How to filter user groups with a scripted attribute
Often users have a lot of AD groups assigned, some of them not needed during authentications. VeridiumID reads these groups and makes them available in the SAML response, making the SAML payload bigger than necessary.
This document is a guide to configuring an environment to deliver filtered user groups in SAML responses by using Shibboleth’s scripted attributes.
Setup
Add this Javascript in Zookeeper configuration by accessing Admin Dashboard → Settings → Advanced → shibboleth/custom-attribute-resolver.xml, as child node for AttributeResolver.
<AttributeDefinition id="memberOfFiltered" xsi:type="ScriptedAttribute">
<Dependency ref="memberOf"/>
<Script><![CDATA[
groupMatchingRegex = /CN=Veridiumid_/gi
memberOfFiltered.getValues().retainAll([]);
for (i = 0; i < memberOf.getValues().length; i++) {
currentGroup = memberOf.getValues().get(i);
if (currentGroup.match(groupMatchingRegex)) {
memberOfFiltered.addValue(currentGroup);
}
}
]]></Script>
<AttributeEncoder encodeType="false" name="urn:mace:dir:attribute-def:memberOfFiltered" xsi:type="SAML1String"/>
<AttributeEncoder encodeType="false" friendlyName="memberOfFiltered" name="urn:mace:dir:attribute-def:memberOfFiltered" xsi:type="SAML2String"/>
</AttributeDefinition>2. update the groupMatchingRegexp with a suitable regexp value. Use these links for reference and validation
This script receives as input the full list of user groups in DN format (e.g. CN=Alerts,OU=Dev,DC=dev,DC=local) and outputs only the groups that match groupMatchingRegexp
If needed, the script can be altered to filter groups that don’t match the regex (negation) or to allow usage of multiple regex by modifying the javascript.
3. Select the desired application from Admin Dashboard → Applications, edit it and add memberOfFiltered attribute in the Attributes filed.
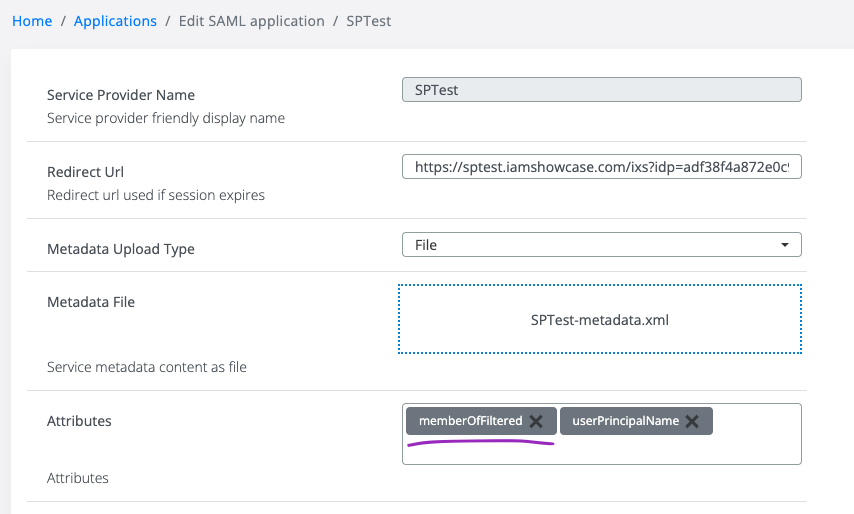
4. Perform an authentication and observe the output.
Troubleshoot
Attribute is not present in the output -> the Application setup may not have been loaded by Shibboleth. Try forcing context reload by modifying Authentication Default Lifetime value under Admin Dashboard → Settings → SAML
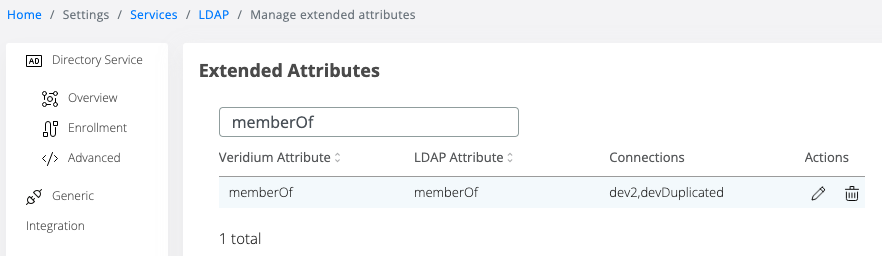
Attribute is not present in the output -> make sure memberOf is returned by LDAP
LDAP → Manage Extended Attributes
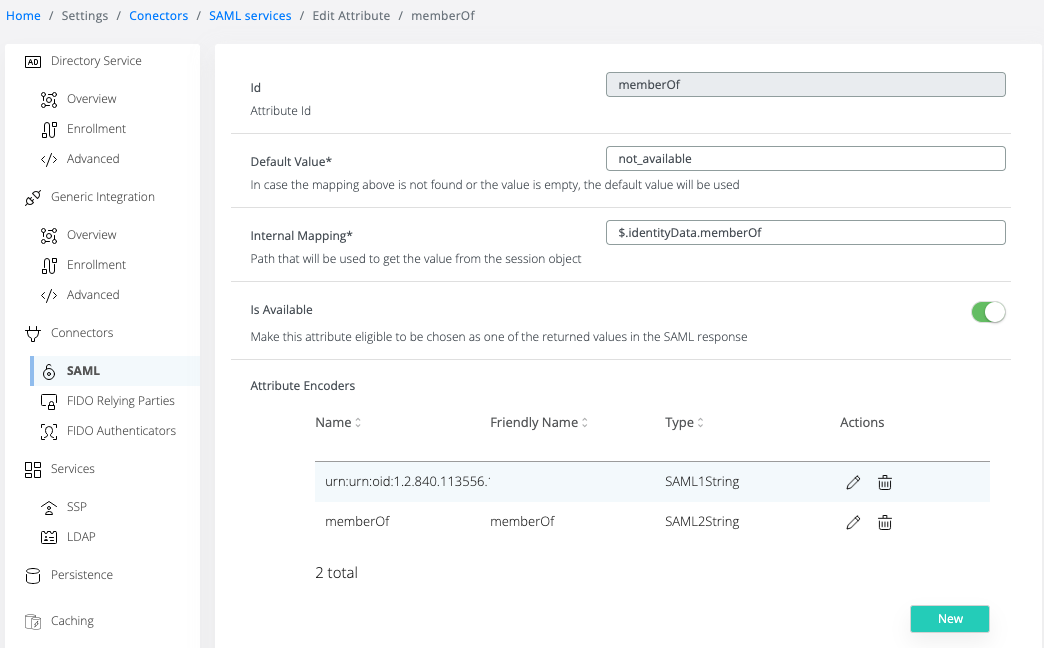
and is defined as SAML attribute under SAML → Subject Derived Attributes
Attribute does not contain the proper values → A logger can be added in the script above and observe the output in idp-process.log
<Script><![CDATA[
logger = Java.type("org.slf4j.LoggerFactory").getLogger("net.shibboleth.idp.saml.attribute.mapping");
groupMatchingRegex = /CN=Veridiumid_/gi
memberOfFiltered.getValues().retainAll([]);
for (i = 0; i < memberOf.getValues().length; i++) {
currentGroup = memberOf.getValues().get(i);
if (currentGroup.match(groupMatchingRegex)) {
logger.info("accepted " + memberOf.getValues().get(i) );
memberOfFiltered.addValue(currentGroup);
}
else {
logger.info("rejected " + memberOf.getValues().get(i) );
}
}
]]></Script>