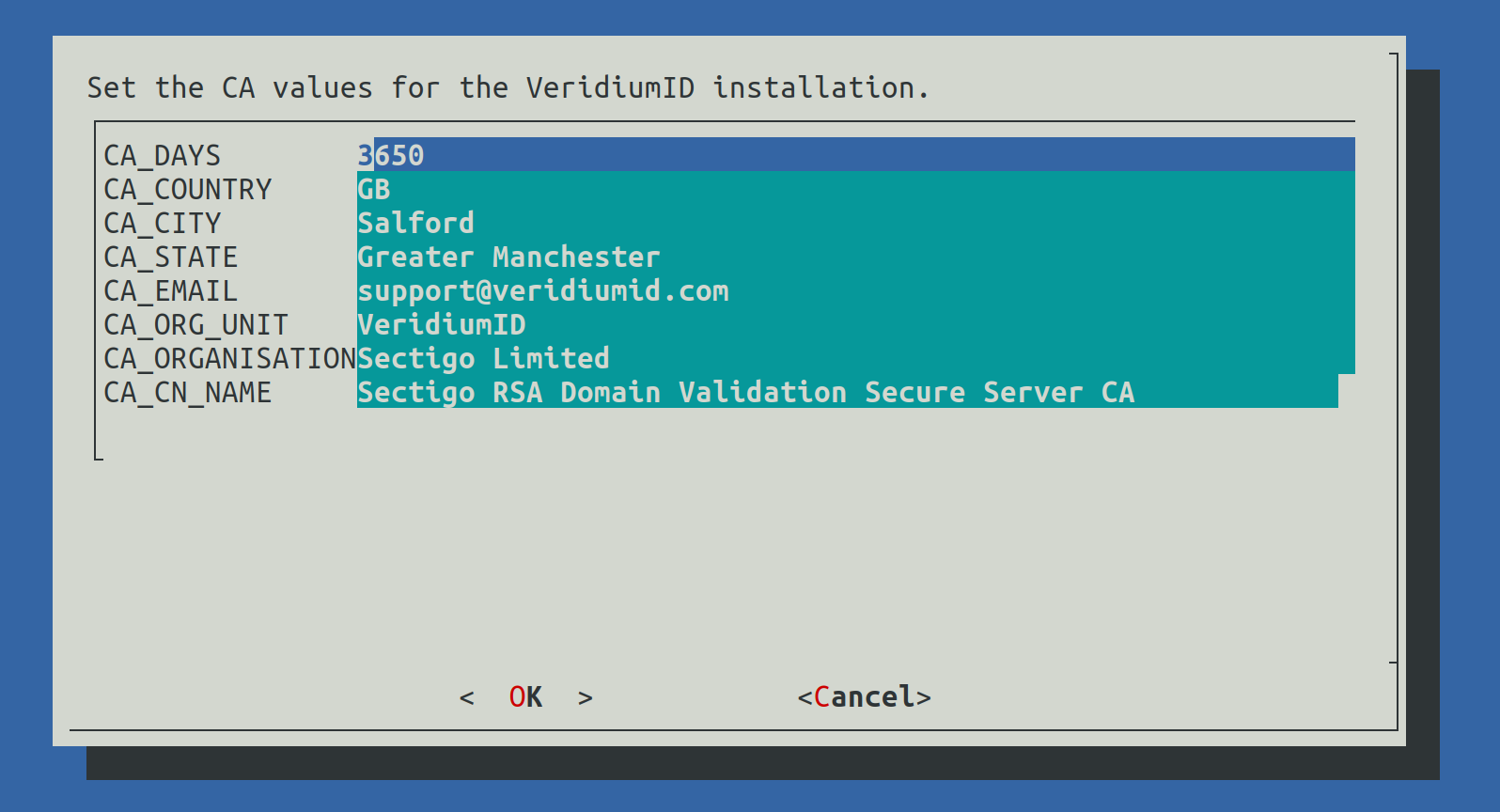
This step will configure the values used for the internal Certification Authority of the VeridiumID deployment (used to generate internal certificates).
2.8) Set Data Center Tag
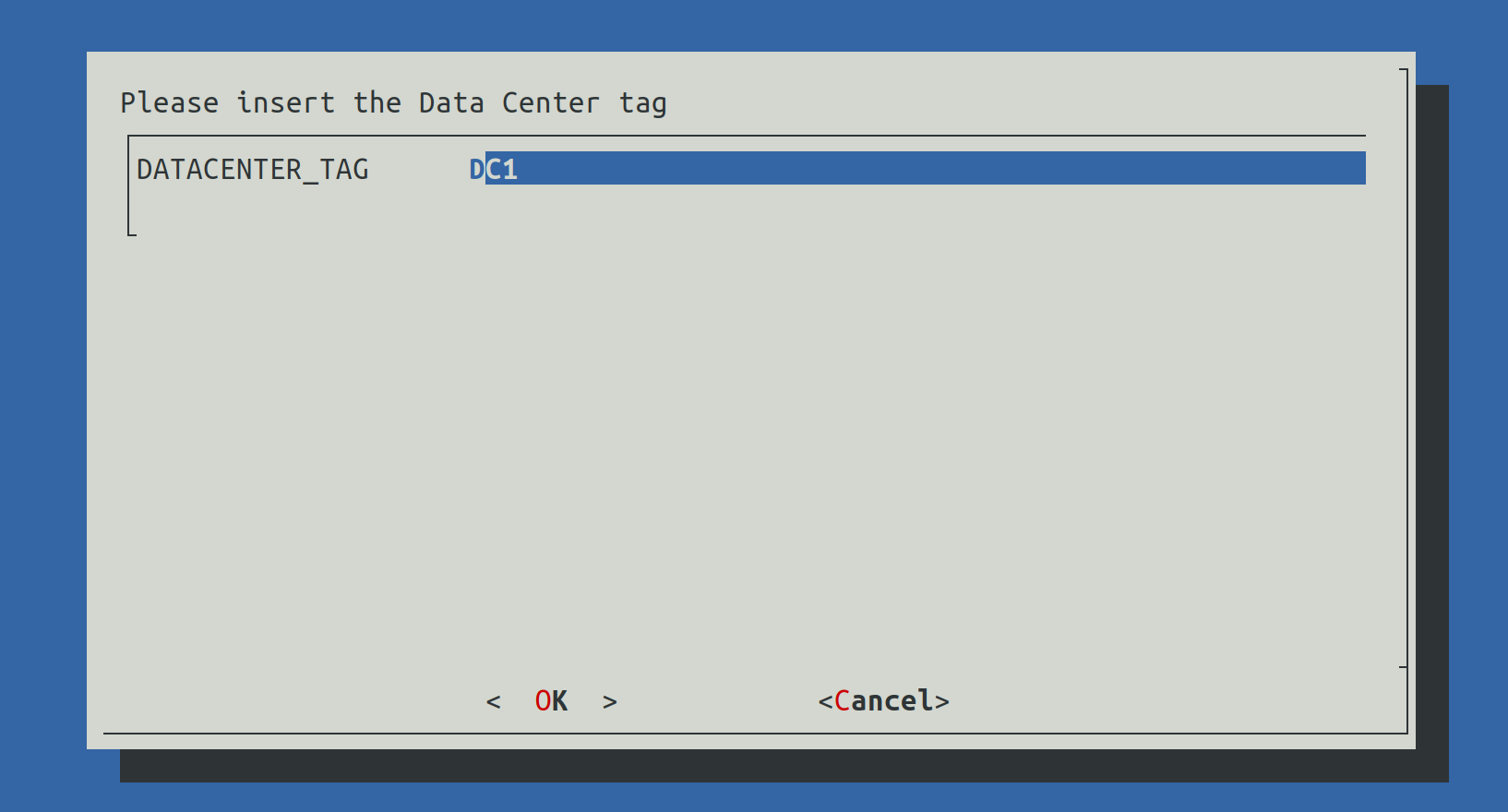
This value will be used to define the name of the current data center.
2.9) Show configuration
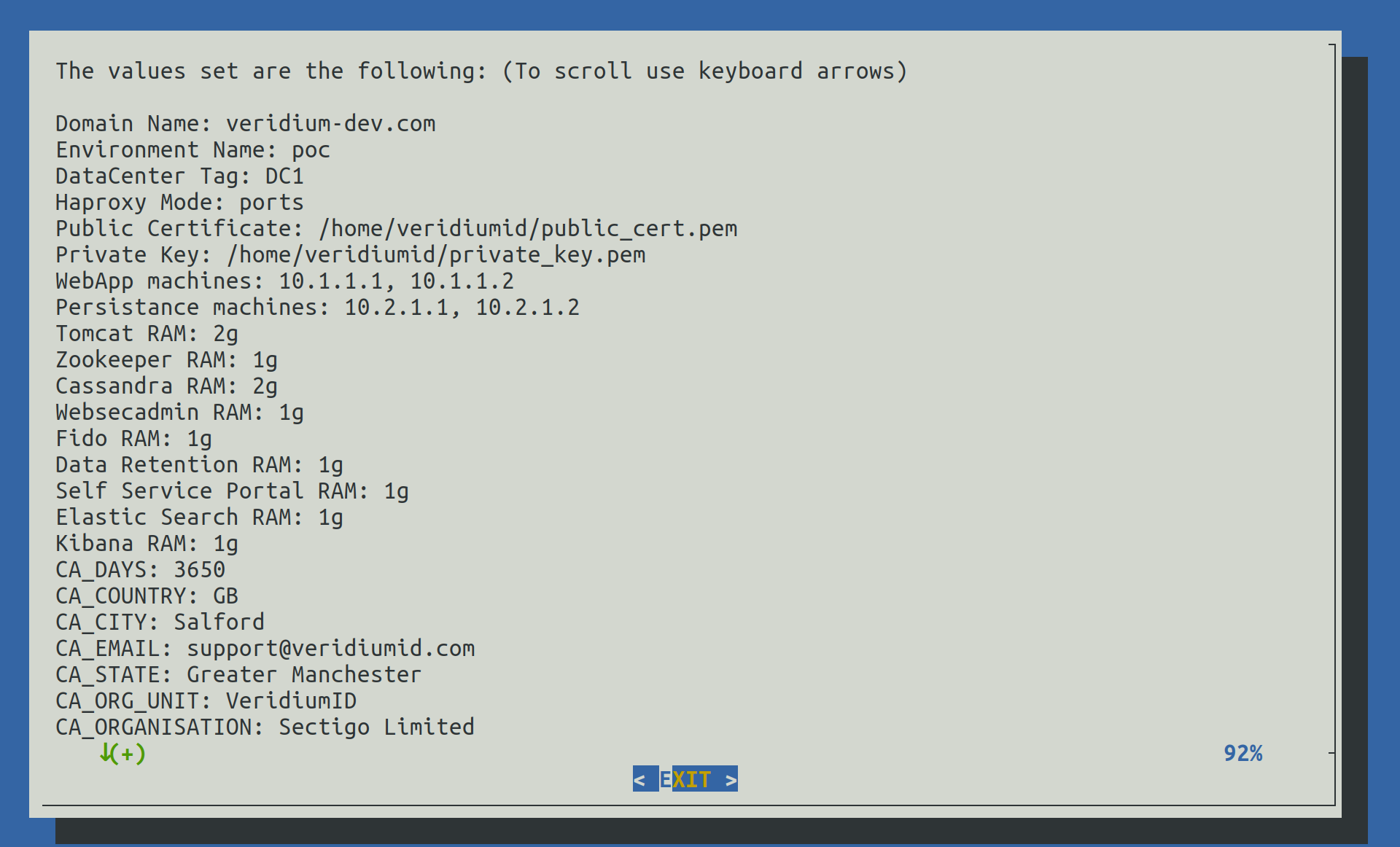
In this step we can verify all value provided earlier to validate them.
2.10) Start deployment
This step will close the Installation Wizard and provide the list of FQDNs:
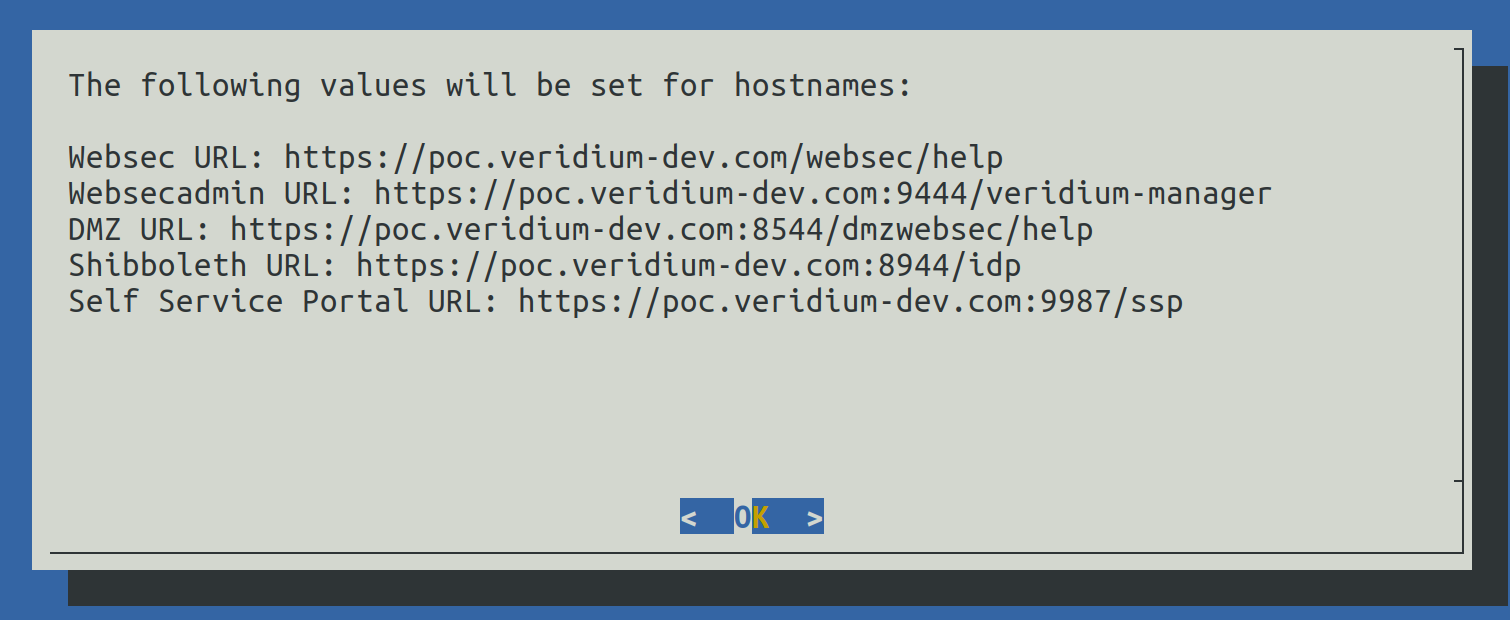
The values can be viewed later in the following file: /home/veridiumid/host_list.txt
After exiting the Installation Wizard, the deployment process will start by:
Checking the SSH connectivity from this node to all other nodes
Install specific VeridiumID components for Webapplication and Persistence nodes
Start the Ansible configuration
3) Deployment
After exiting the Python Installation Wizard the deployment will start.
During this step please don’t close the terminal from which the script has been executed.
In case of any error during the deployment, a message will be shown in the terminal that points to the step’s log file.
All log files can be found in the following path: /home/veridiumid/logs
In case of needing to start the deployment from the beginning please run the following commands from the installation node:
# To remove local files:
bash /home/veridiumid/cleanup_install_files.sh -l
# To remove the previously generated CA (in case the install-ca step has been completed) and the local files
bash /home/veridiumid/cleanup_install_files.sh -l -c4) Post-deployment steps
After the installation has succeeded to cleanup docker and local repository files (including vsftpd) please run the following on all nodes:
sudo docker system prune -a
sudo yum -y remove docker-ce docker-ce-cli containerd.io
sudo rm -f /usr/local/bin/docker-compose
sudo rm -rf /usr/bin/docker-compose
sudo ip link delete docker0
5) Set a signed certificate for the installation
Replace the self signed certificate with a proper one, delivered by client. If the client has a p12, the following script can be executed to extract the certificates. It will be generated a in conversion_result, the private key and the public certificate. Please copy, as per instructions, the file in haproxy and restart the service. Also in websecadmin, remove the selfsigned certificate and import the correct one.
/etc/veridiumid/scripts/convert_haproxy_cert.sh certificate.p12
#To change the Haproxy domain certificate please use the following command as root user:
# cp conversion_result/server.pem /etc/veridiumid/haproxy/server.pem; chown ver_haproxy:veridiumid /etc/veridiumid/haproxy/server.pem
# To restart the server after changing the certificate use the following command as root:
# service ver_haproxy restart